Web3 Security:クイズの答え
現在UPされているクイズの回答
Private Key Security
Important Exchange Security Features
Website & dApp Security
Recognizing Risk Signals on the Exchange
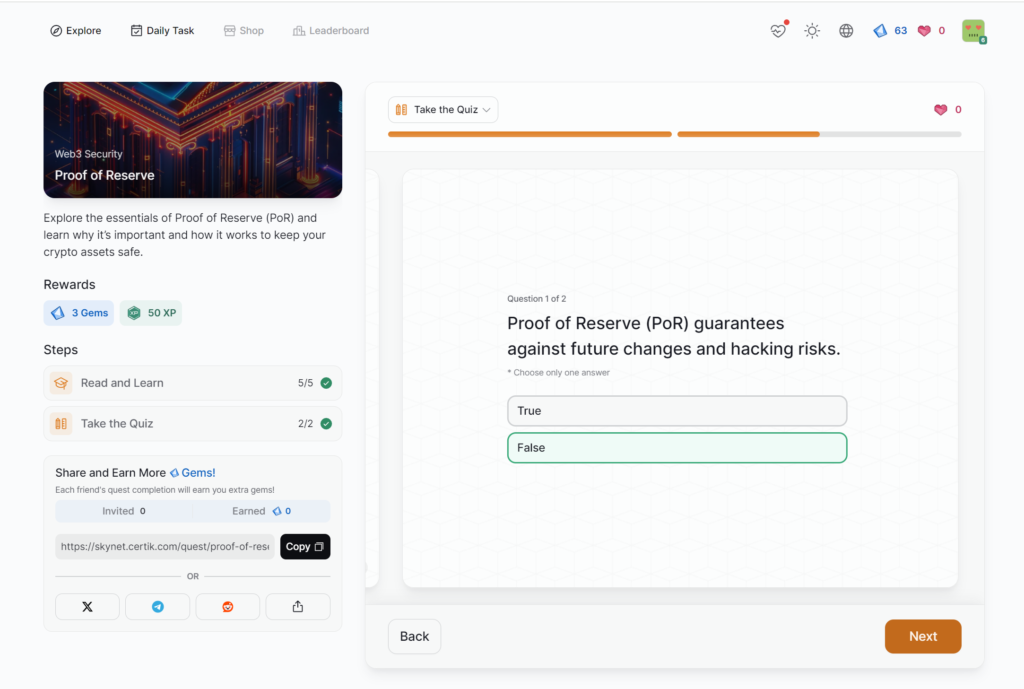
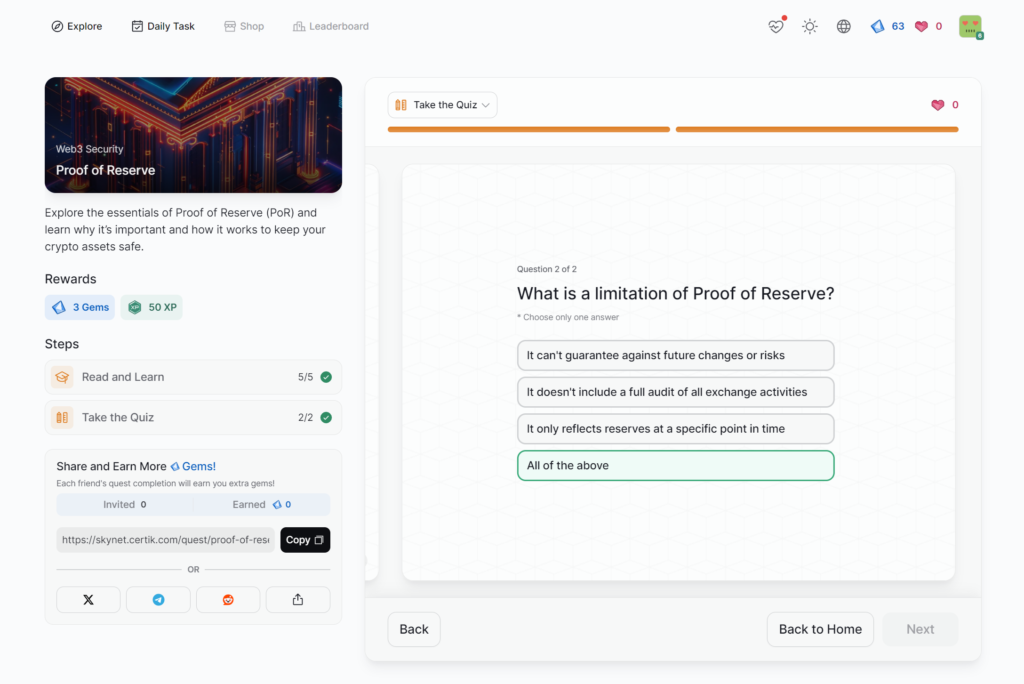
Proof of Reserve
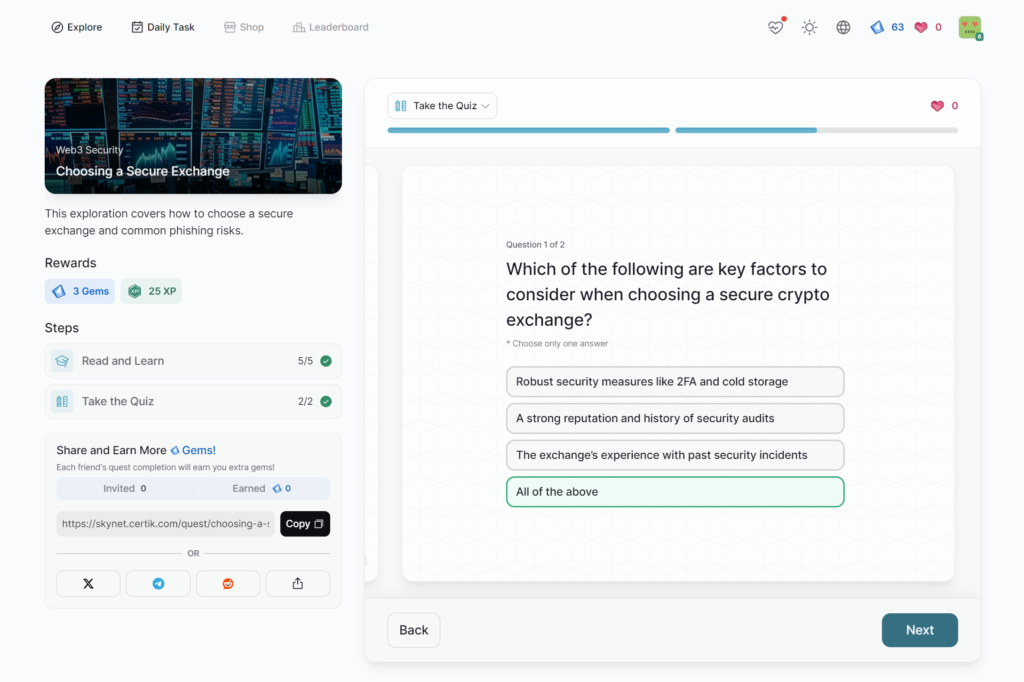
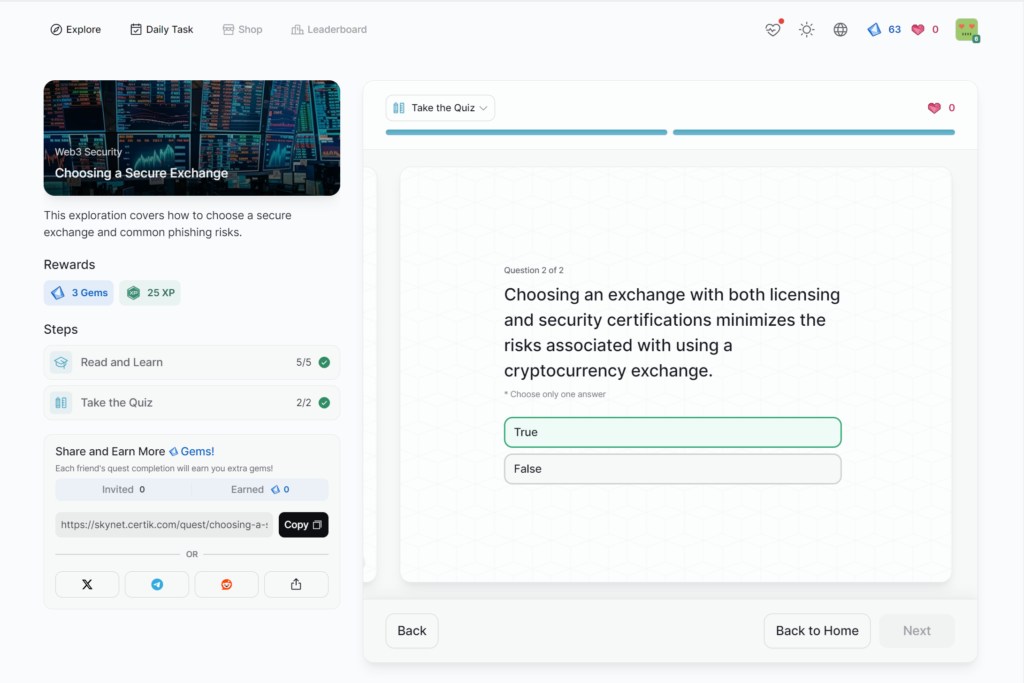
Choosing a Secure Exchange
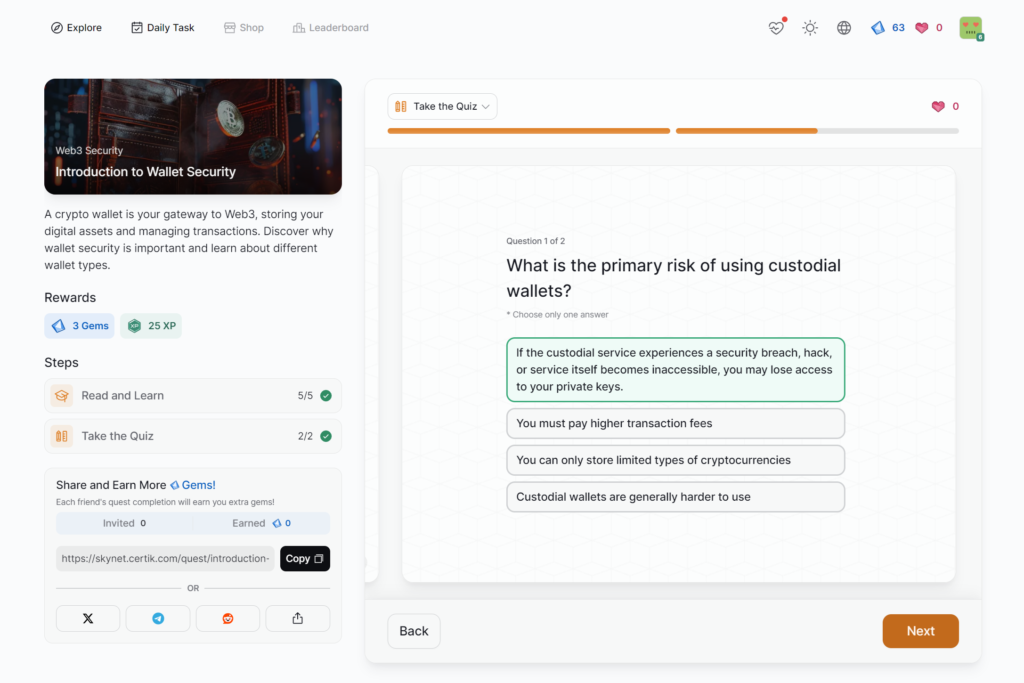
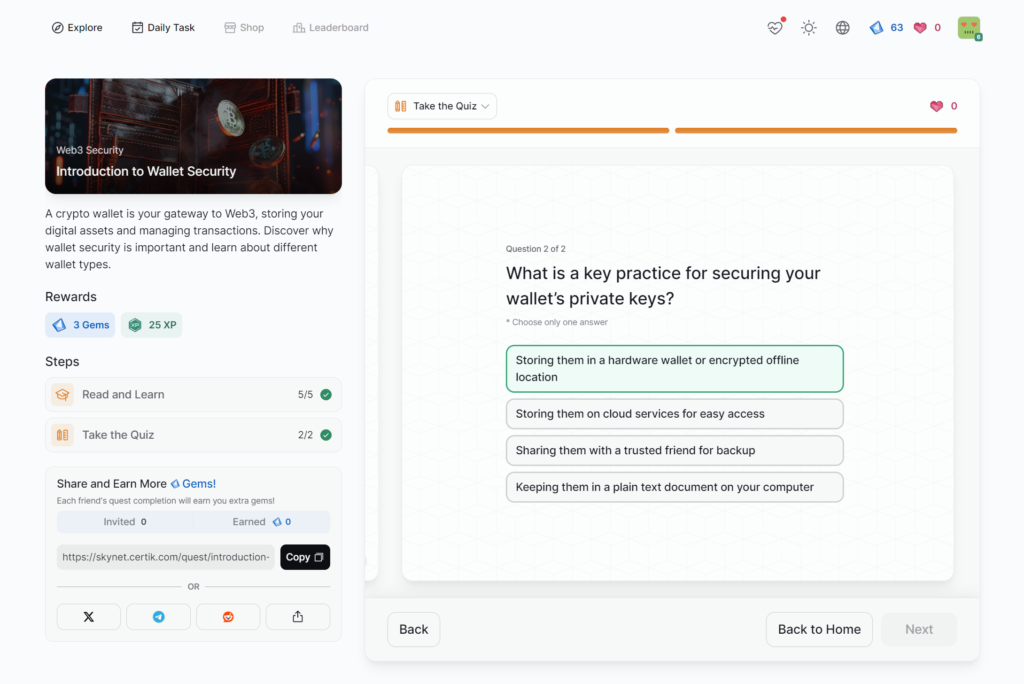
Introduction to Wallet Security
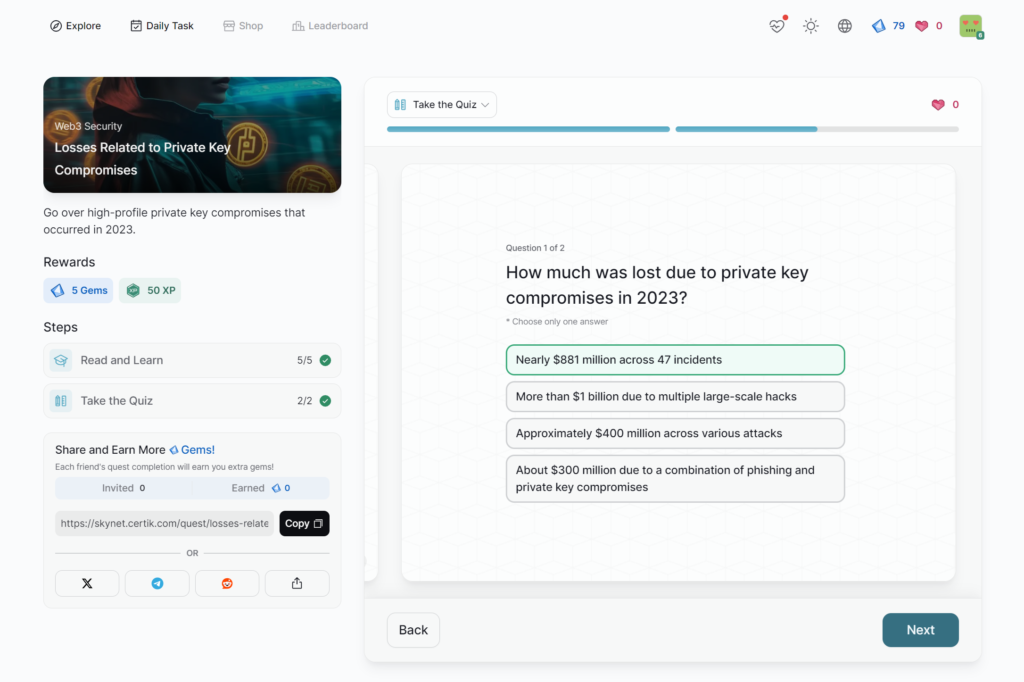
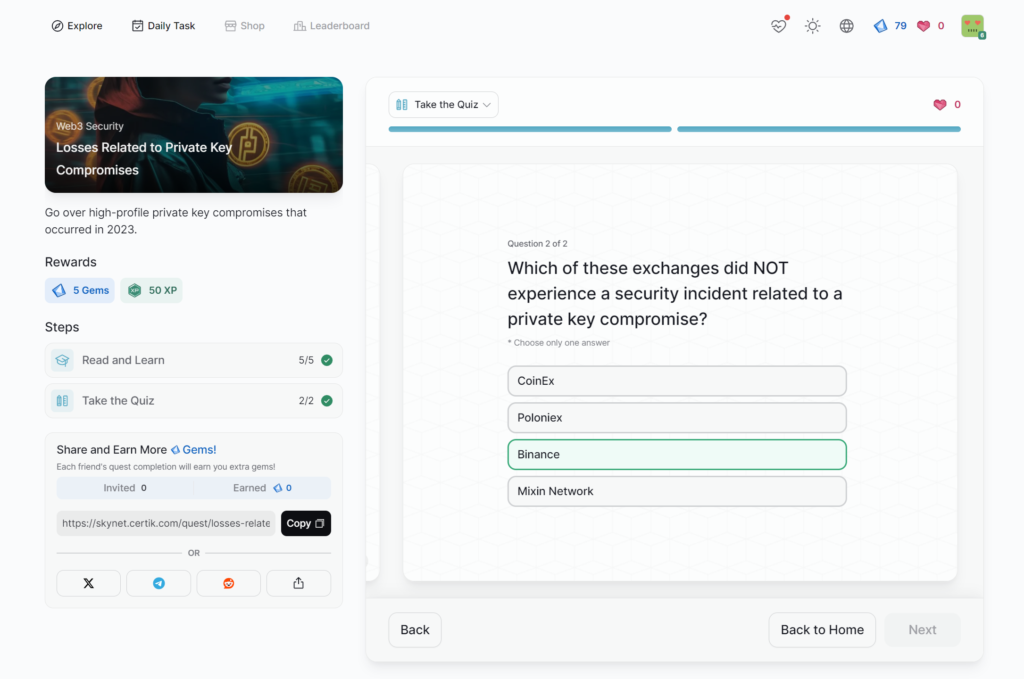
Losses Related to Private Key Compromises
Private Key Security: Seed Phrases
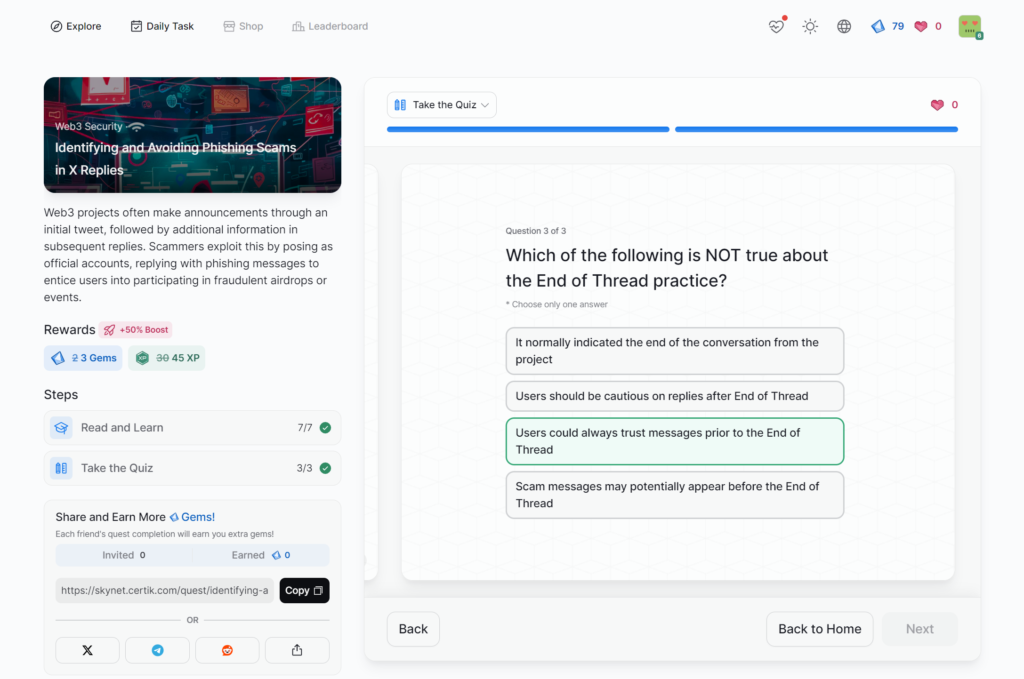
Identifying and Avoiding Phishing Scams in X Replies
Common Web3 Phishing Methods
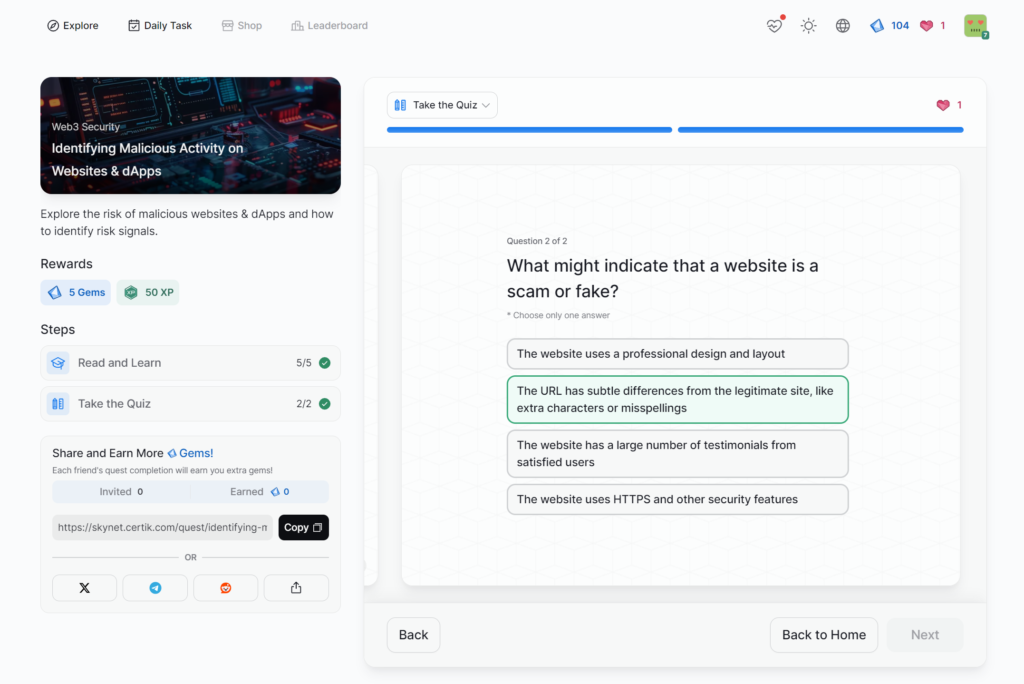
Identifying Malicious Activity on Websites & dApps
Introduction to User Security
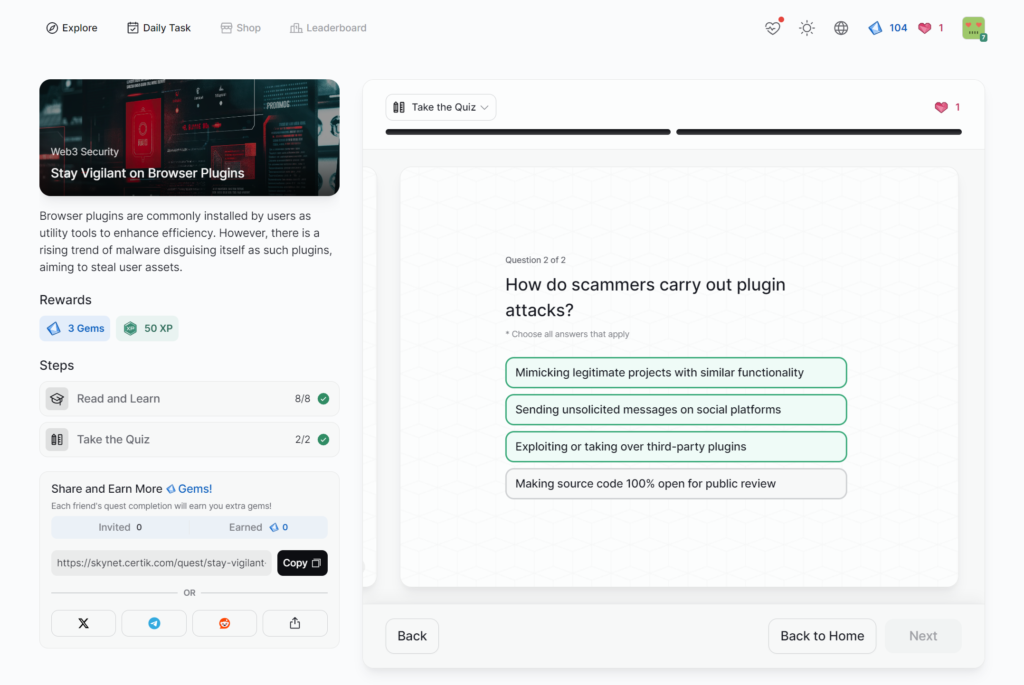
Stay Vigilant on Browser Plugins
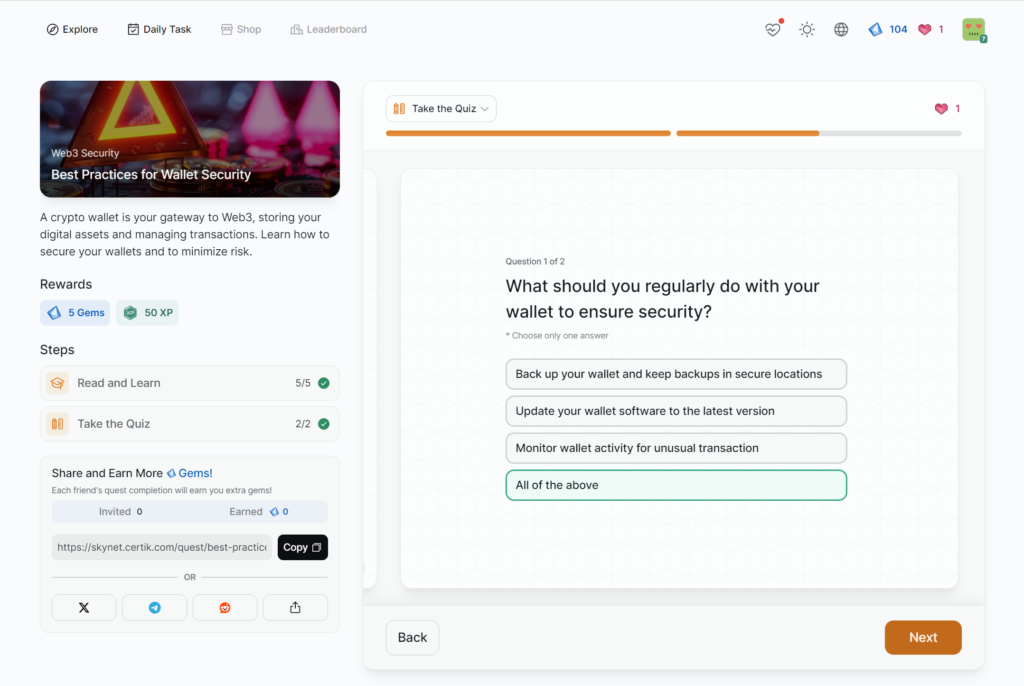
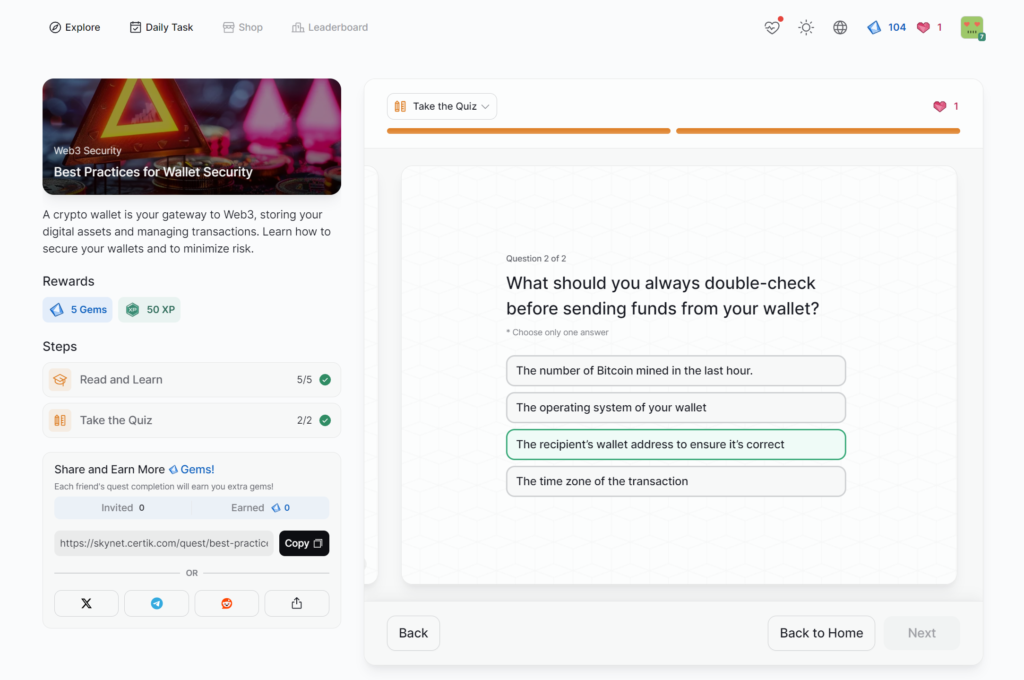
Best Practices for Wallet Security
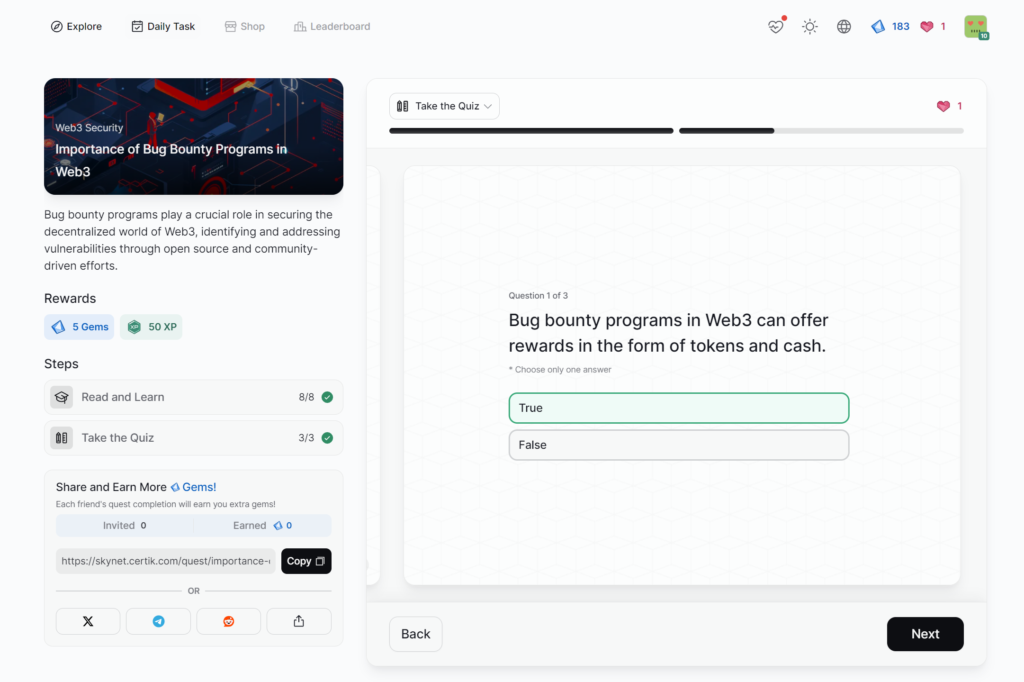
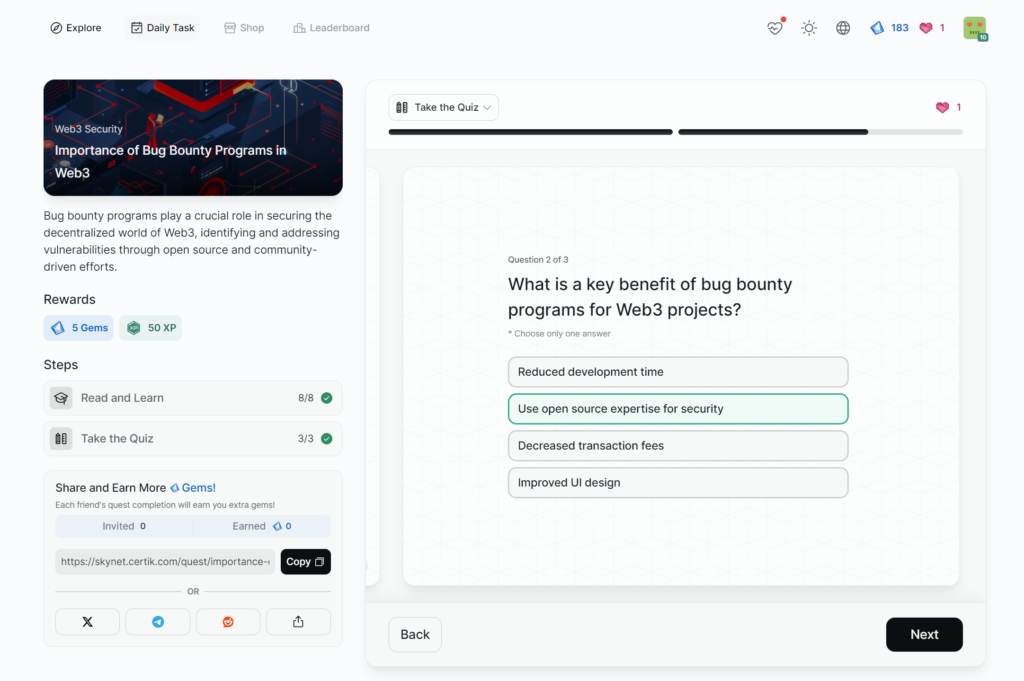
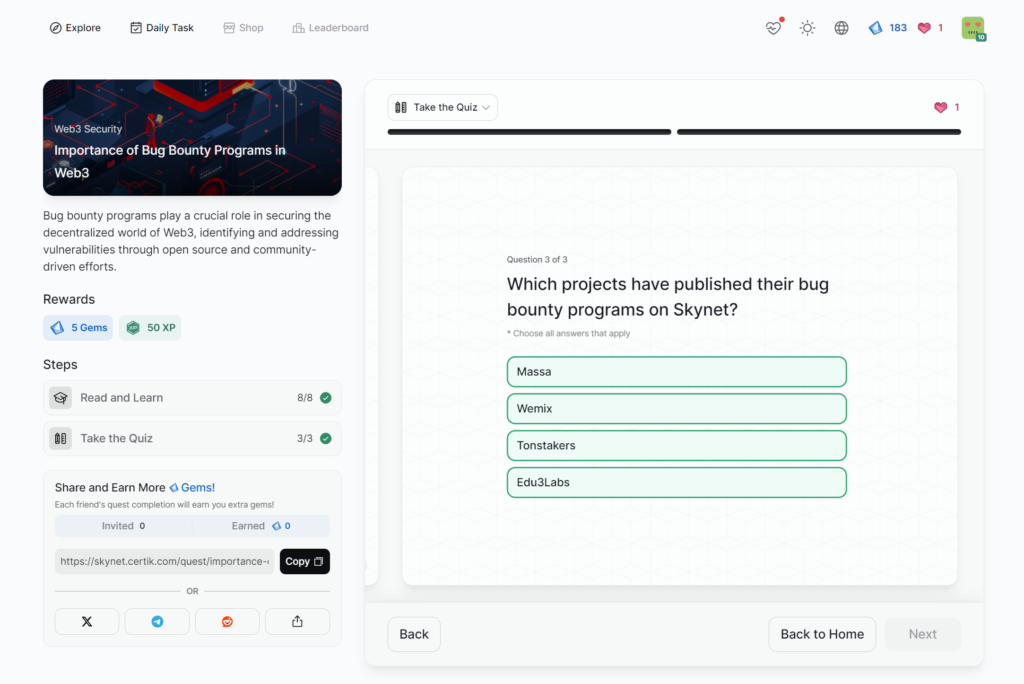
Importance of Bug Bounty Programs in Web3
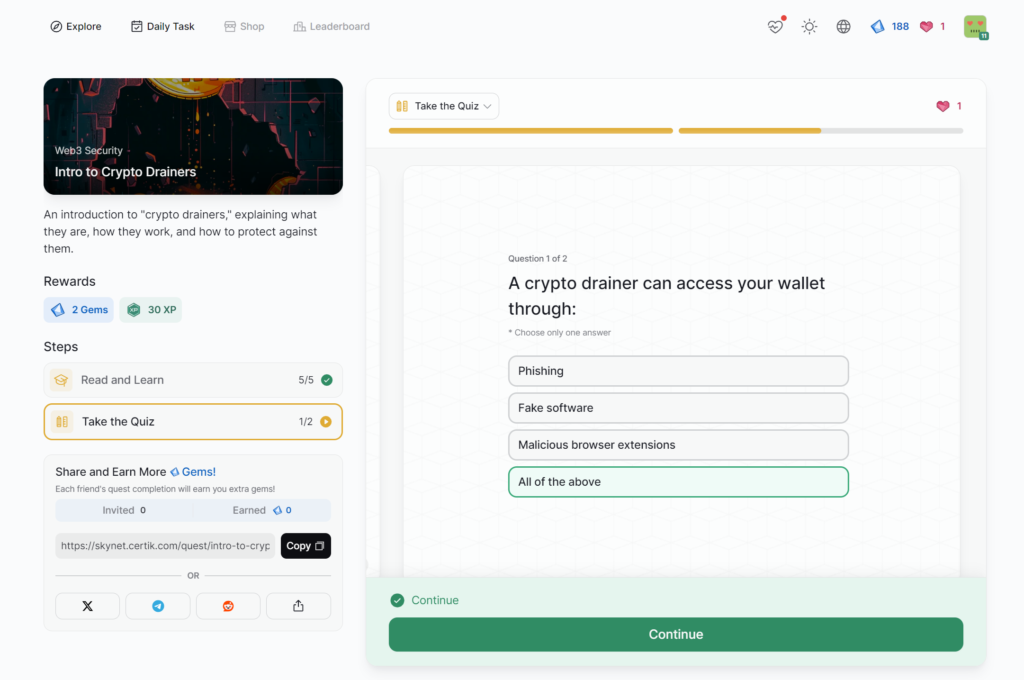
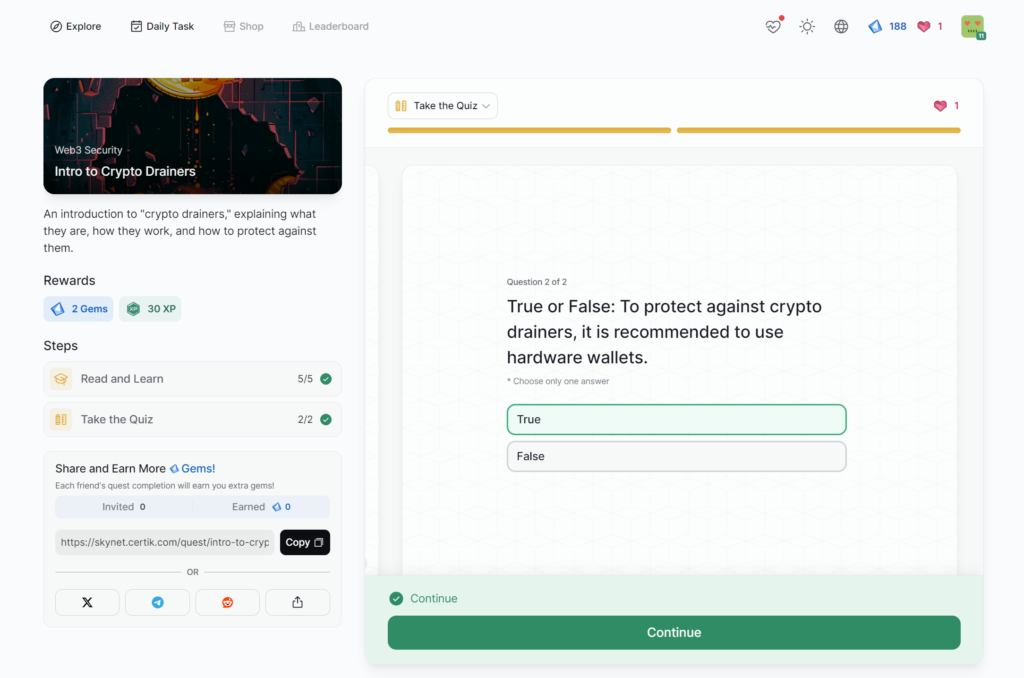
Intro to Crypto Drainers
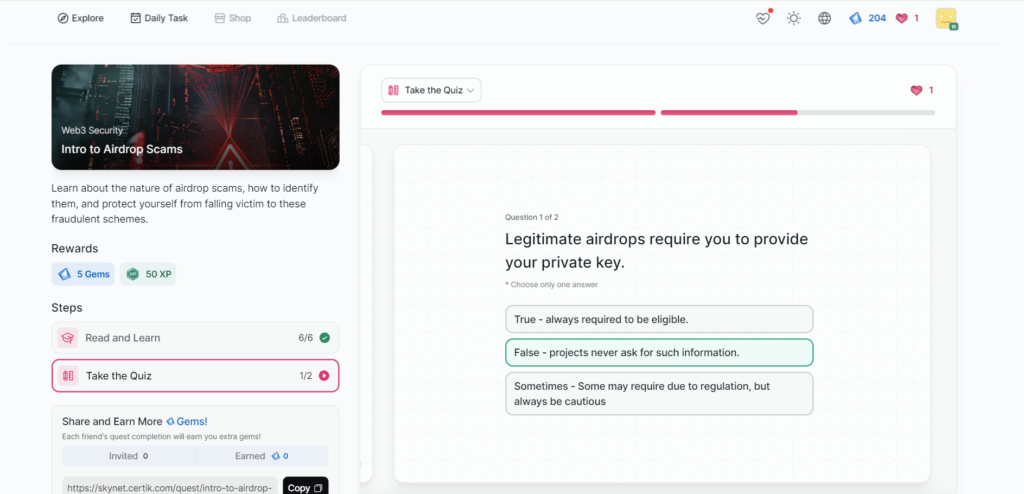
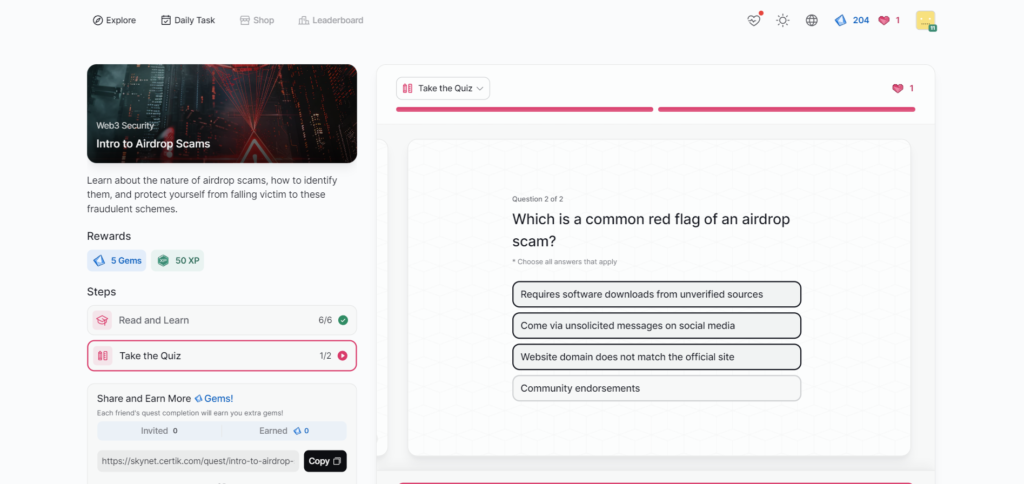
Intro to Airdrop Scams
Evaluating Cryptocurrency News Sources
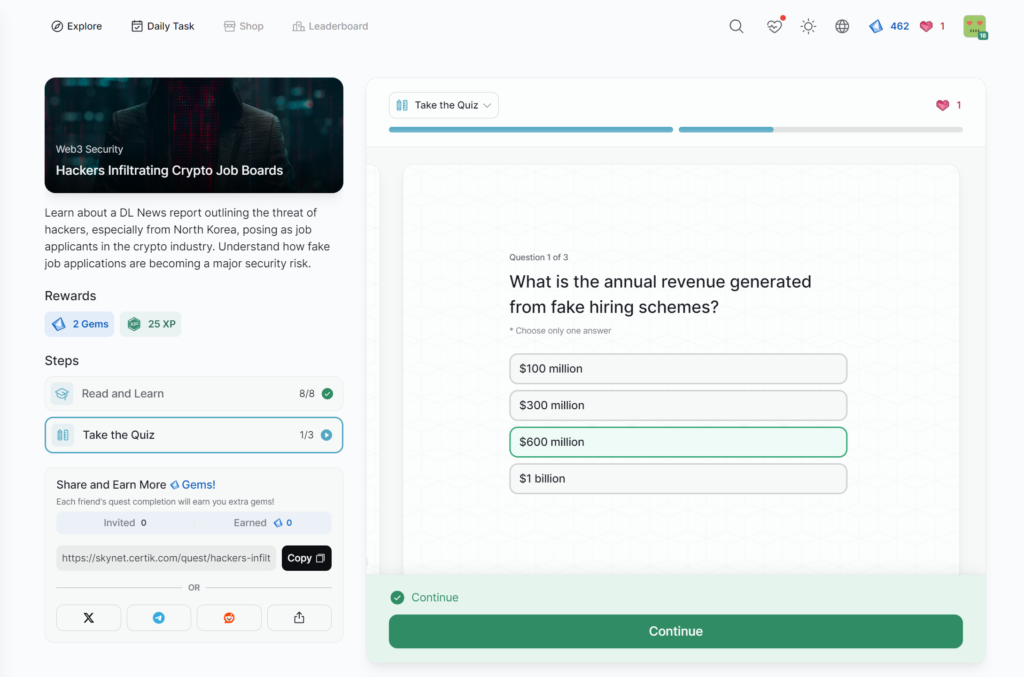
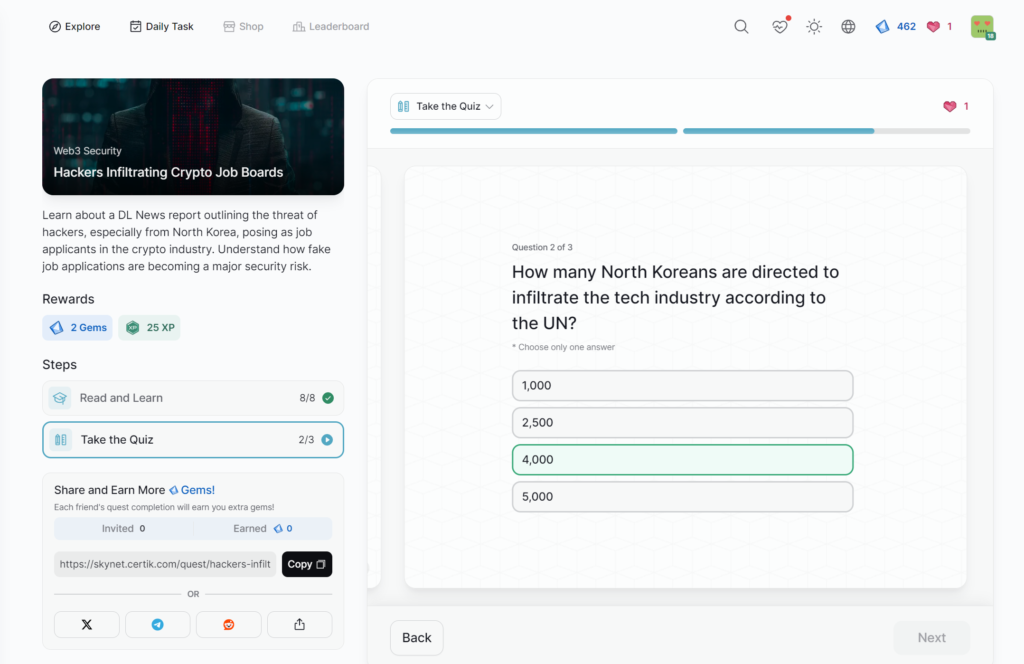
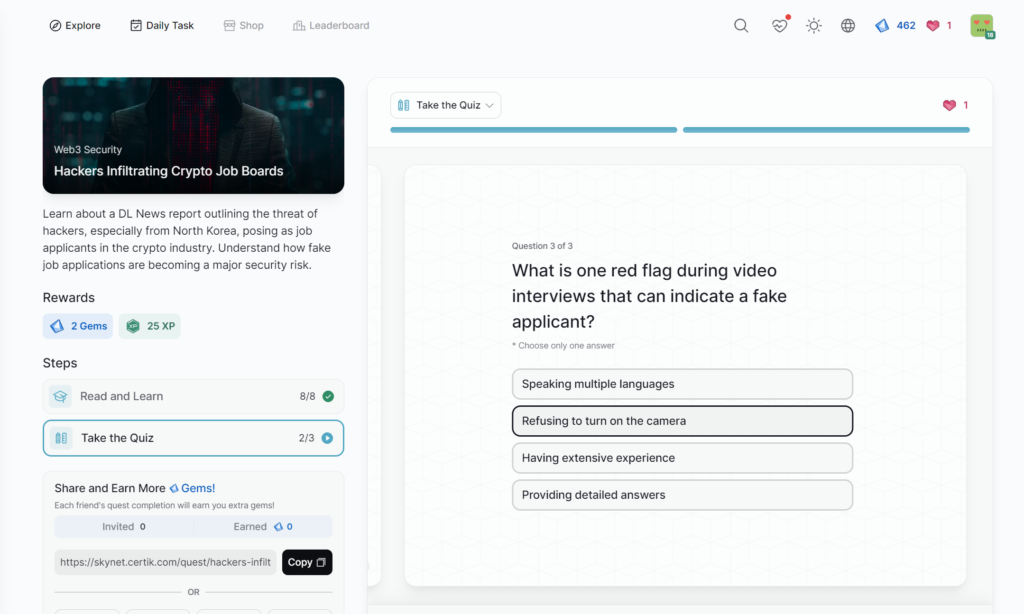
Hackers Infiltrating Crypto Job Boards
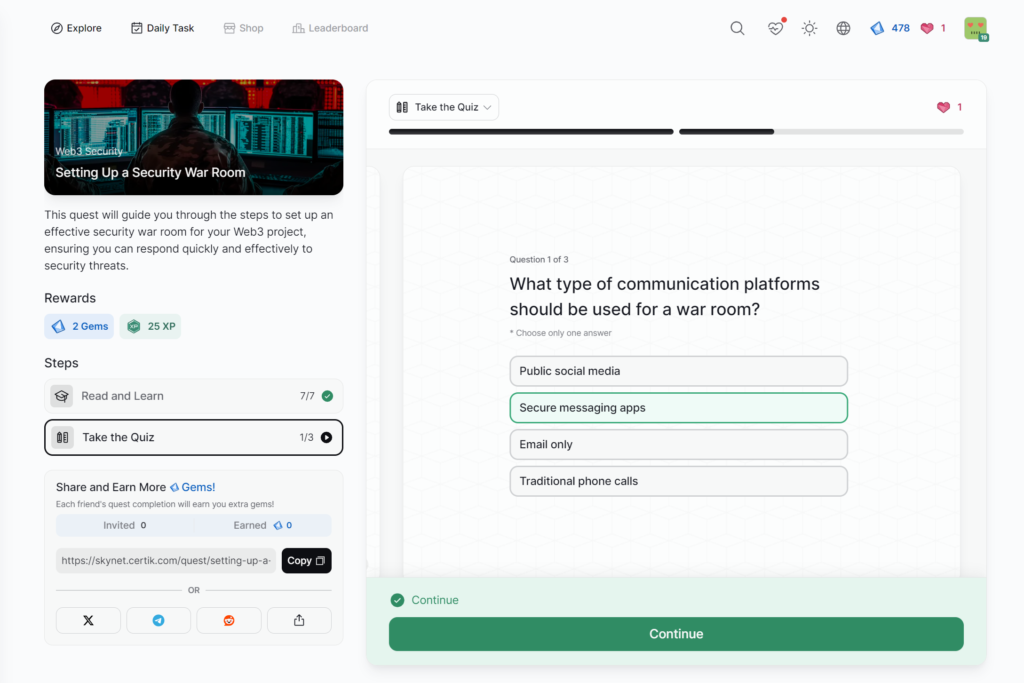
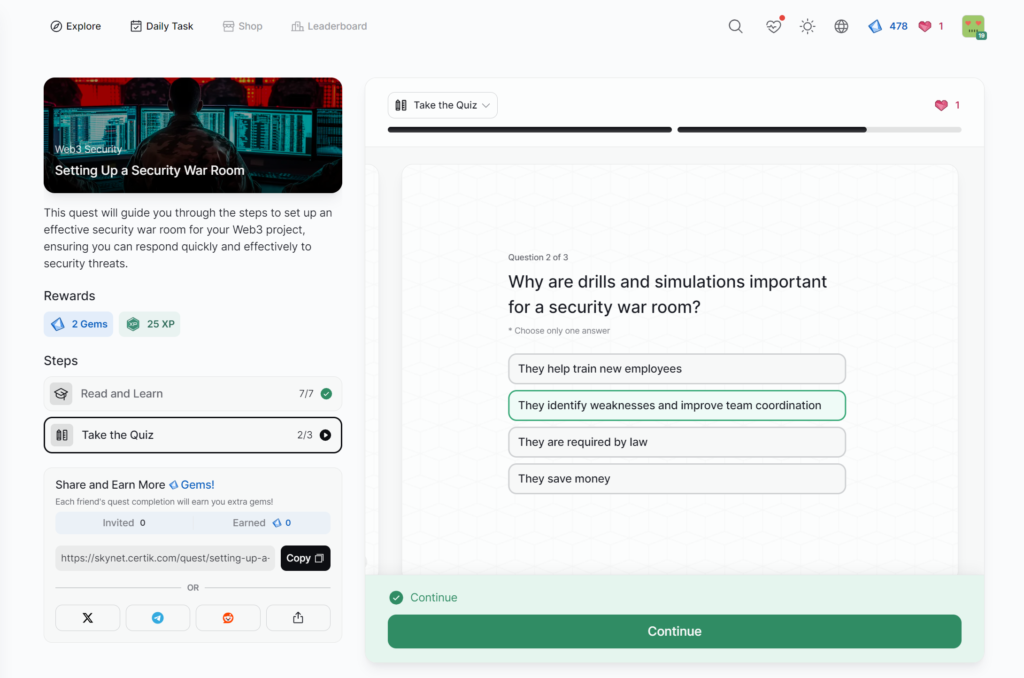
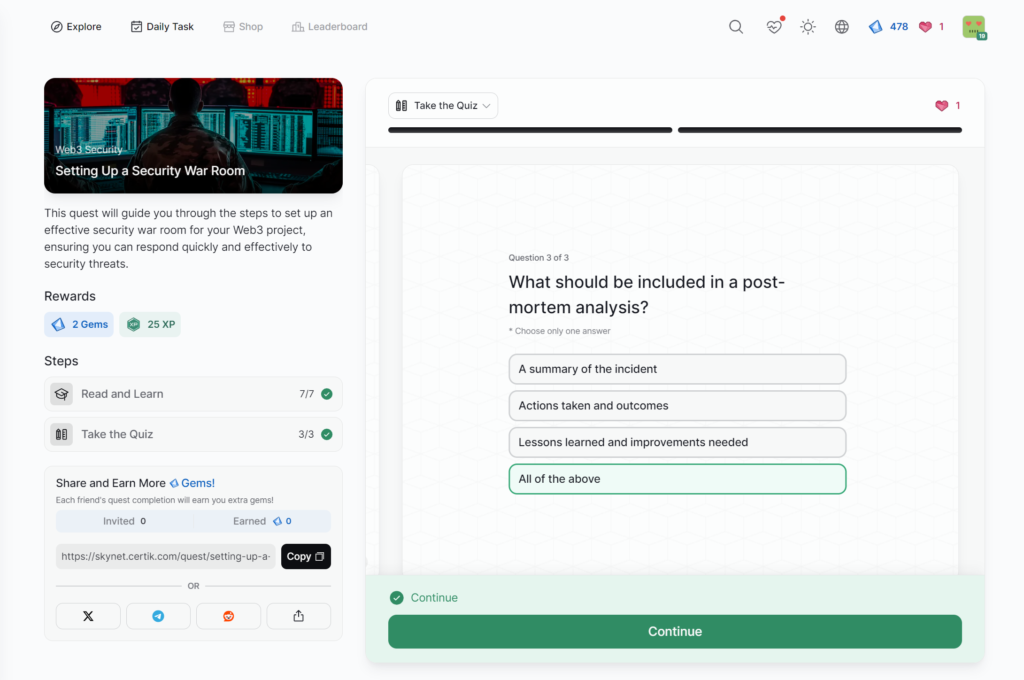
Setting Up a Security War Room
What Is a Keylogger?
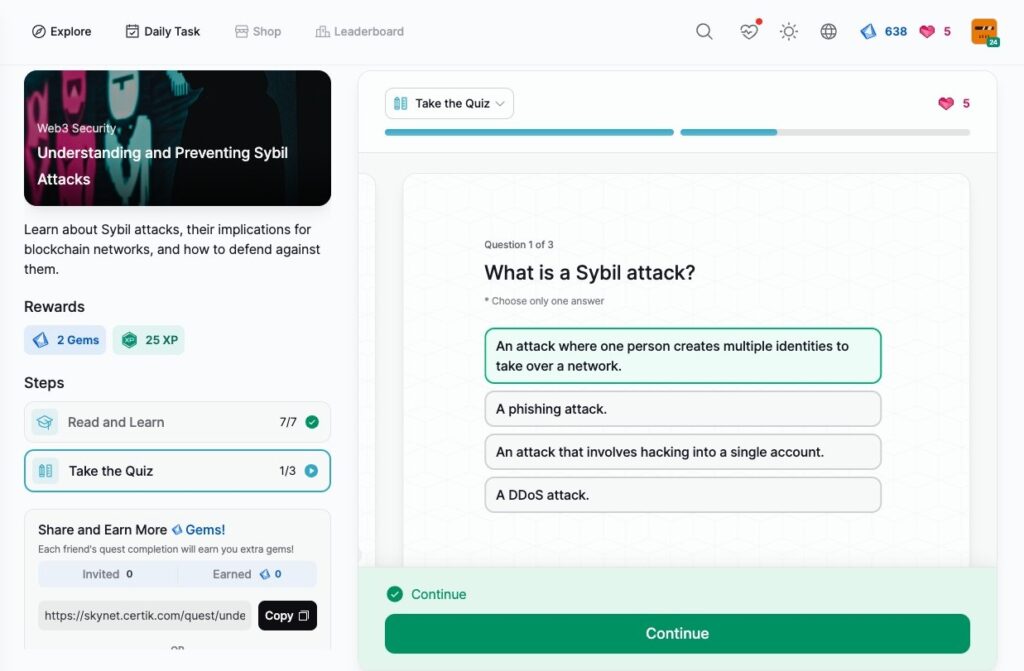
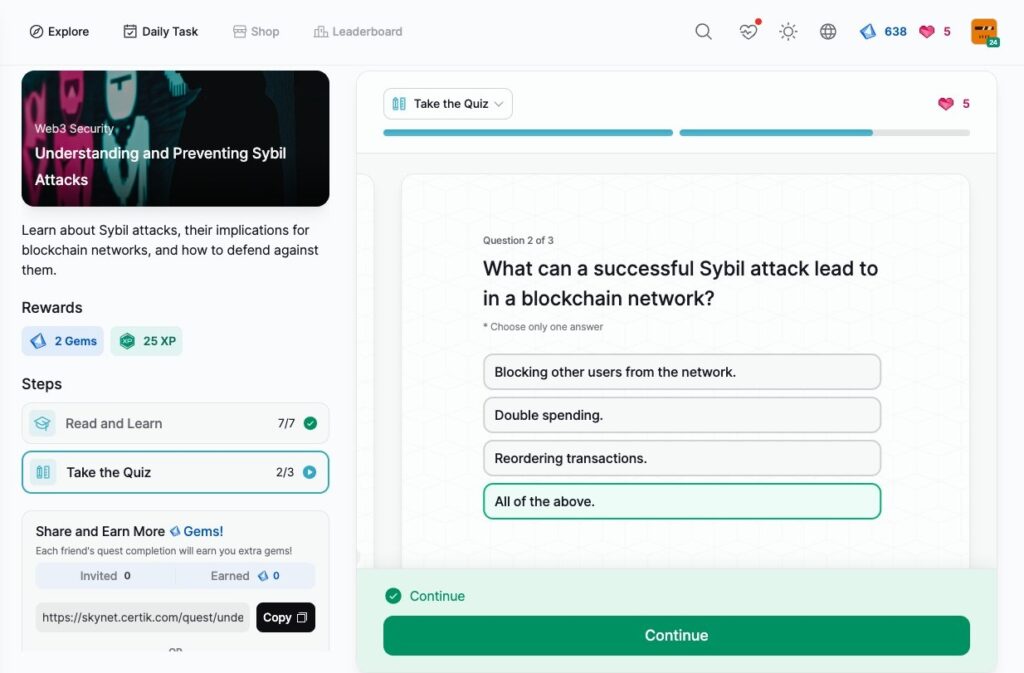
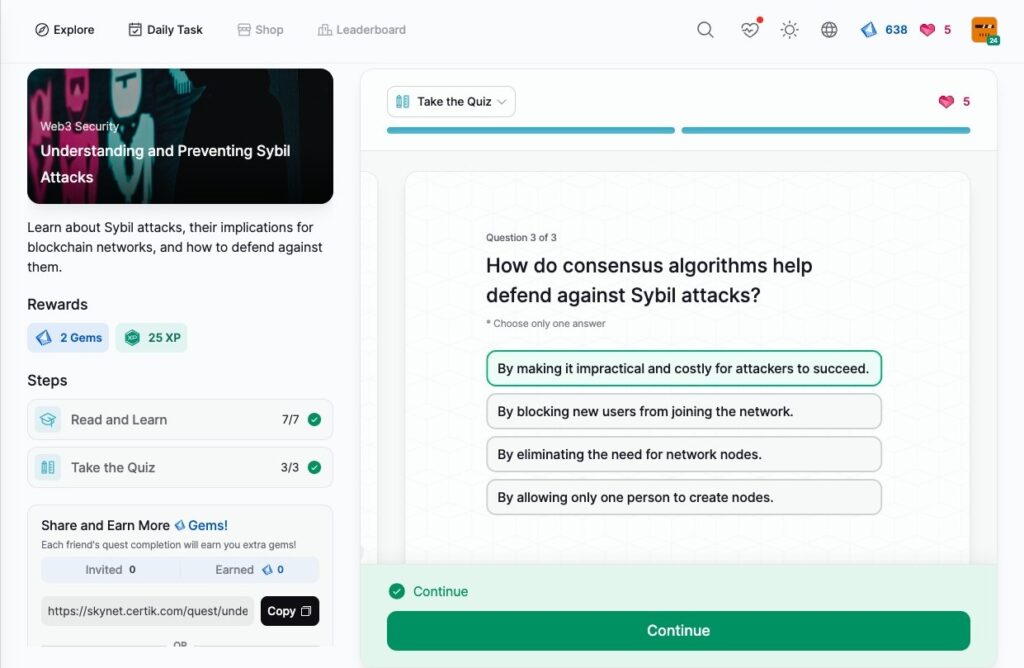
Understanding and Preventing Sybil Attacks
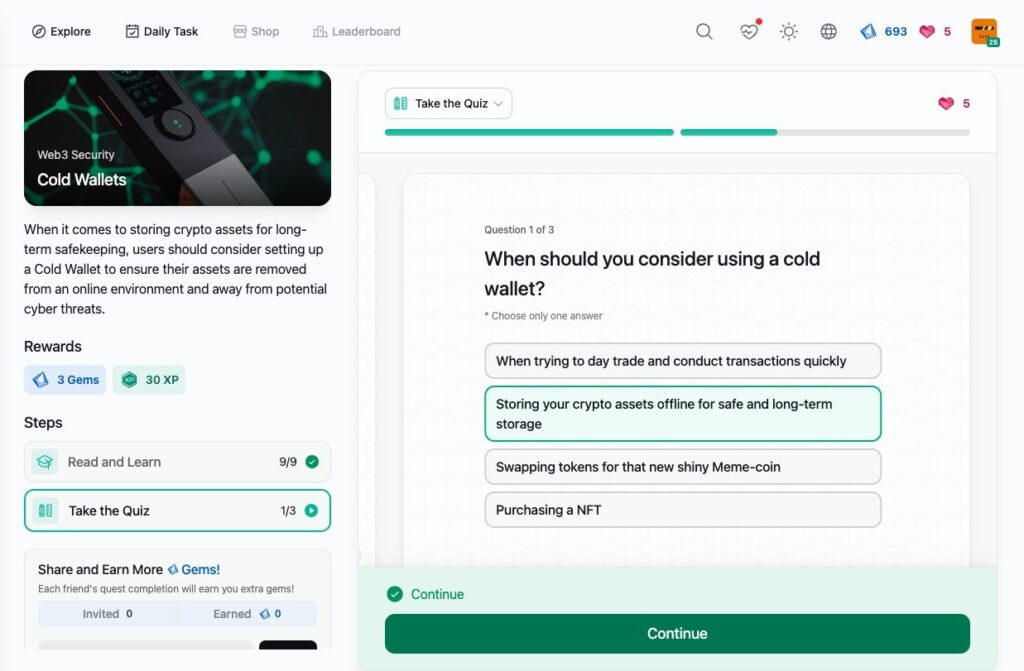
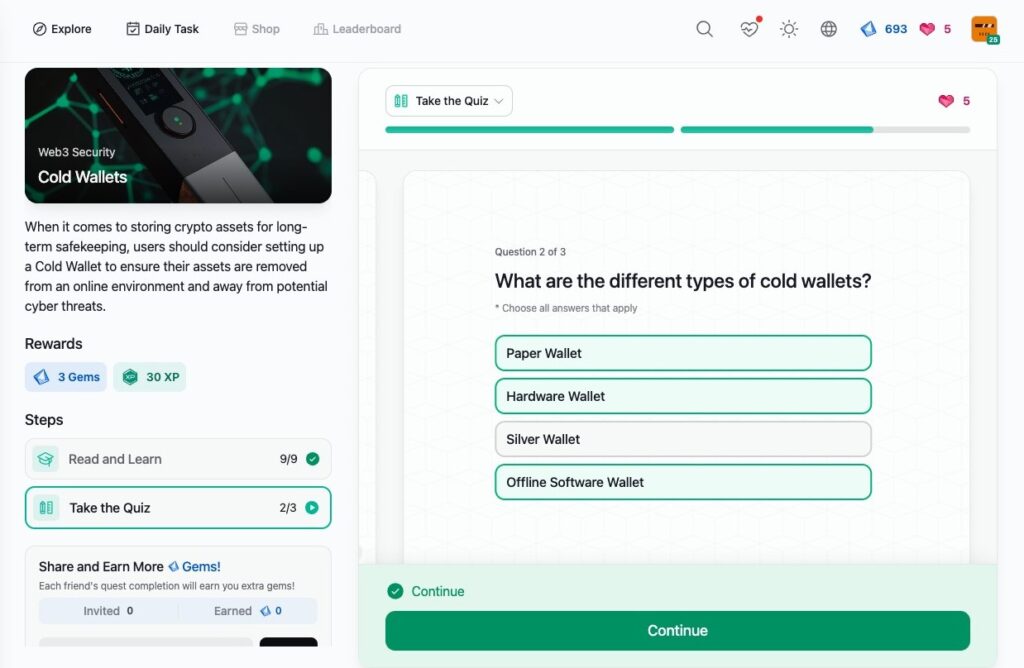
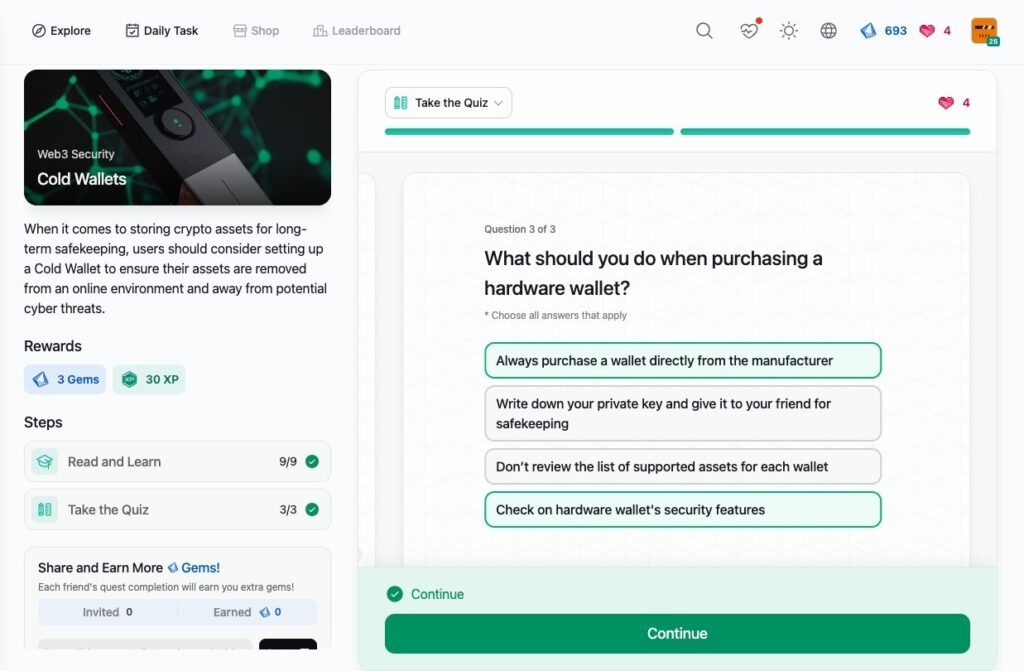
Cold Wallets
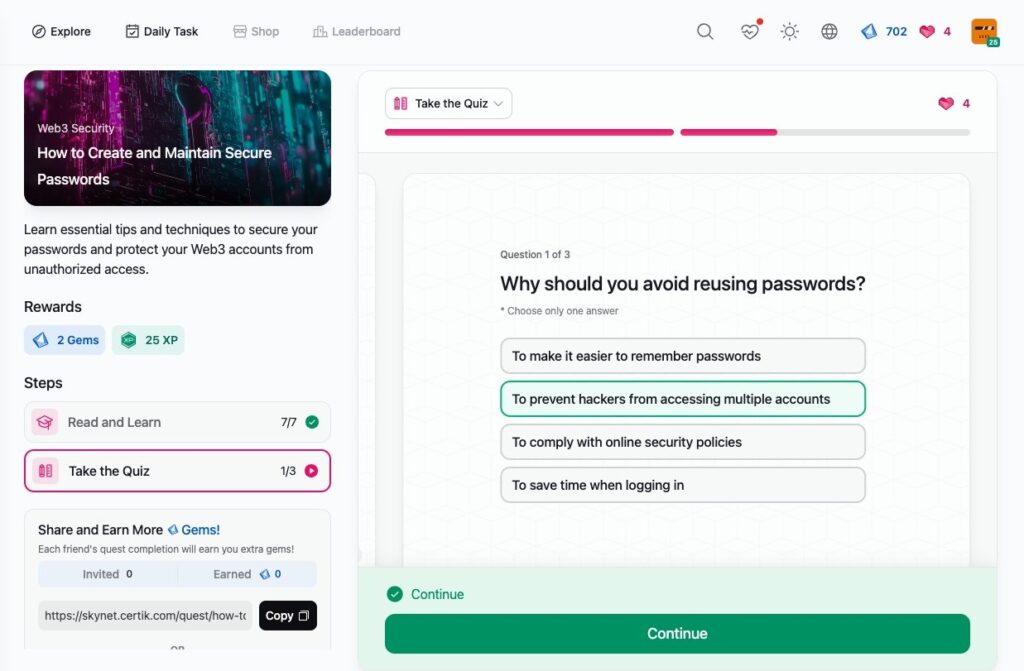
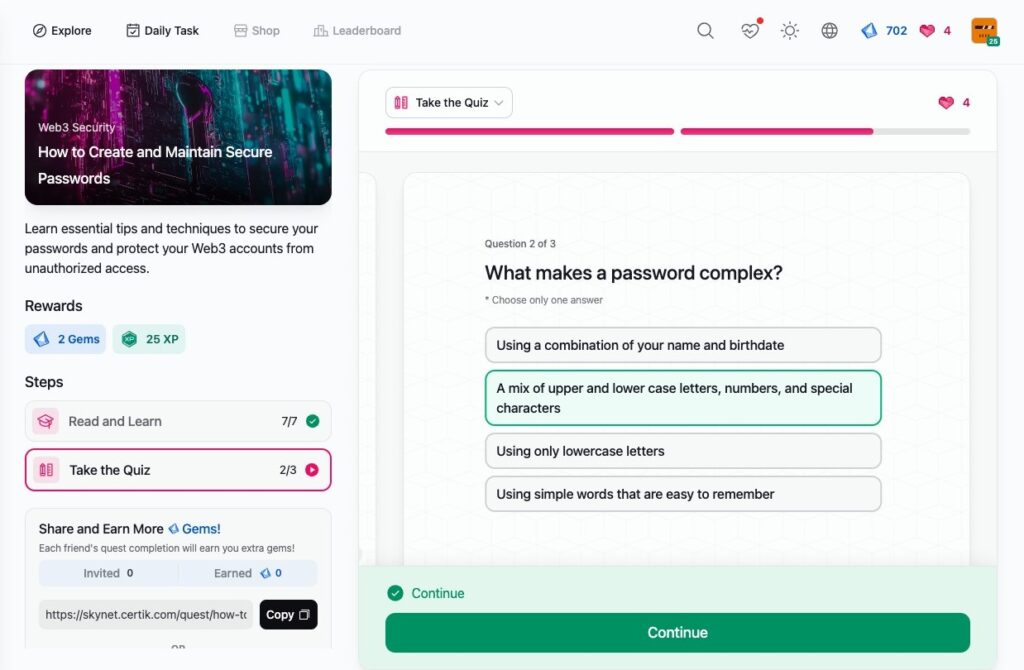
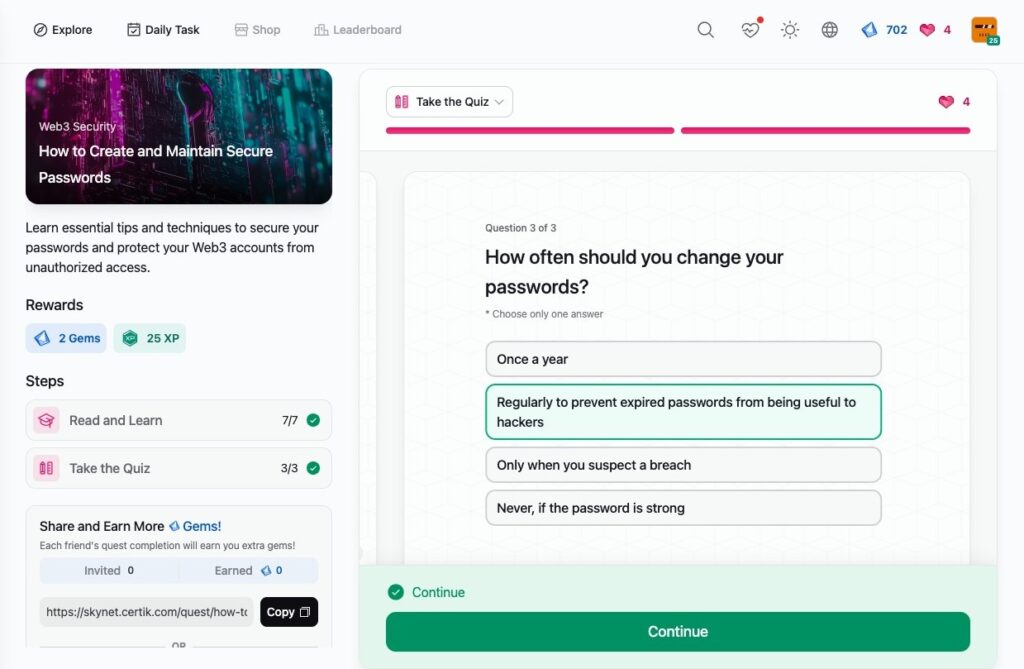
How to Create and Maintain Secure Passwords
Protecting Yourself from Discord Scams
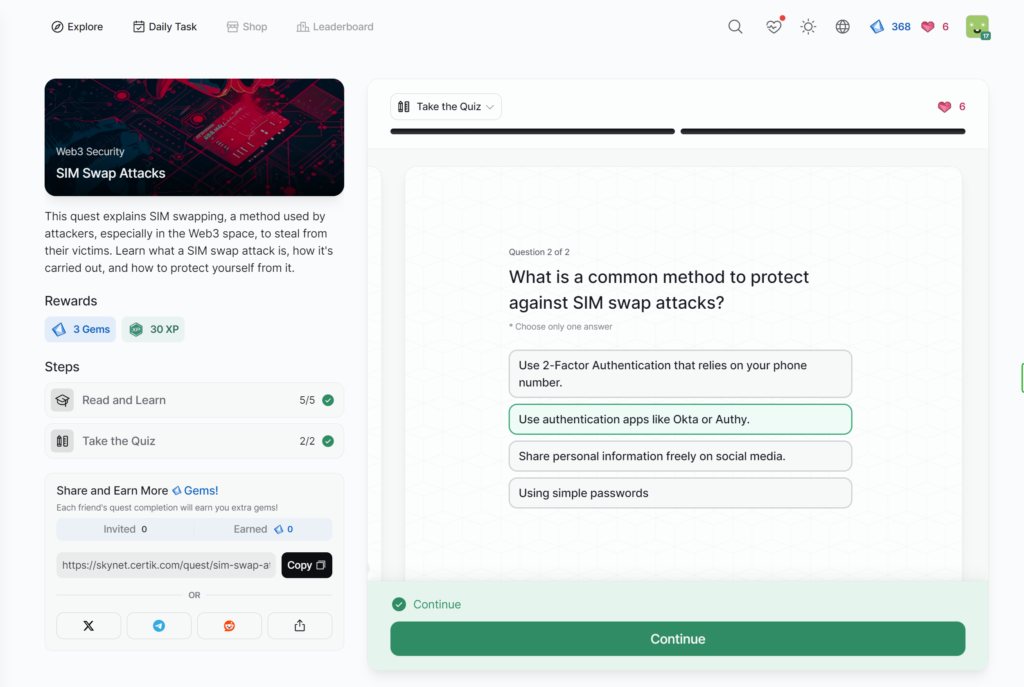
SIM Swap Attacks
Understanding and Mitigating 51% Attacks
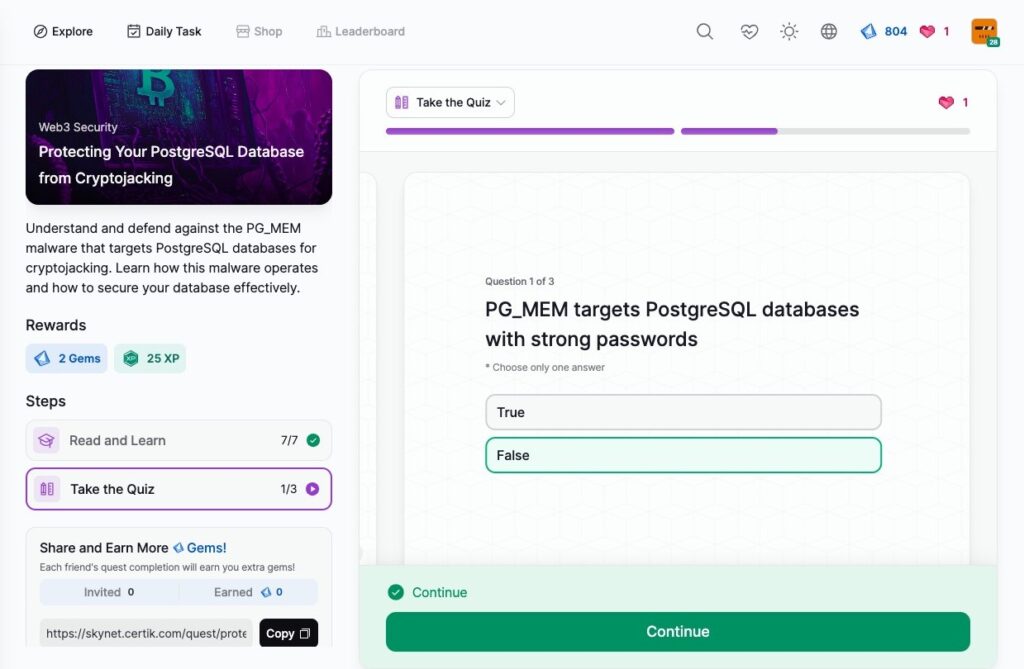
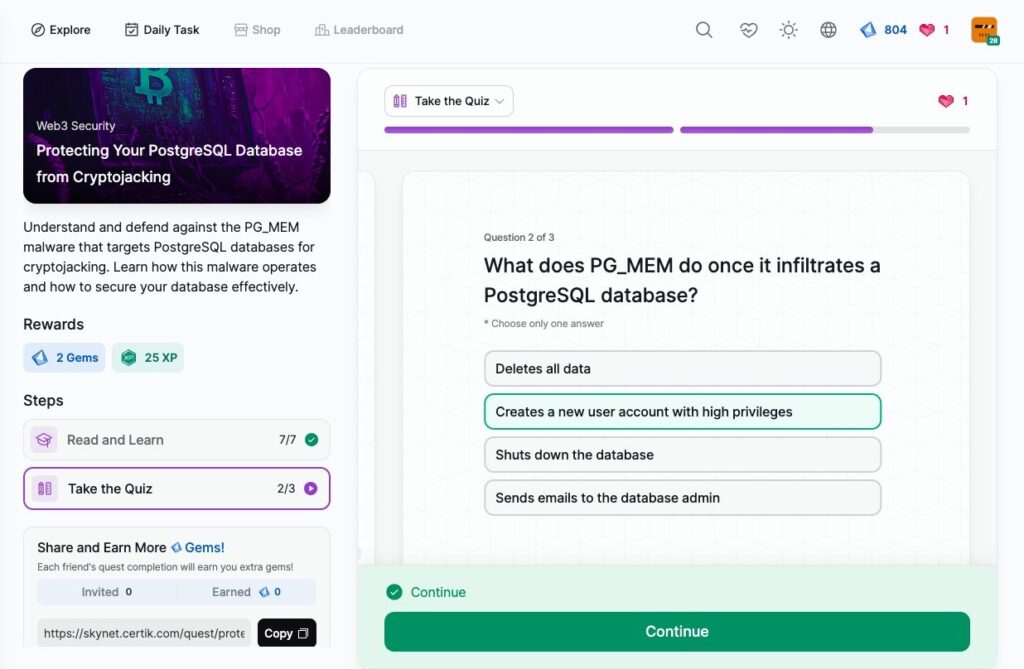
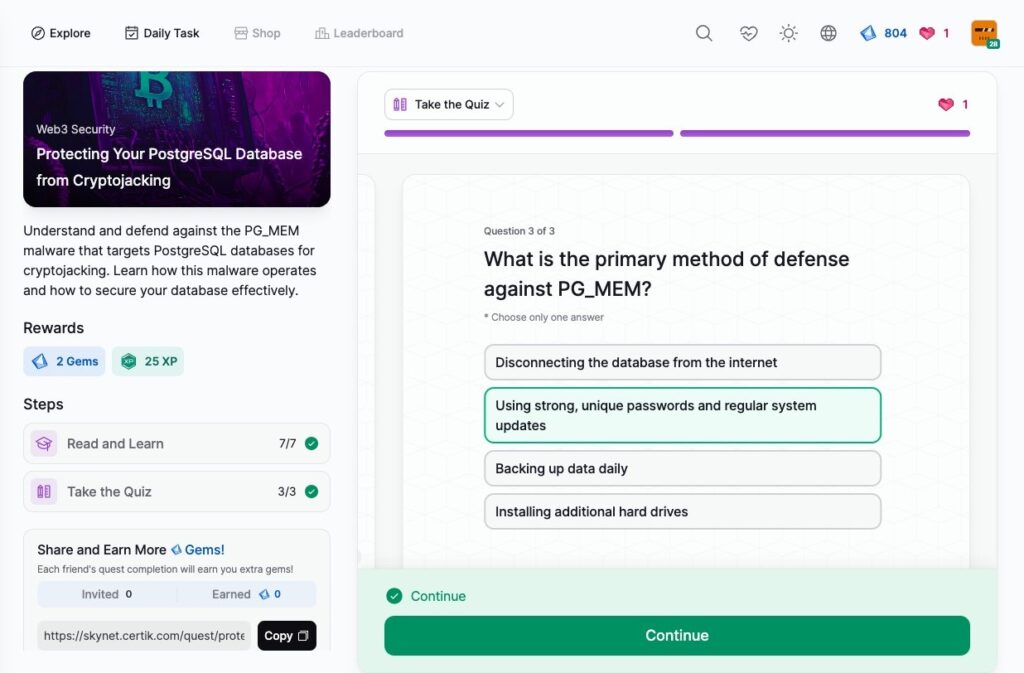
Protecting Your PostgreSQL Database from Cryptojacking
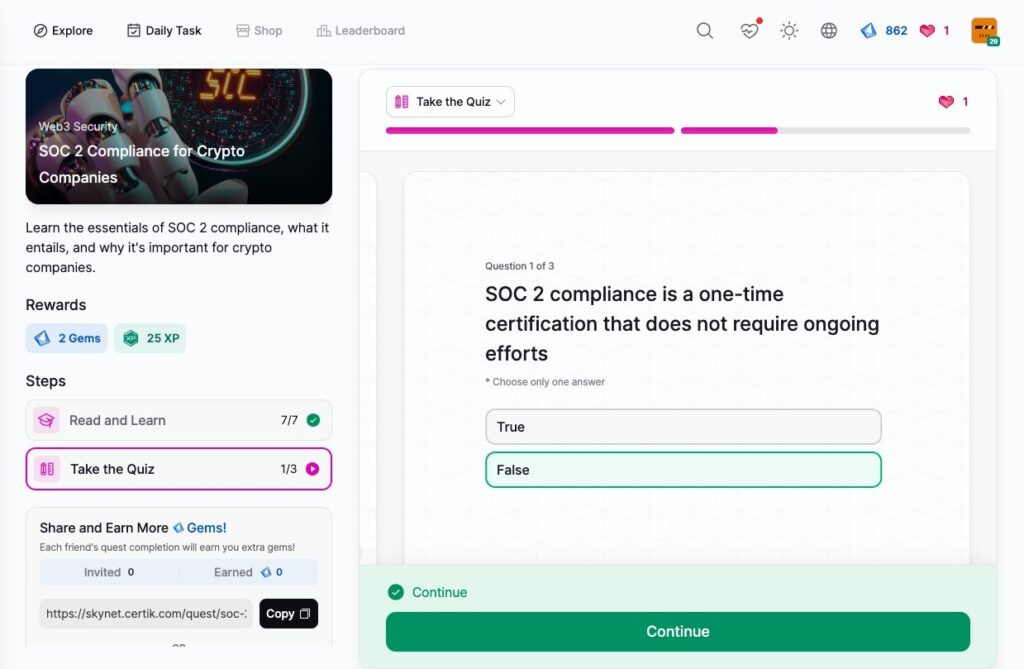
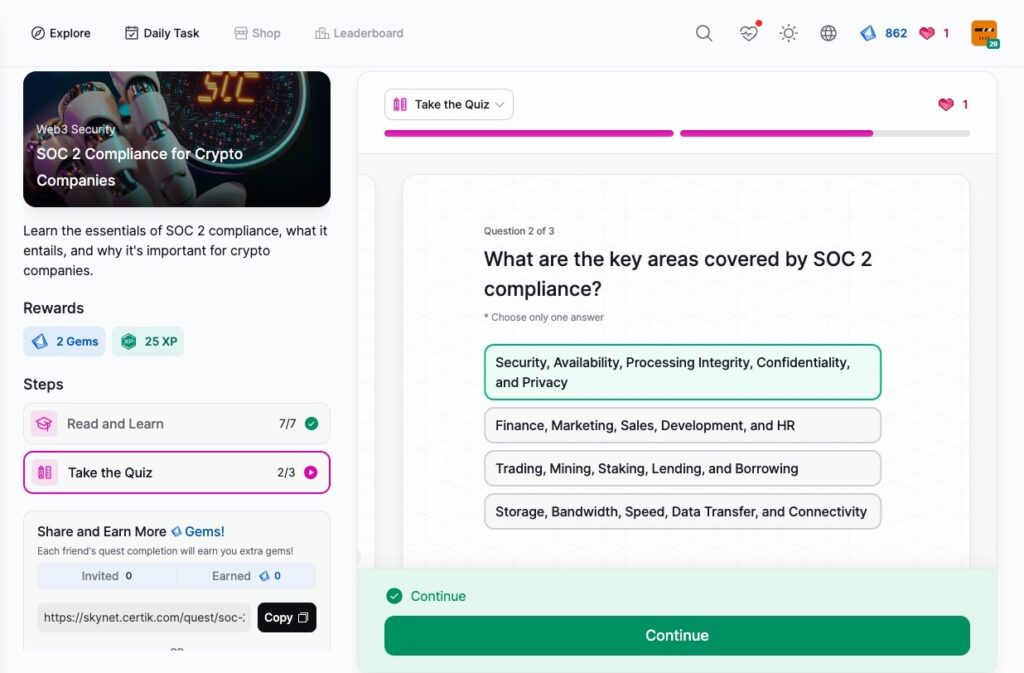
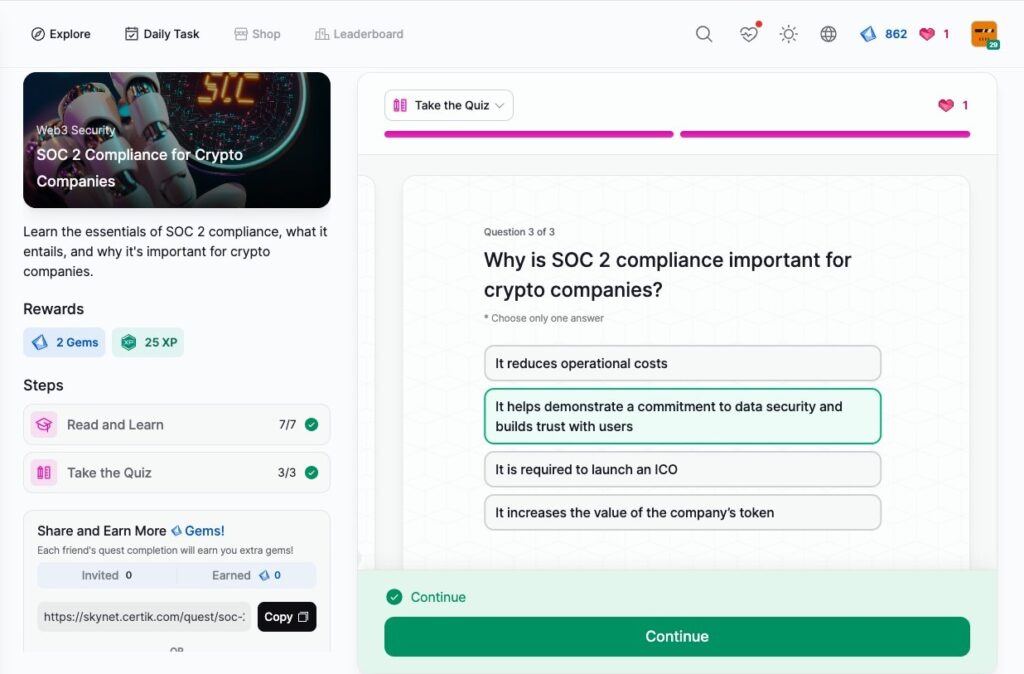
SOC 2 Compliance for Crypto Companies
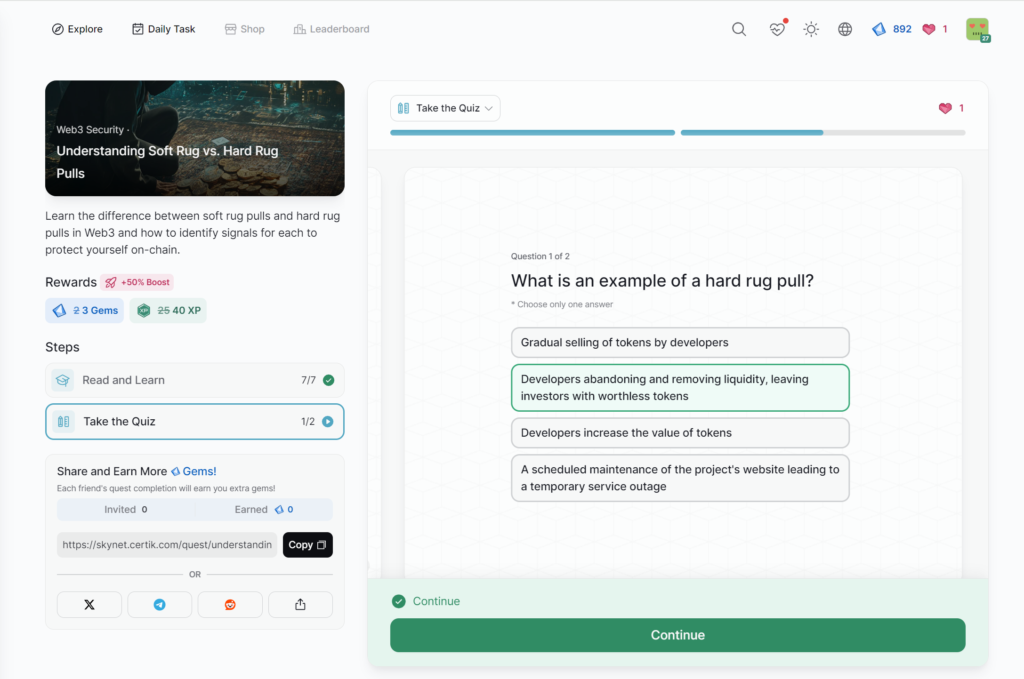
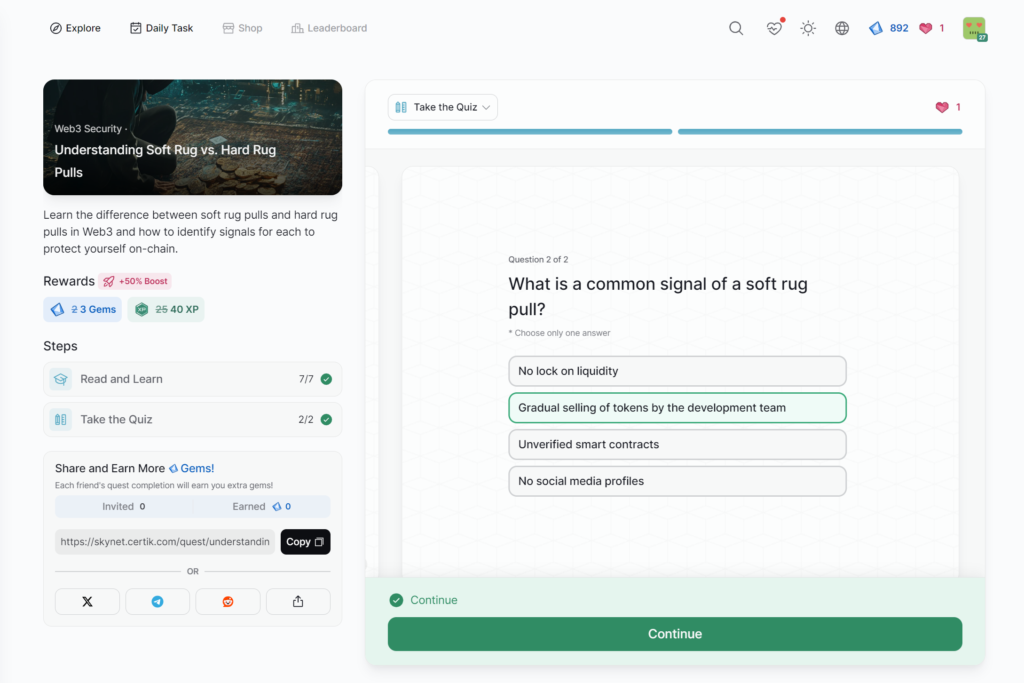
Understanding Soft Rug vs. Hard Rug Pulls
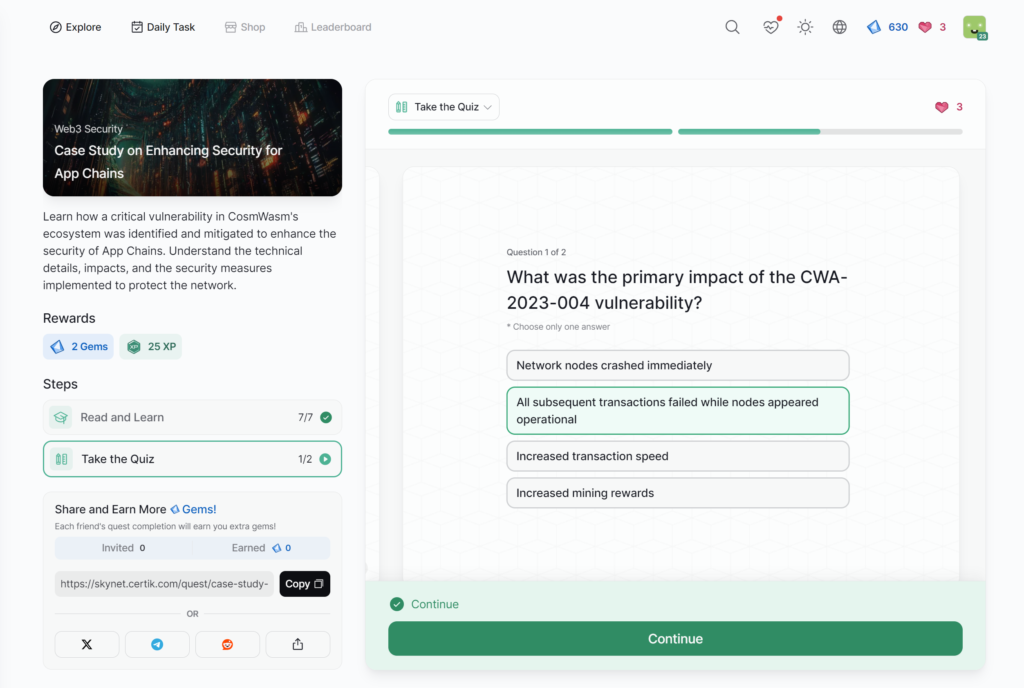
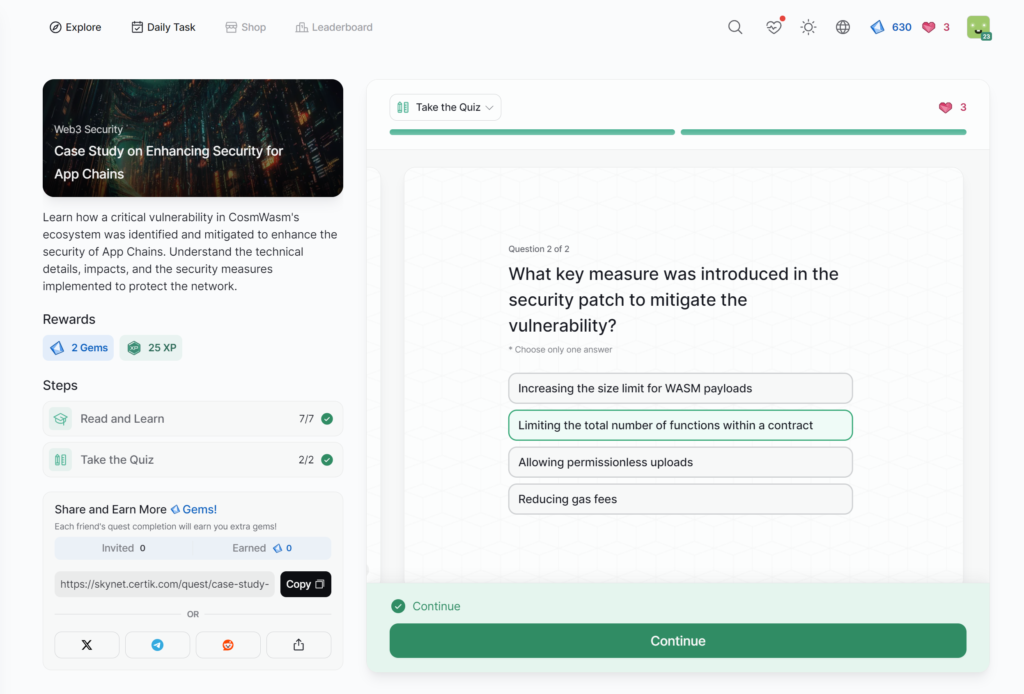
Case Study on Enhancing Security for App Chains
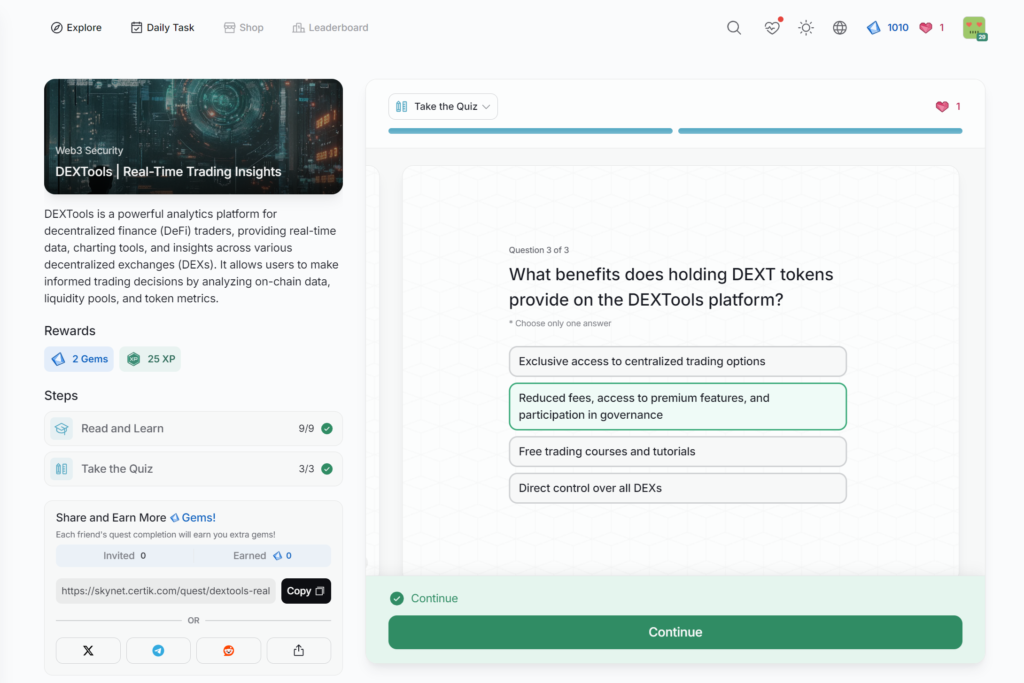
DEXTools | Real-Time Trading Insights
Understanding Economic Exploits and Tokenomics
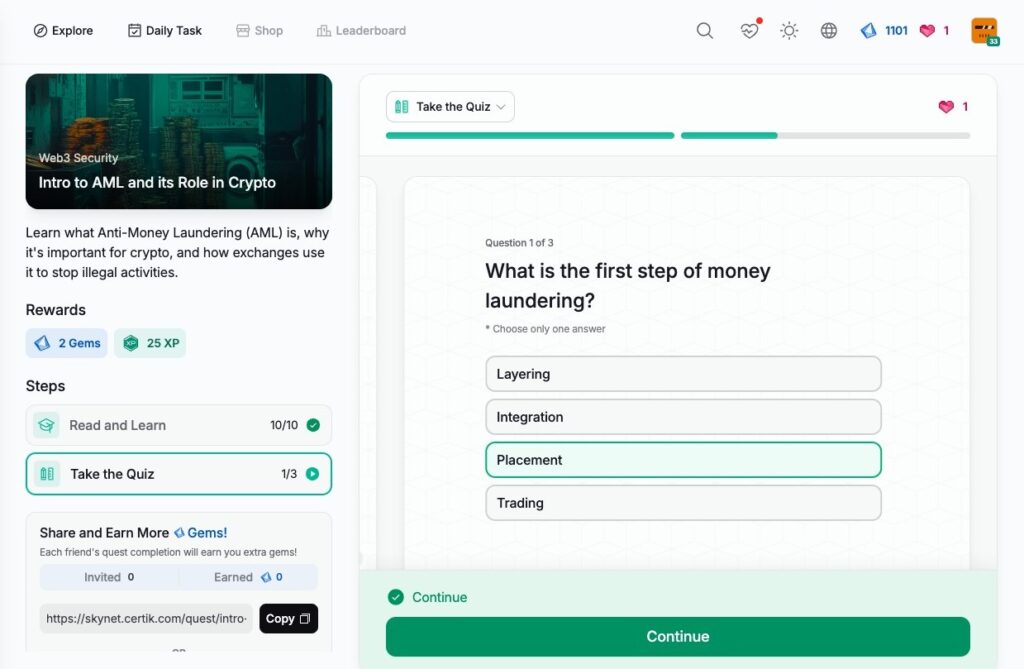
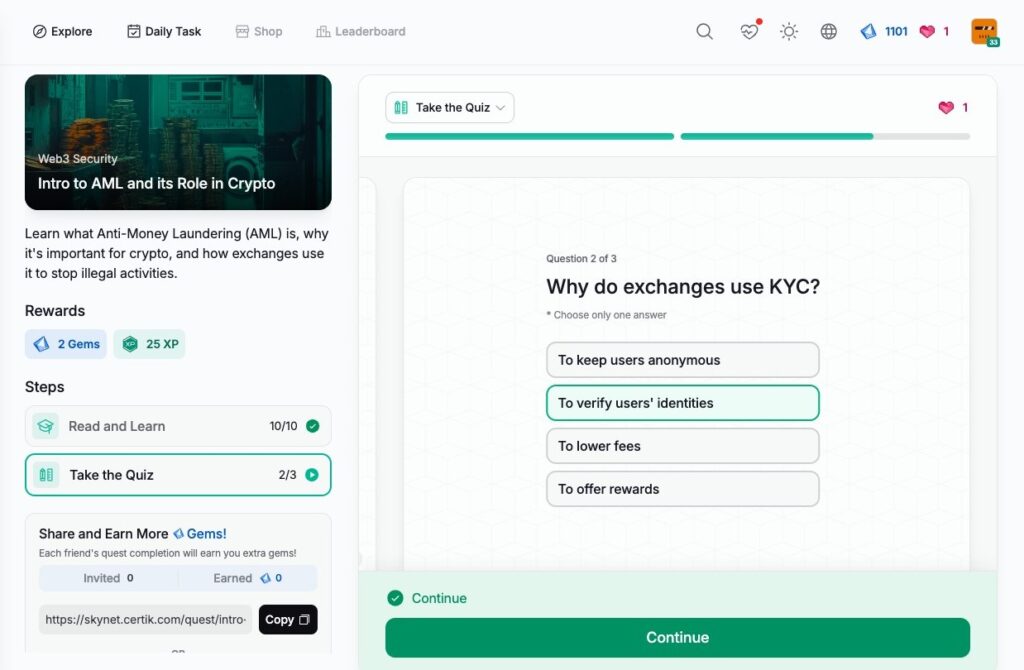
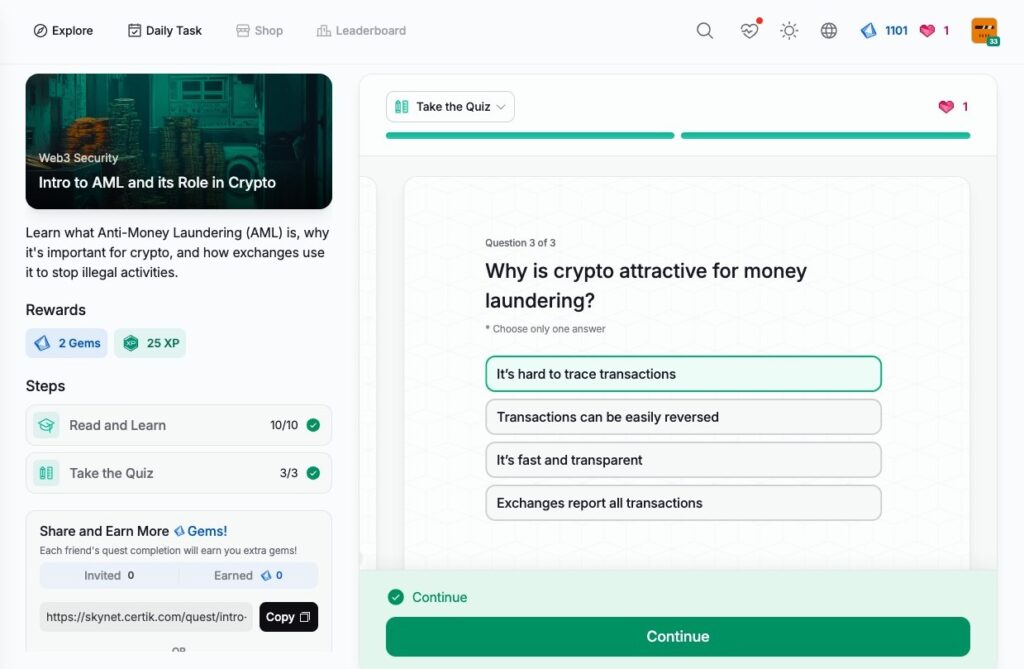
Intro to AML and its Role in Crypto
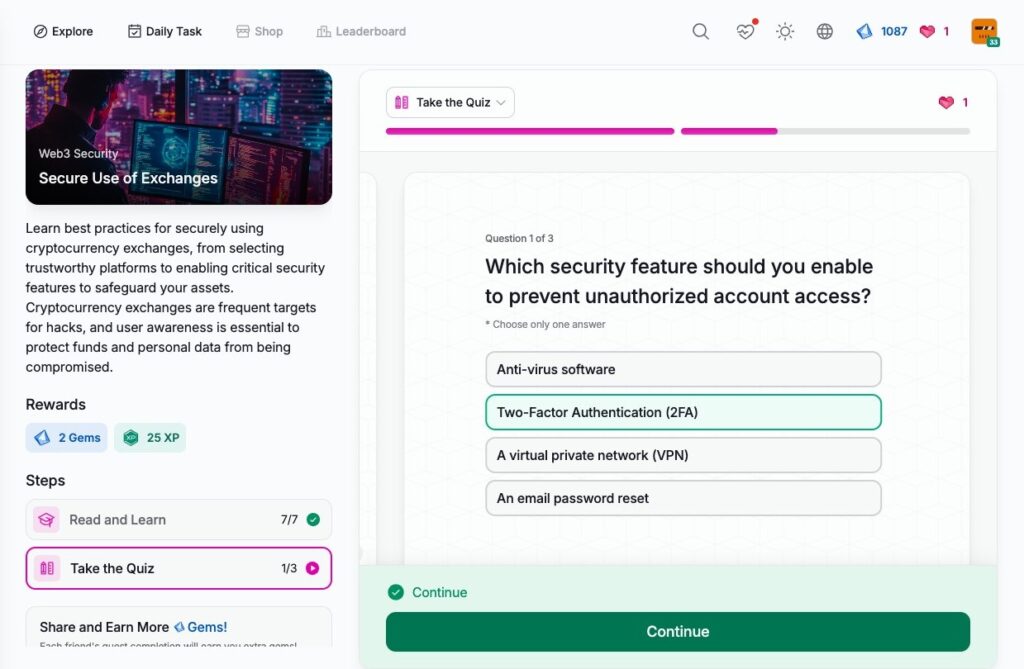
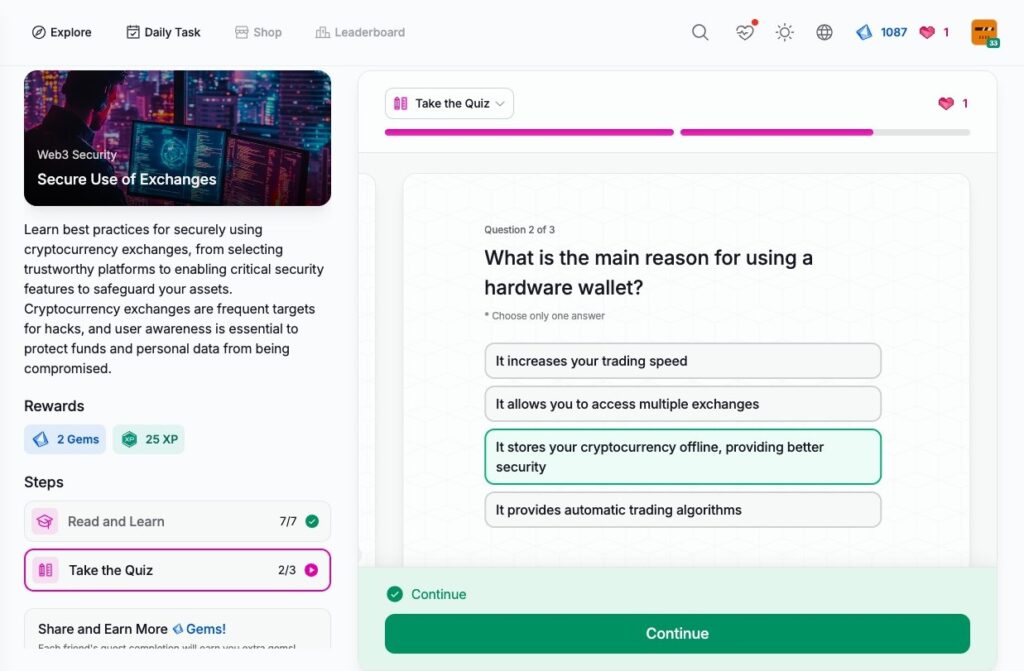
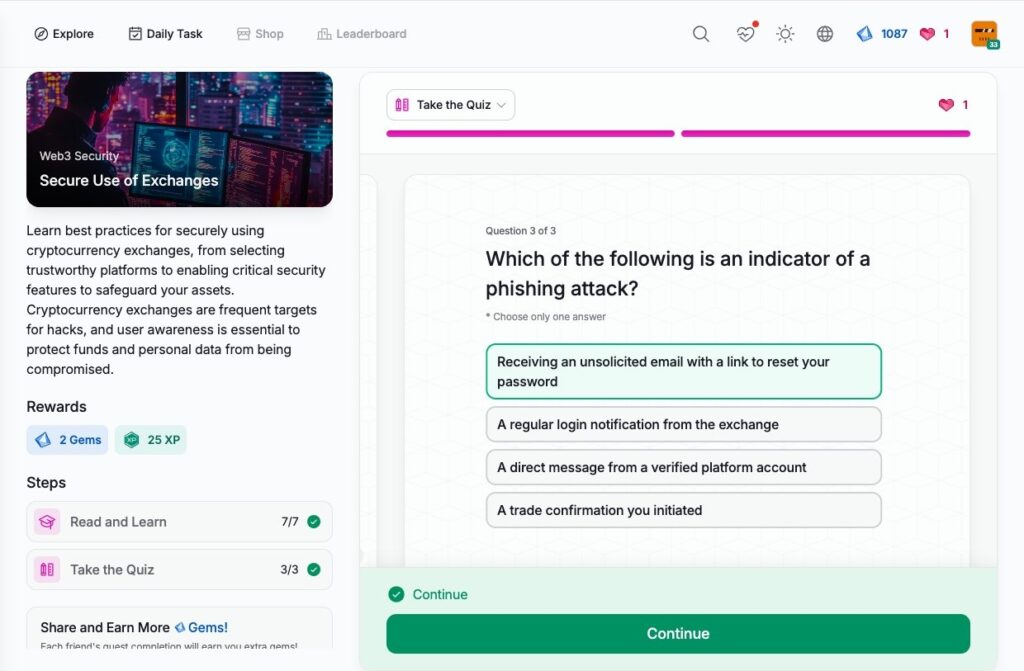
Secure Use of Exchanges
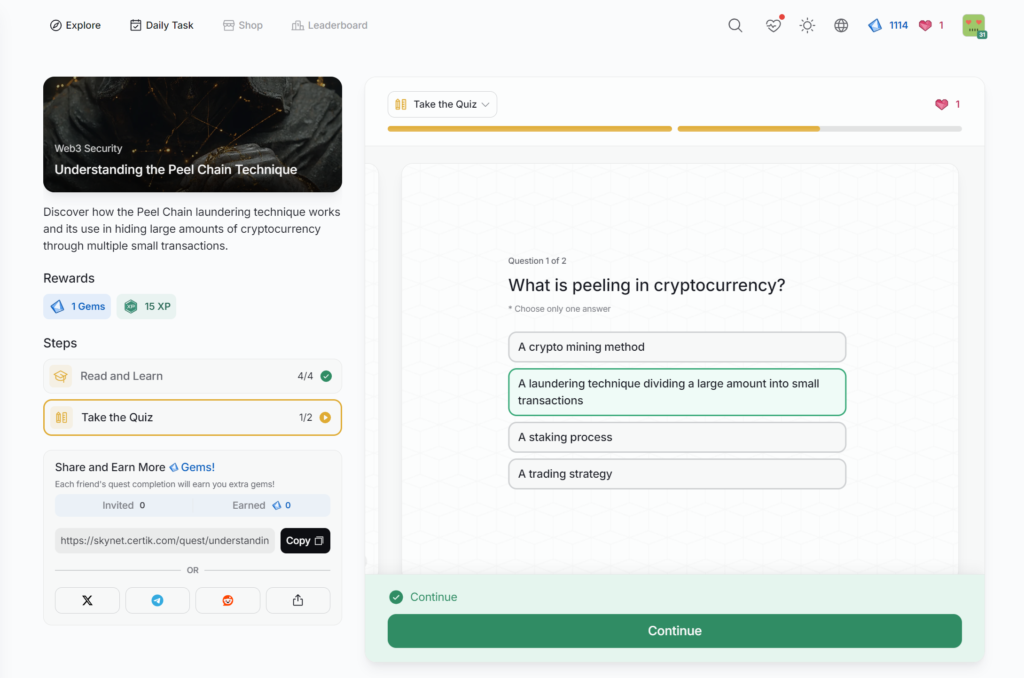
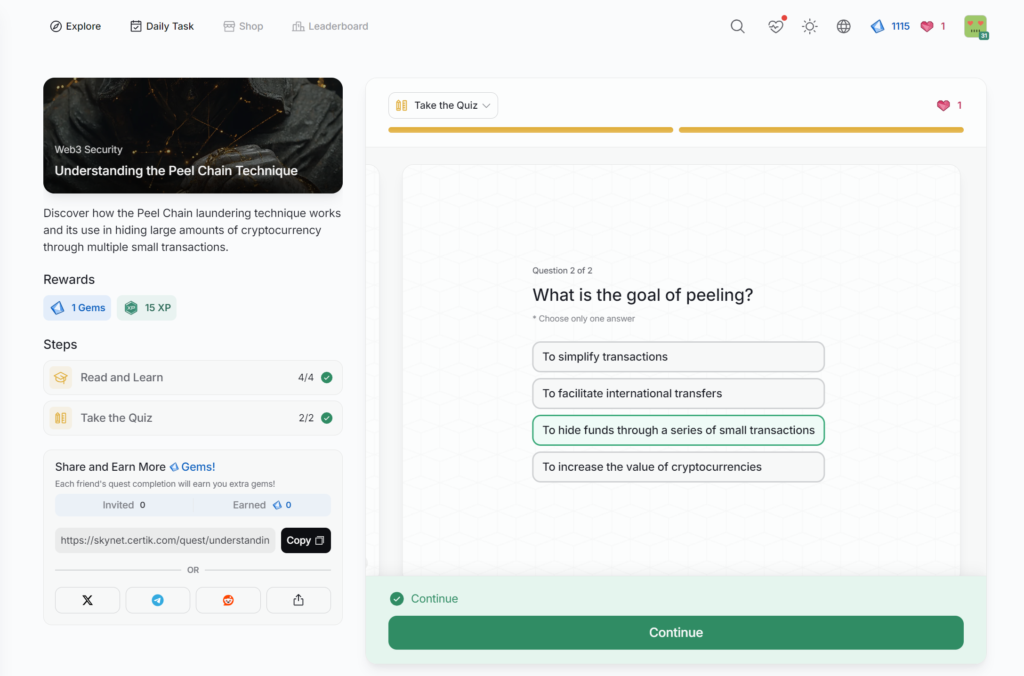
Understanding the Peel Chain Technique
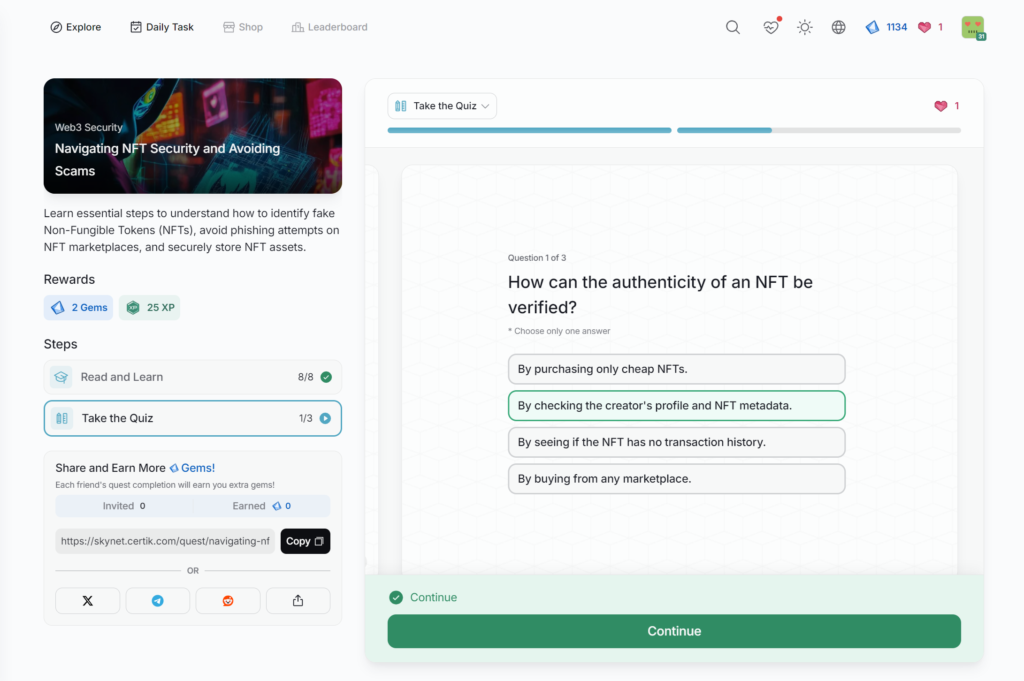
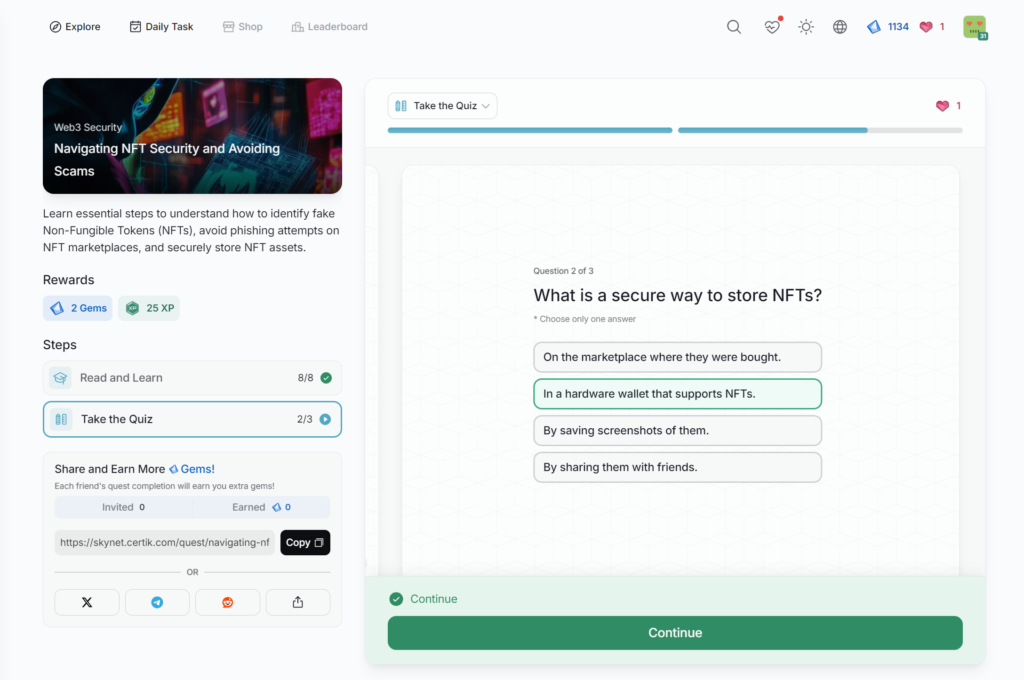
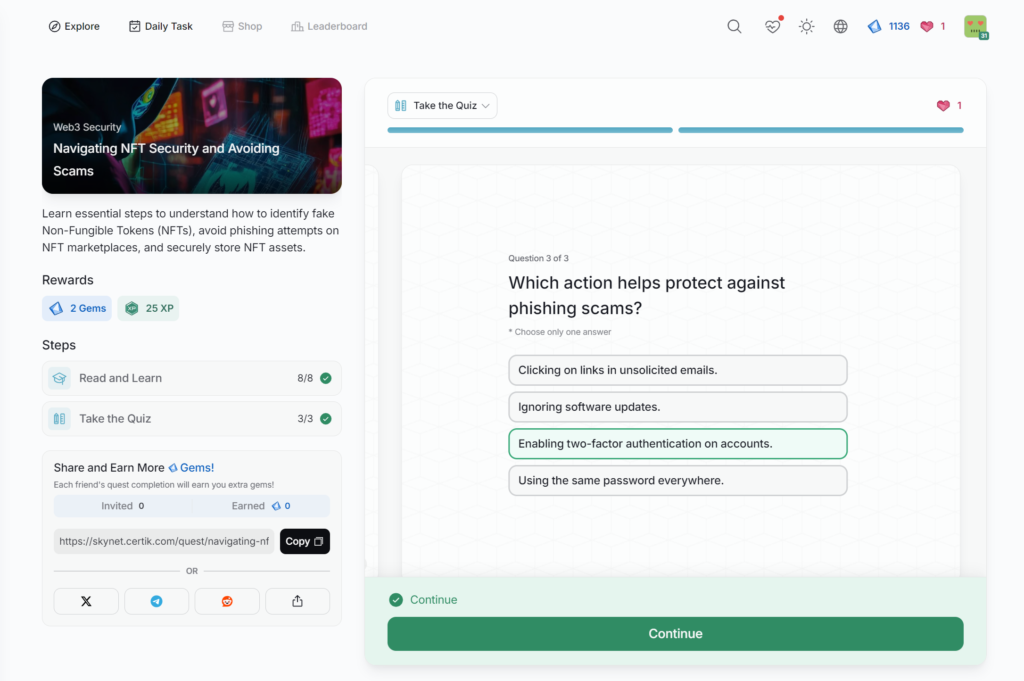
Navigating NFT Security and Avoiding Scams
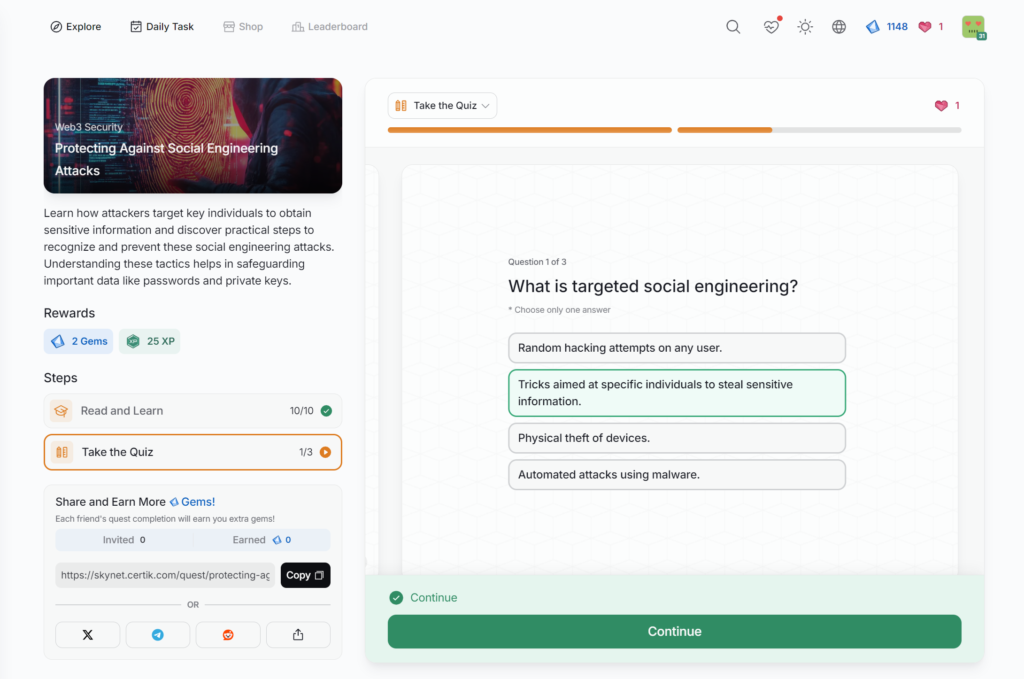
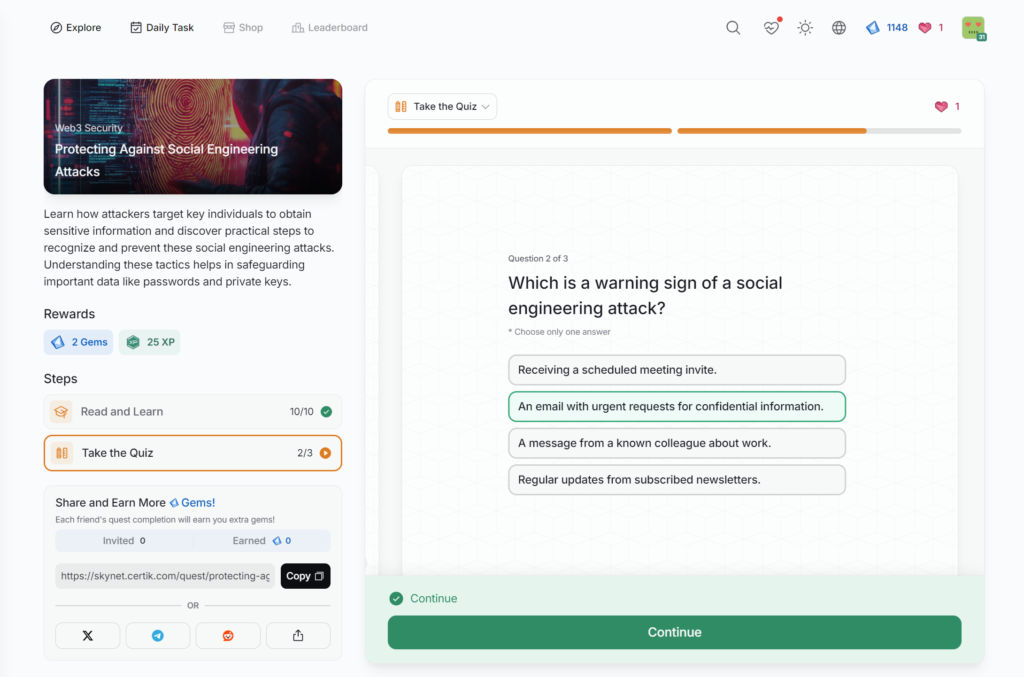
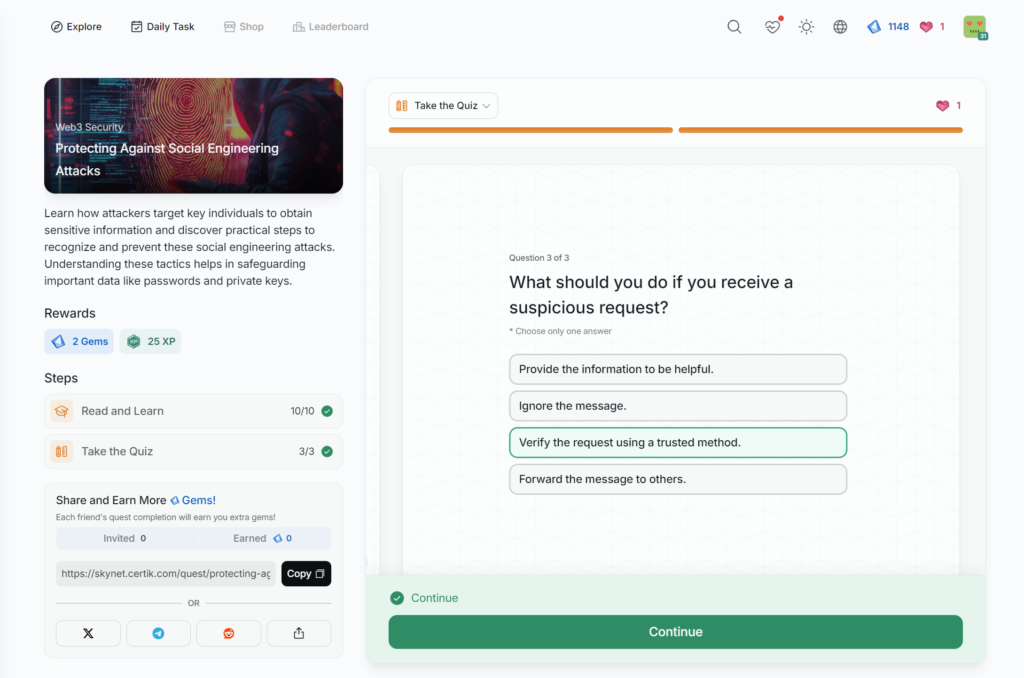
Protecting Against Social Engineering Attacks
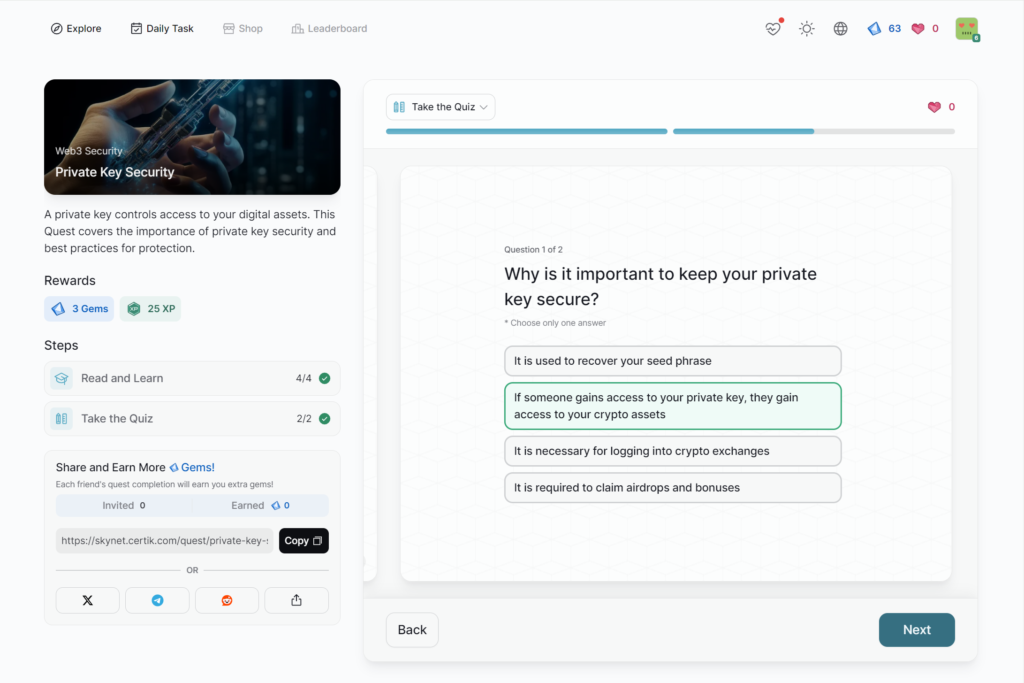
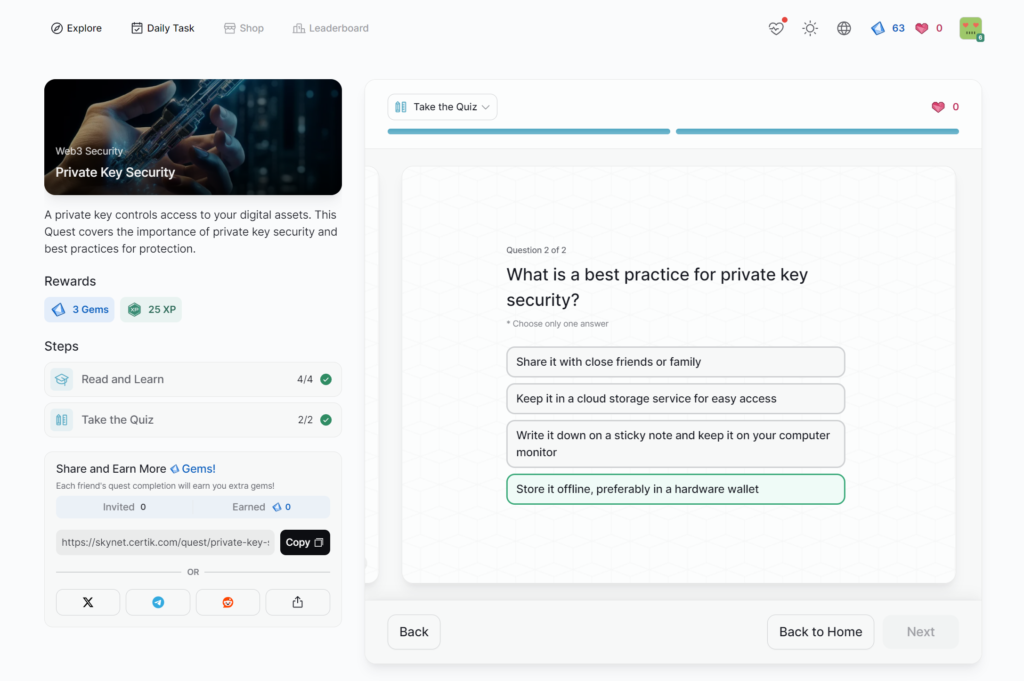
Private Key Security
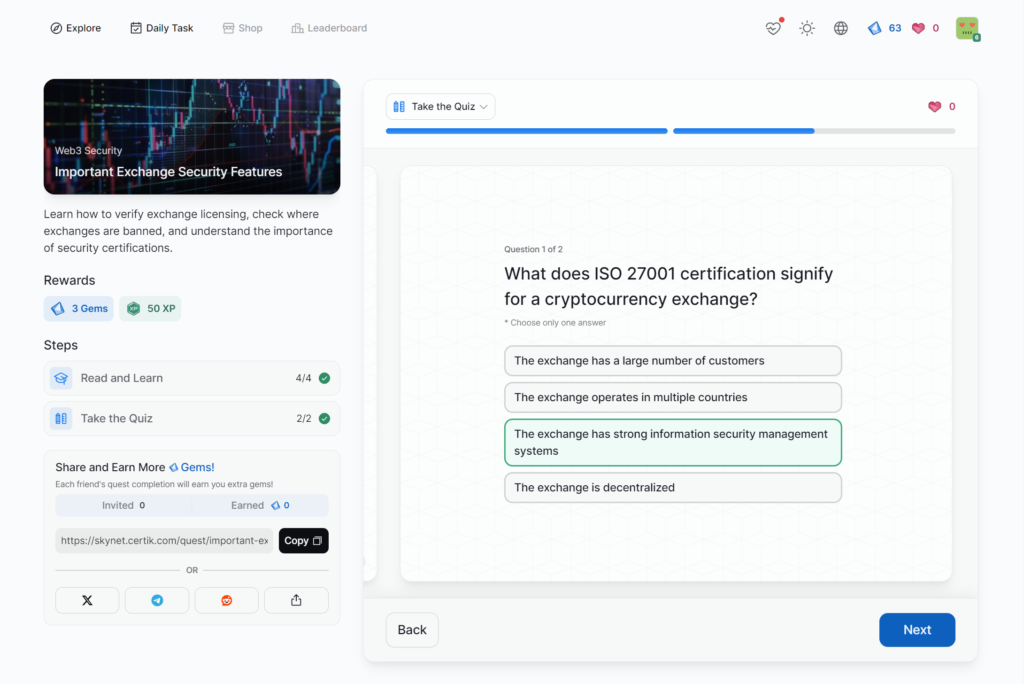
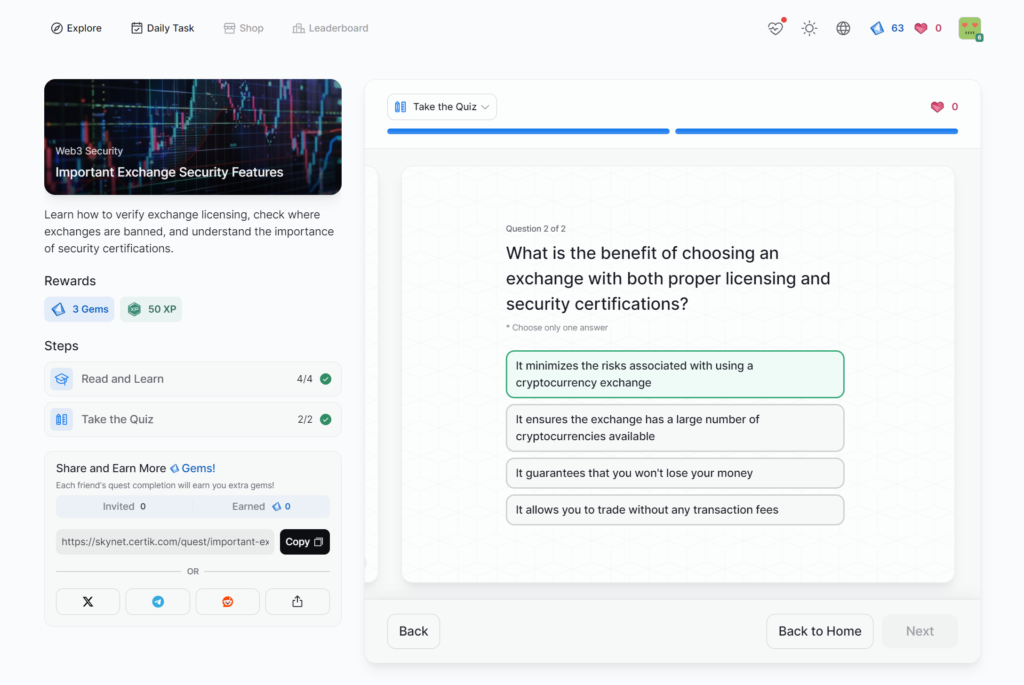
Important Exchange Security Features
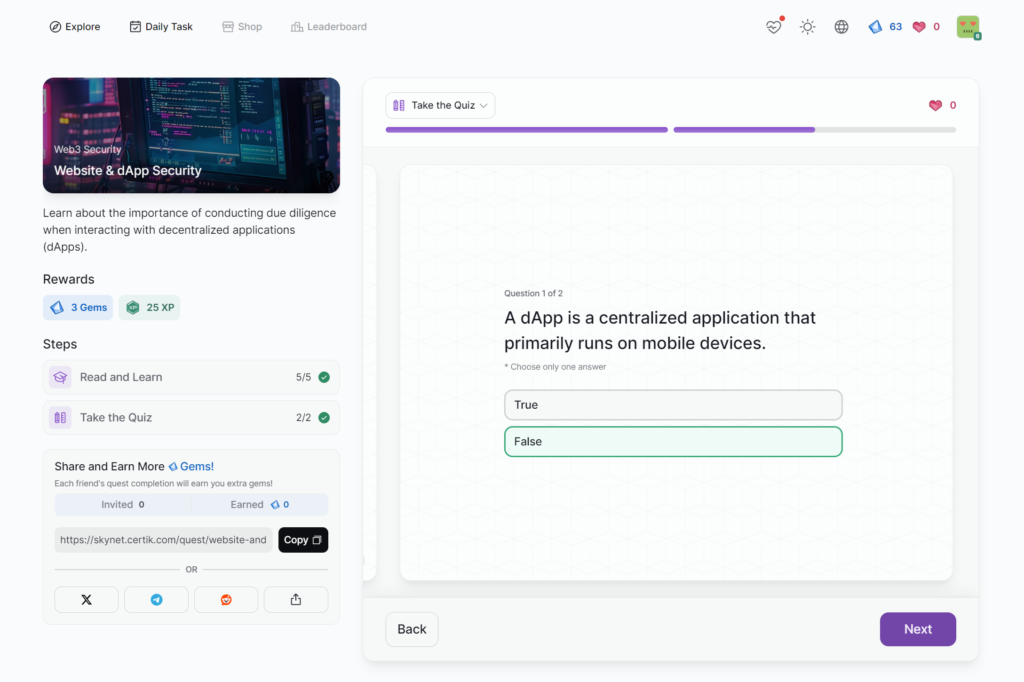
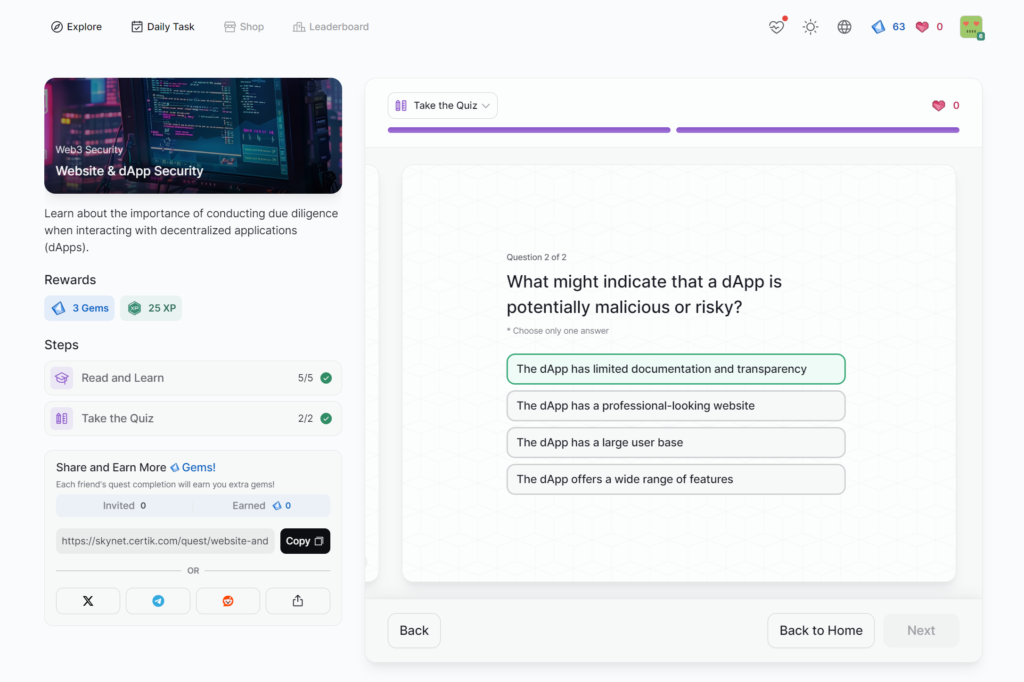
Website & dApp Security
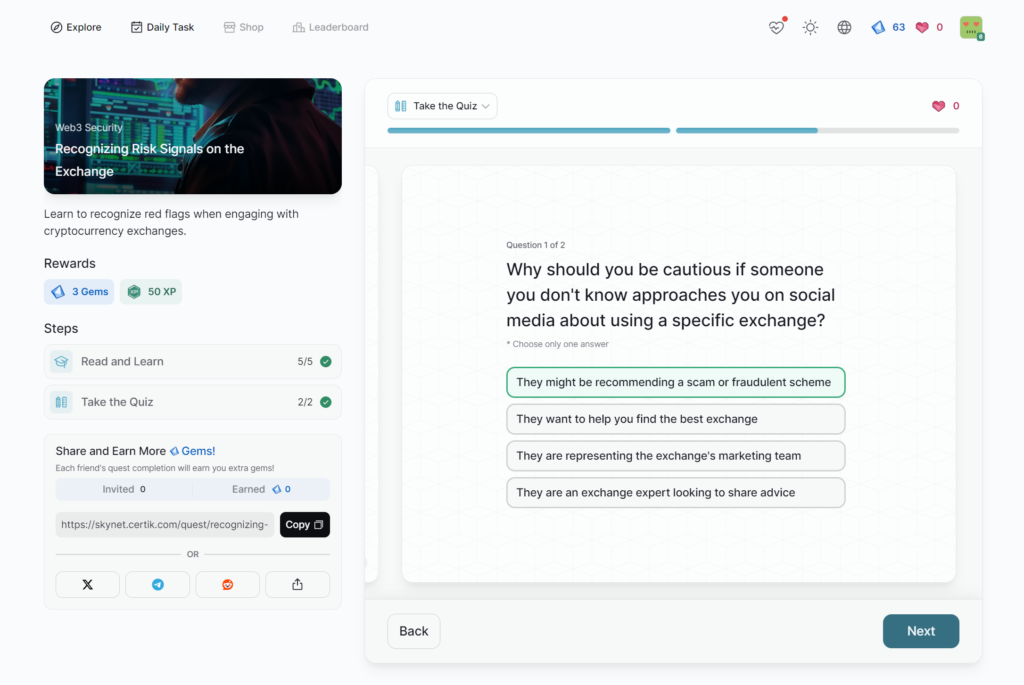
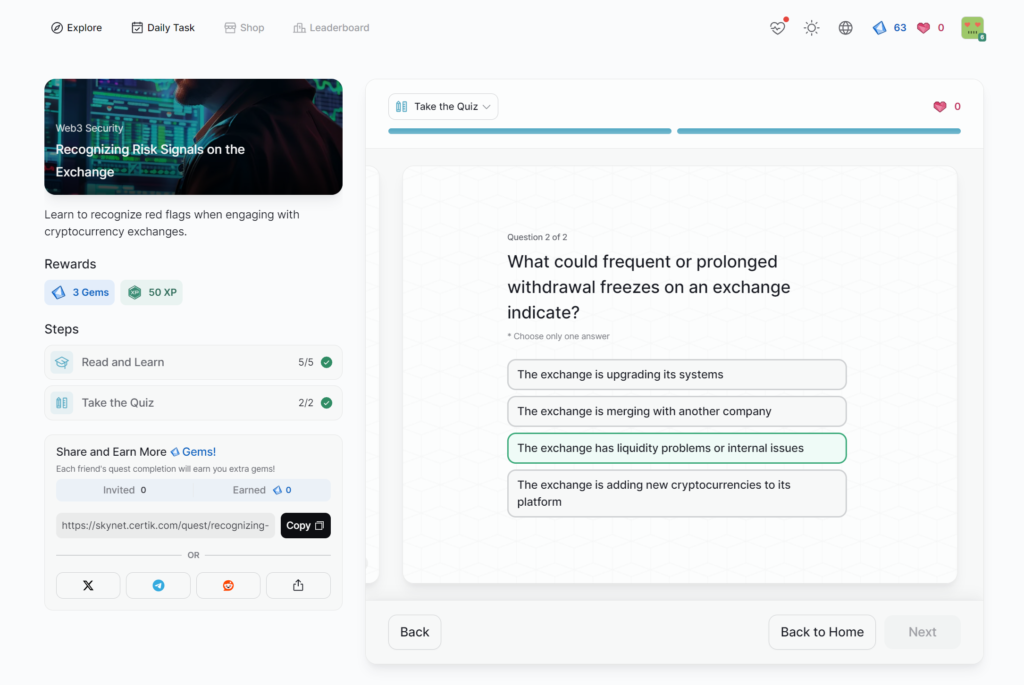
Recognizing Risk Signals on the Exchange
Proof of Reserve
Choosing a Secure Exchange
Introduction to Wallet Security
Losses Related to Private Key Compromises
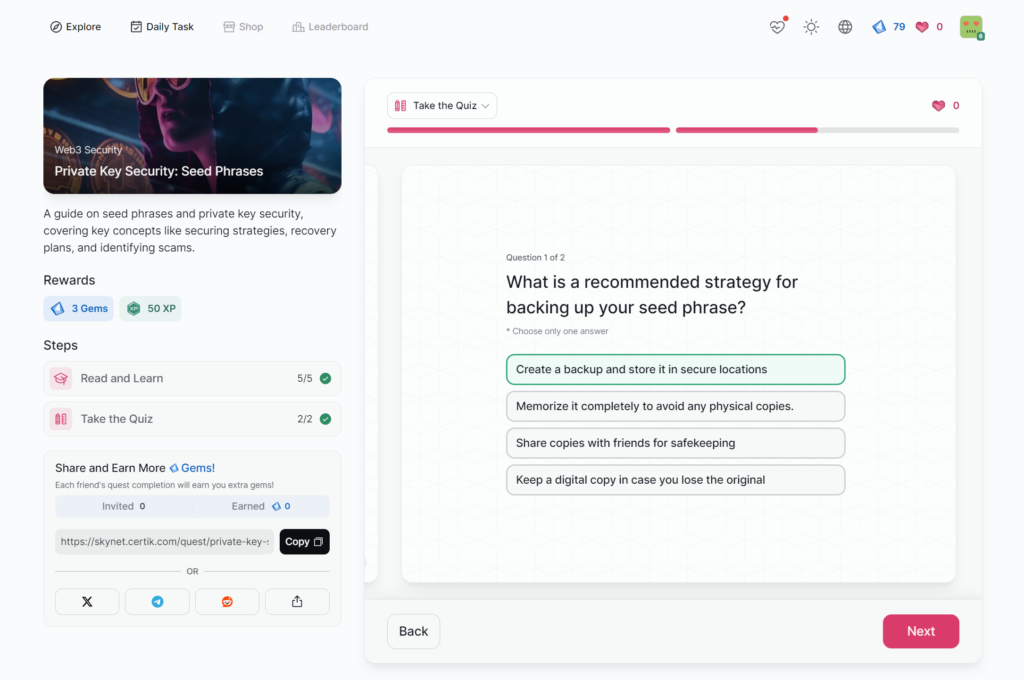
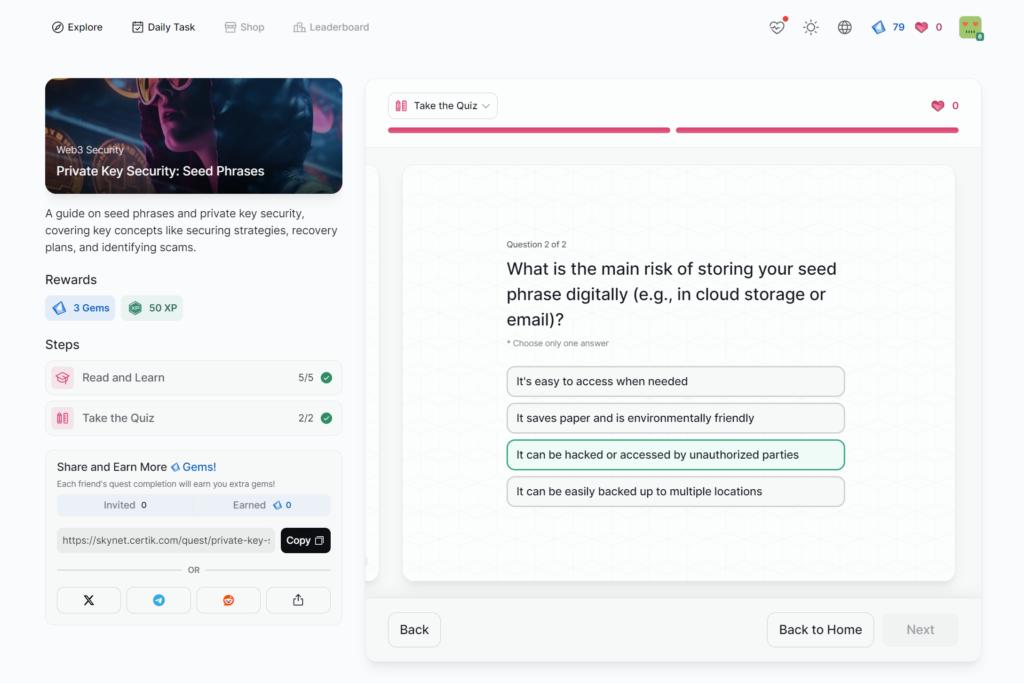
Private Key Security: Seed Phrases
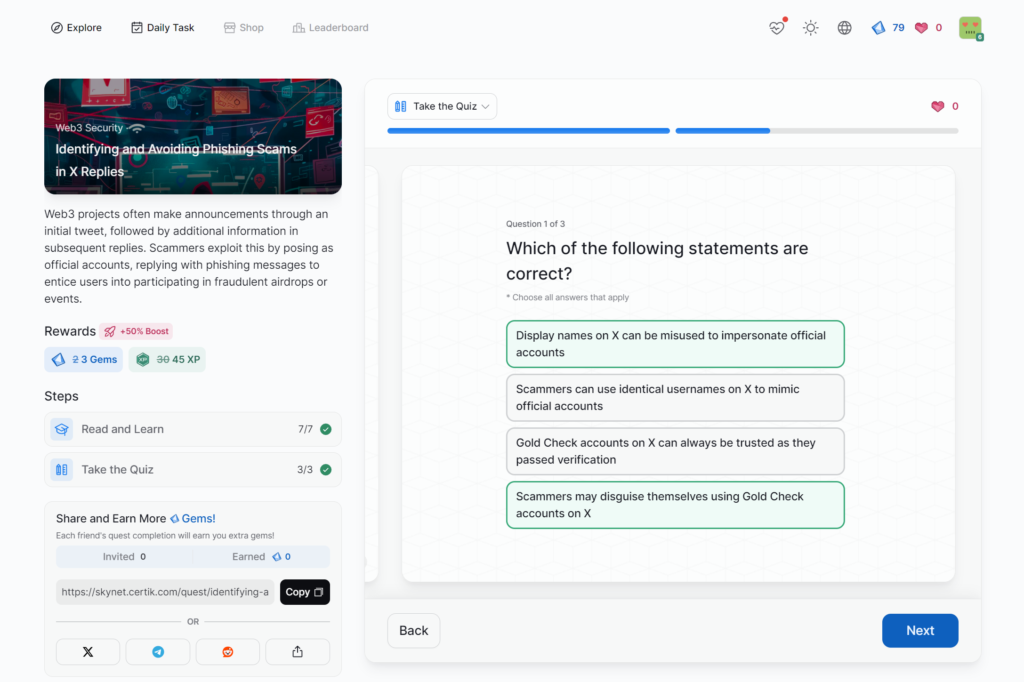
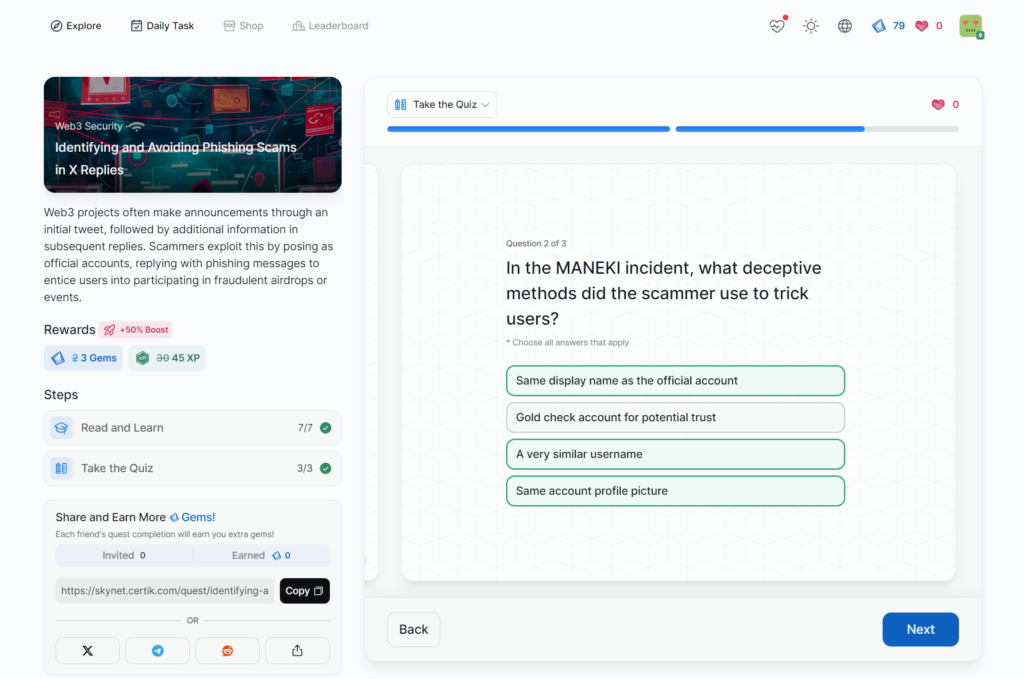
Identifying and Avoiding Phishing Scams in X Replies
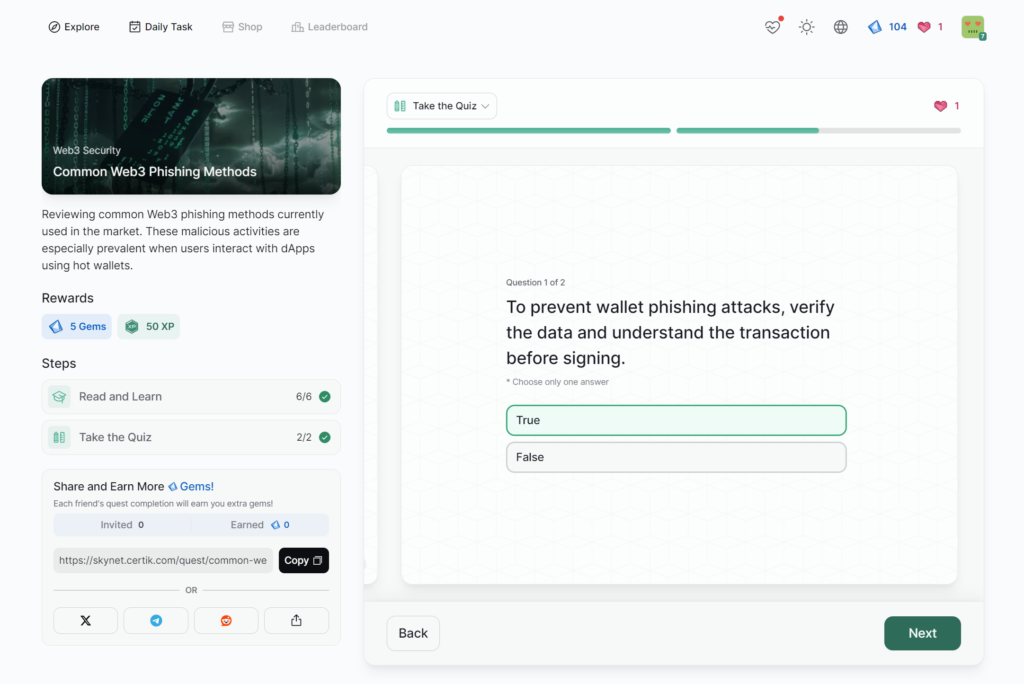
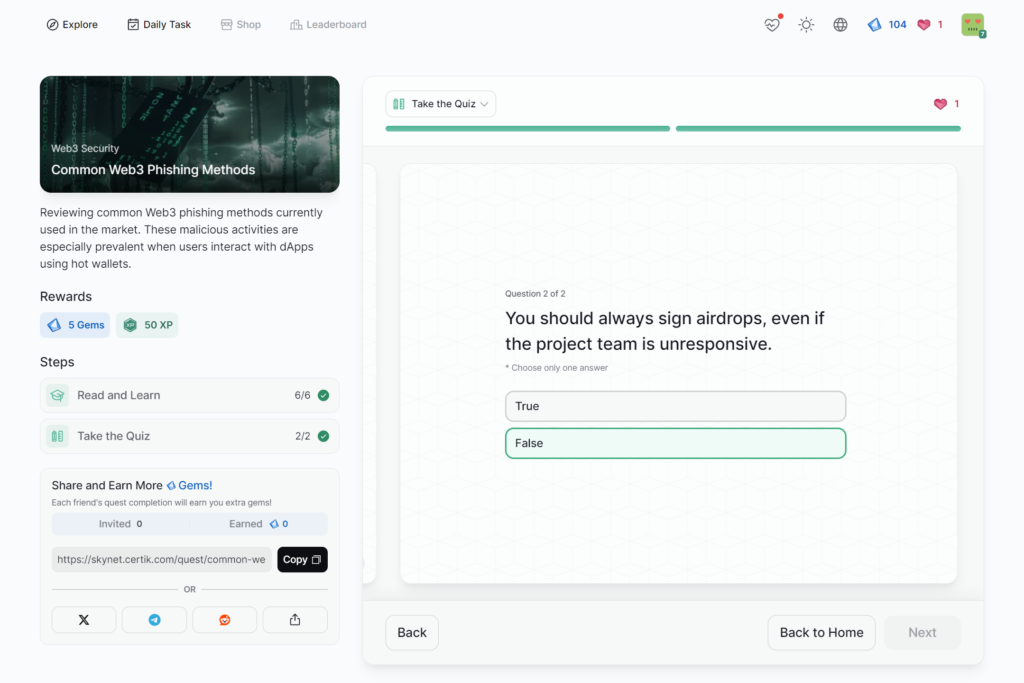
Common Web3 Phishing Methods
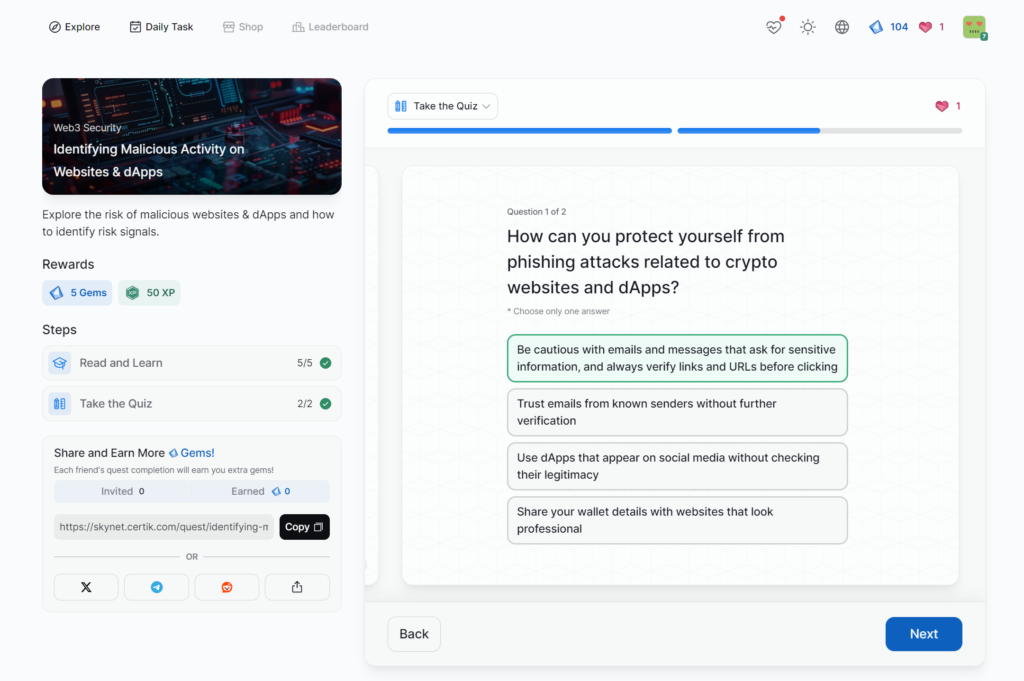
Identifying Malicious Activity on Websites & dApps
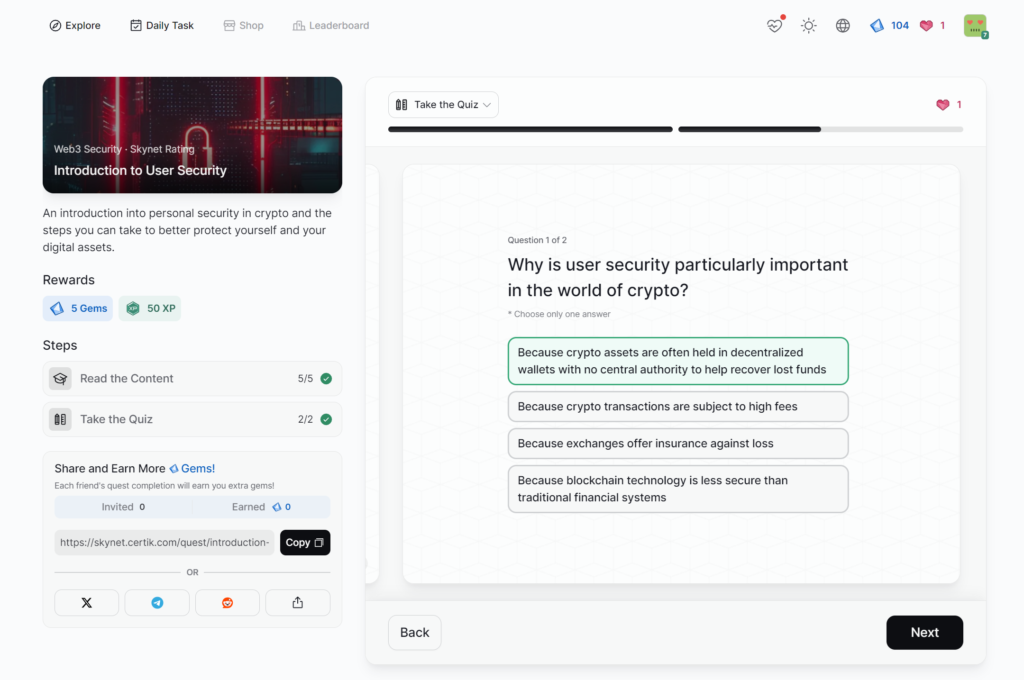
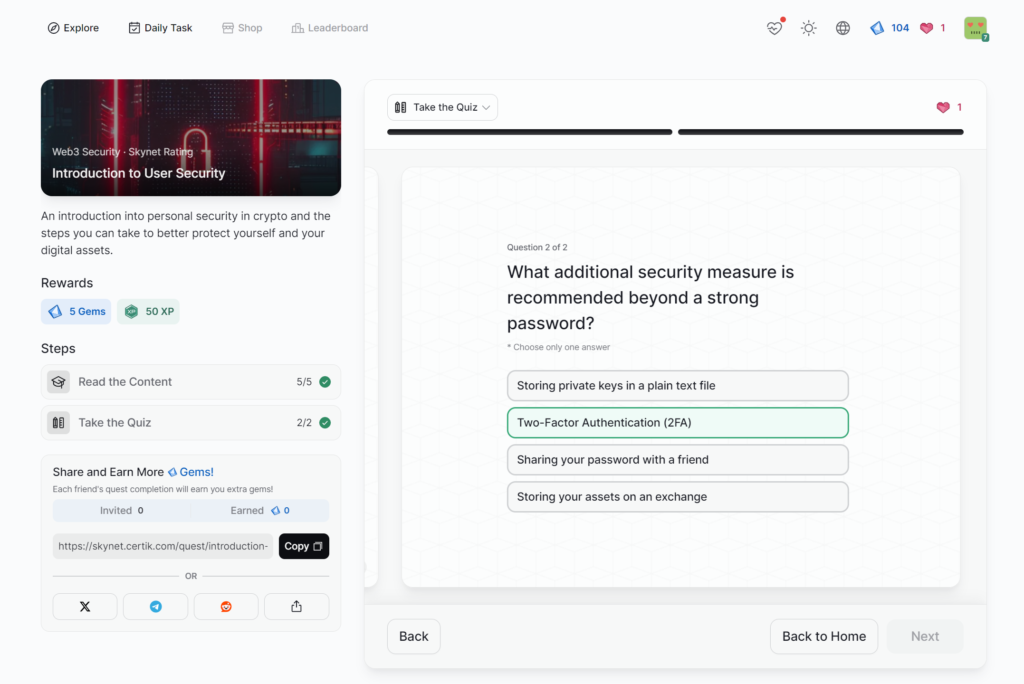
Introduction to User Security
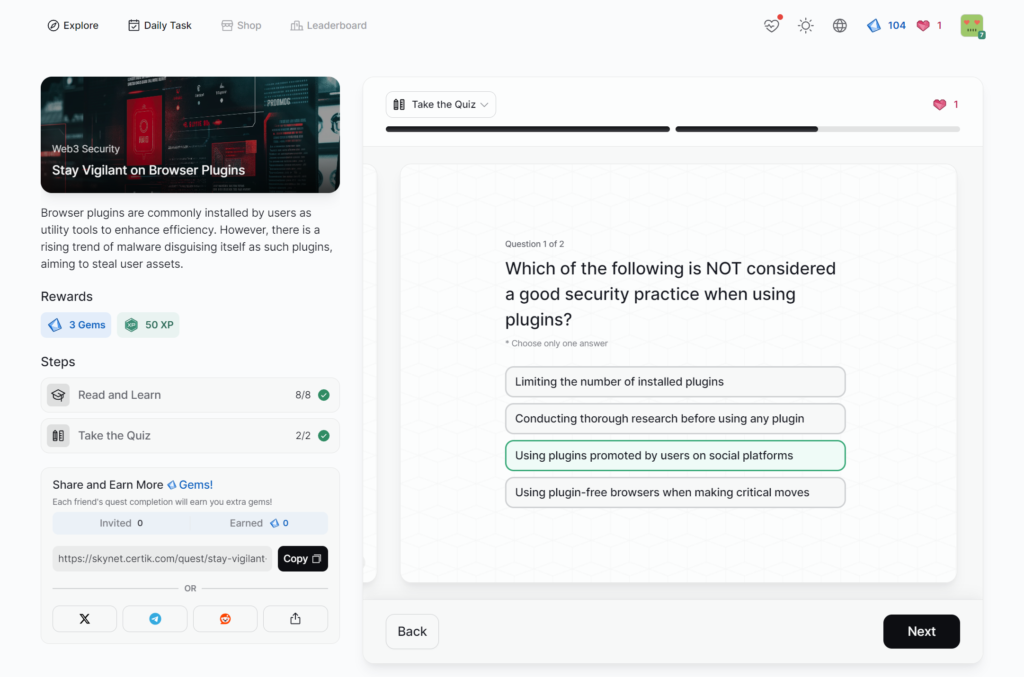
Stay Vigilant on Browser Plugins
Best Practices for Wallet Security
Importance of Bug Bounty Programs in Web3
Intro to Crypto Drainers
Intro to Airdrop Scams
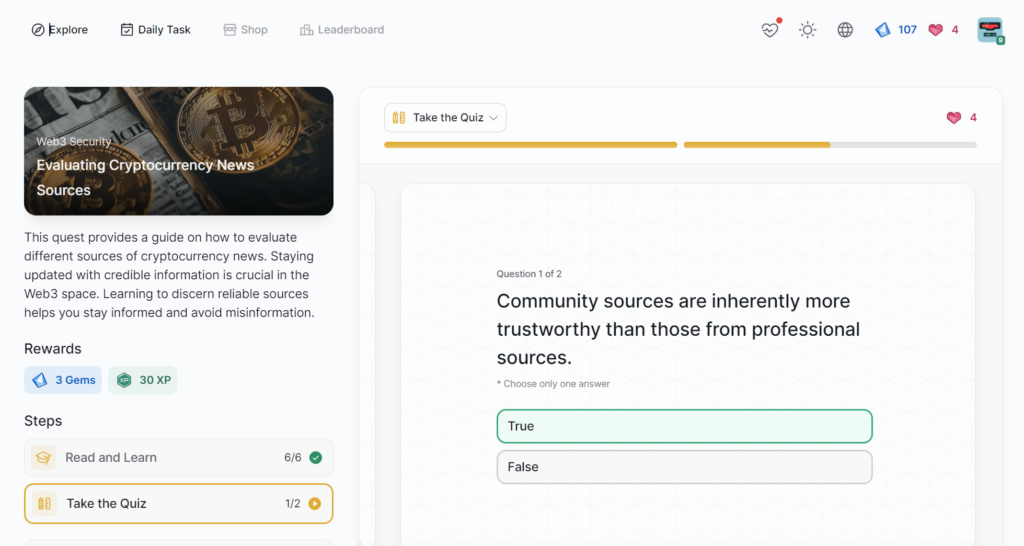
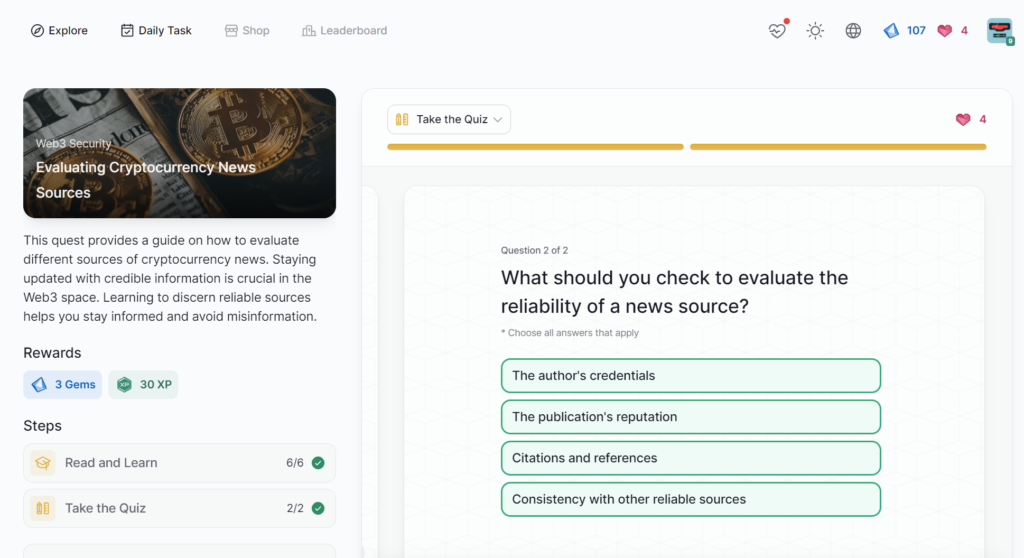
Evaluating Cryptocurrency News Sources
Hackers Infiltrating Crypto Job Boards
Setting Up a Security War Room
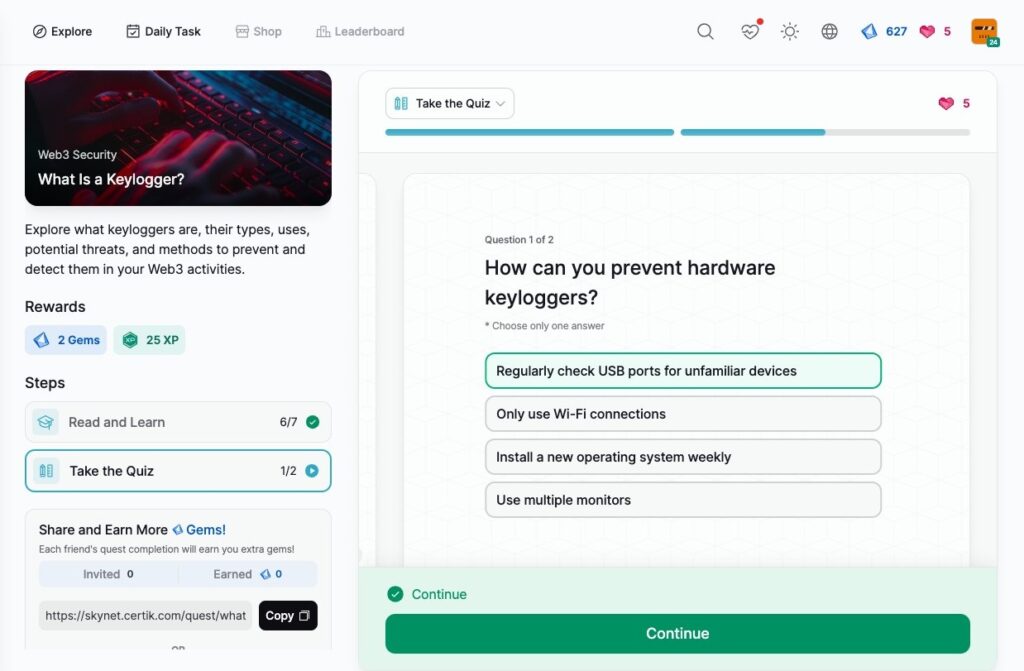
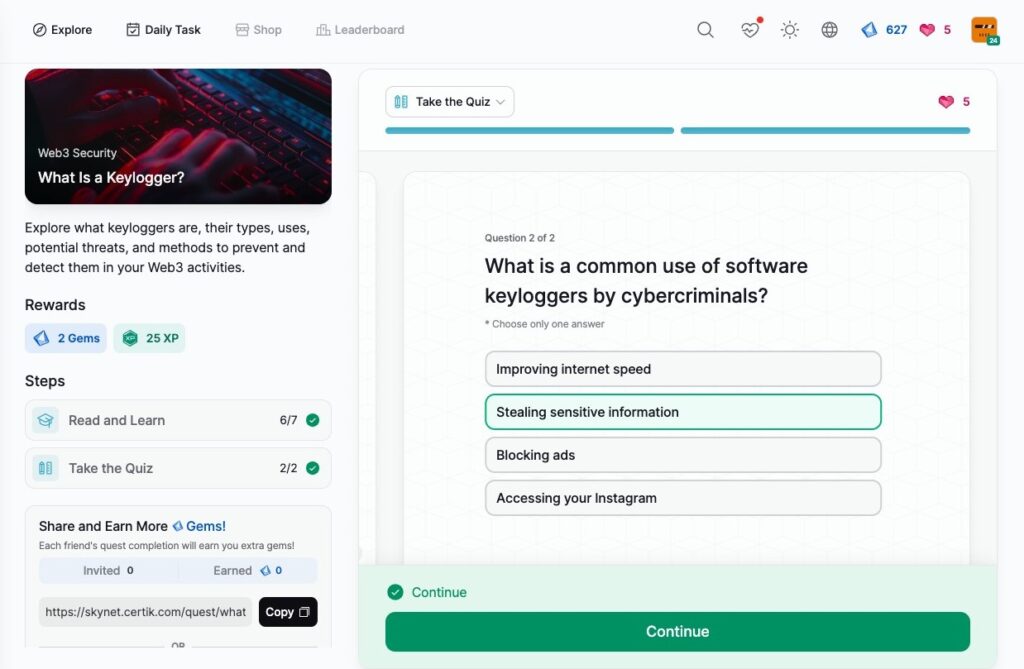
What Is a Keylogger?
Understanding and Preventing Sybil Attacks
Cold Wallets
How to Create and Maintain Secure Passwords
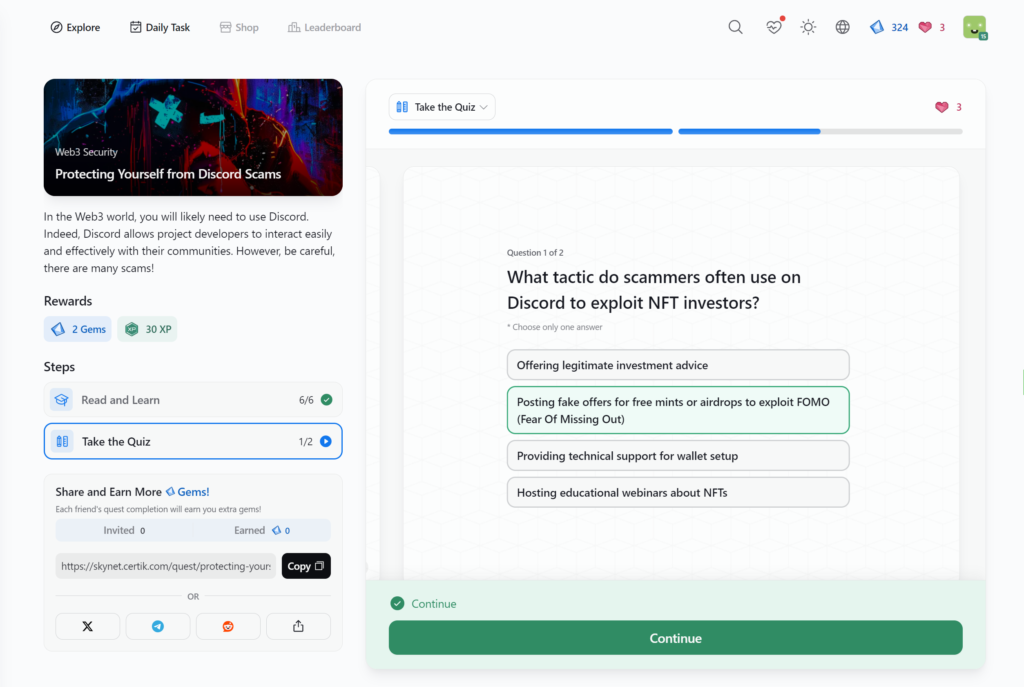
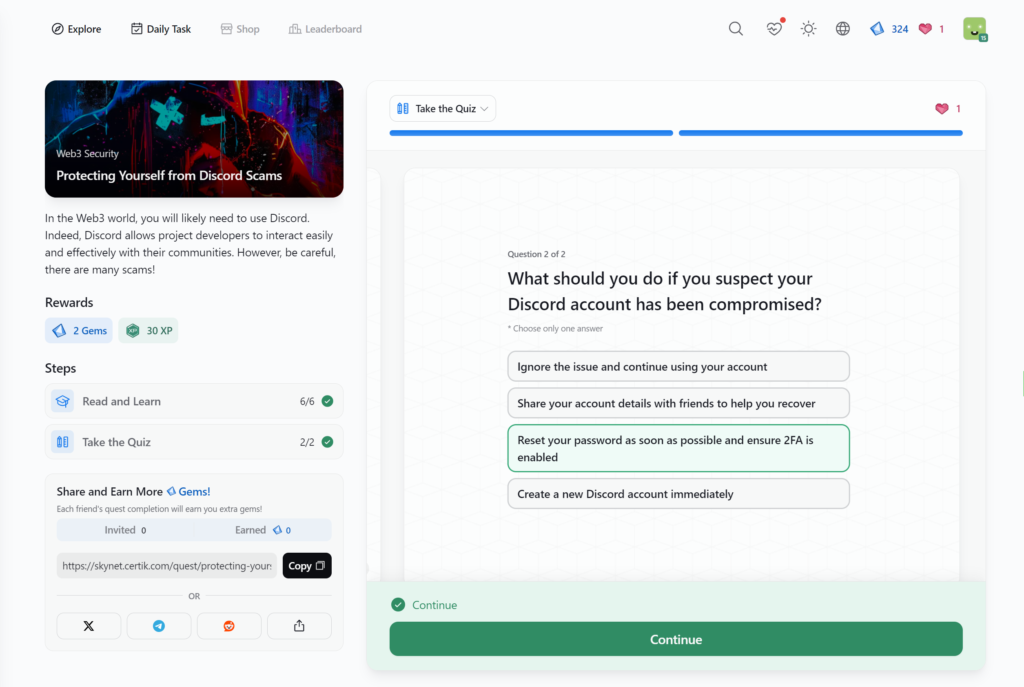
Protecting Yourself from Discord Scams
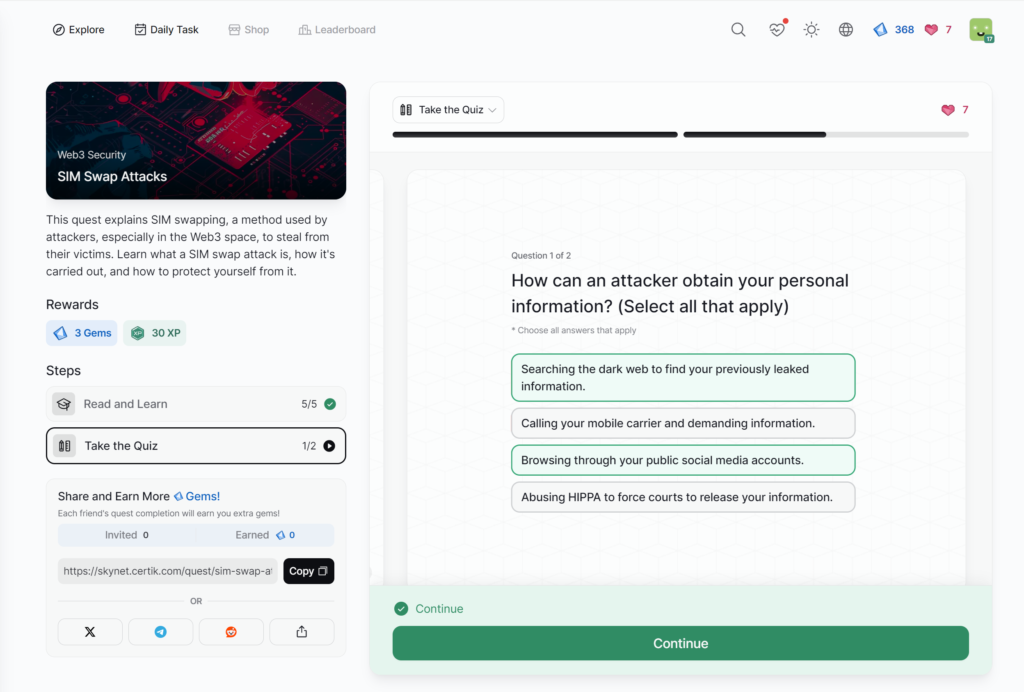
SIM Swap Attacks
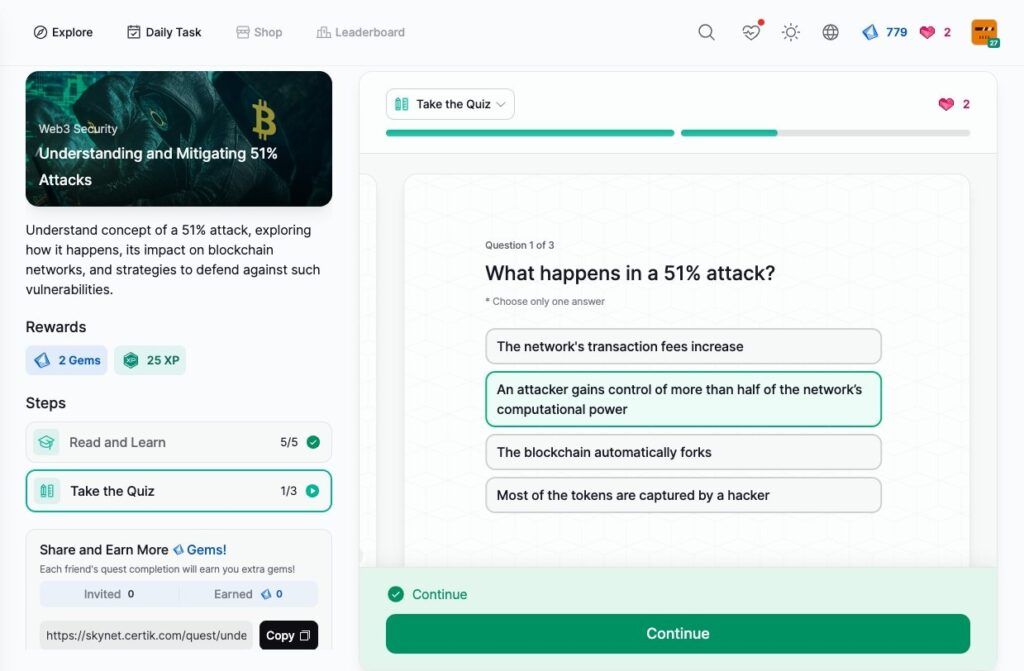
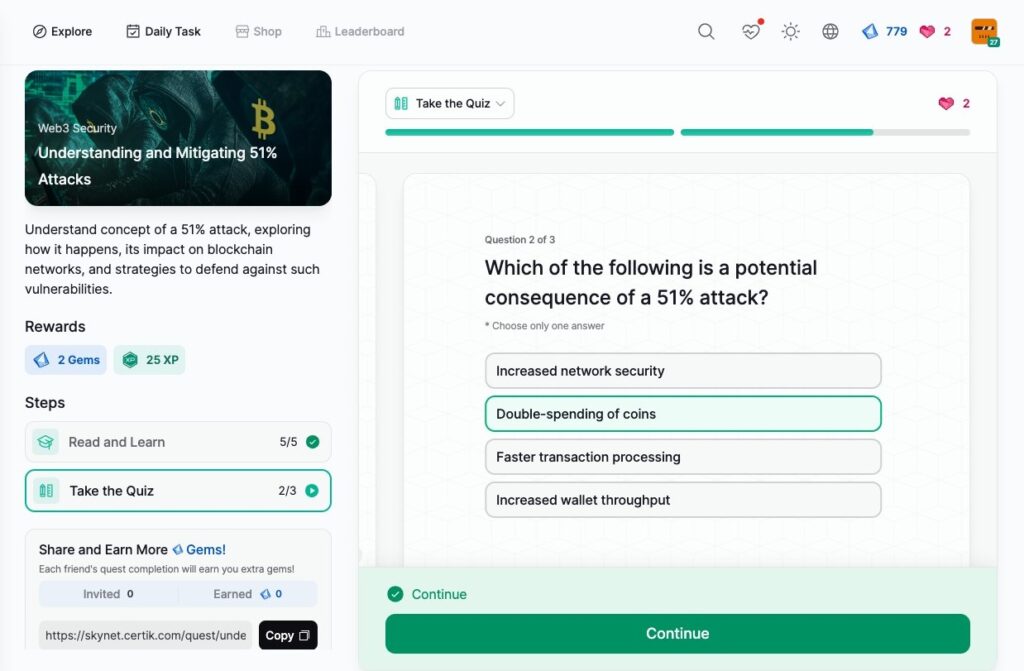
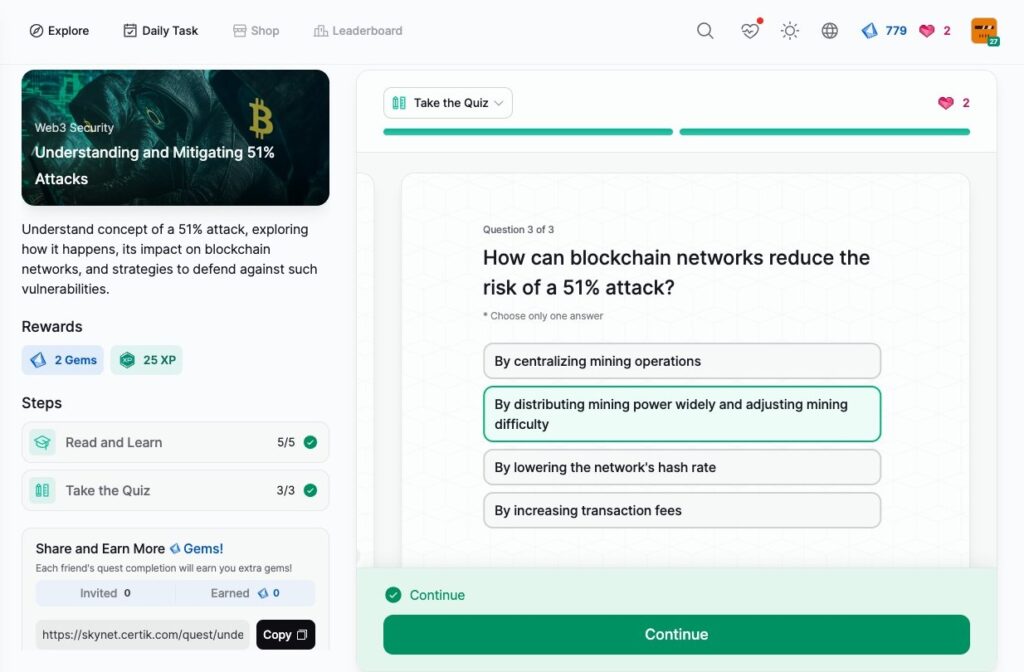
Understanding and Mitigating 51% Attacks
Protecting Your PostgreSQL Database from Cryptojacking
SOC 2 Compliance for Crypto Companies
Understanding Soft Rug vs. Hard Rug Pulls
Case Study on Enhancing Security for App Chains
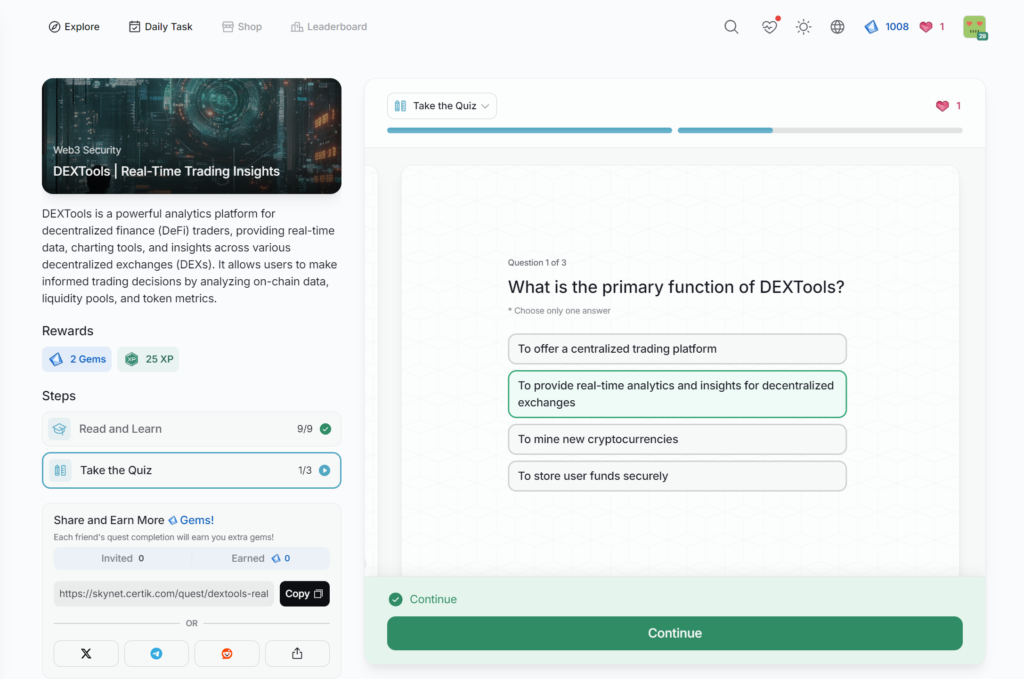
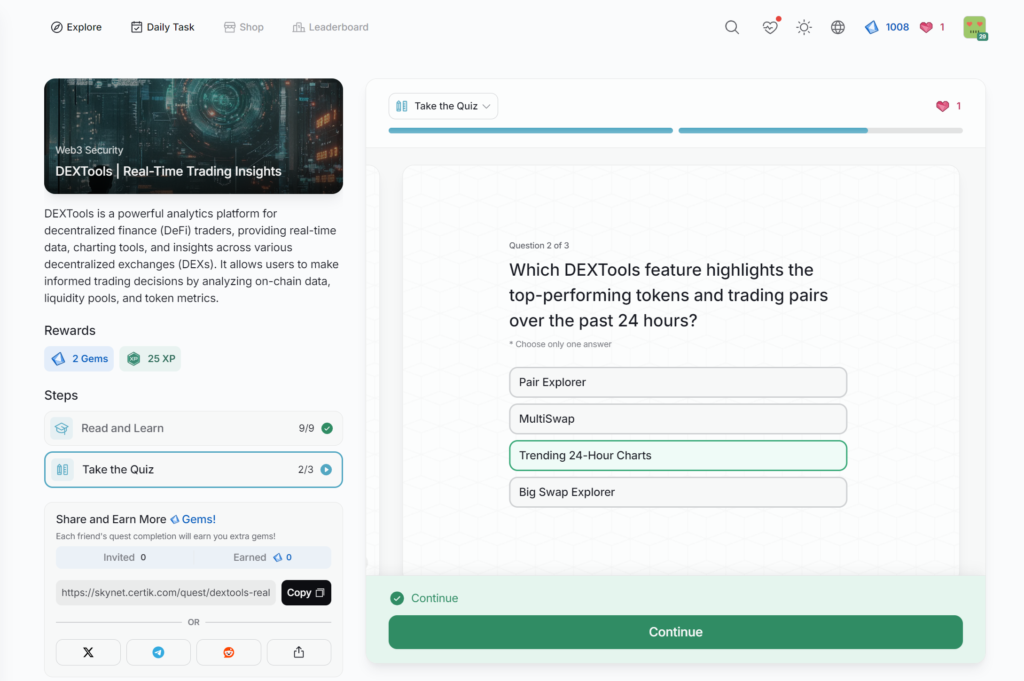
DEXTools | Real-Time Trading Insights
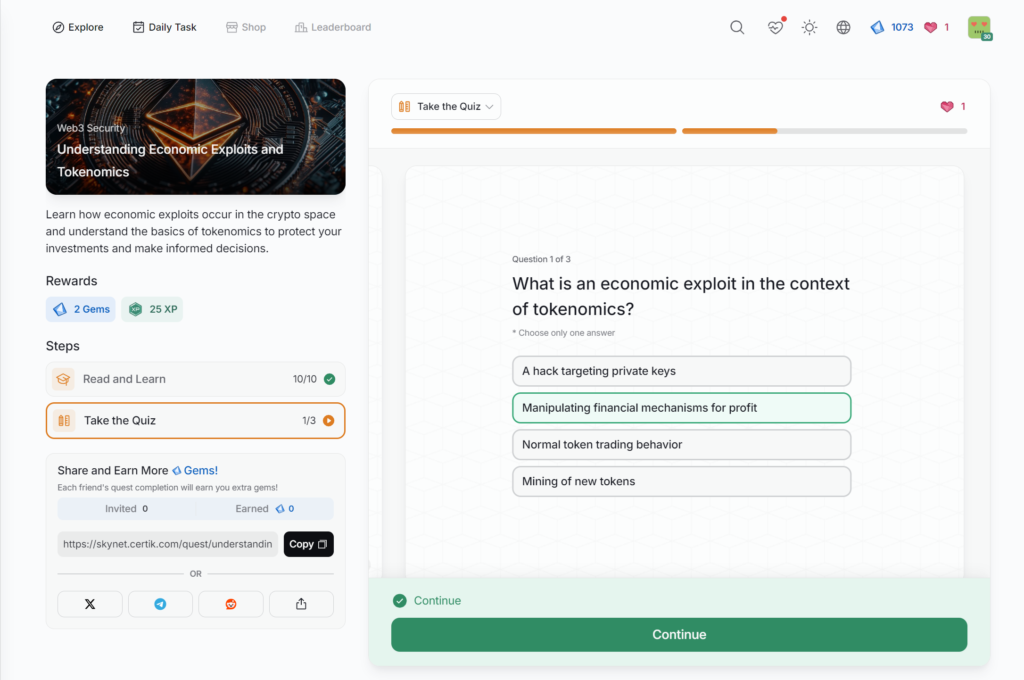
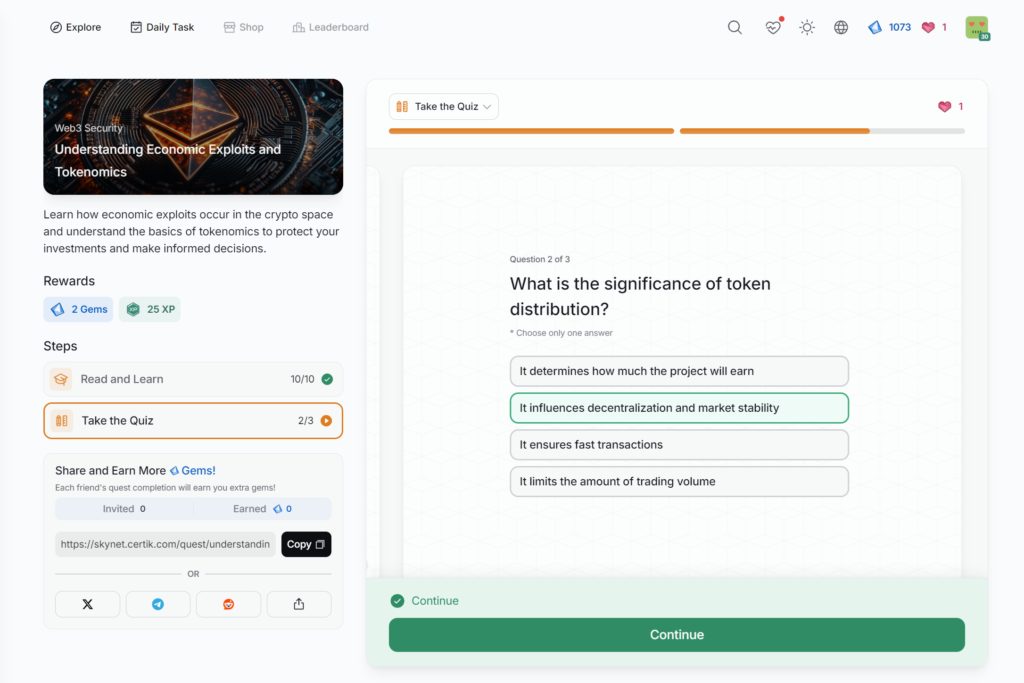
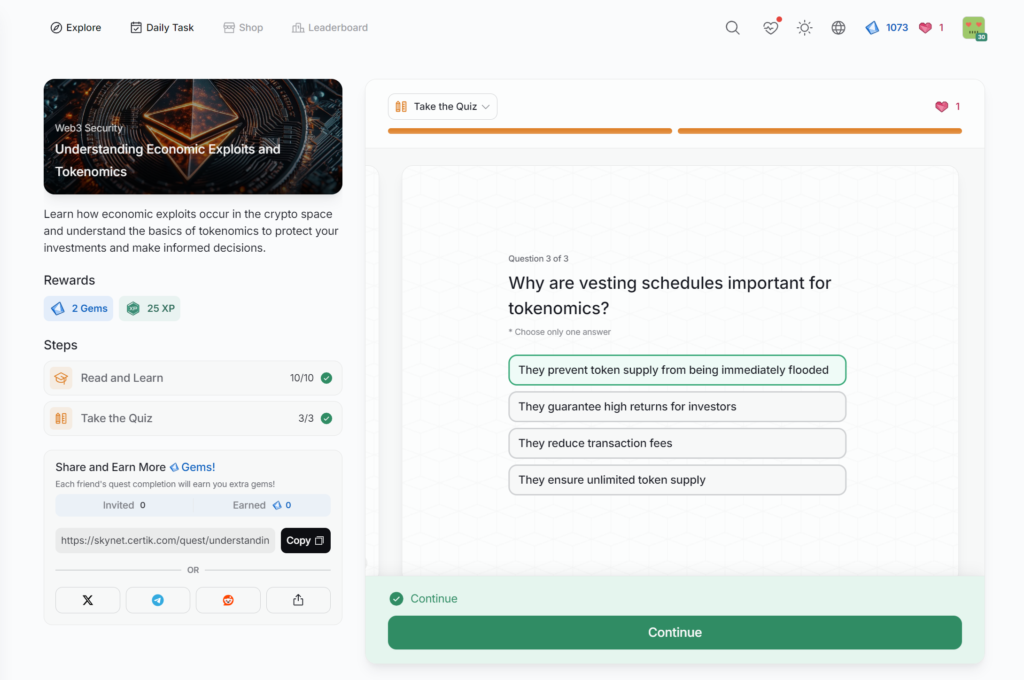
Understanding Economic Exploits and Tokenomics
Intro to AML and its Role in Crypto
Secure Use of Exchanges
Understanding the Peel Chain Technique
Navigating NFT Security and Avoiding Scams
Protecting Against Social Engineering Attacks