- Industry Insights
- User Security
- Security Analysis
- Project Spotlights
- Skynet Platform
- CertiK Highlights
- Web3 Fundamentals
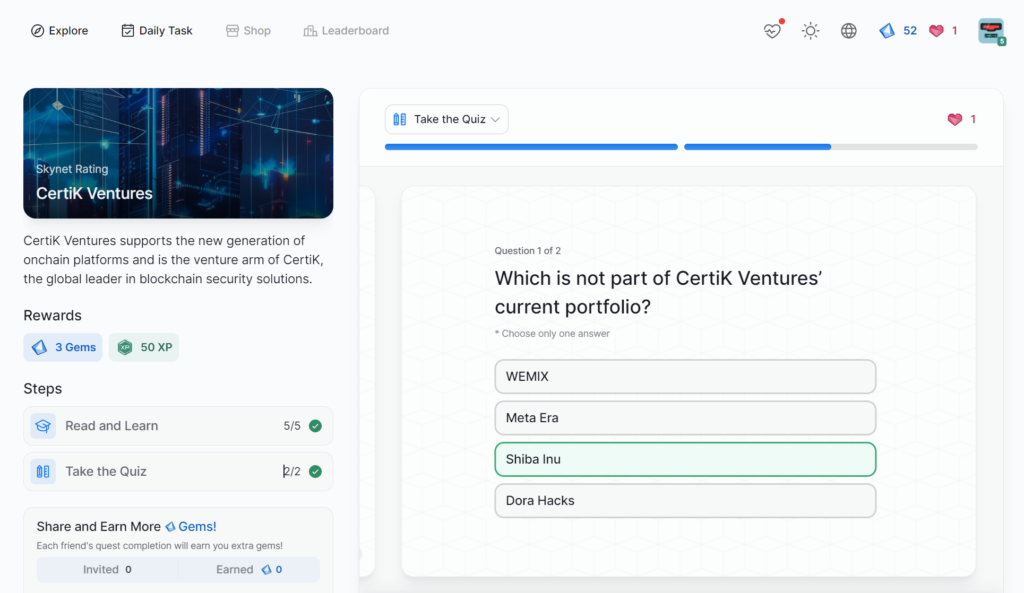
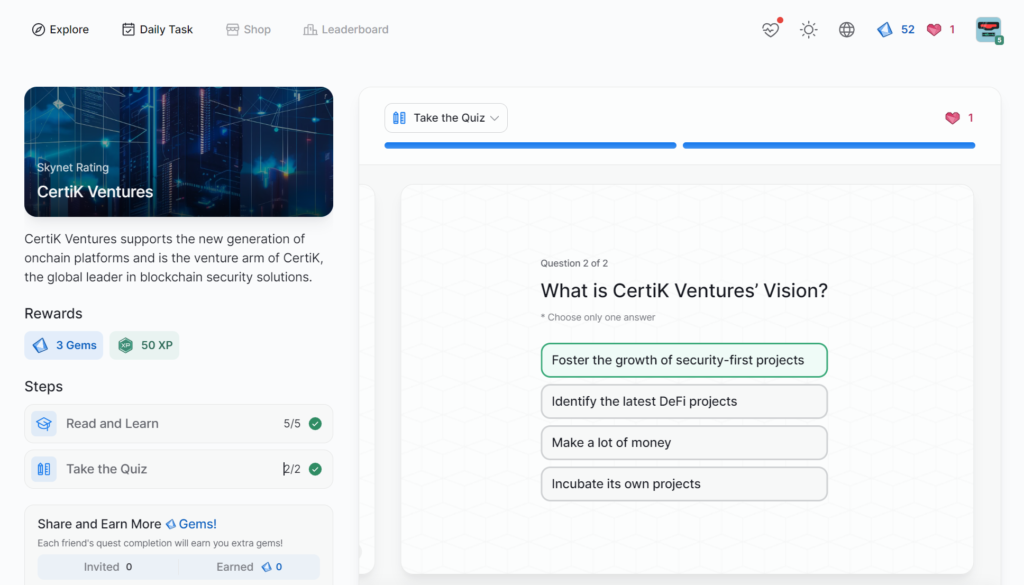
- CertiK Ventures
- Web3 Security with Skynet
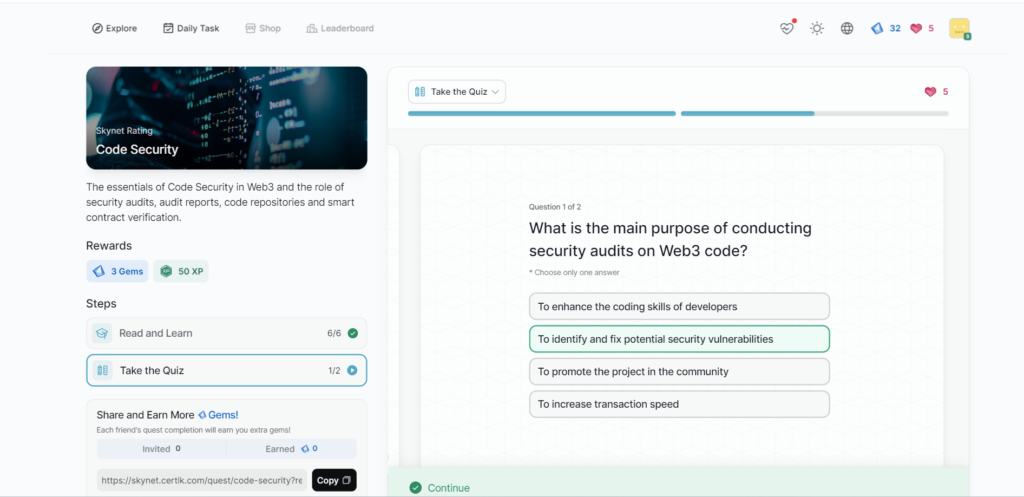
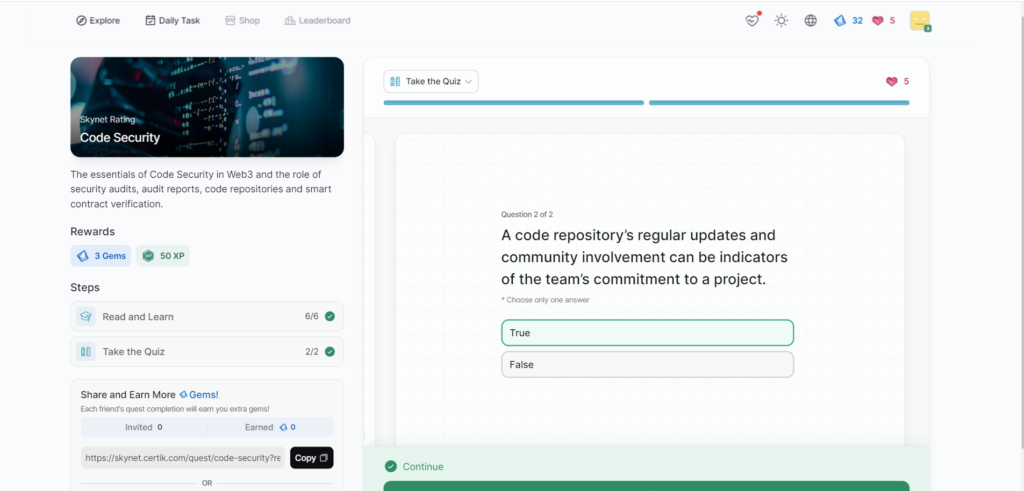
- Code Security
- Governance and Security in DAOs
- Introduction to User Security
- Operational Security
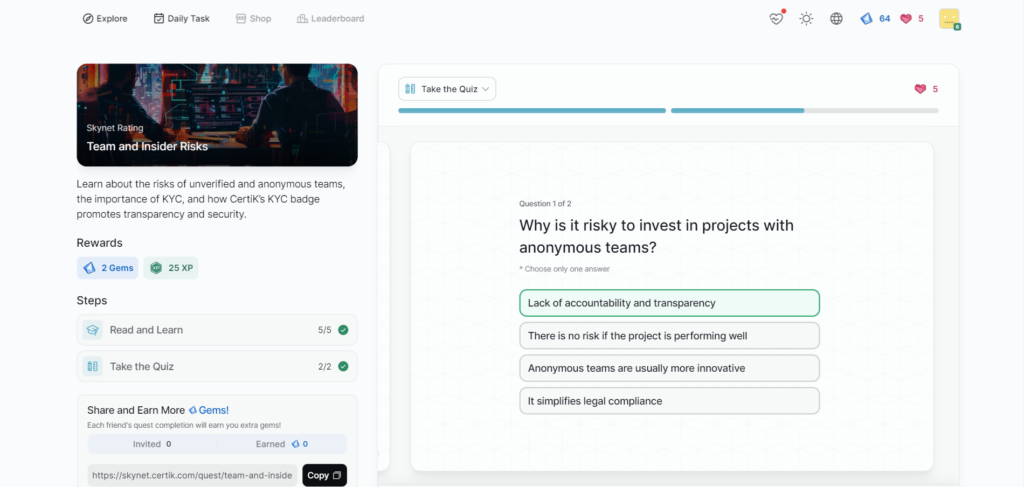
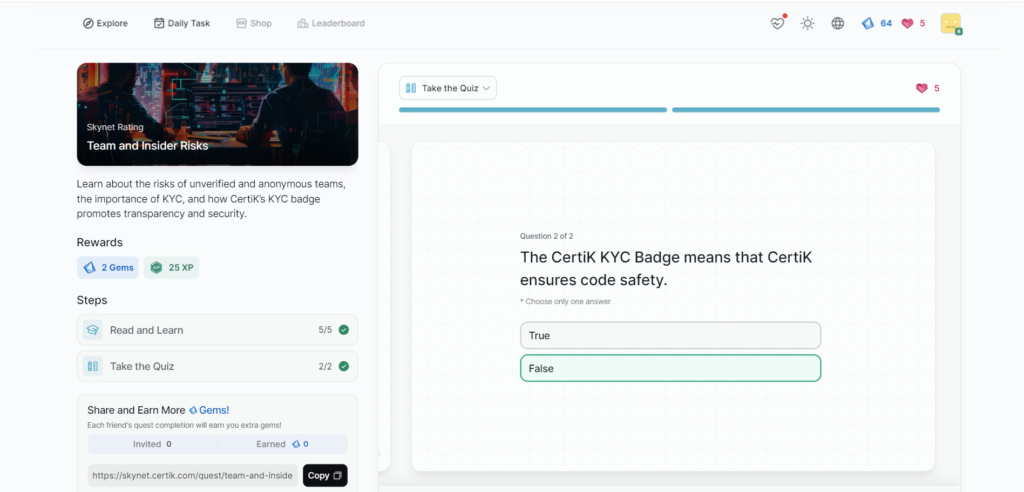
- Team and Insider Risks
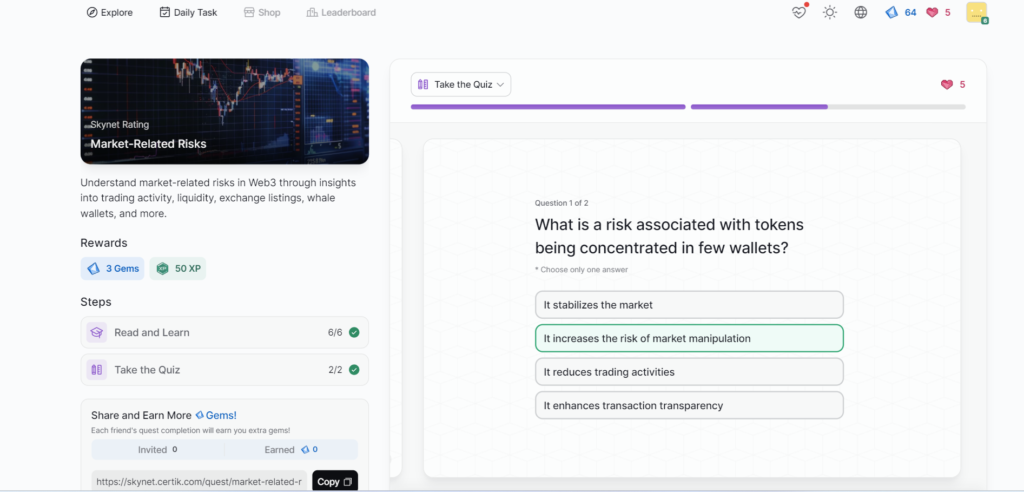
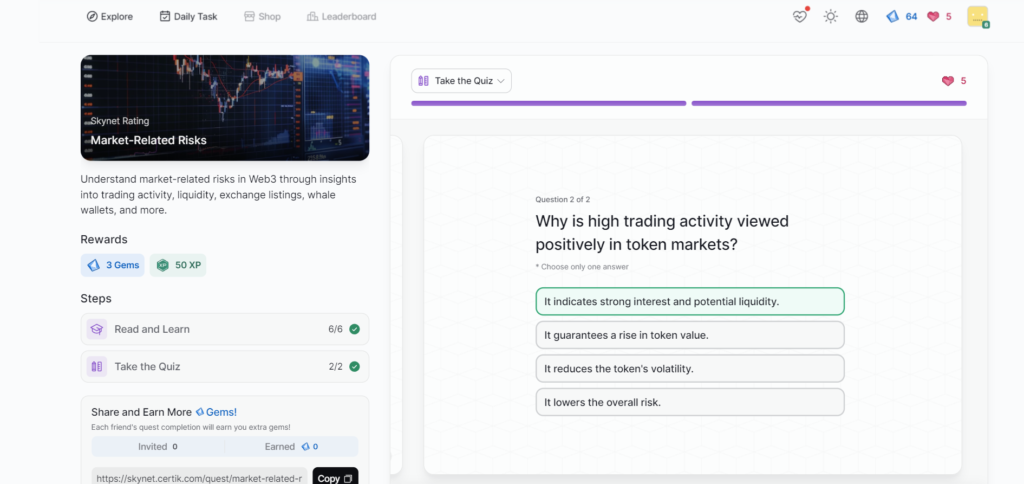
- Market-Related Risks
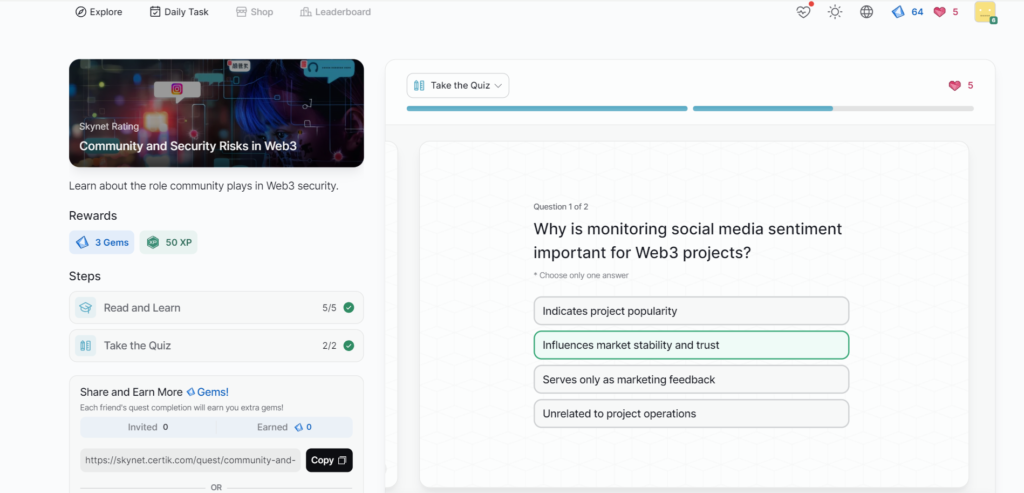
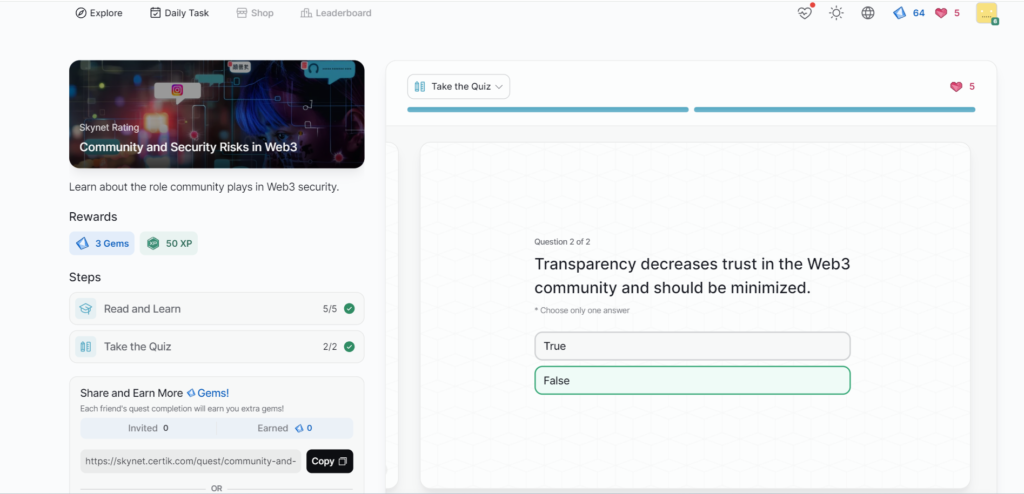
- Community and Security Risks in Web3
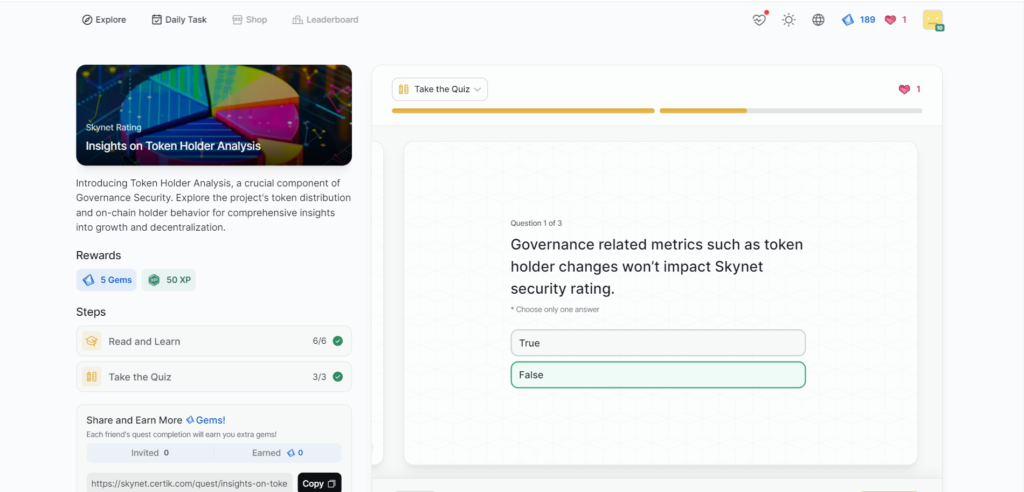
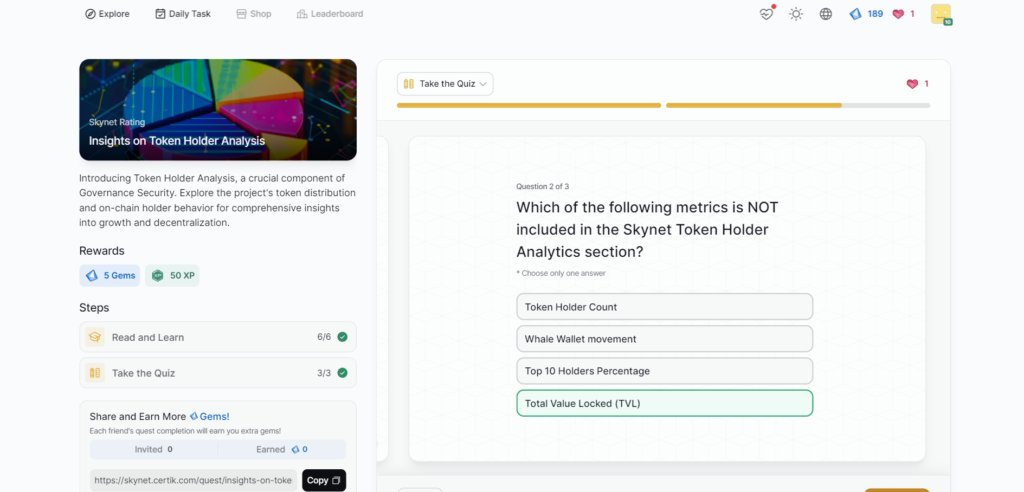
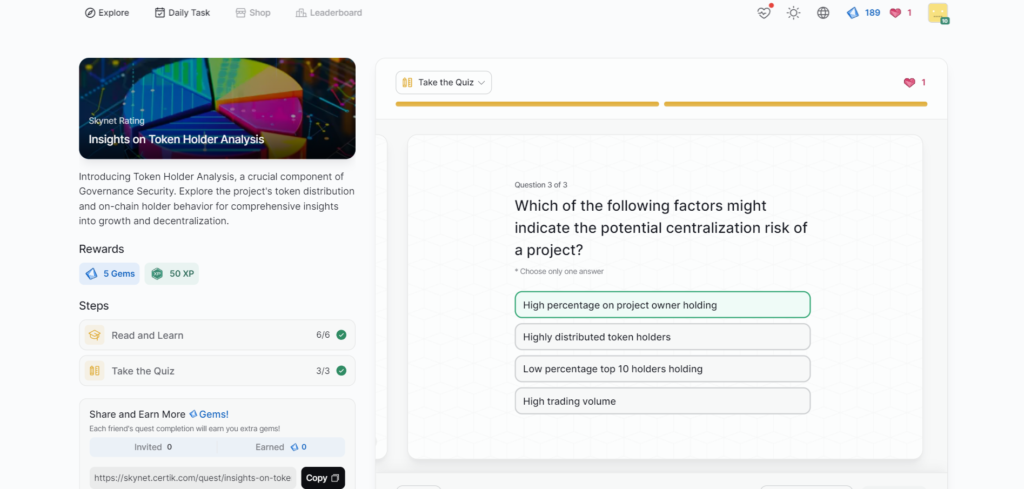
- Insights on Token Holder Analysis
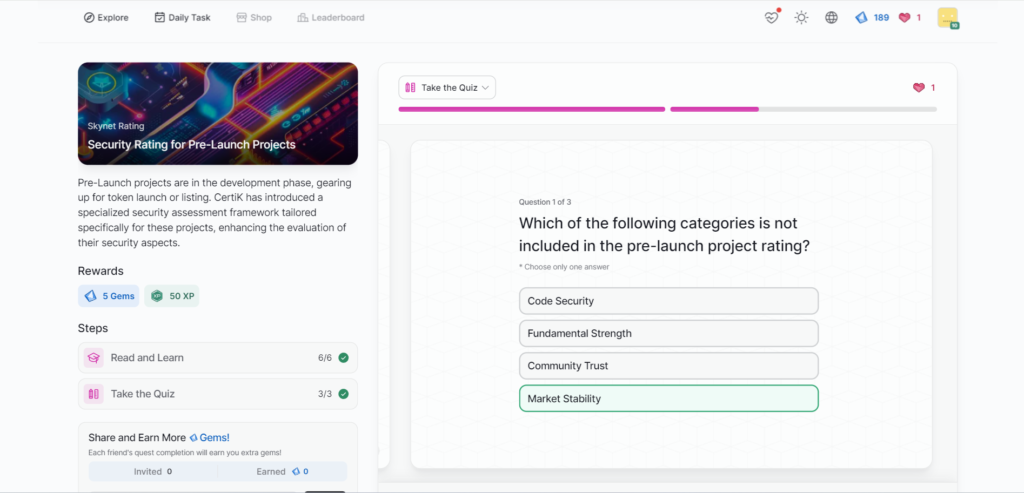
- Security Rating for Pre-Launch Projects
- RWA Security and Leaderboard
- Proof of Work versus Proof of Stake
- Security Score Impacts with OKX
- Skynet Pulse – Real-Time Insights by Security Experts
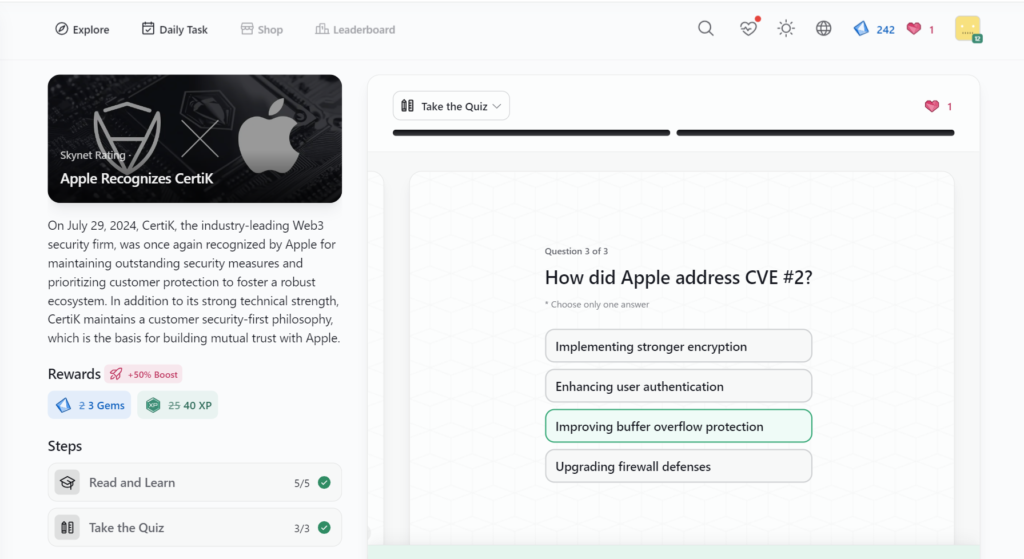
- Apple Recognizes CertiK
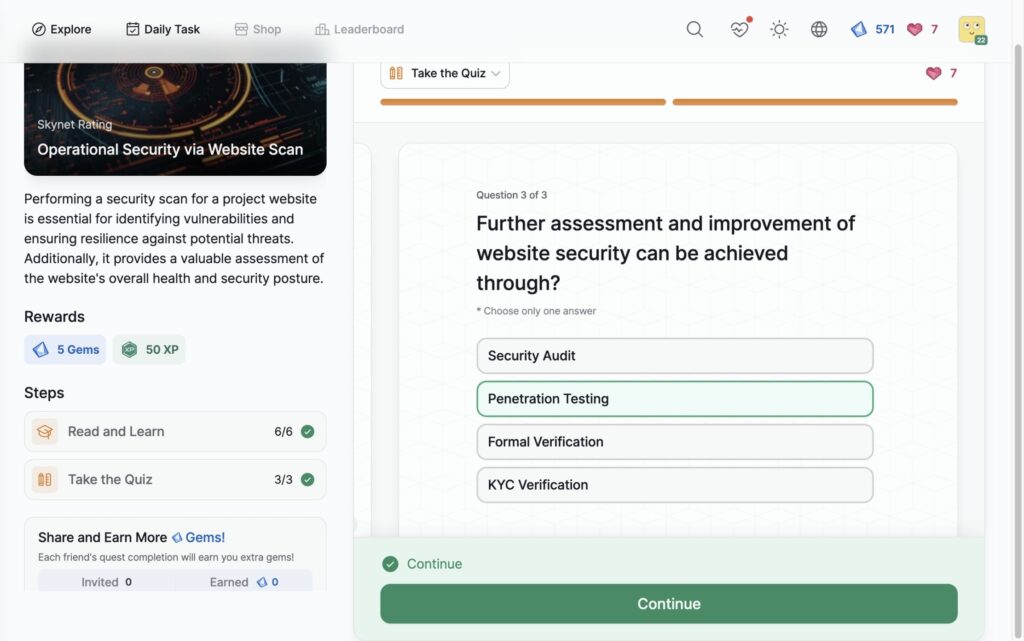
- Operational Security via Website Scan
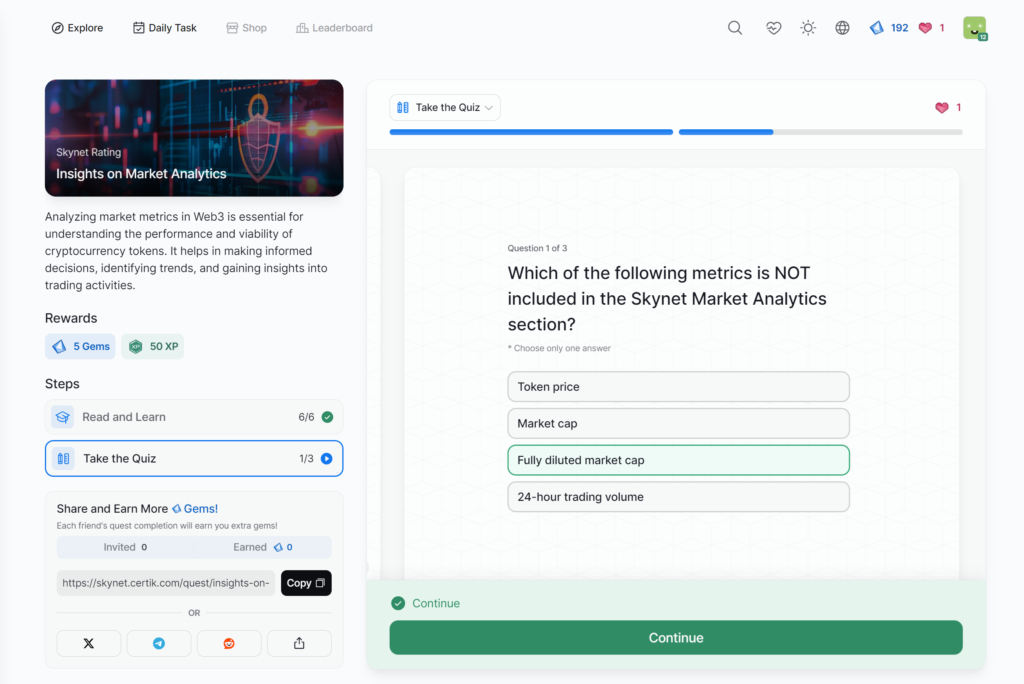
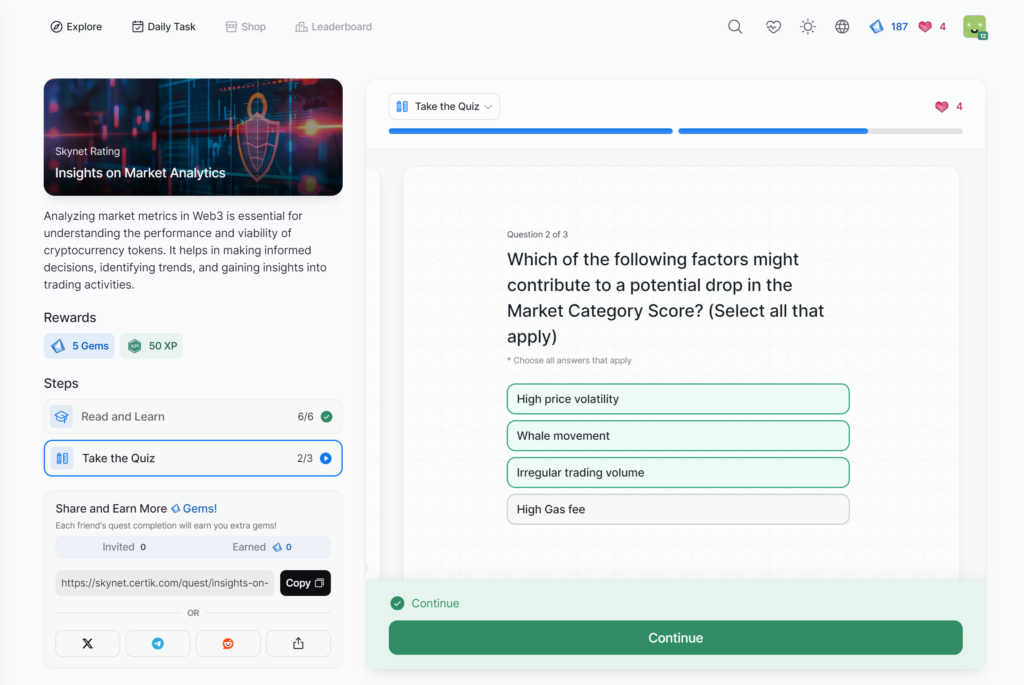
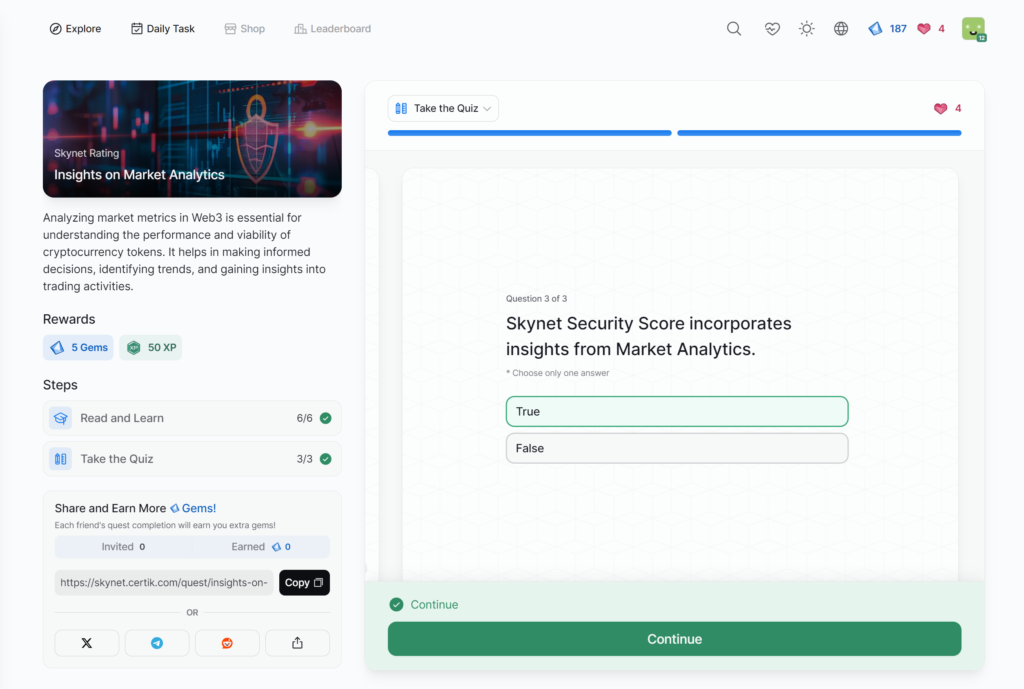
- Insights on Market Analytics
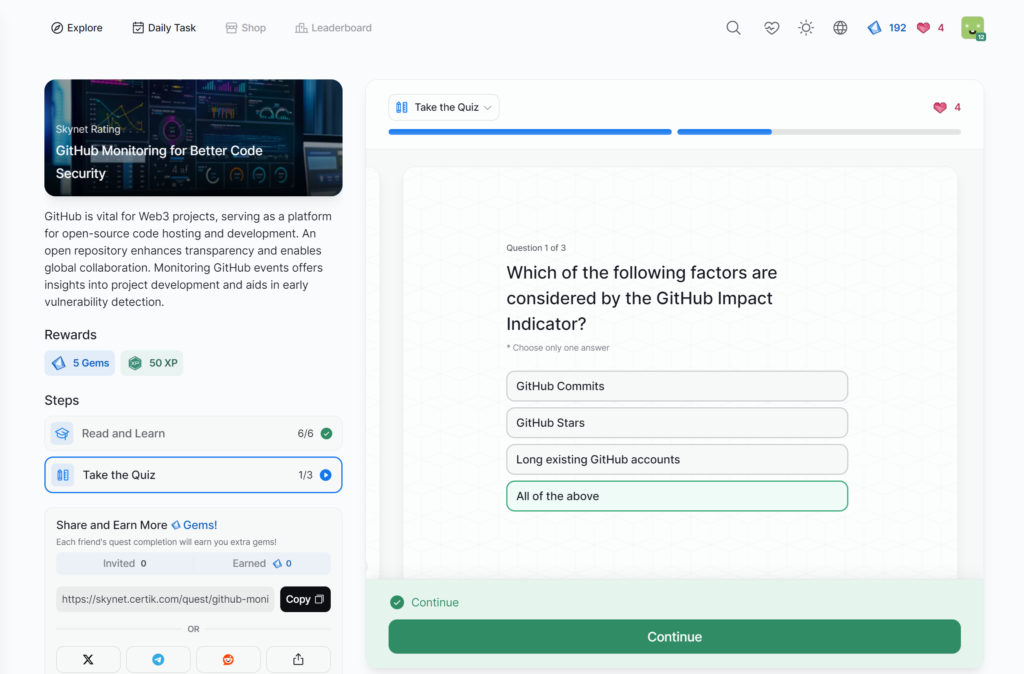
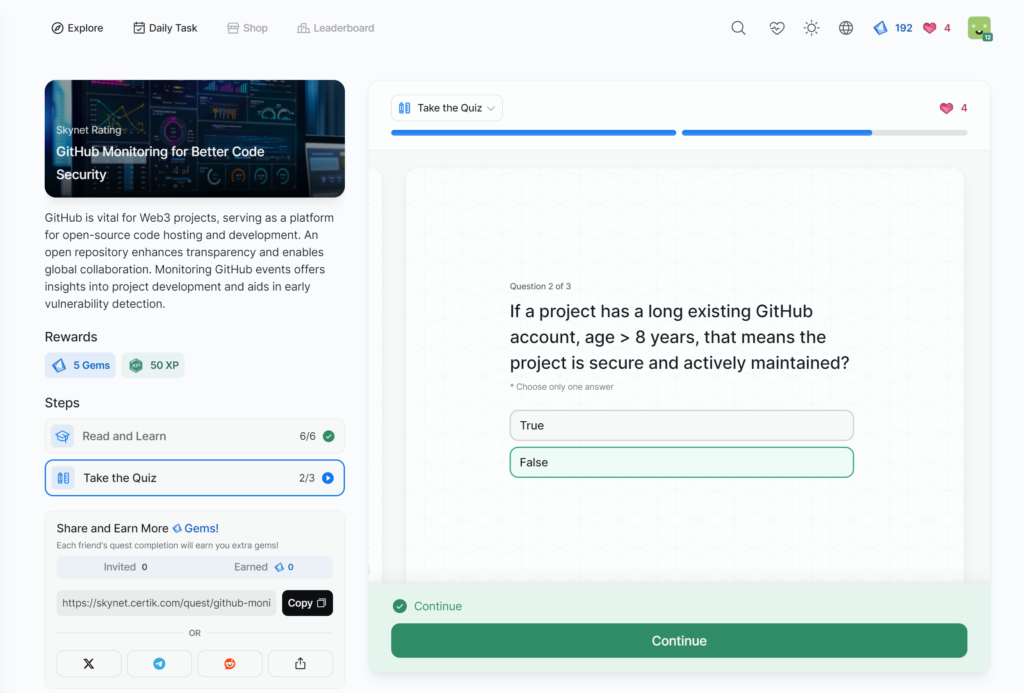
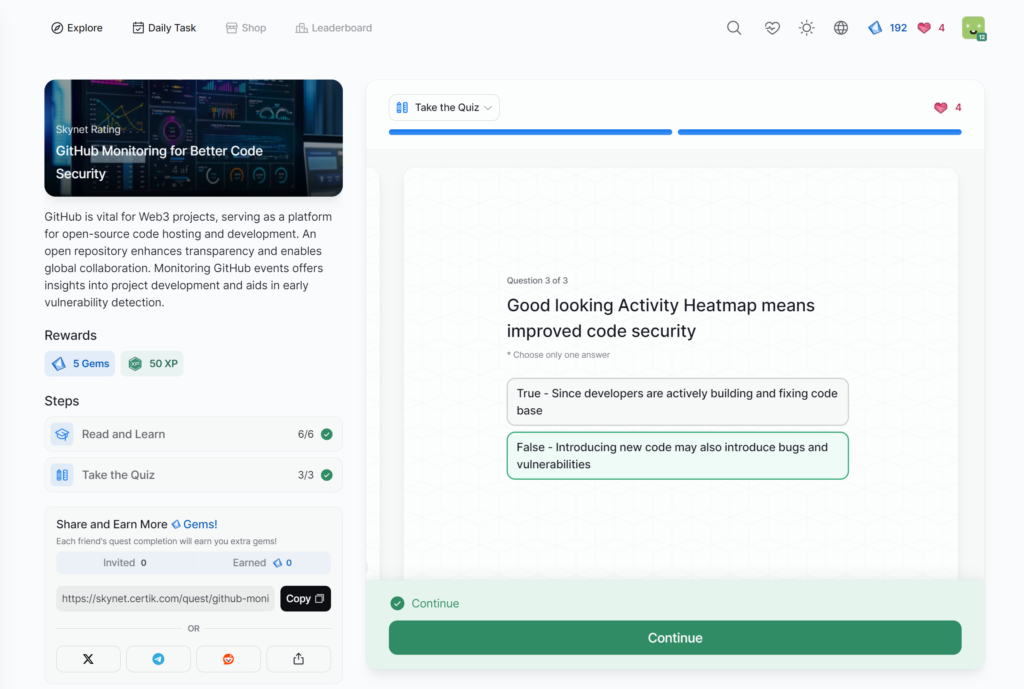
- GitHub Monitoring for Better Code Security
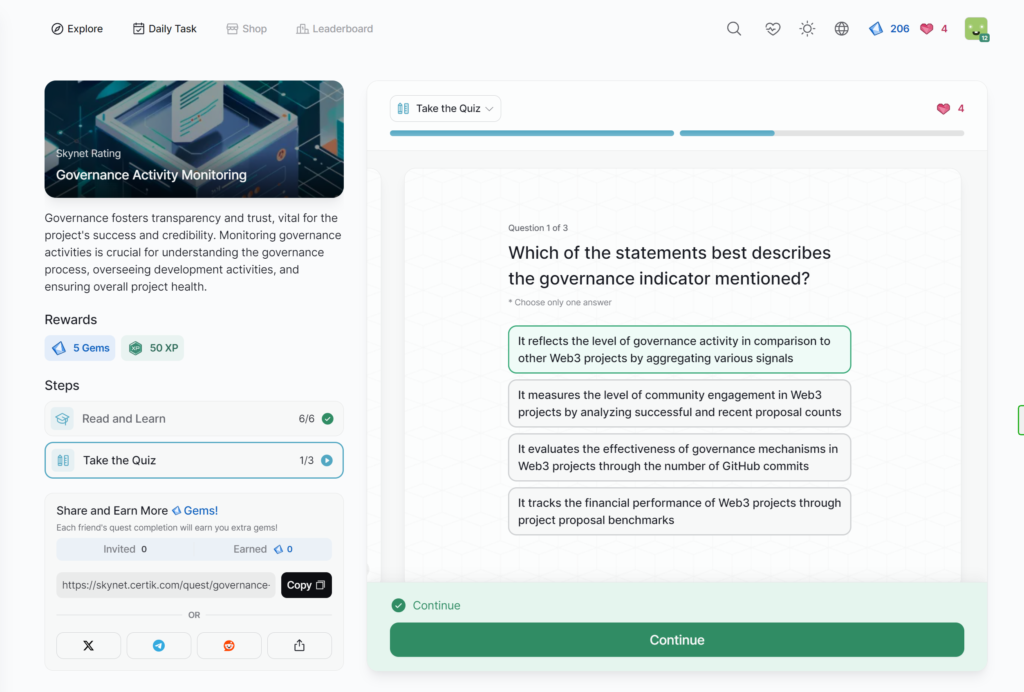
- Governance Activity Monitoring
- Apple Recognizes CertiK
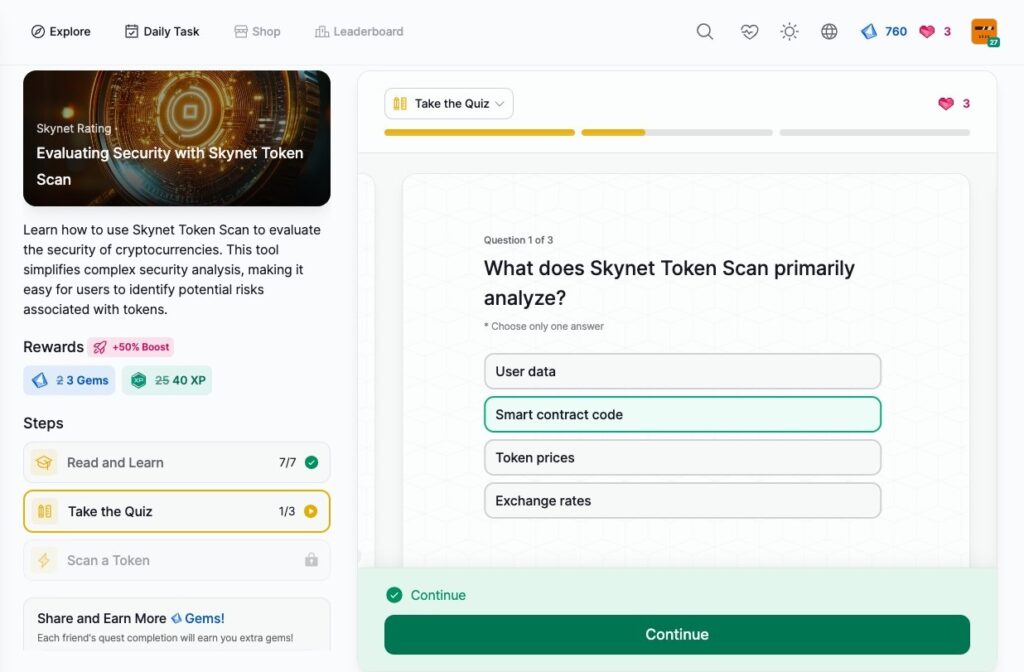
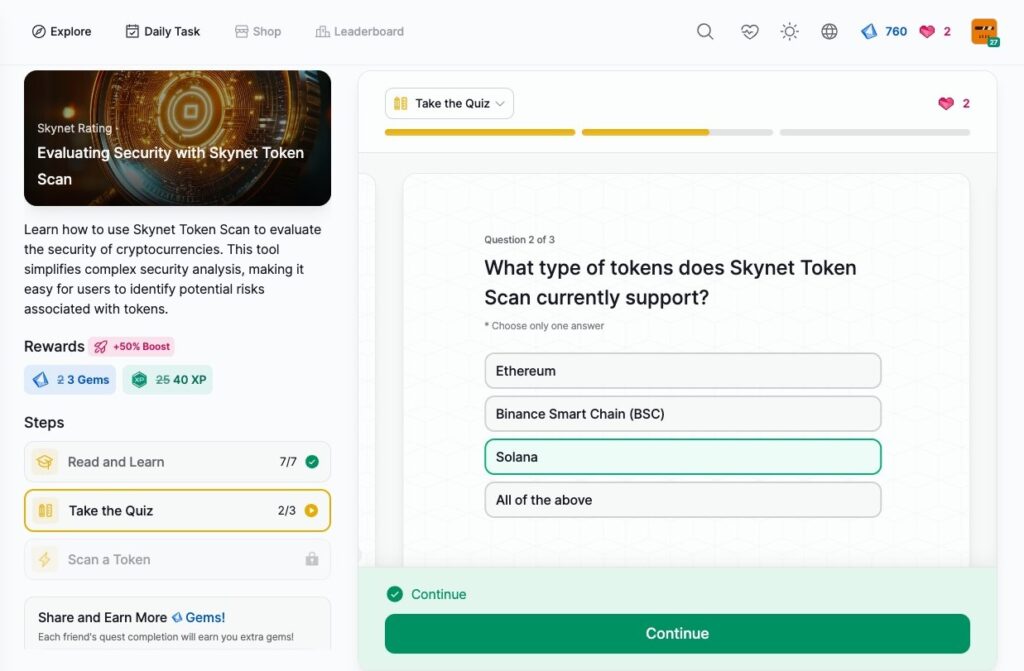
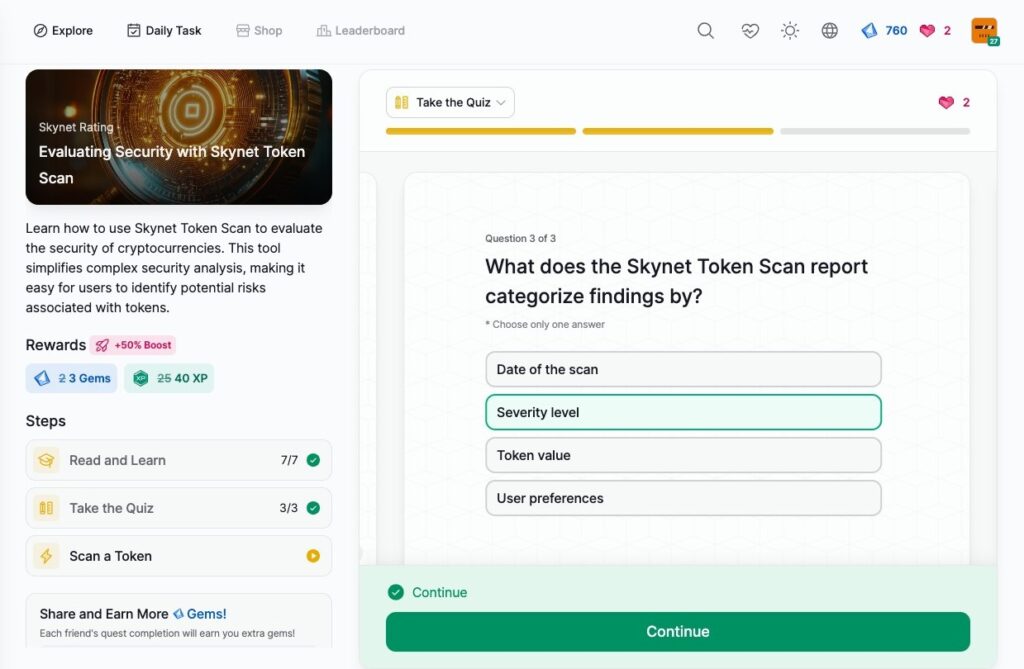
- Evaluating Security with Skynet Token Scan
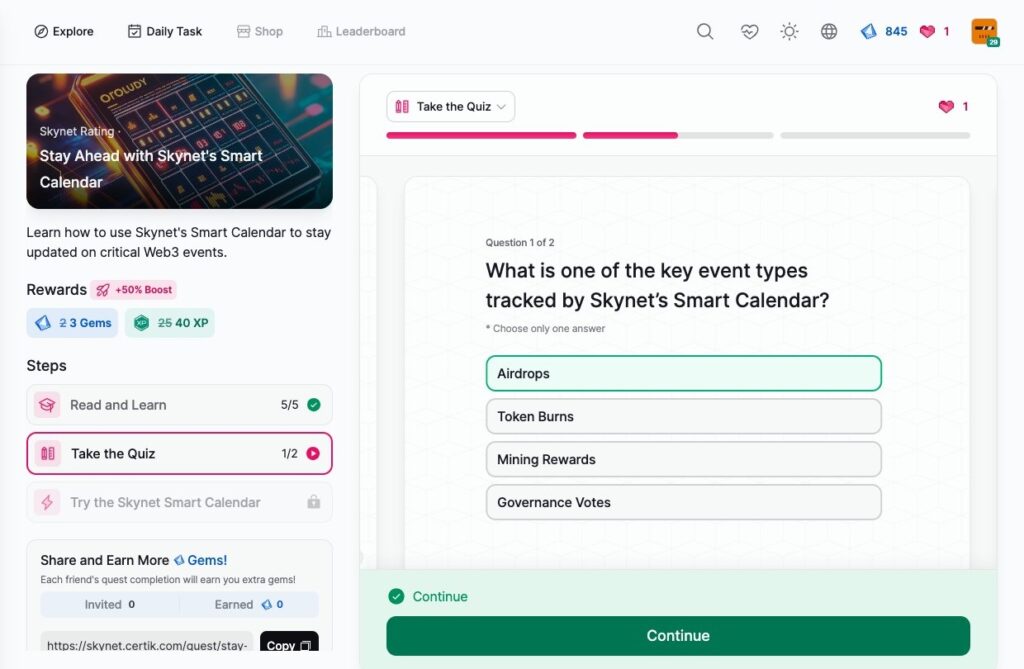
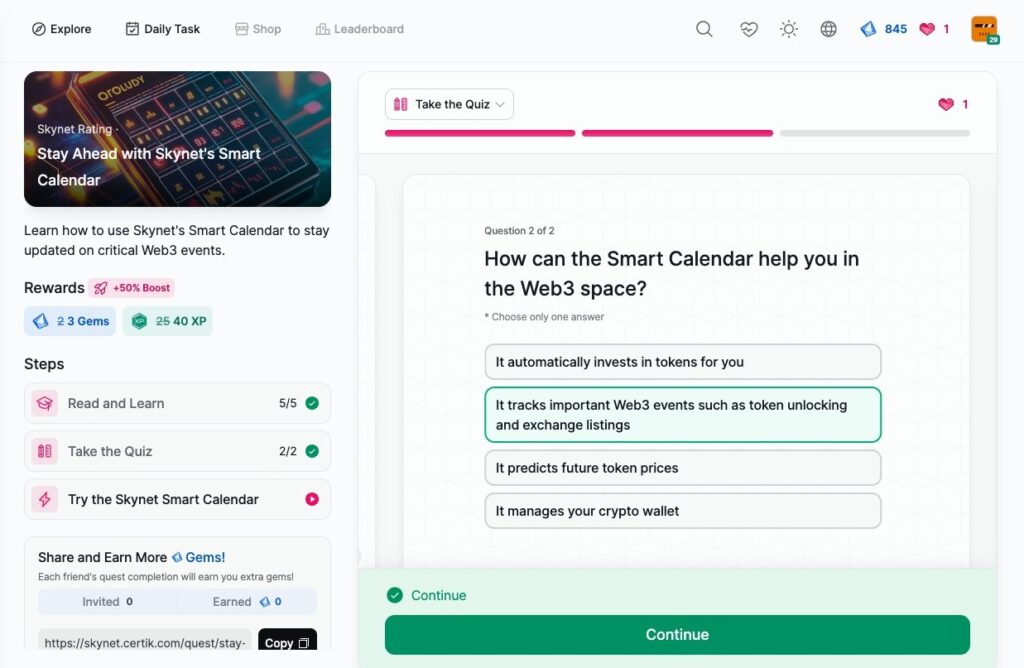
- Stay Ahead with Skynet’s Smart Calendar
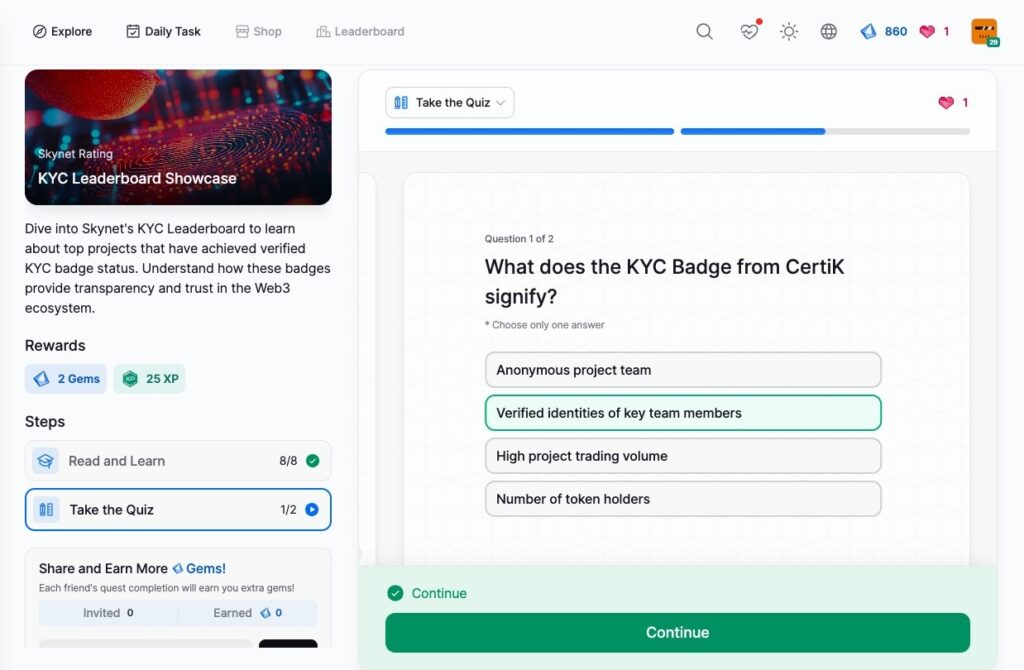
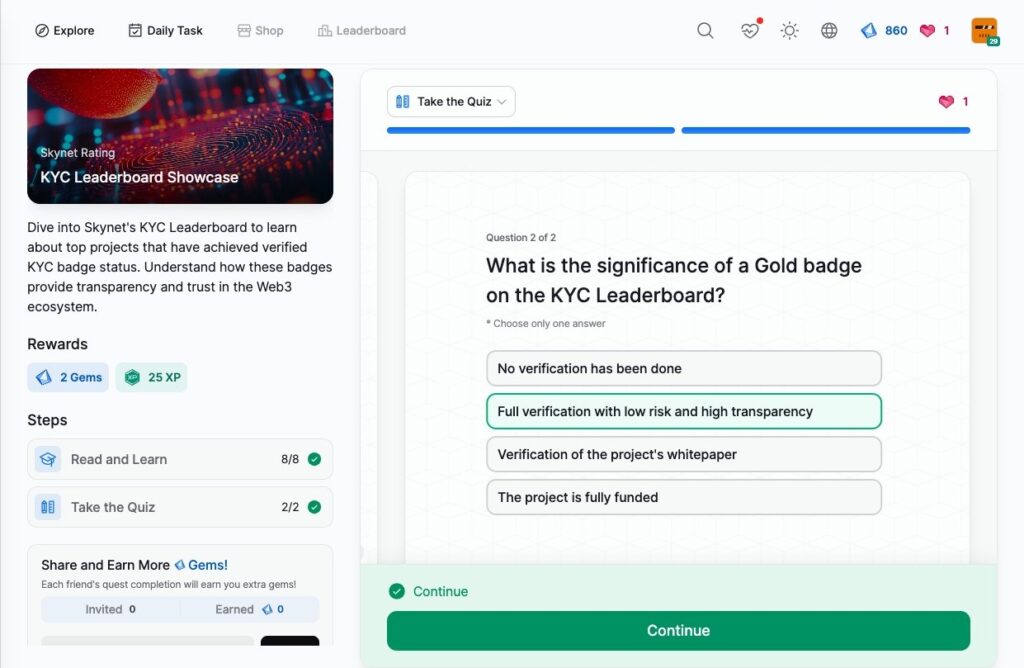
- KYC Leaderboard Showcase
- Prioritize Wallet Security with Skynet Wallet Scanning
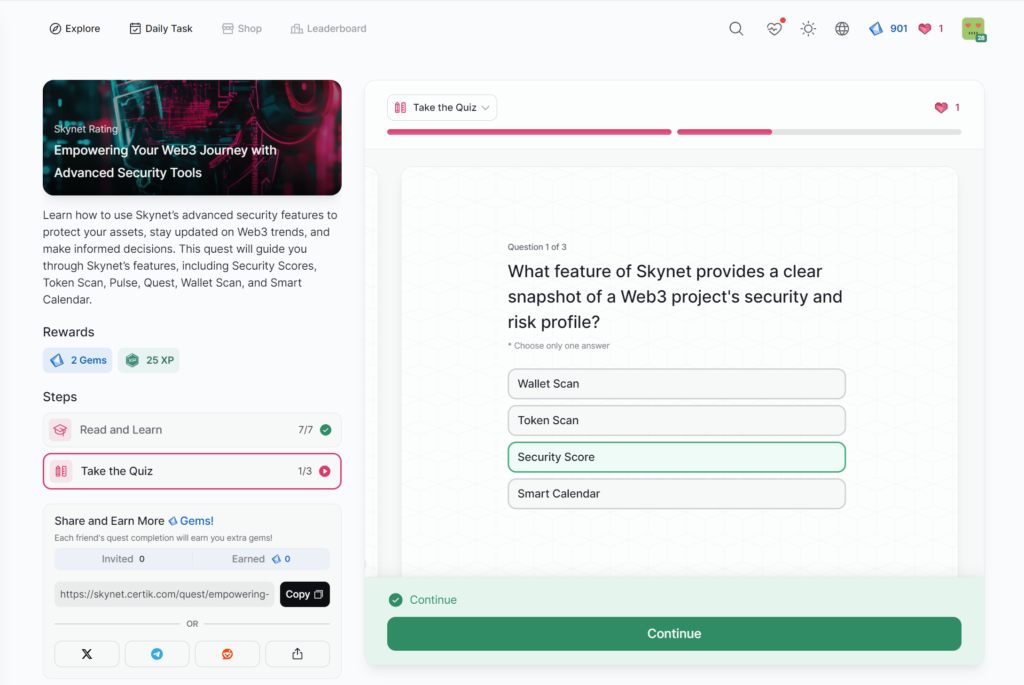
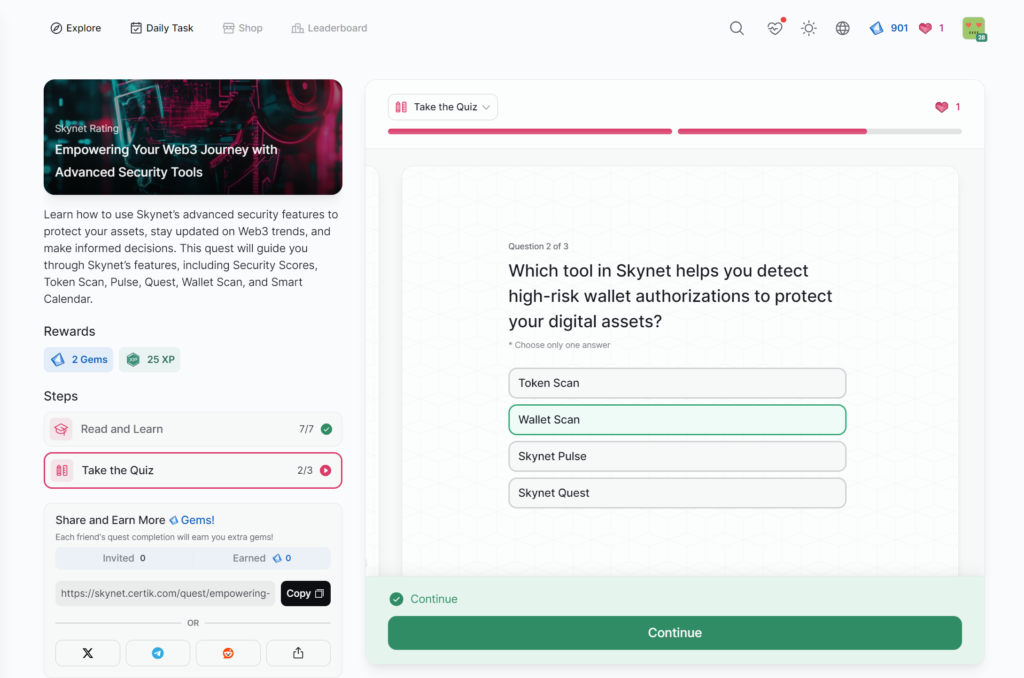
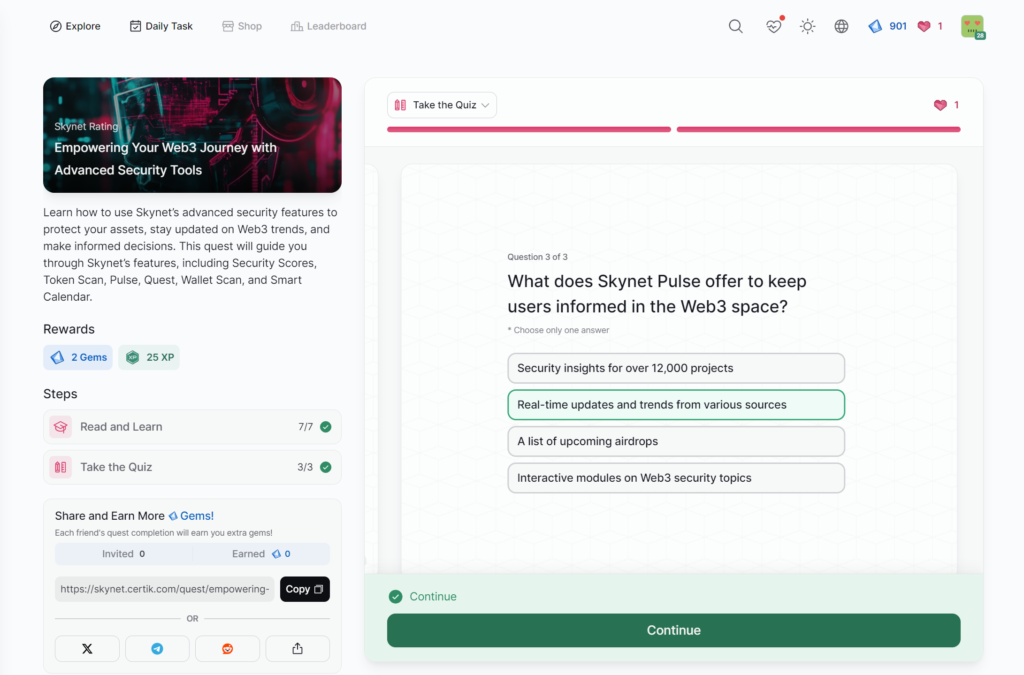
- Empowering Your Web3 Journey with Advanced Security Tools
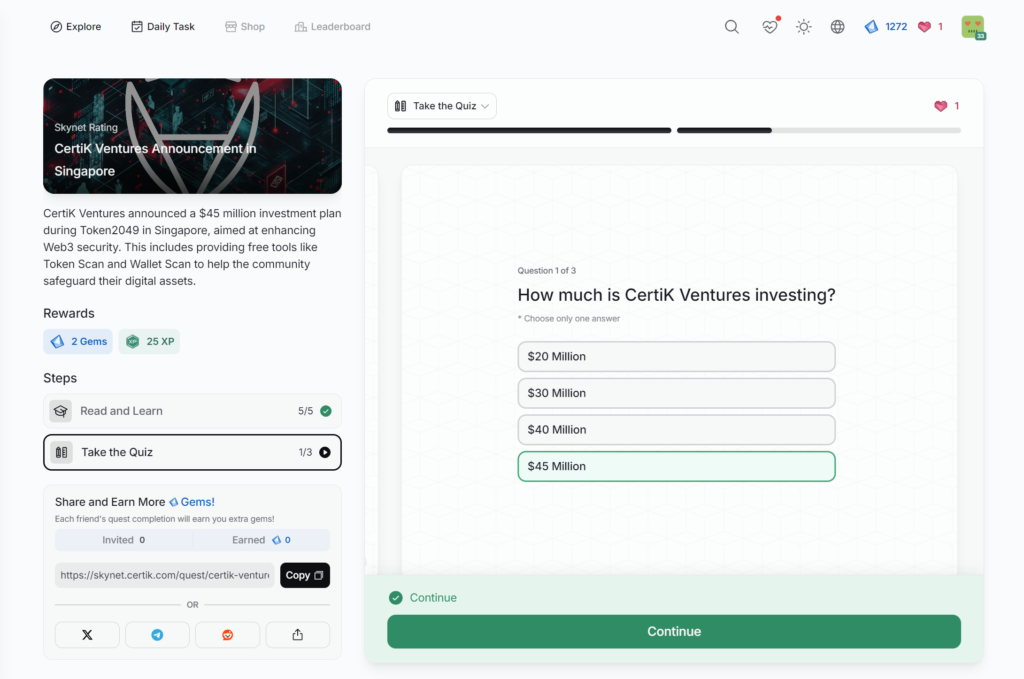
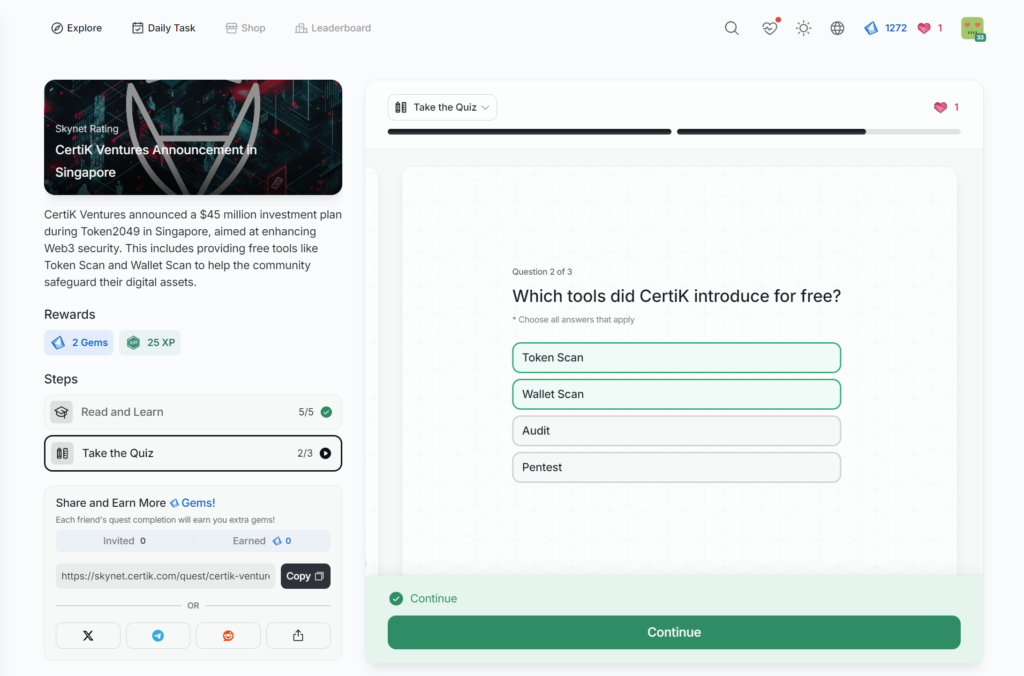
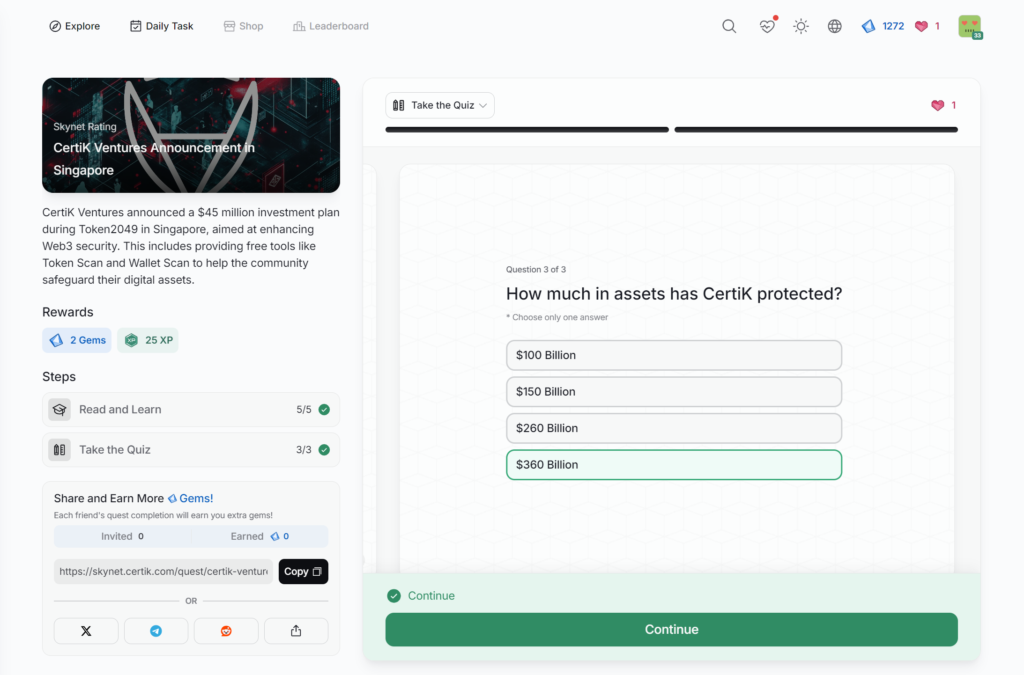
- CertiK Ventures Announcement in Singapore
- Private Key Security
- Important Exchange Security Features
- Website & dApp Security
- Recognizing Risk Signals on the Exchange
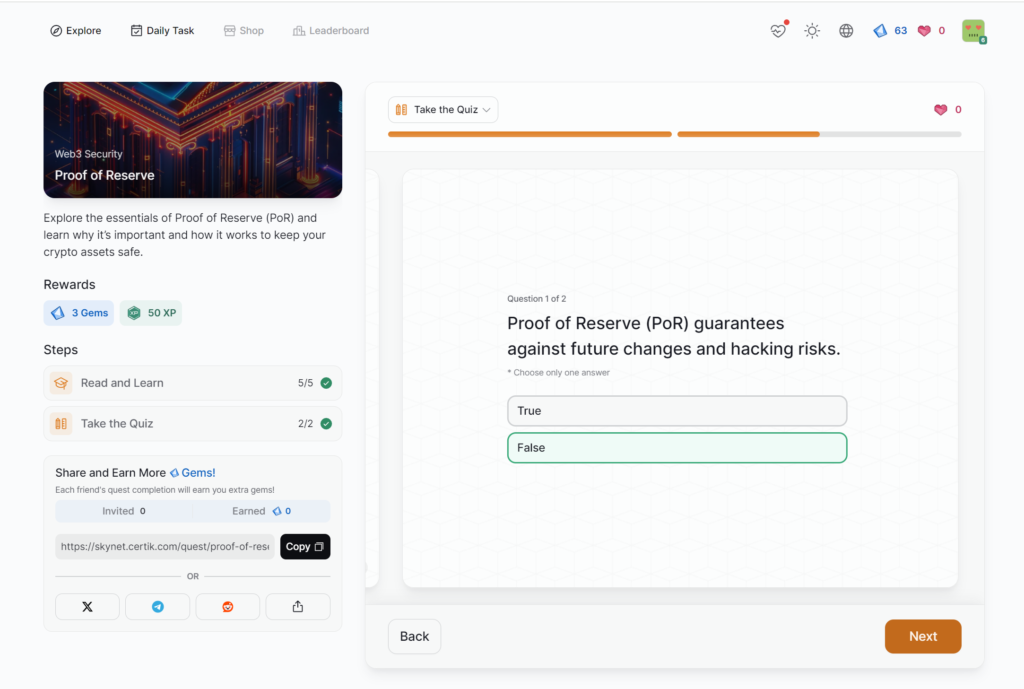
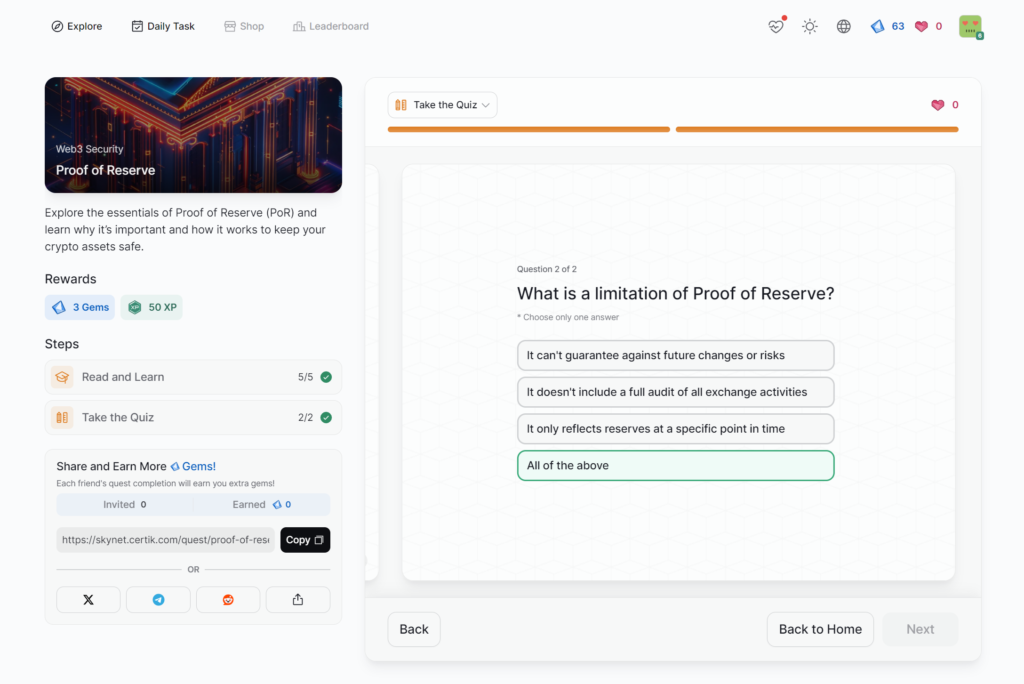
- Proof of Reserve
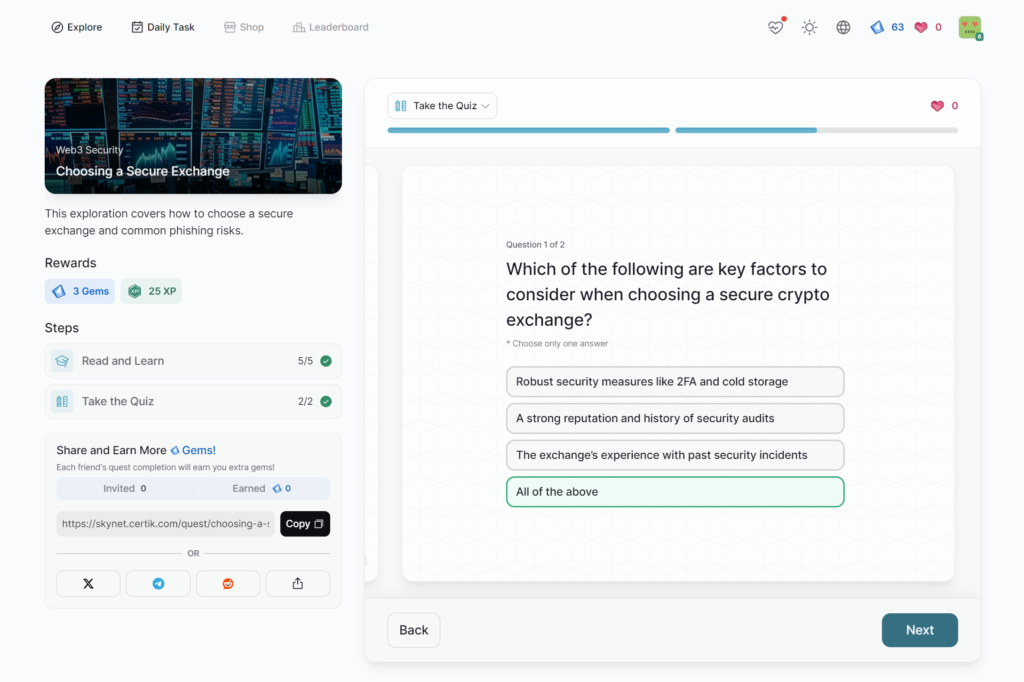
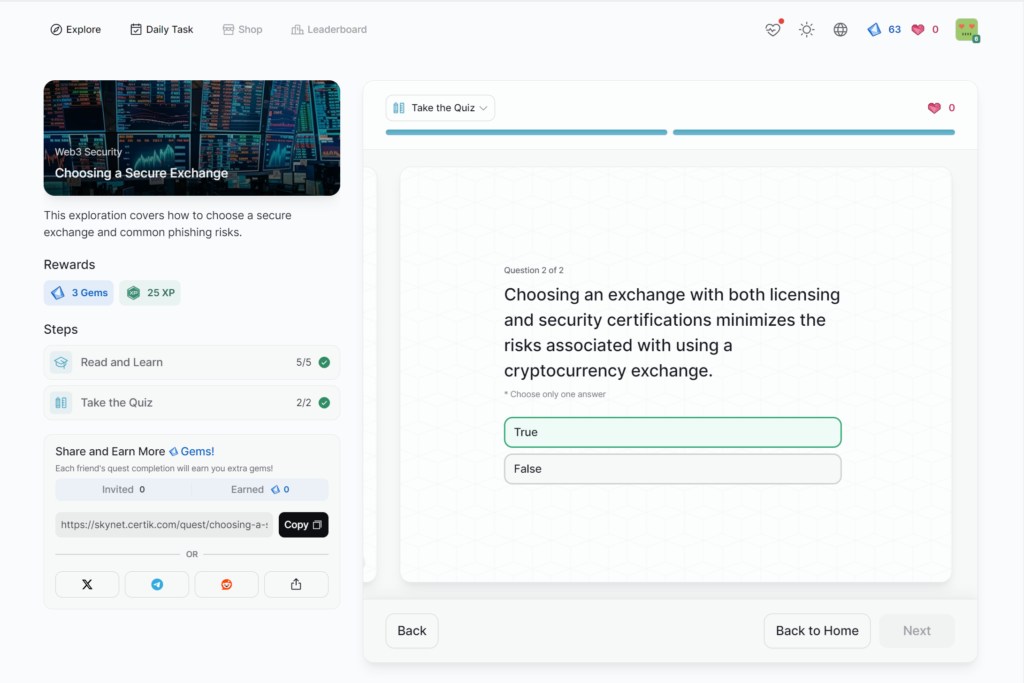
- Choosing a Secure Exchange
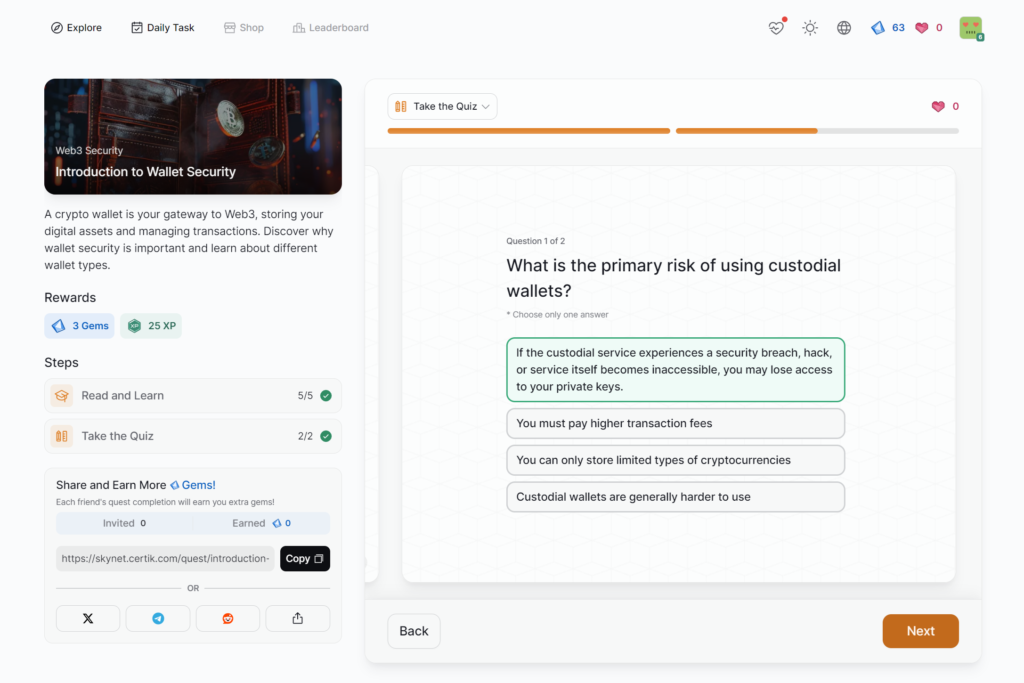
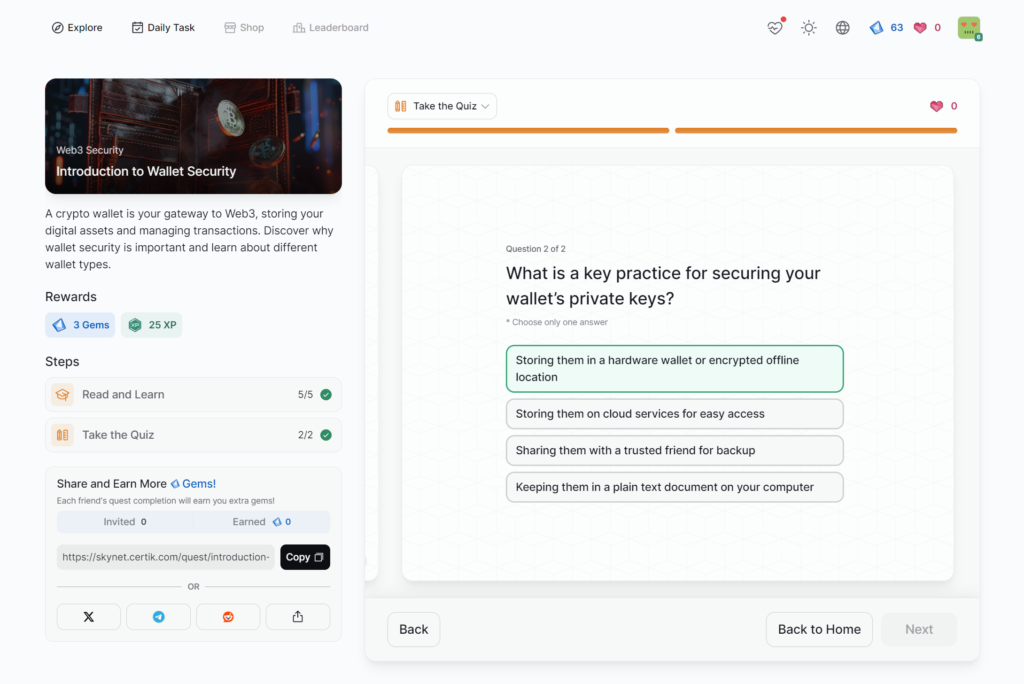
- Introduction to Wallet Security
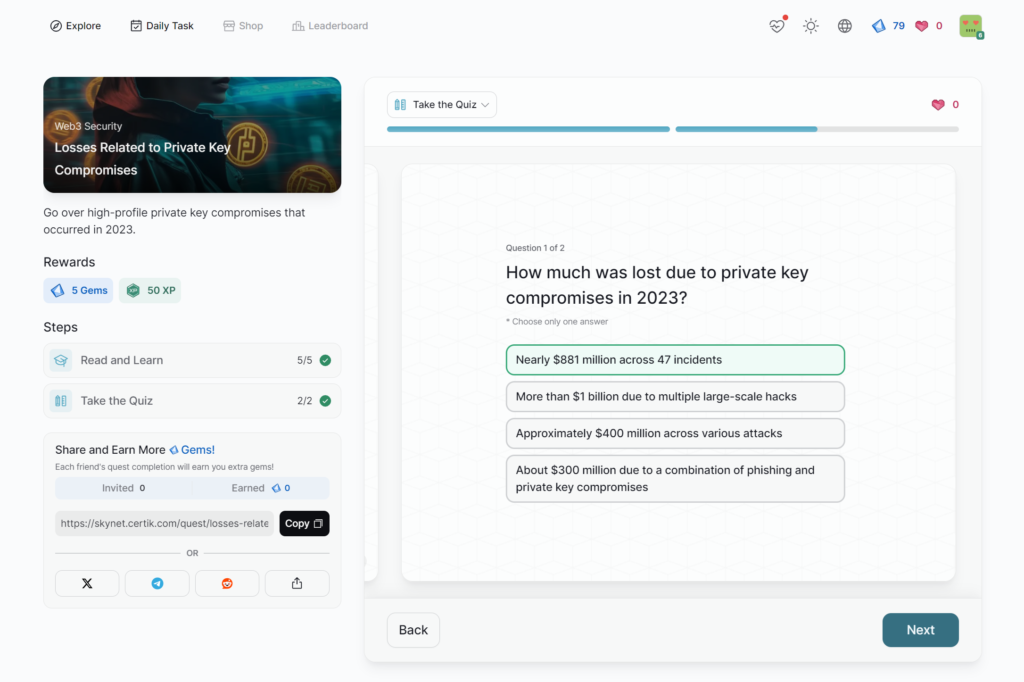
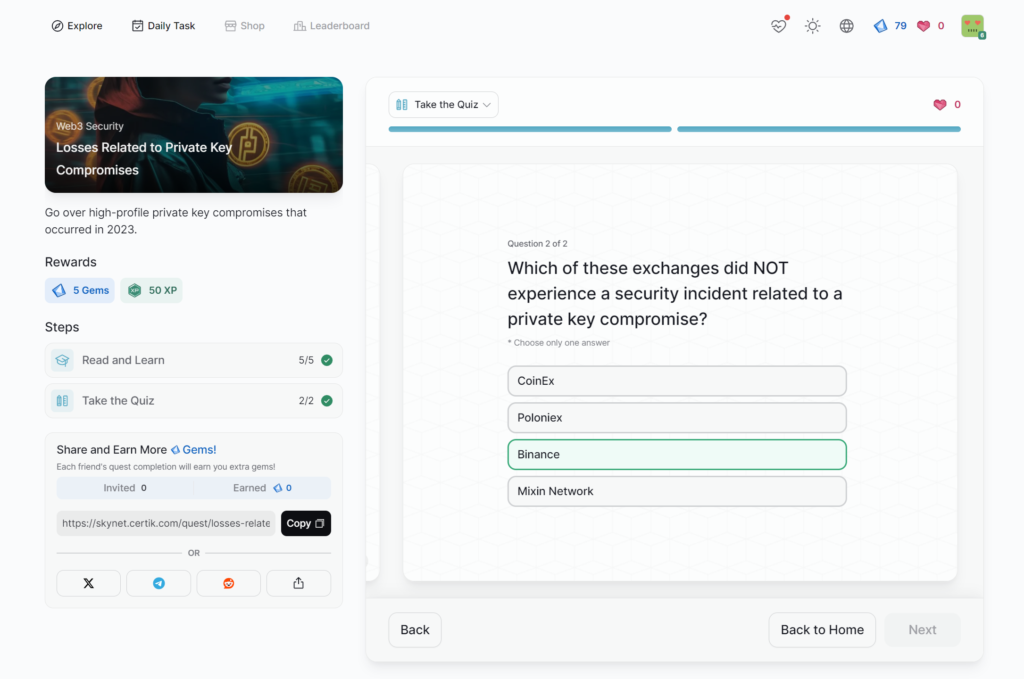
- Losses Related to Private Key Compromises
- Private Key Security: Seed Phrases
- Identifying and Avoiding Phishing Scams in X Replies
- Common Web3 Phishing Methods
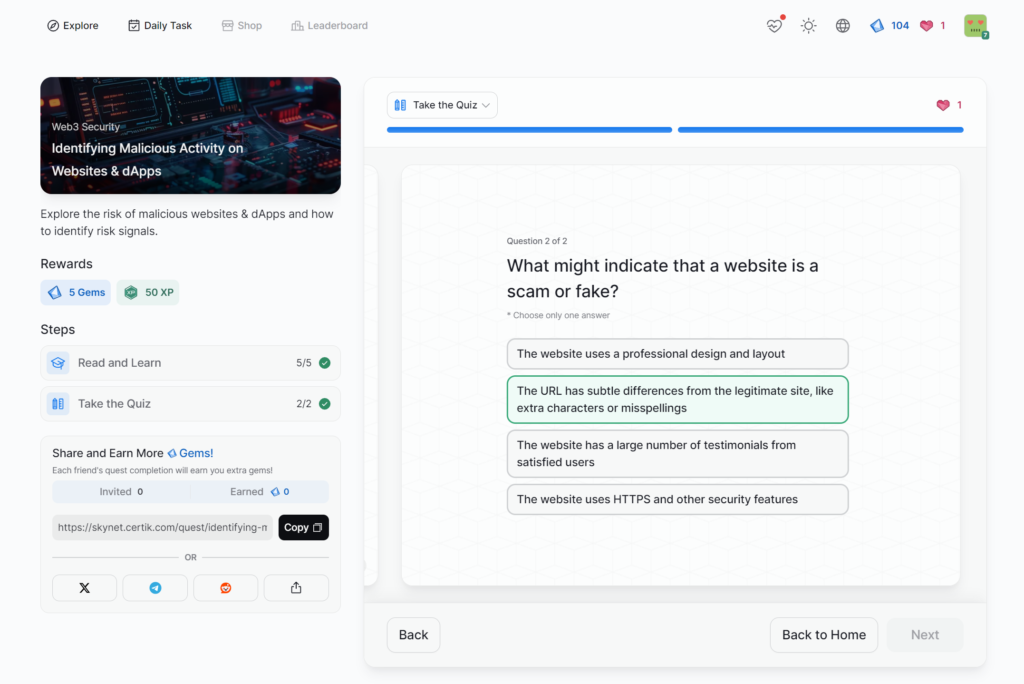
- Identifying Malicious Activity on Websites & dApps
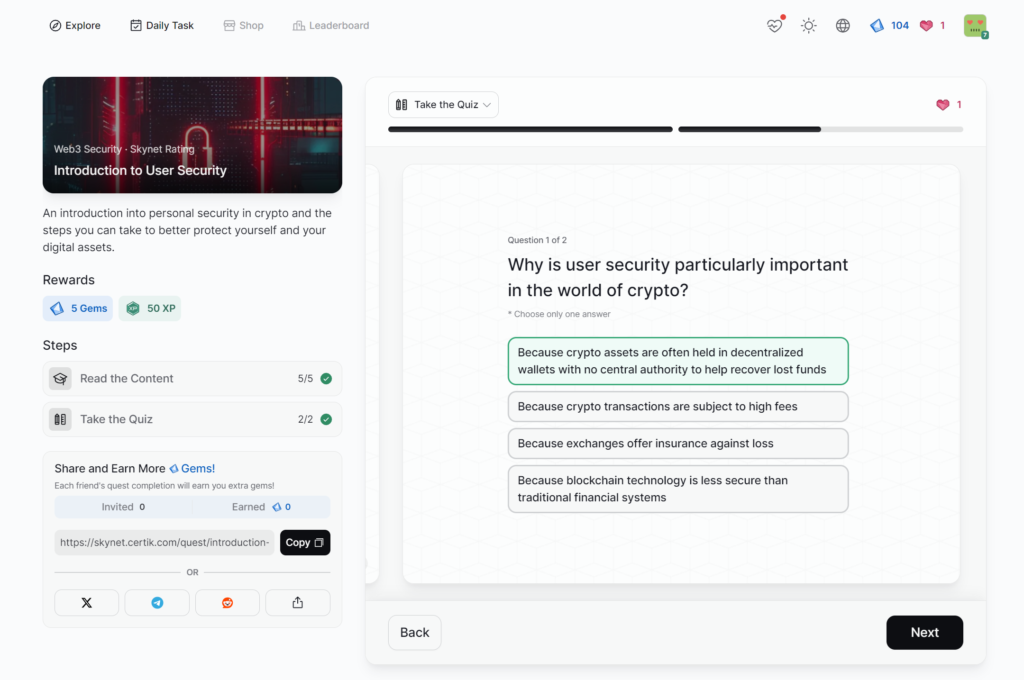
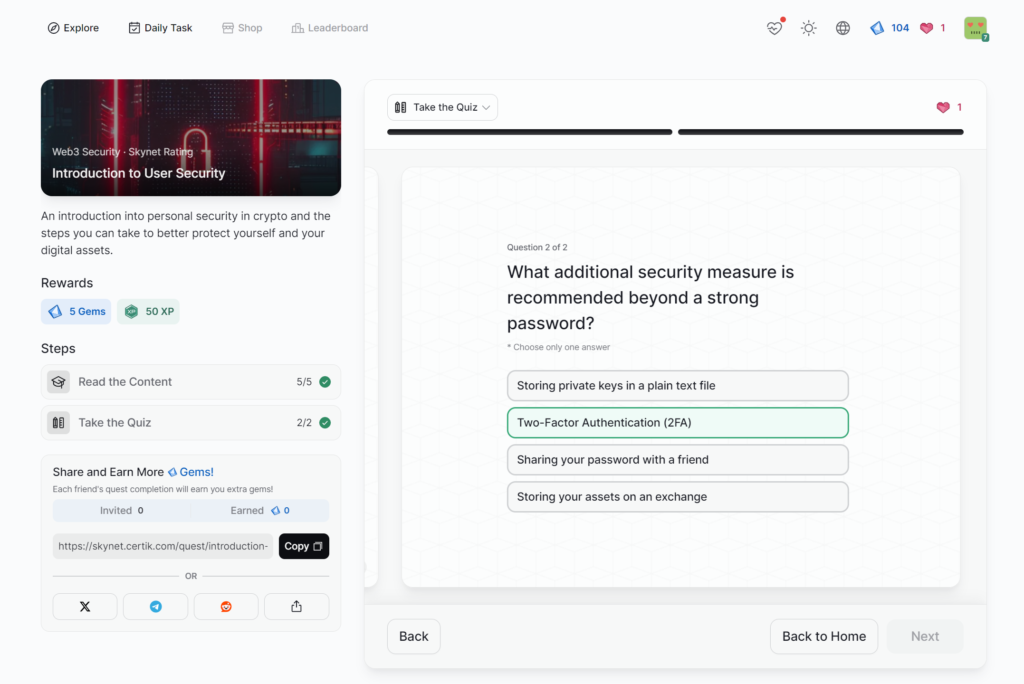
- Introduction to User Security
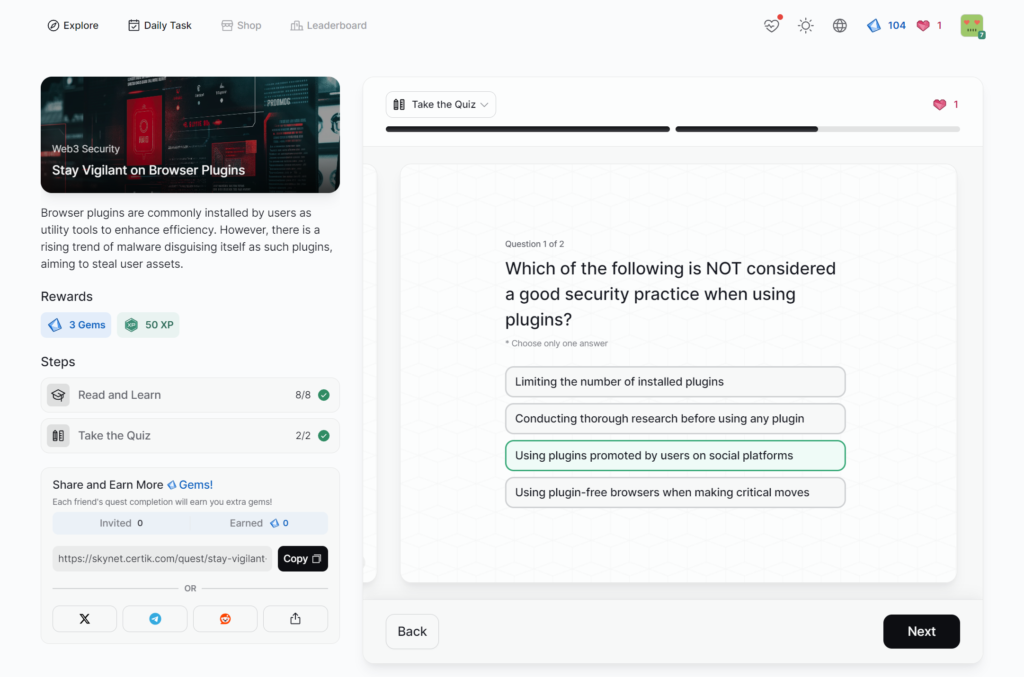
- Stay Vigilant on Browser Plugins
- Best Practices for Wallet Security
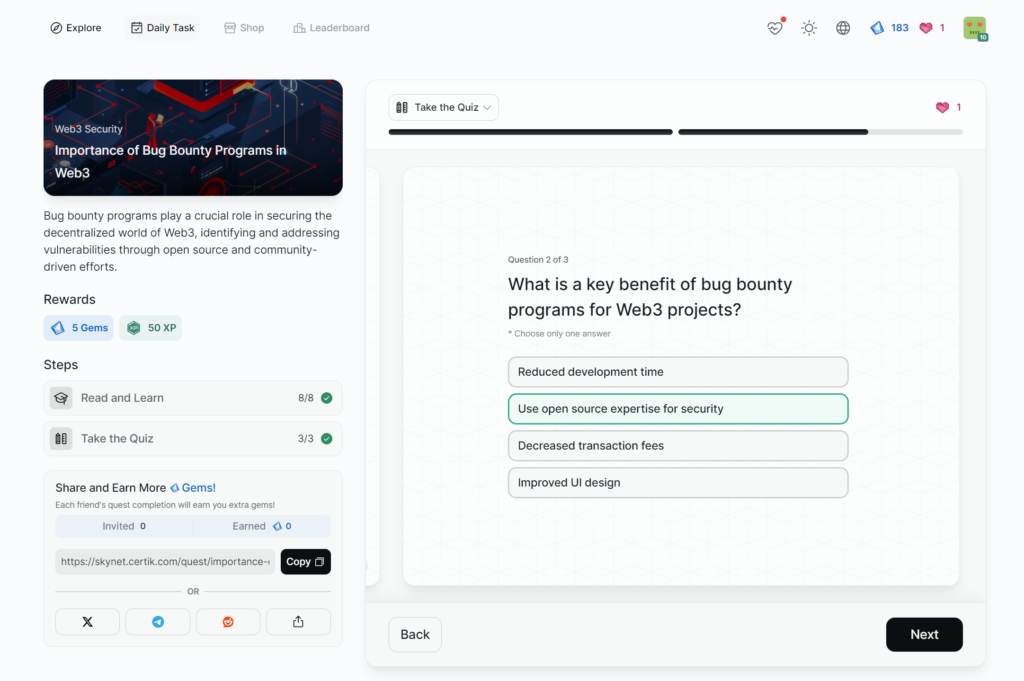
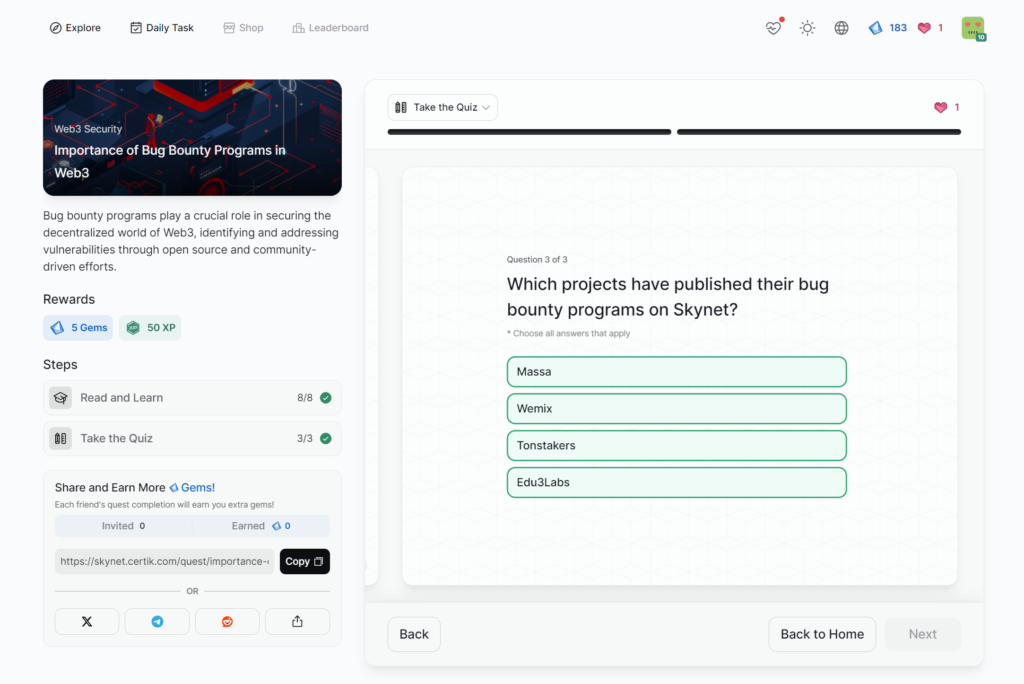
- Importance of Bug Bounty Programs in Web3
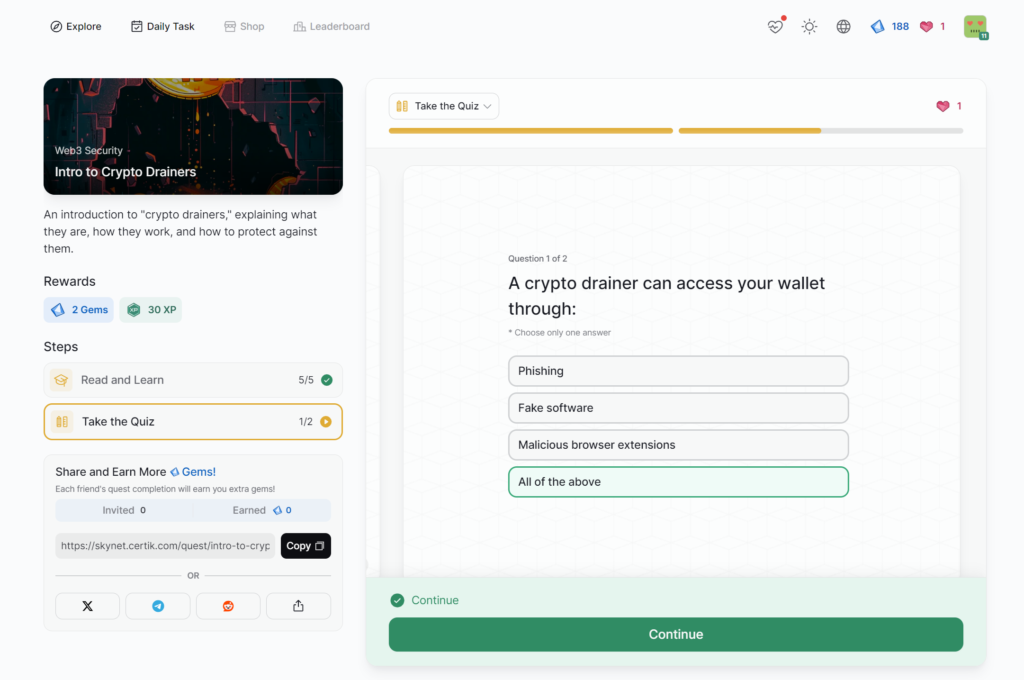
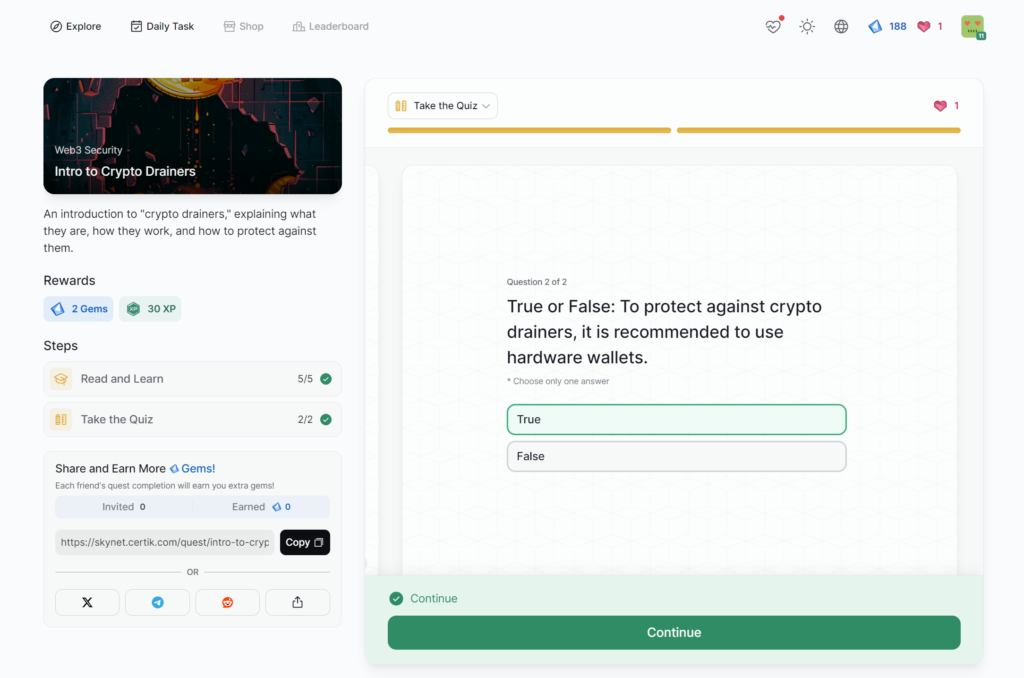
- Intro to Crypto Drainers
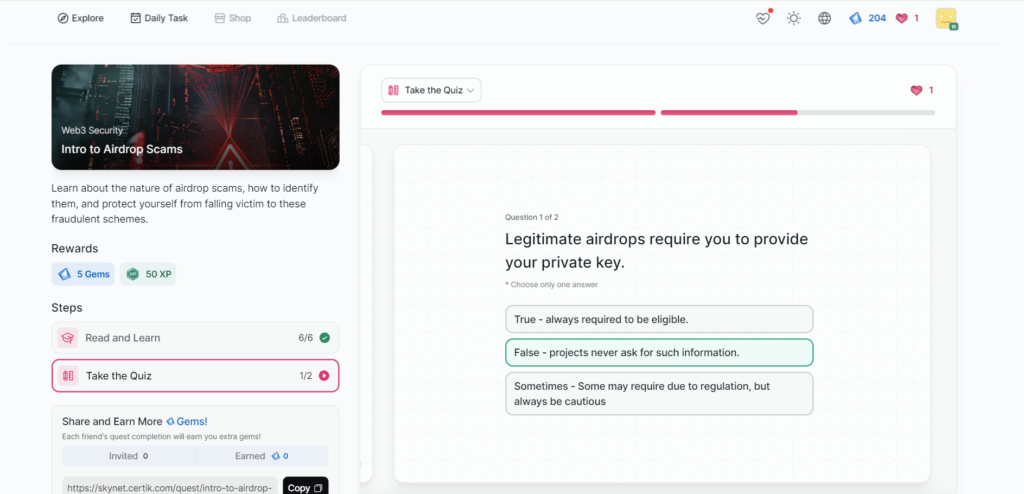
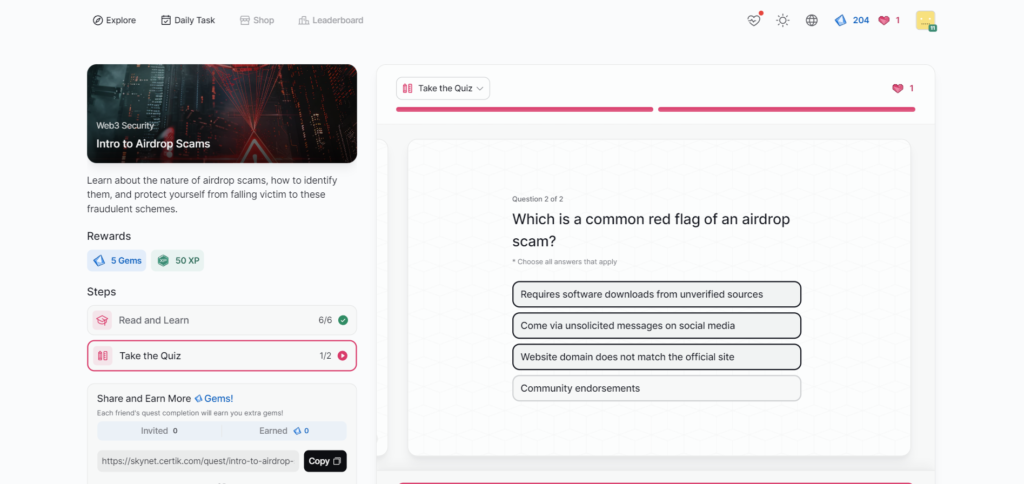
- Intro to Airdrop Scams
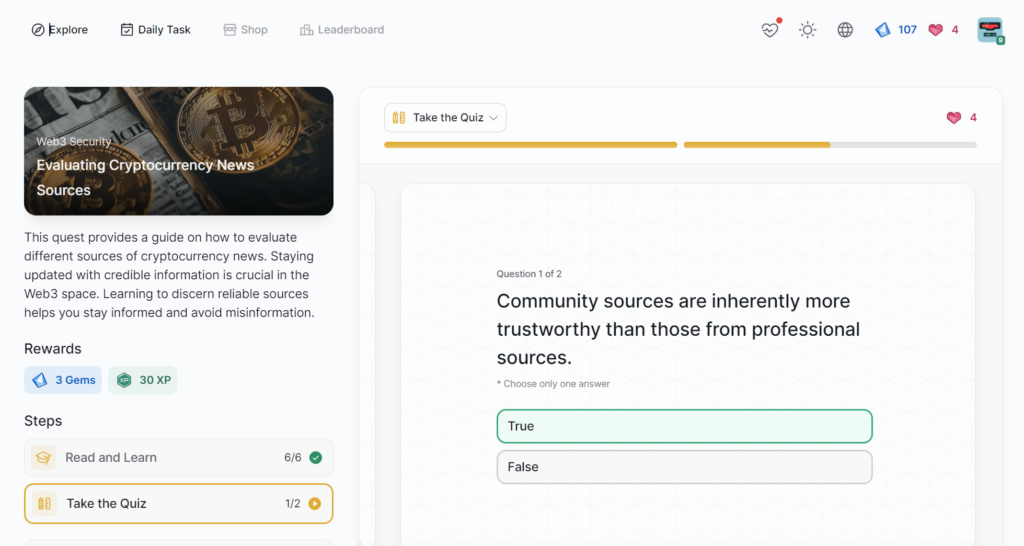
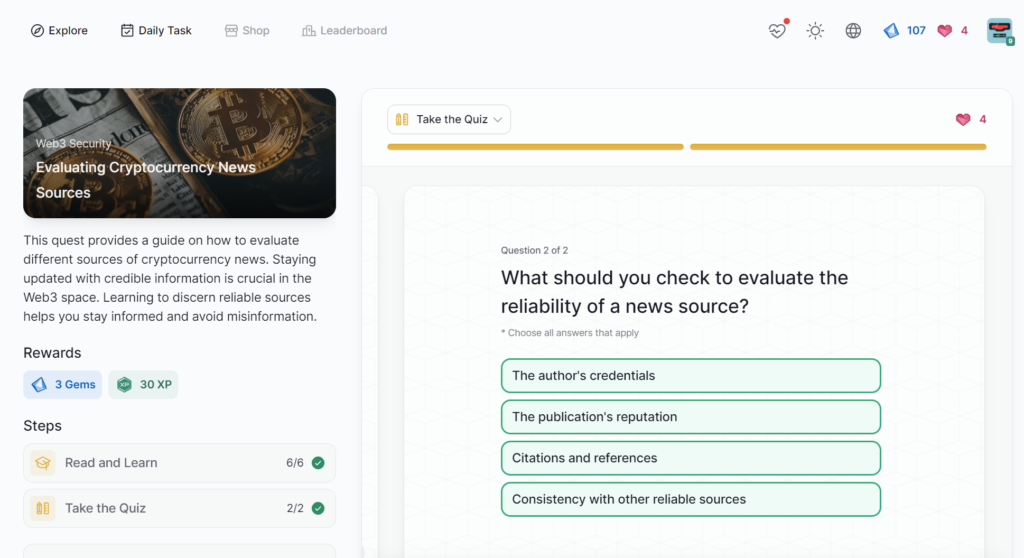
- Evaluating Cryptocurrency News Sources
- Hackers Infiltrating Crypto Job Boards
- Setting Up a Security War Room
- What Is a Keylogger?
- Understanding and Preventing Sybil Attacks
- Cold Wallets
- How to Create and Maintain Secure Passwords
- Protecting Yourself from Discord Scams
- SIM Swap Attacks
- Understanding and Mitigating 51% Attacks
- Protecting Your PostgreSQL Database from Cryptojacking
- SOC 2 Compliance for Crypto Companies
- Understanding Soft Rug vs. Hard Rug Pulls
- Case Study on Enhancing Security for App Chains
- DEXTools | Real-Time Trading Insights
- Understanding Economic Exploits and Tokenomics
- Intro to AML and its Role in Crypto
- Secure Use of Exchanges
- Understanding the Peel Chain Technique
- Navigating NFT Security and Avoiding Scams
- Protecting Against Social Engineering Attacks
- Exploring Etherscan
- Understanding Chain Hopping and Crypto Money Laundering
- How the DHS is Stopping Ransomware Attacks
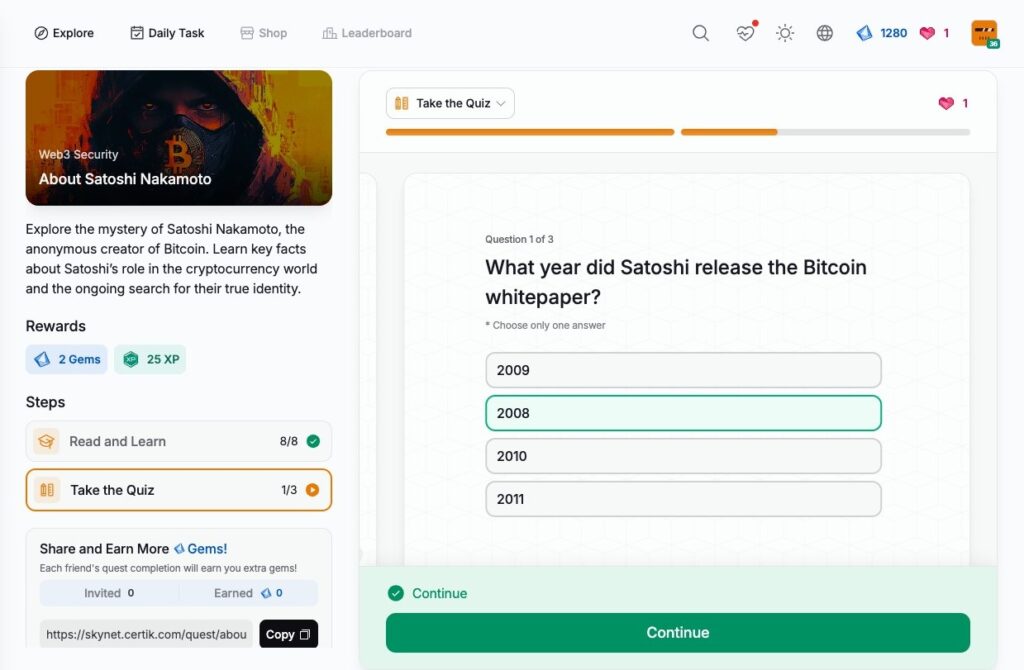
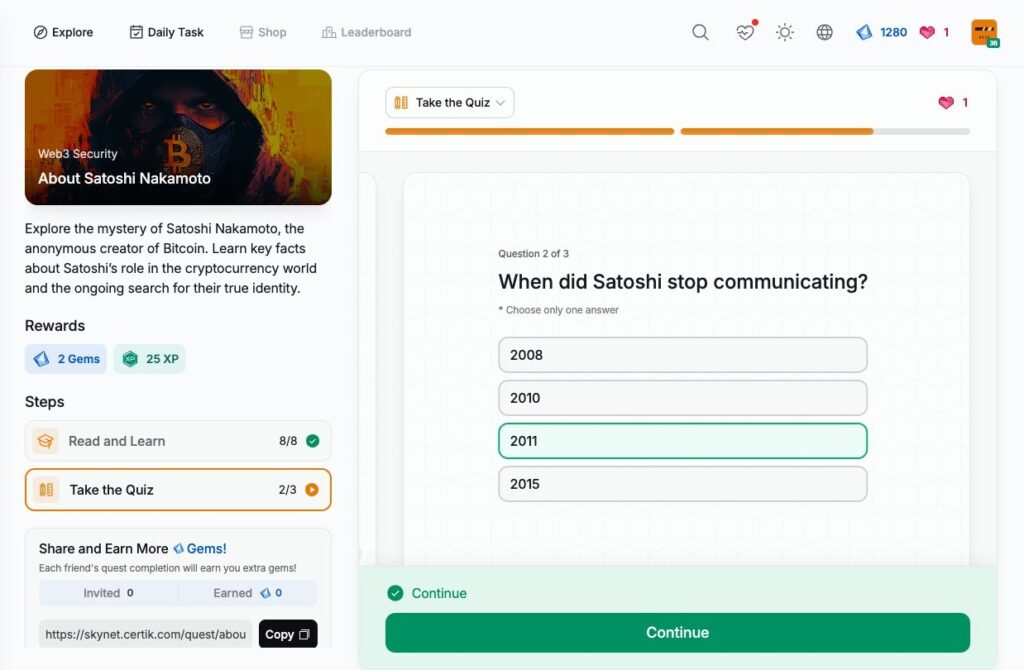
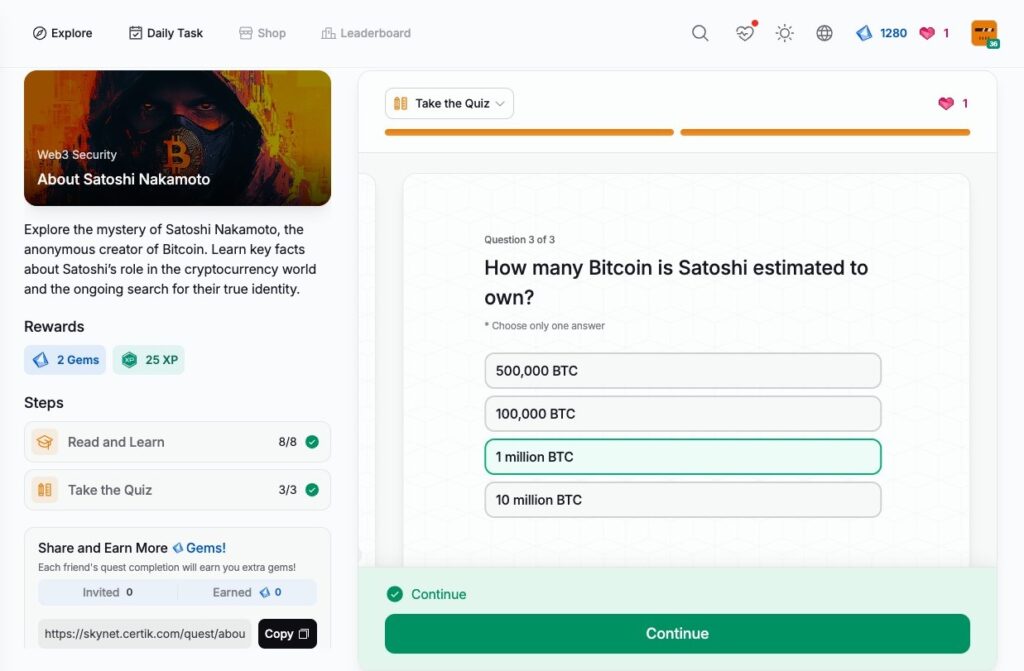
- About Satoshi Nakamoto
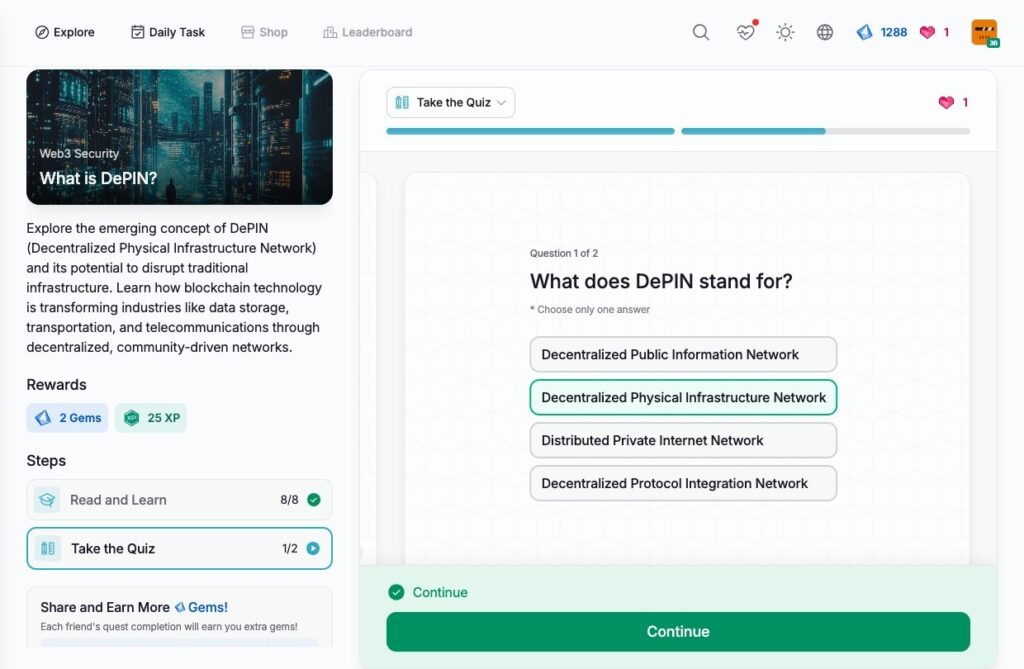
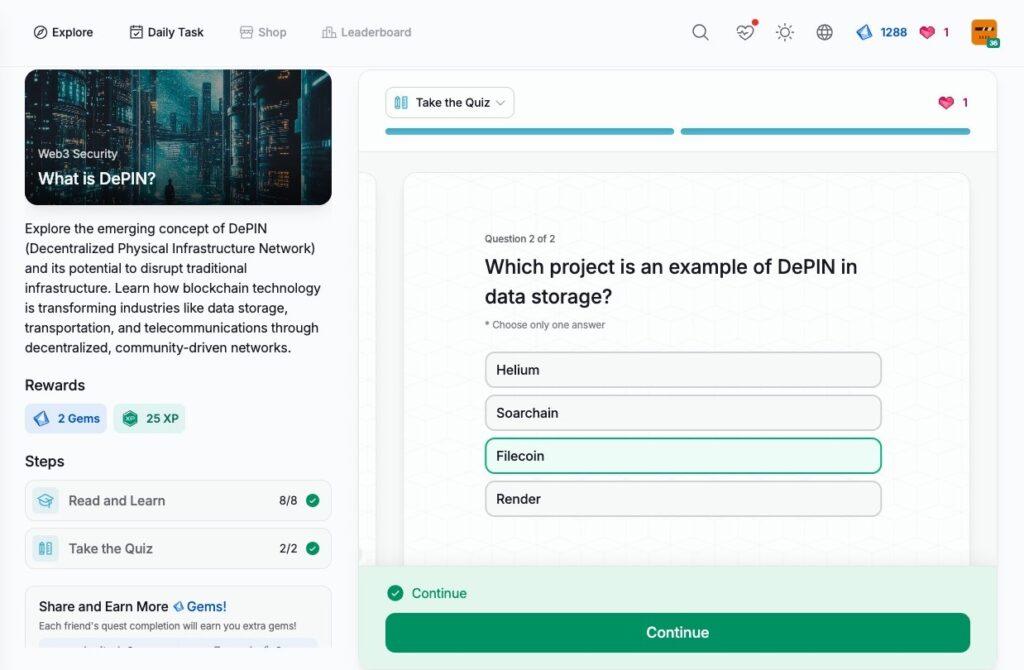
- What is DePIN?
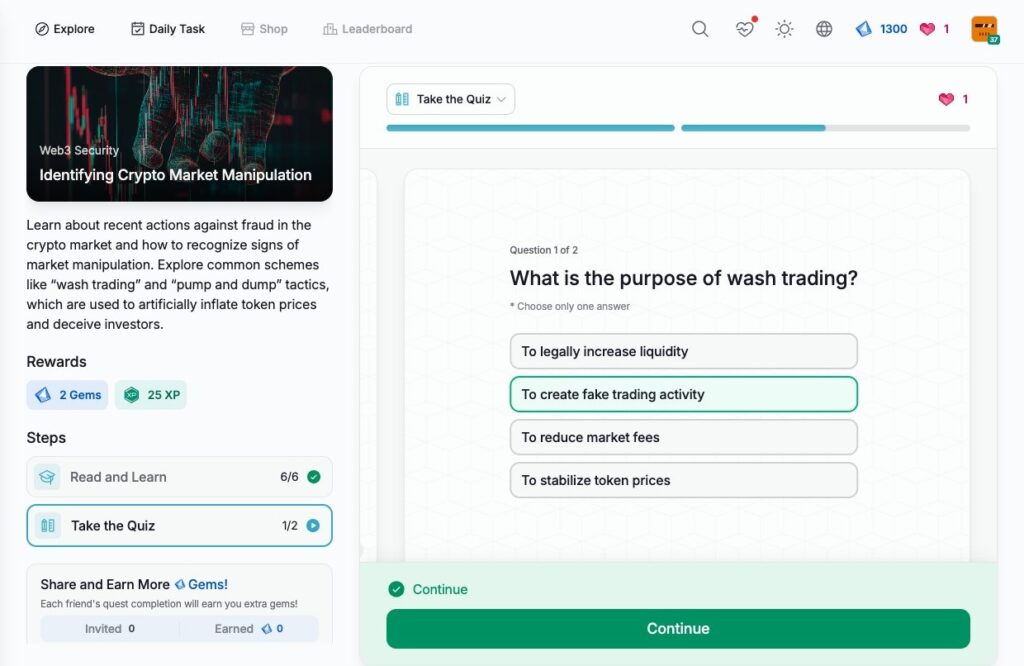
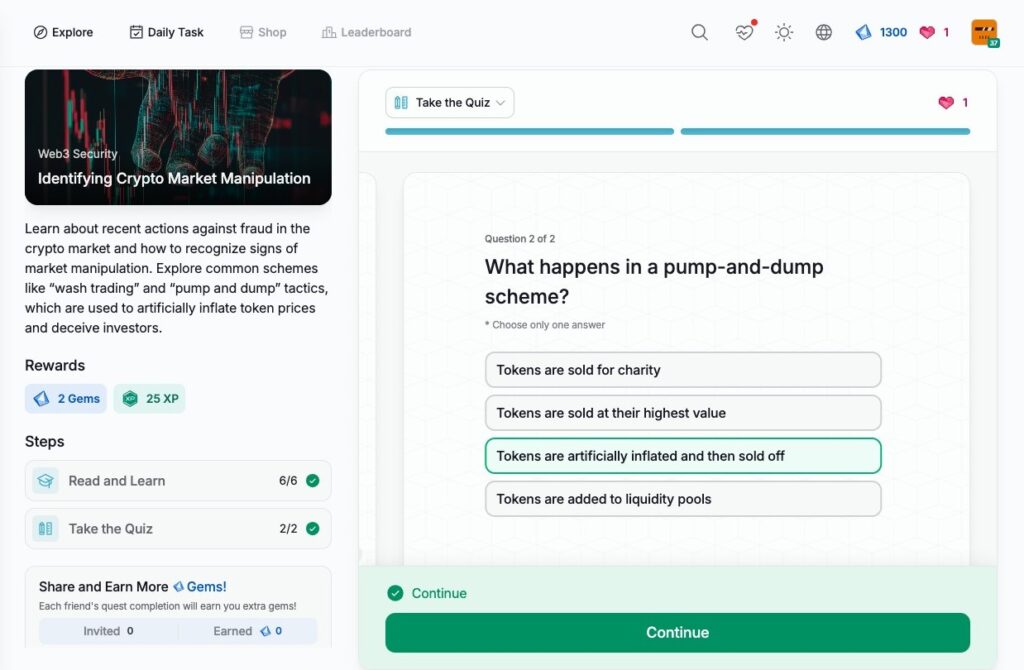
- Identifying Crypto Market Manipulation
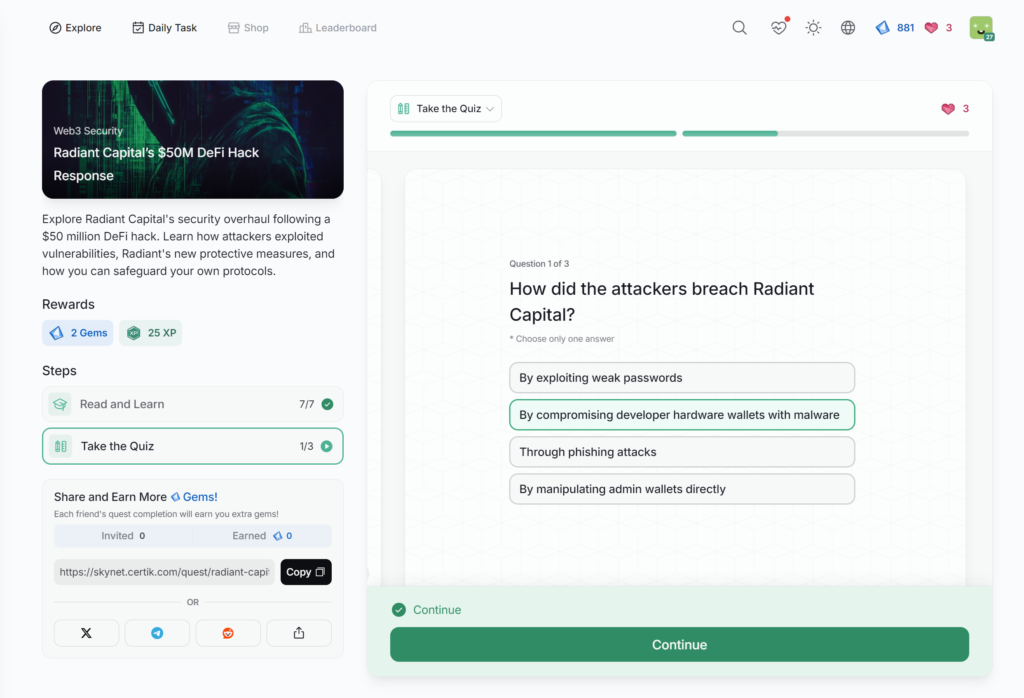
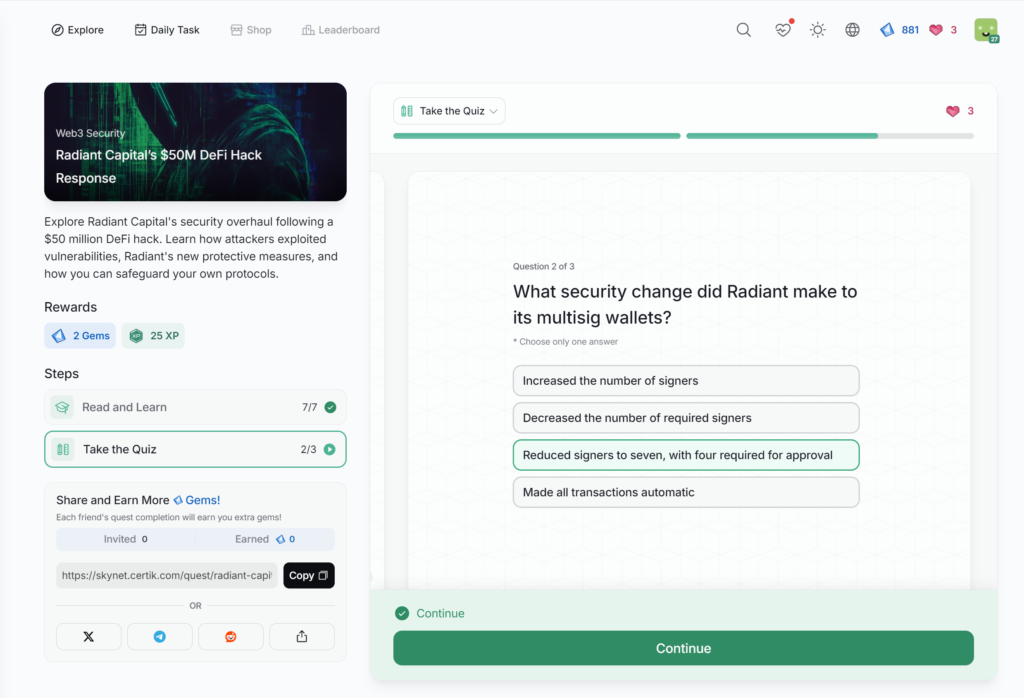
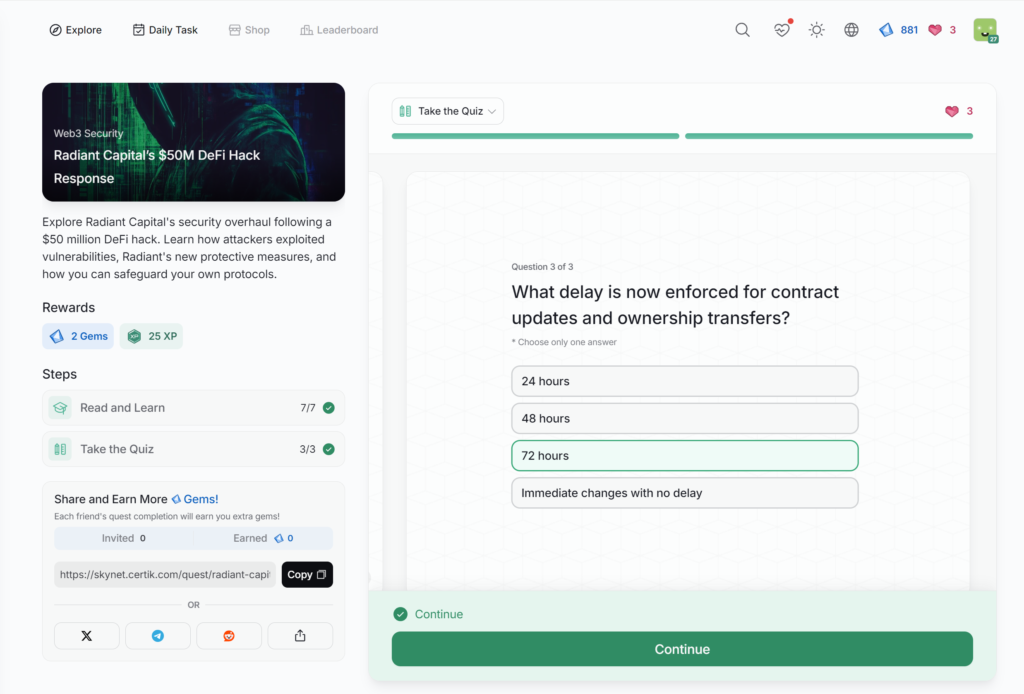
- Radiant Capital’s M DeFi Hack Response
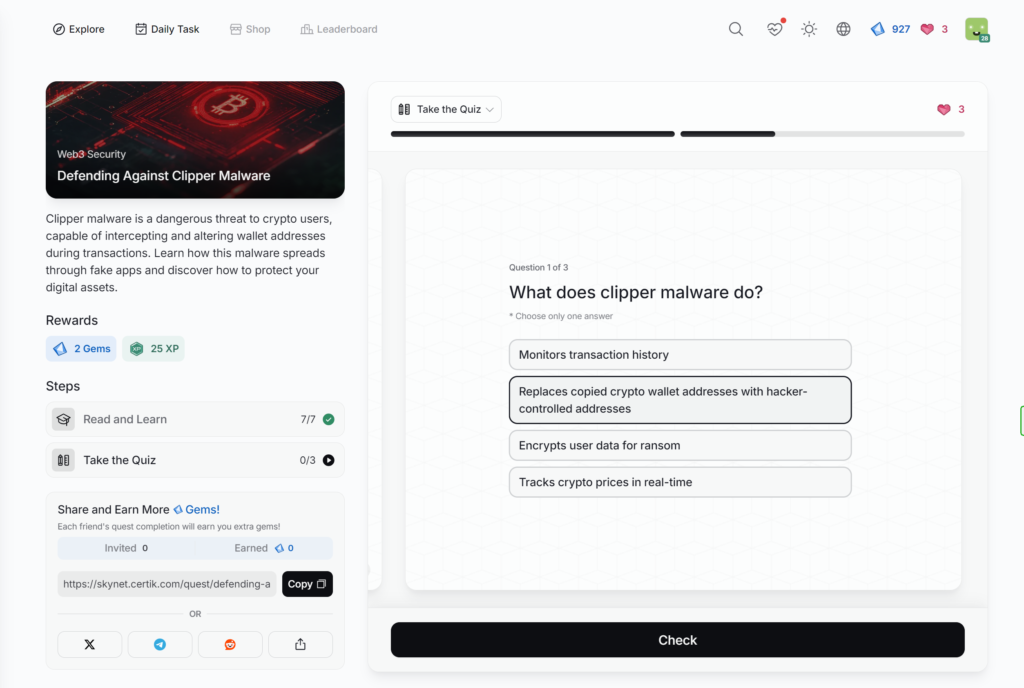
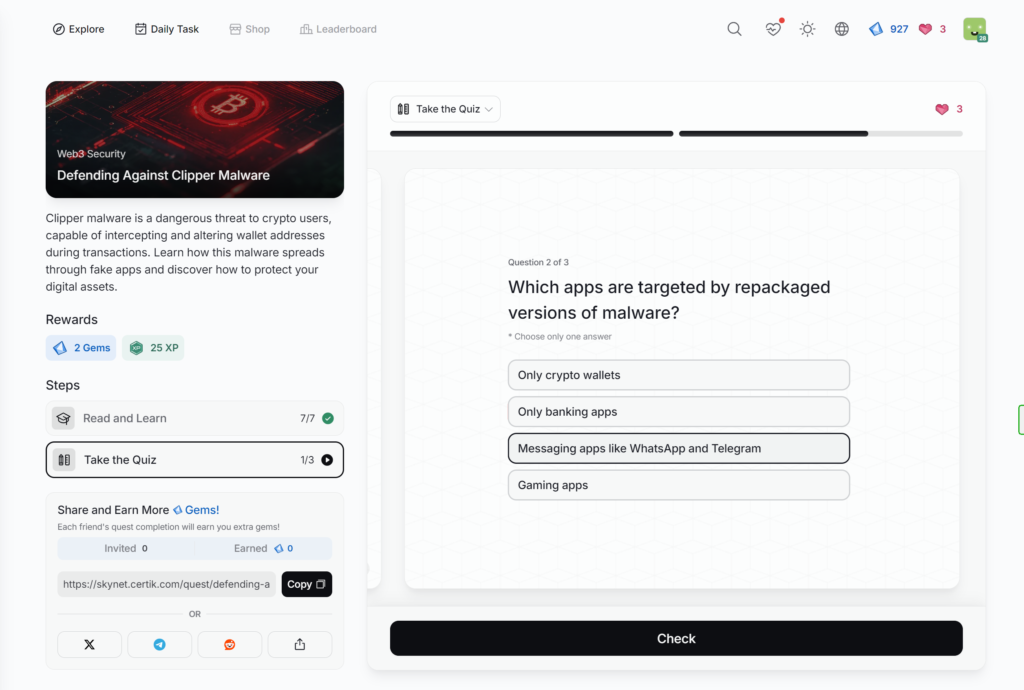
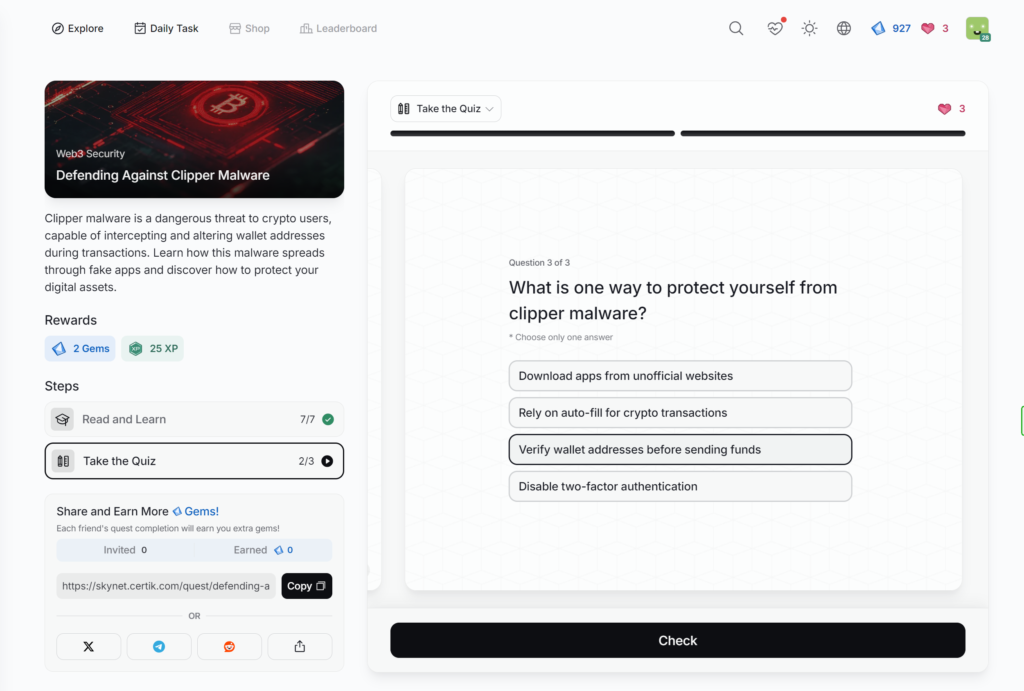
- Defending Against Clipper Malware
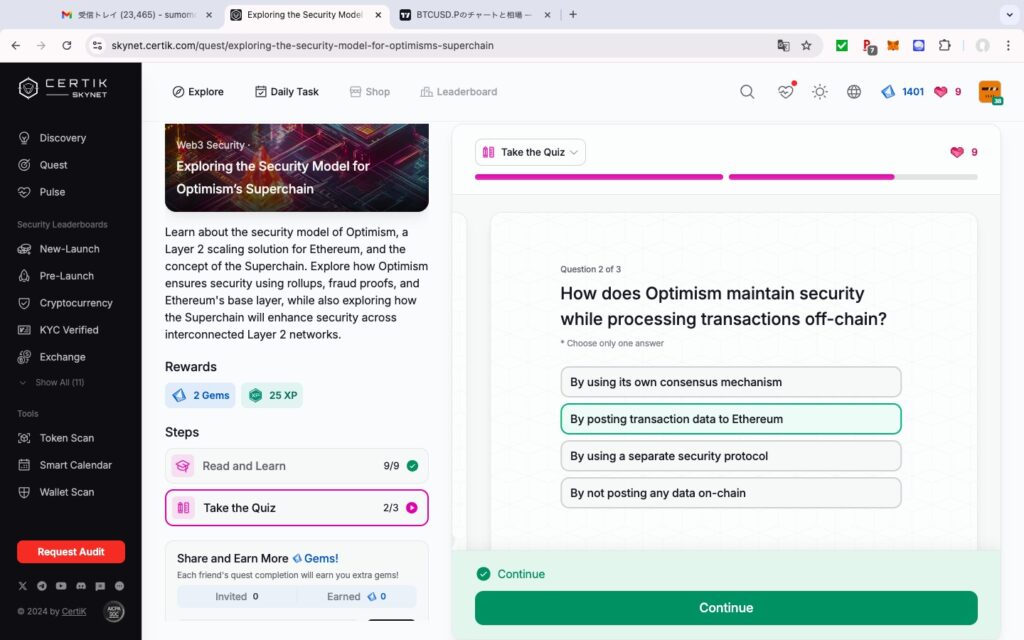
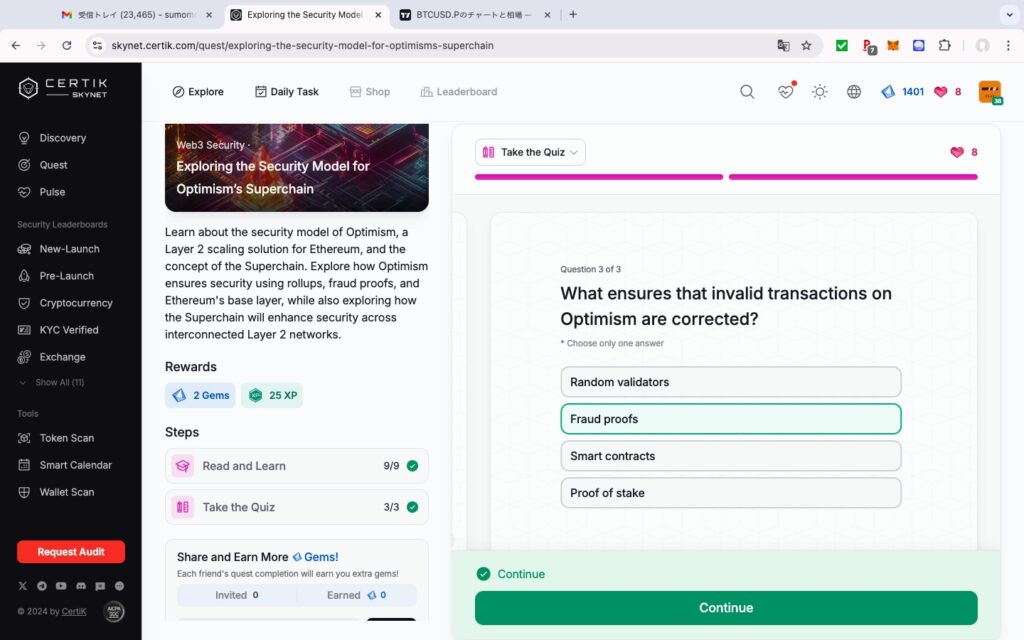
- Exploring the Security Model for Optimism’s Superchain
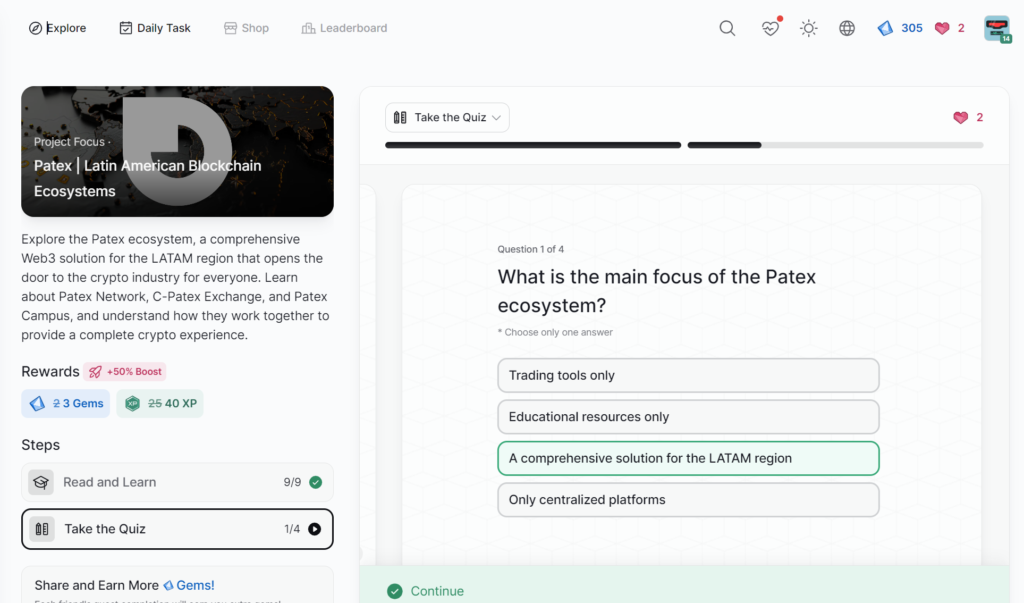
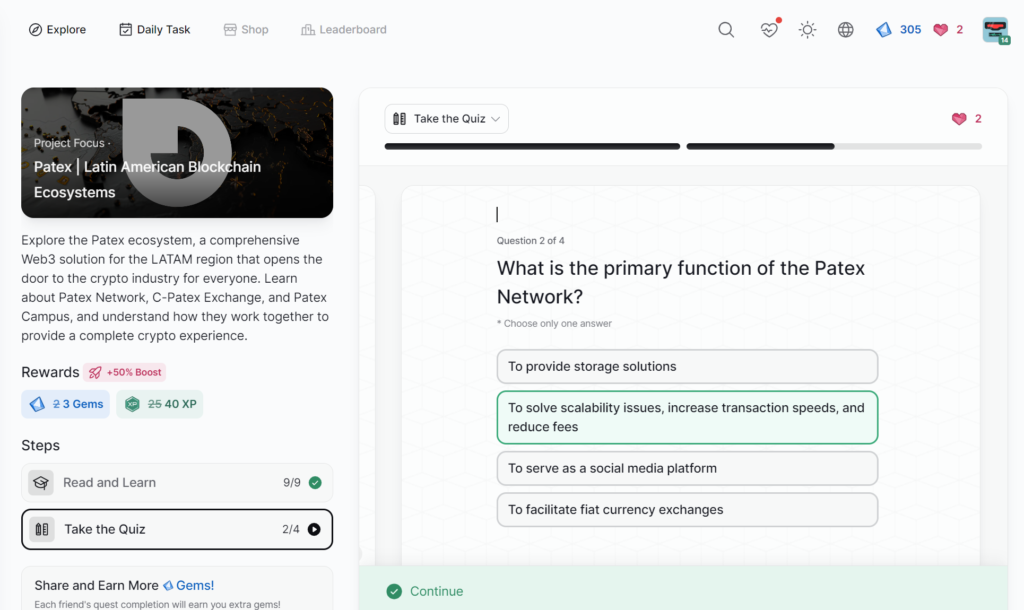
- Patex | Latin American Blockchain Ecosystems
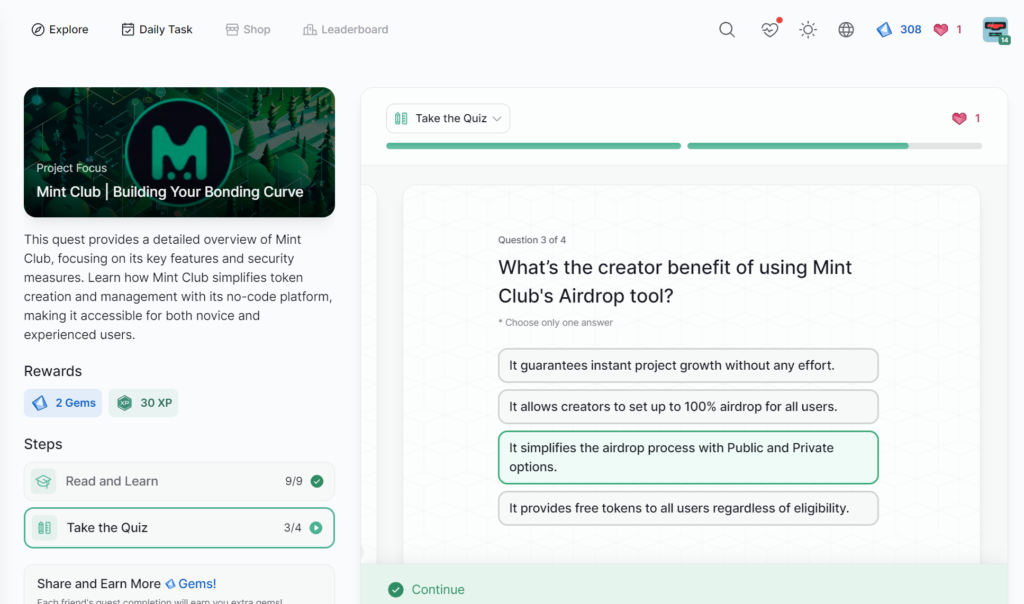
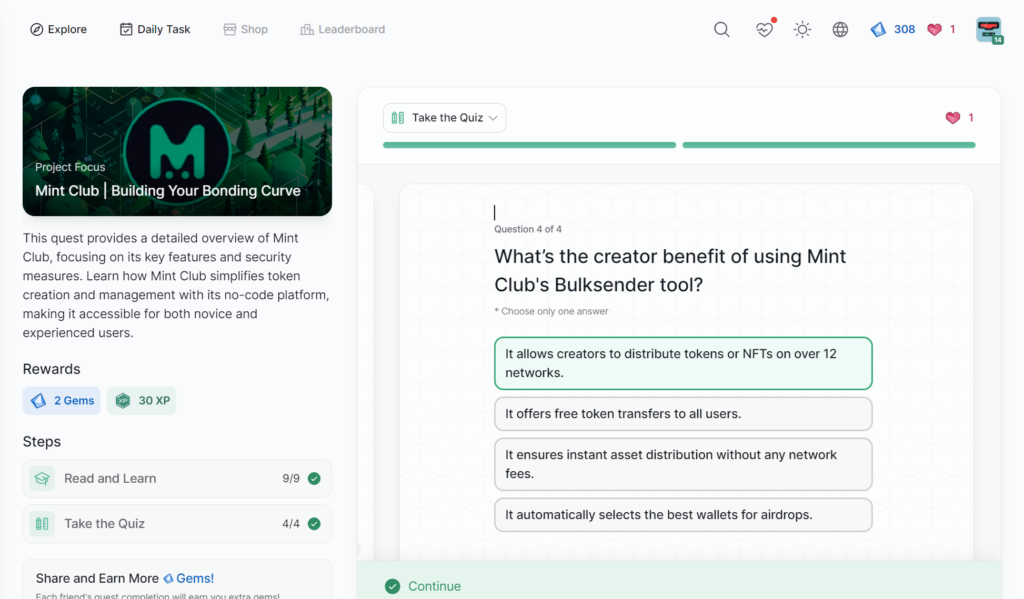
- Mint Club | Building Your Bonding Curve
- OpenGPU | Harnessing Decentralized GPU Computing
- HanChain | Transforming Music Copyright
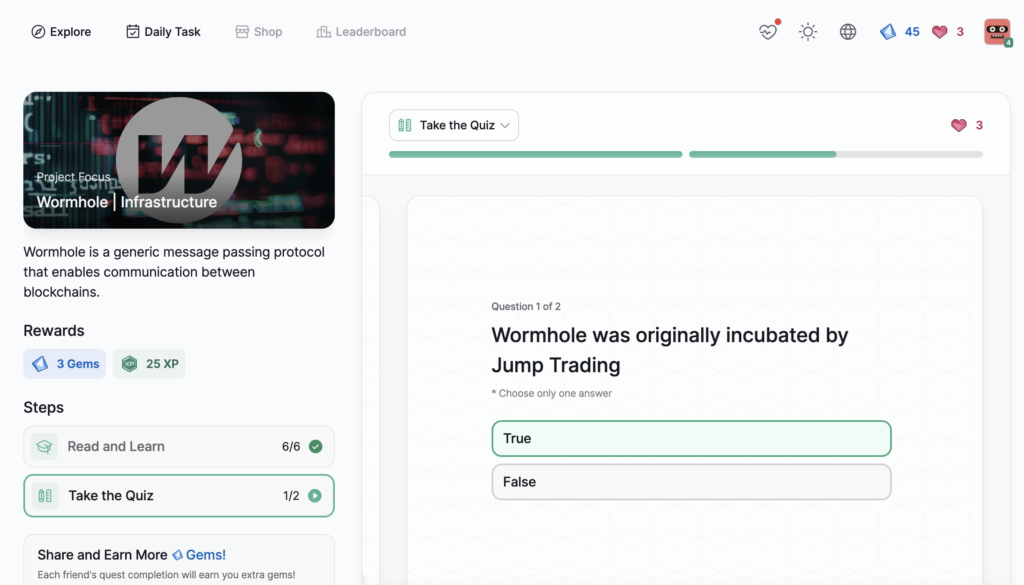
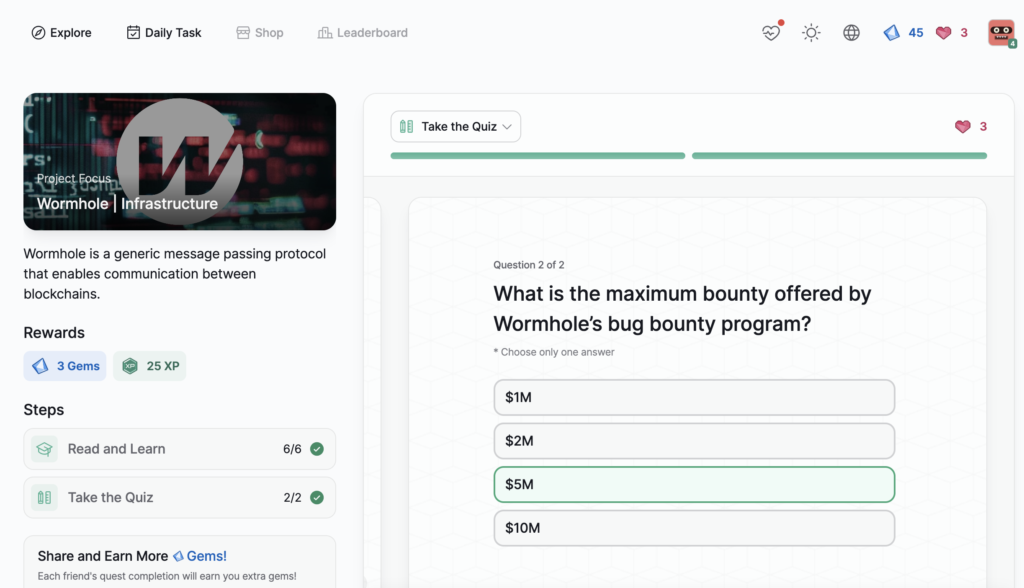
- Wormhole | Infrastructure
- Worldcoin | Store of Value
- Trinique | RAT
- Ripple (XRP Ledger) | Layer 1
- PAW Chain | Ecosystem
- Ondo Finance | RWA
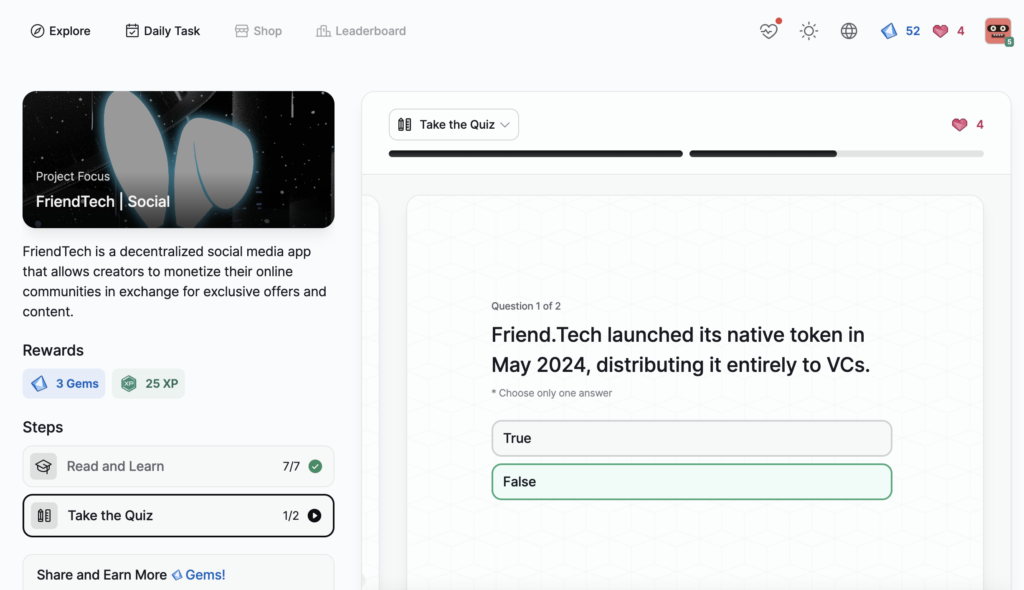
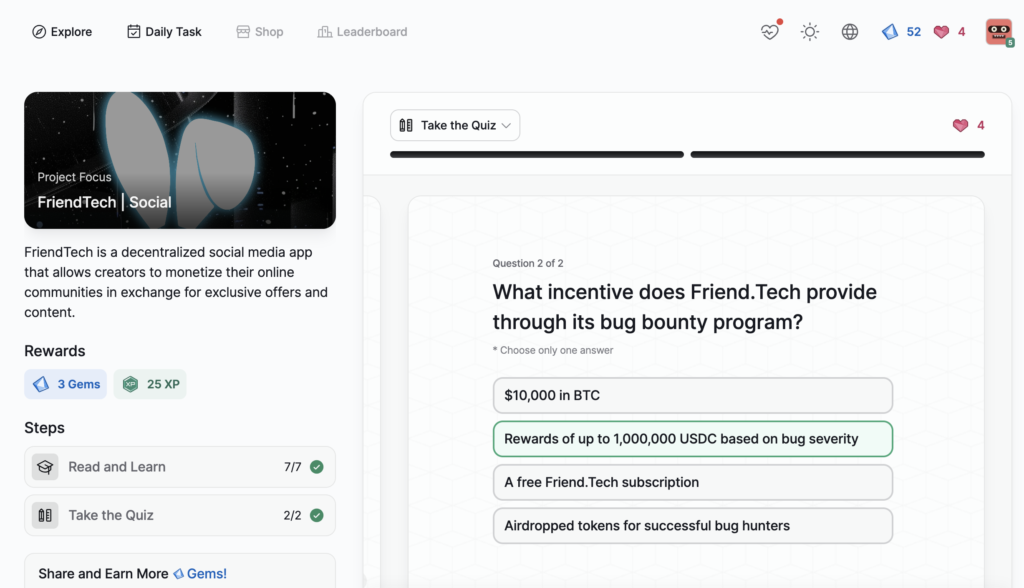
- FriendTech | Social
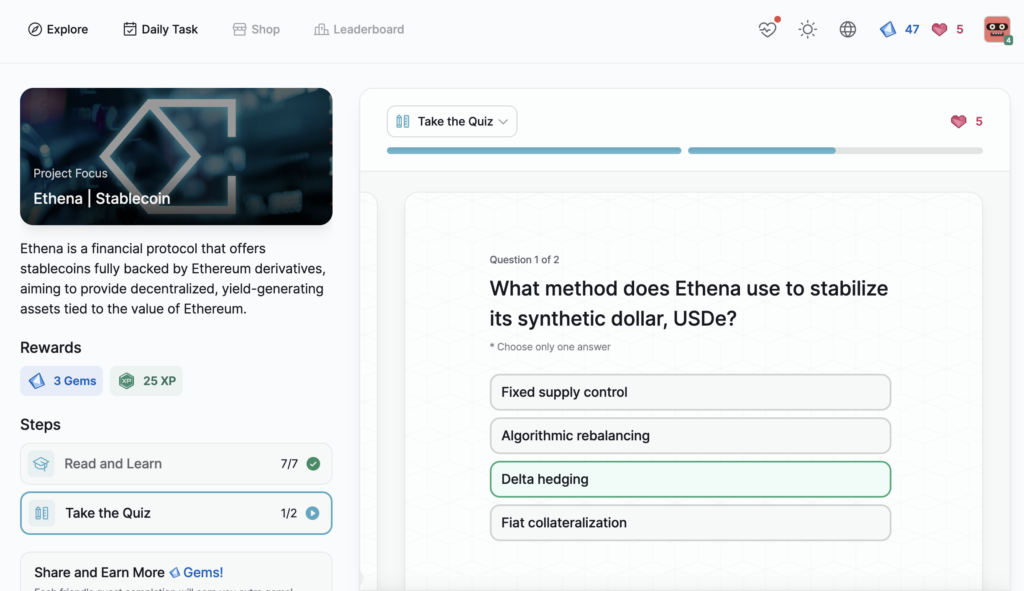
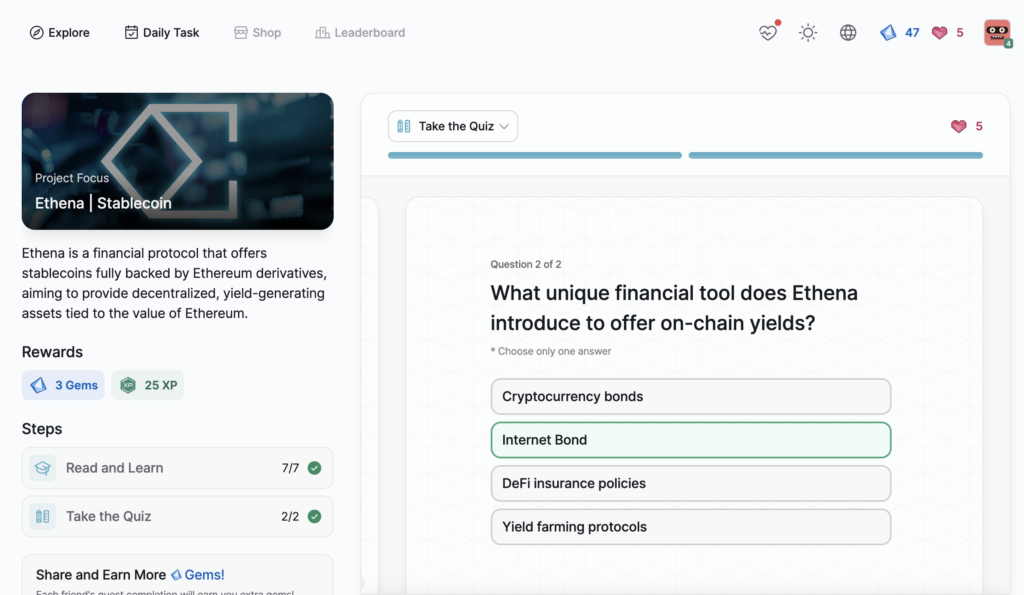
- Ethena | Stablecoin
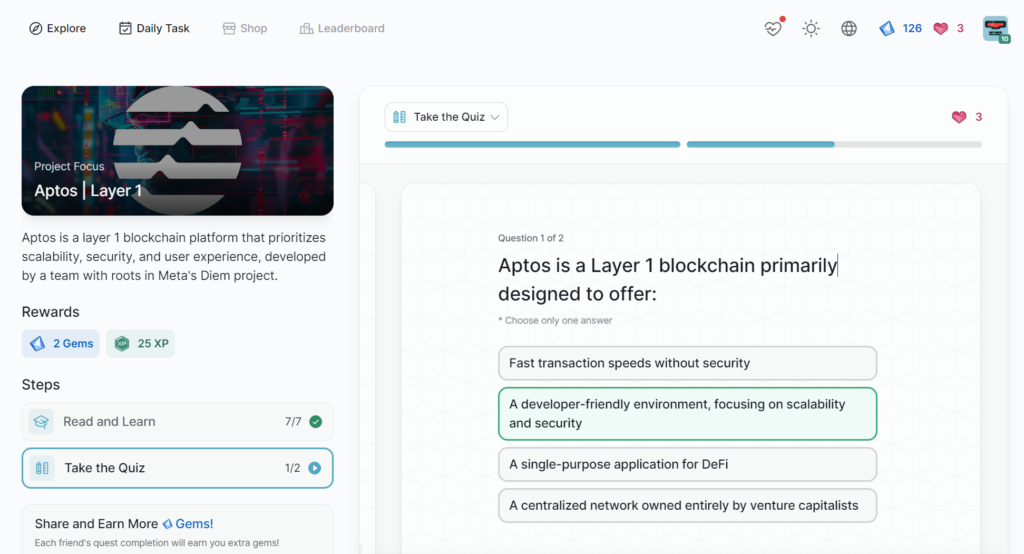
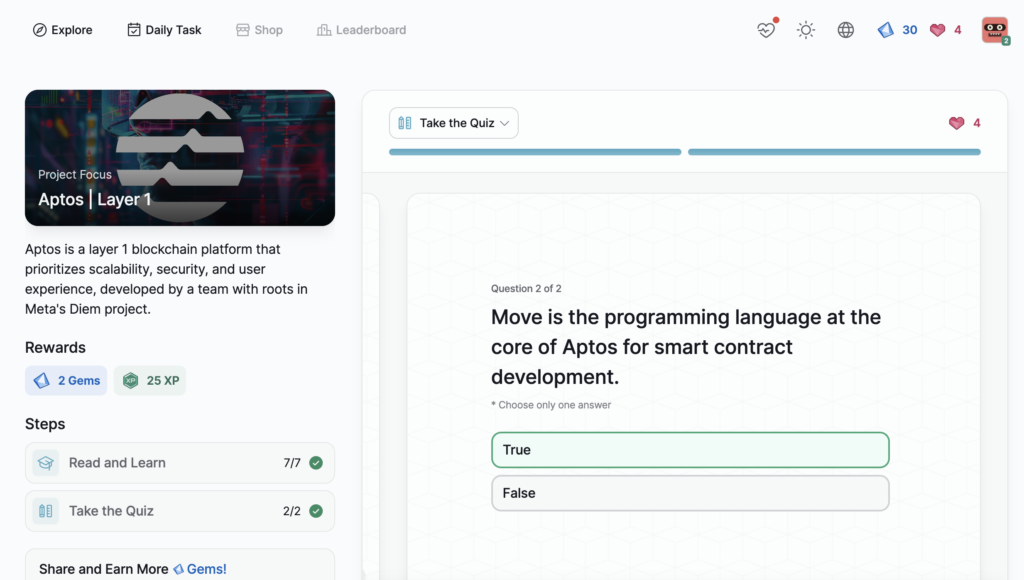
- Aptos | Layer 1
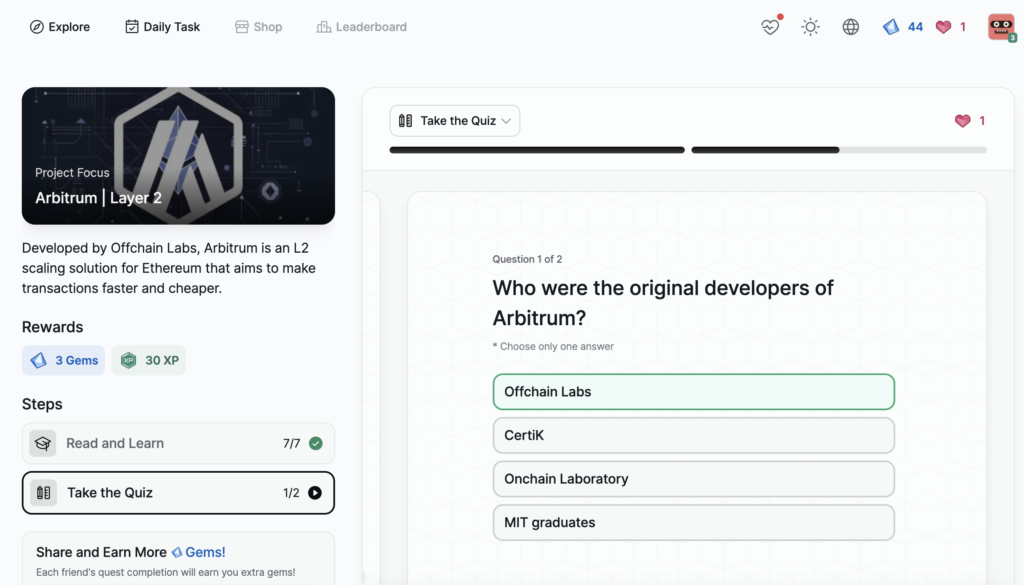
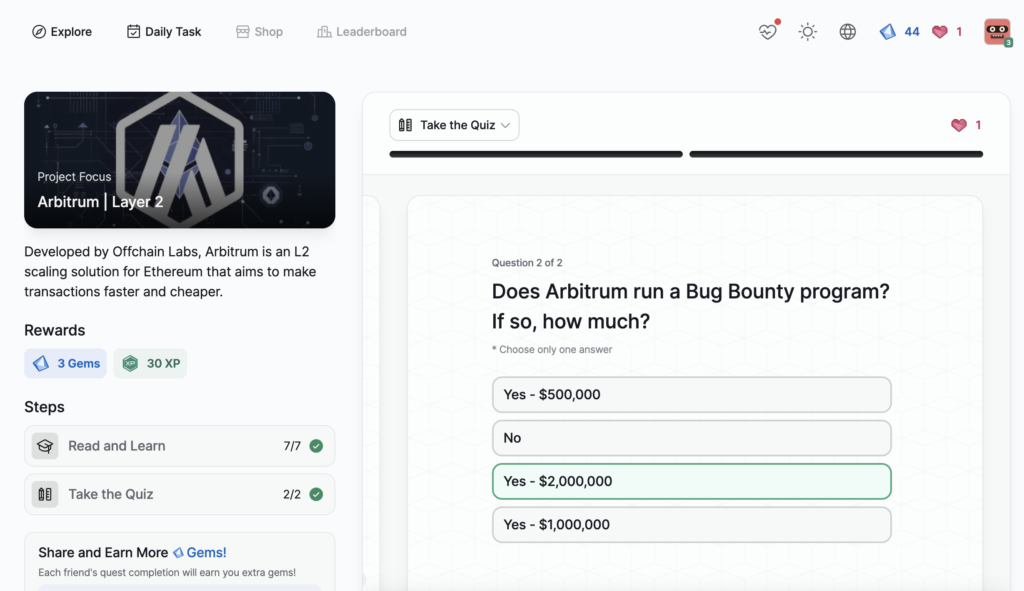
- Arbitrum | Layer 2
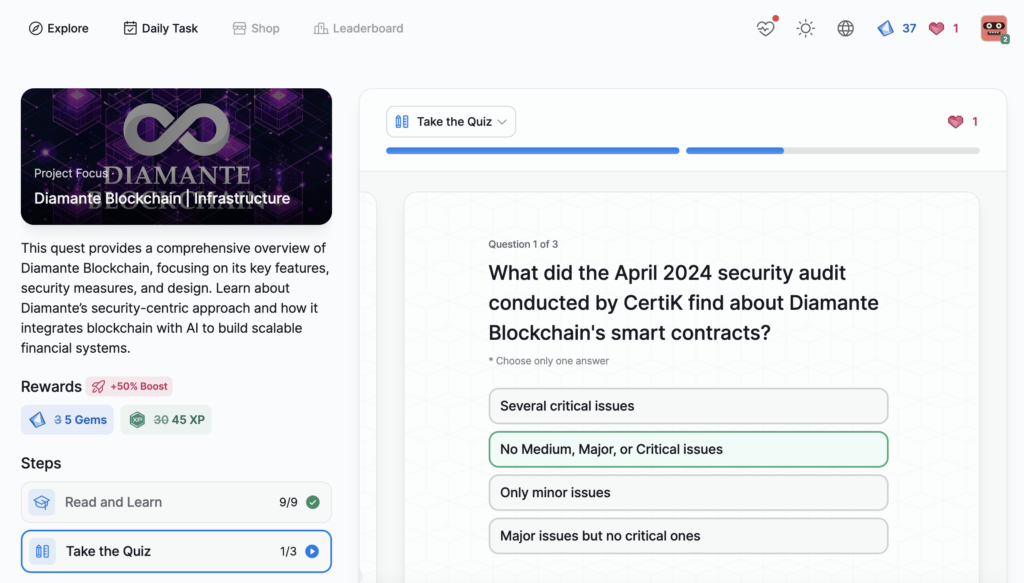
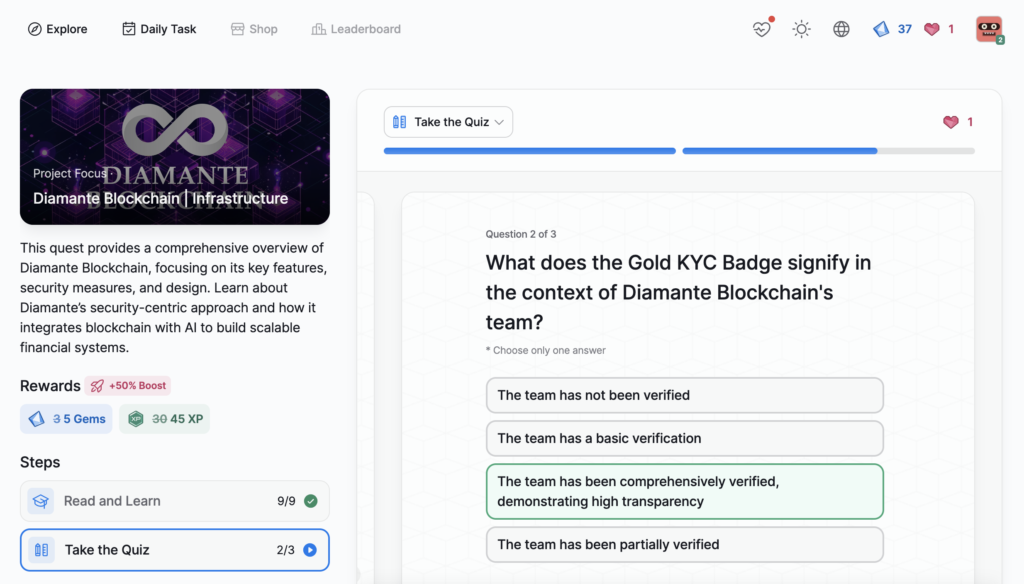
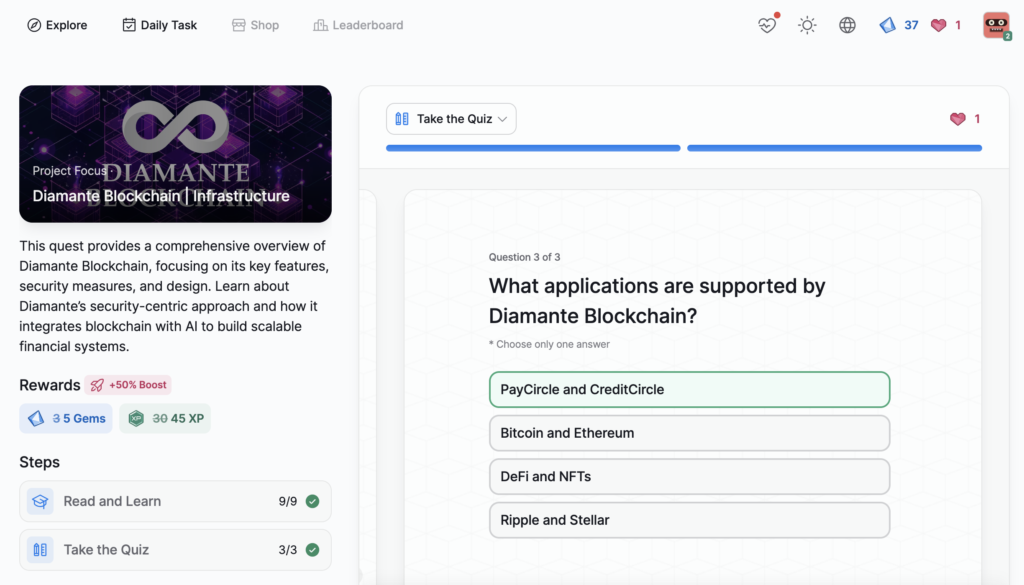
- Diamante Blockchain | Infrastructure
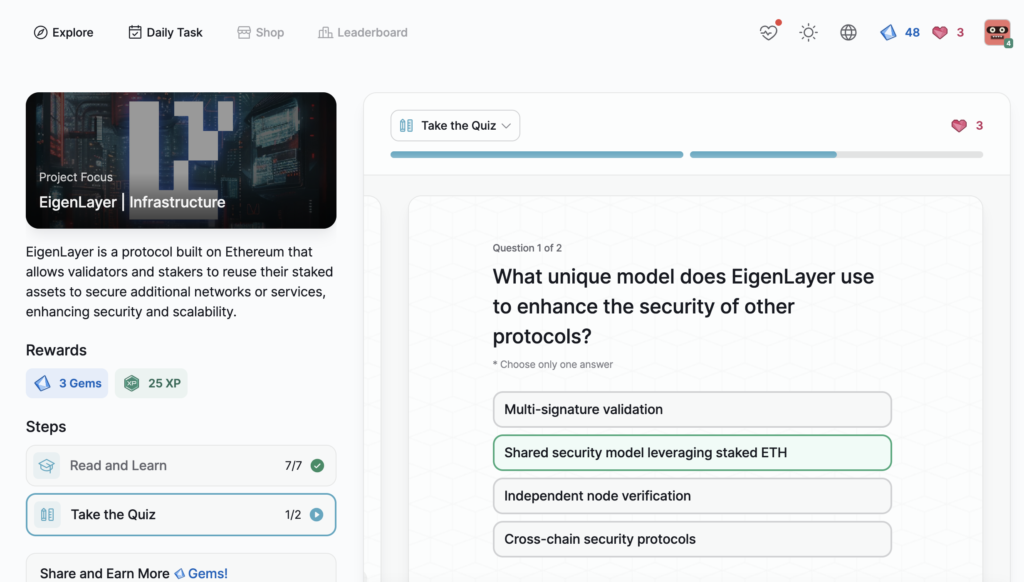
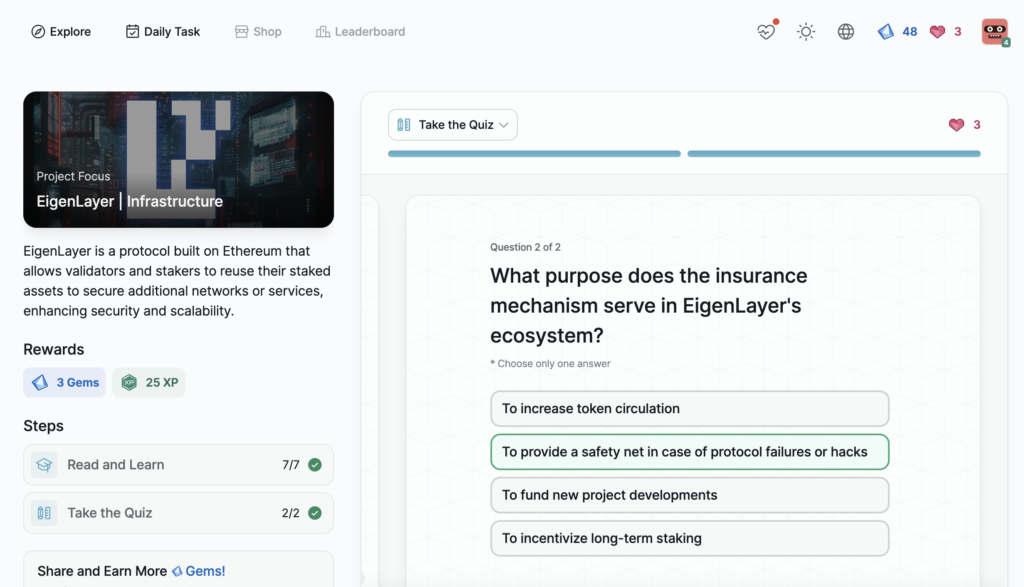
- EigenLayer | Infrastructure
- PEPE | Meme
- TON | Layer 1
- zkSwap Finance | DeFi
- Core DAO | Infrastructure
- Edu3Labs | The Future of Education
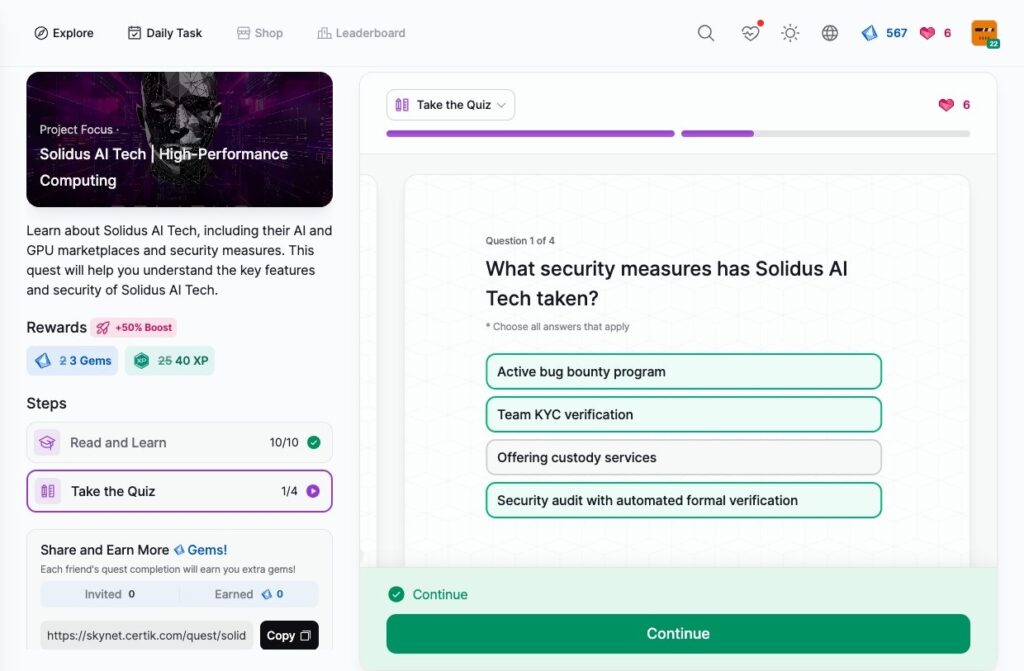
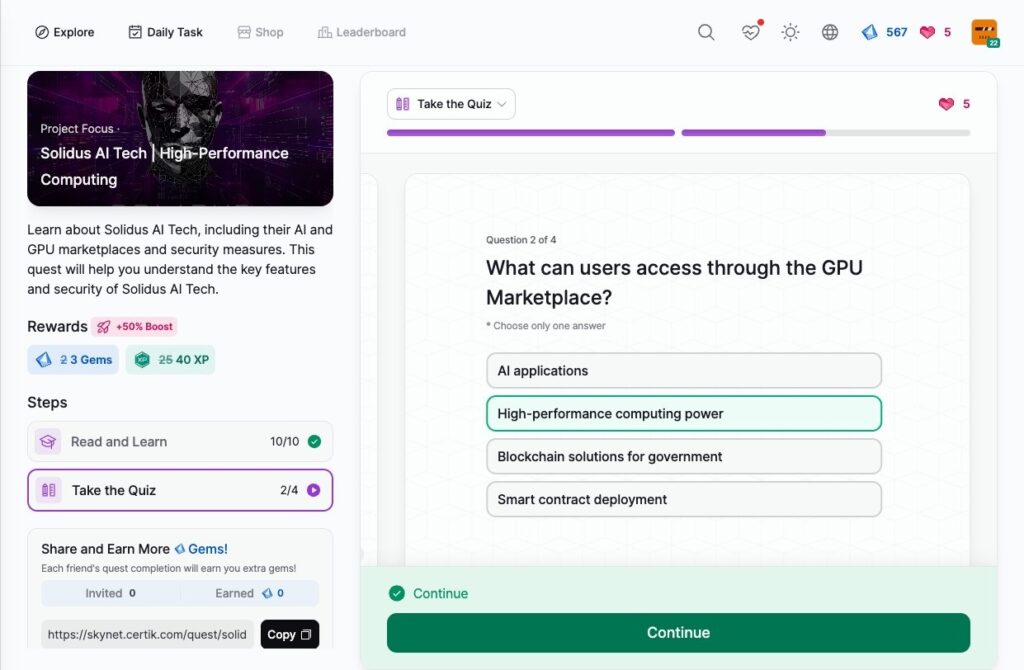
- Solidus AI Tech | High-Performance Computing
- Mintlayer | Build on Bitcoin
- Script Network | Open Source Video Protocol
- OKX Wallet | Multi-Chain Web3 Wallet
- Polymarket | Prediction Markets
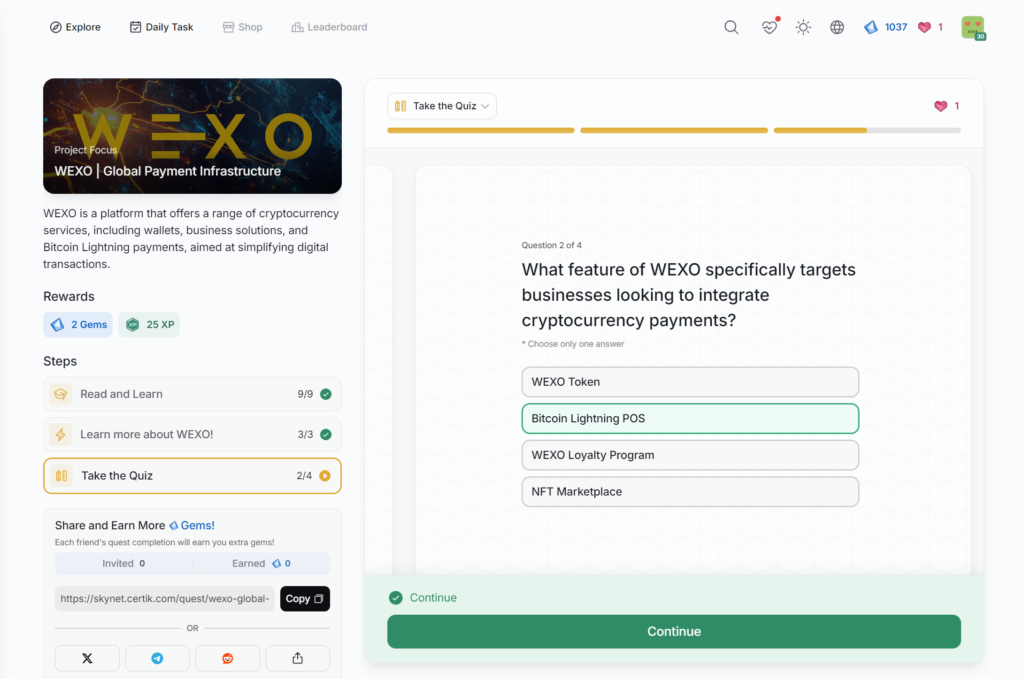
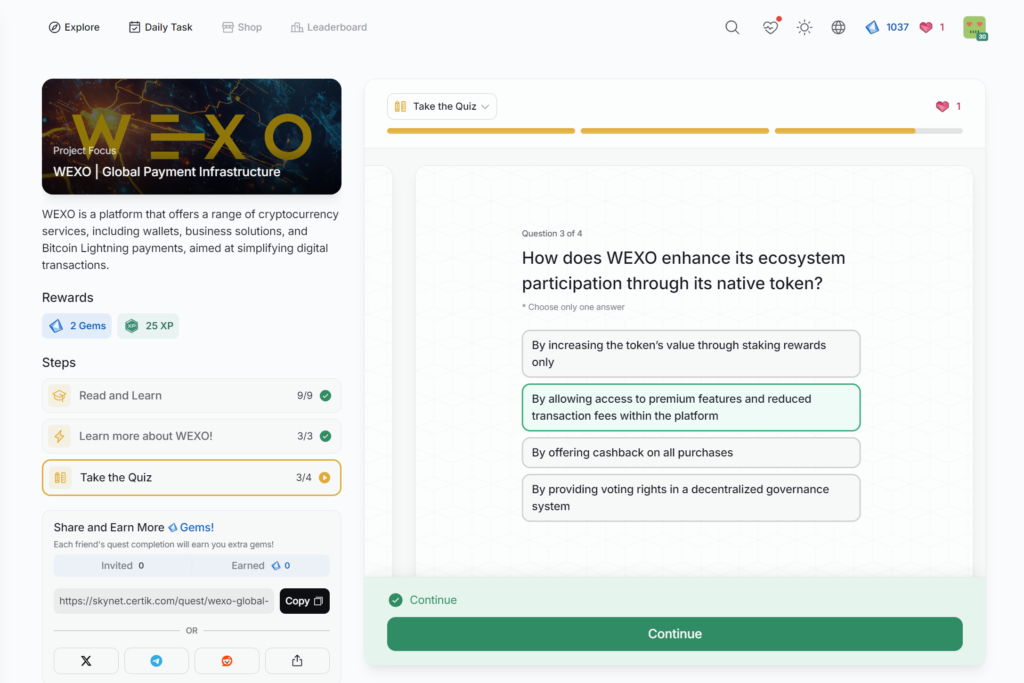
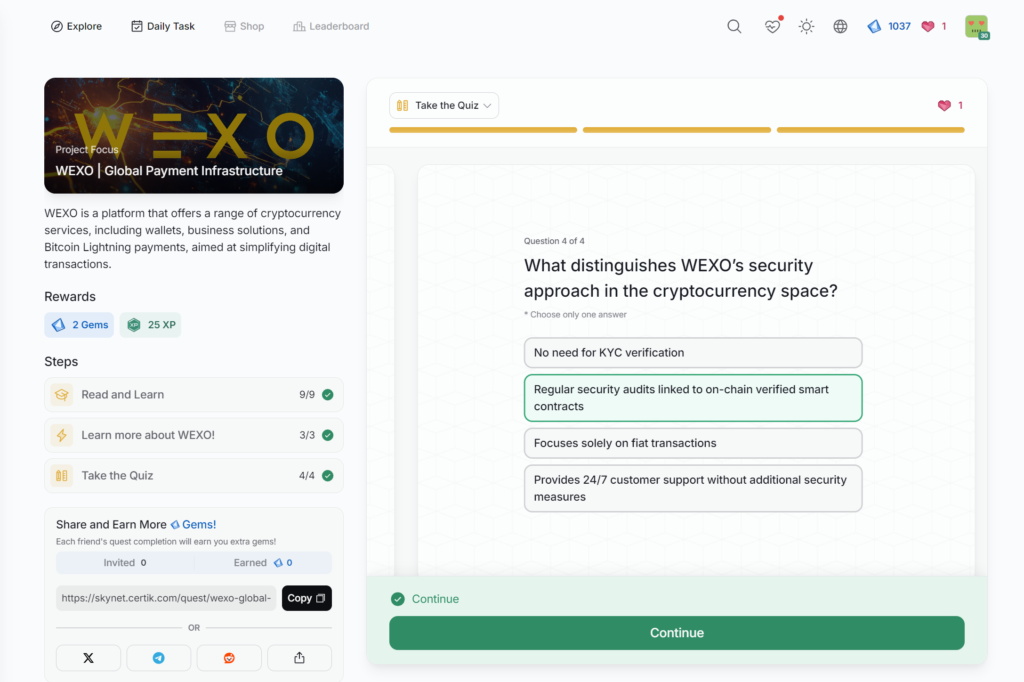
- WEXO | Global Payment Infrastructure
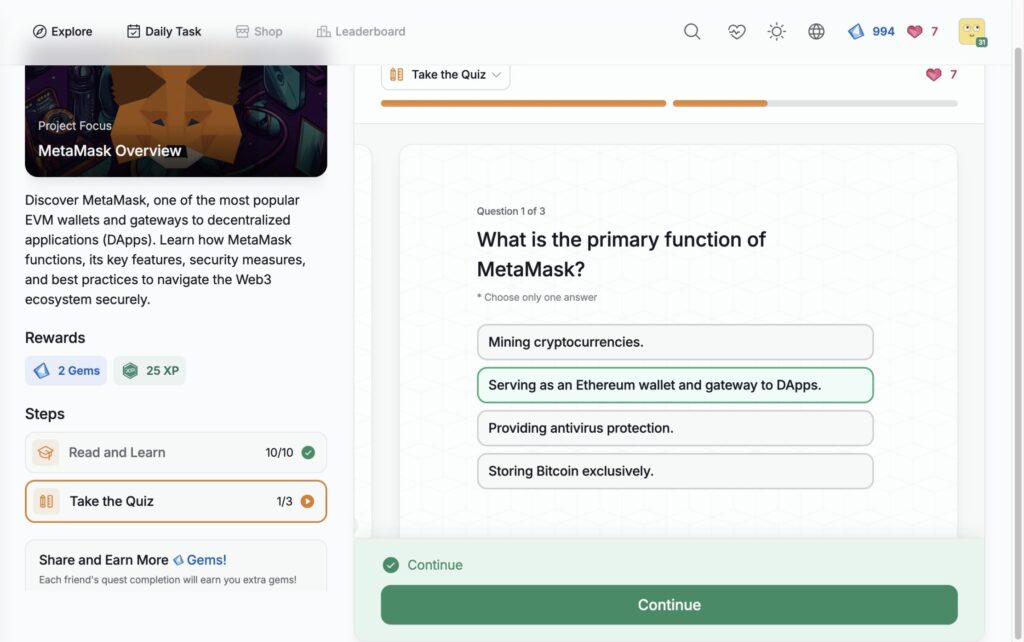
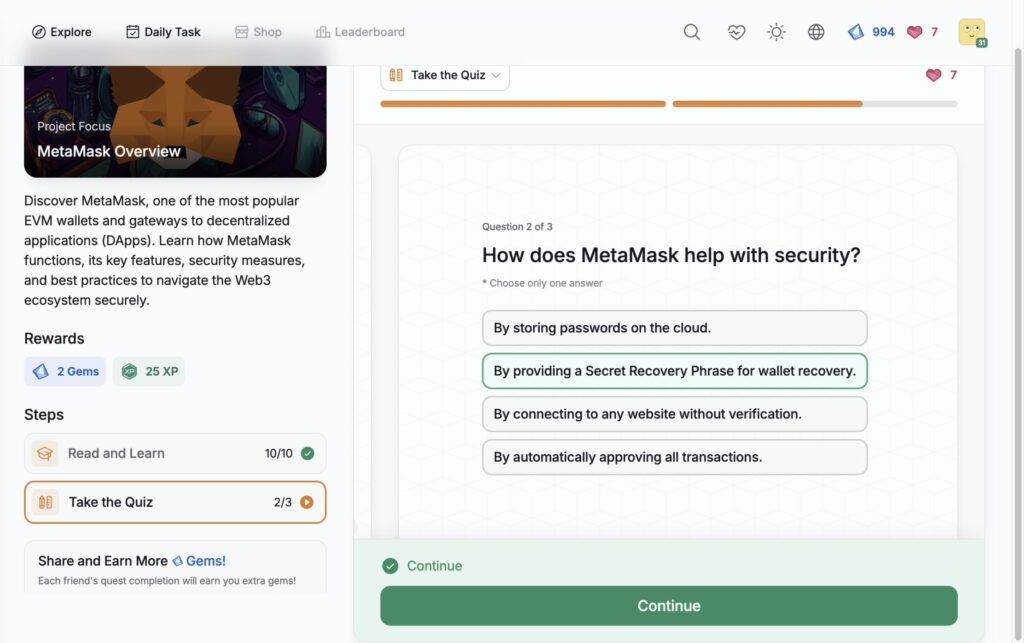
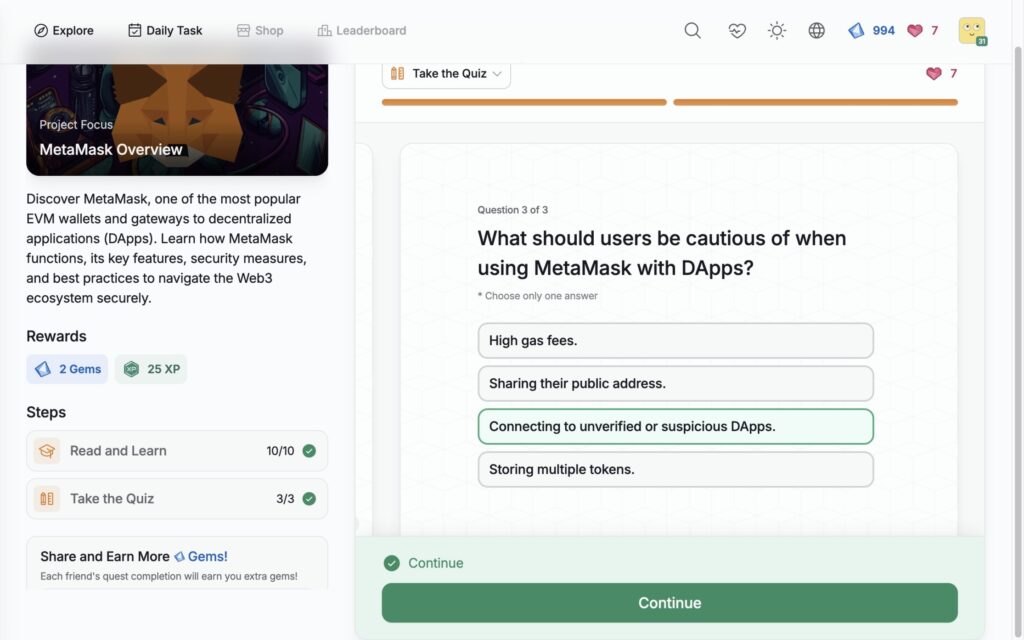
- MetaMask Overview
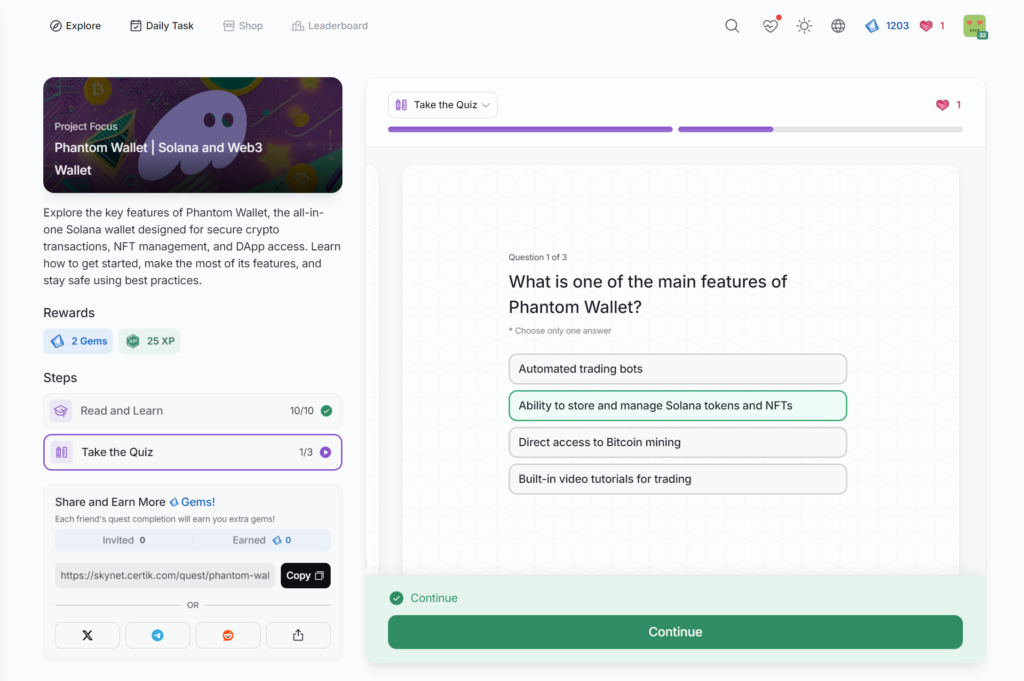
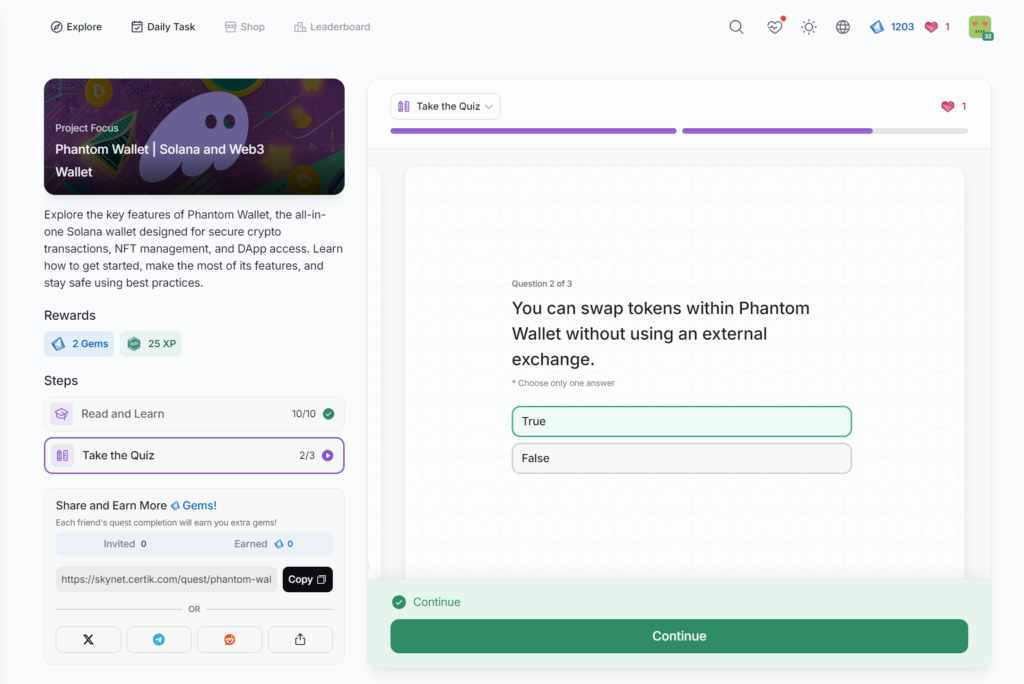
- Phantom Wallet | Solana and Web3 Wallet
- How Exit Scammers Mint Tokens Undetected
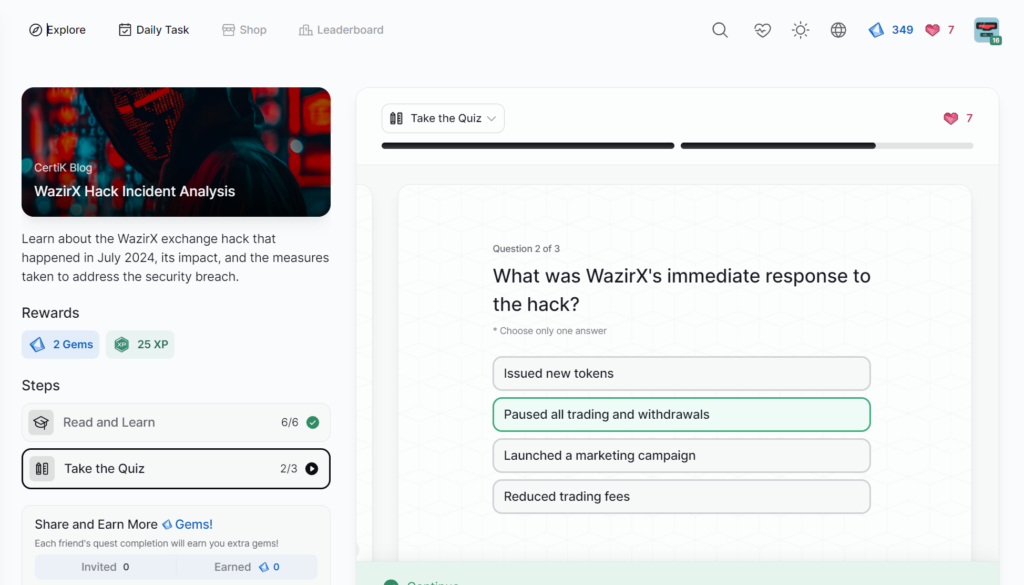
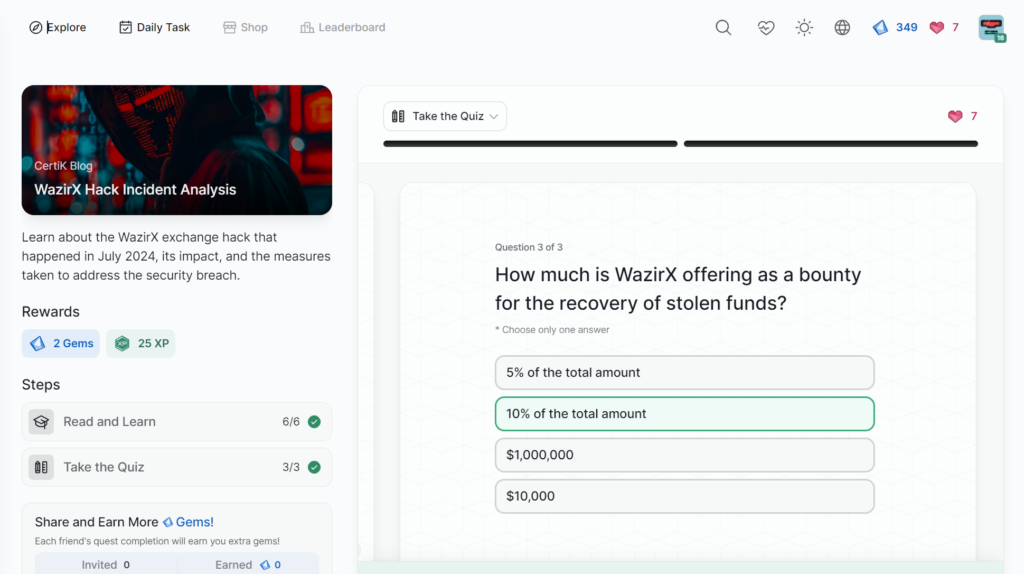
- WazirX Hack Incident Analysis
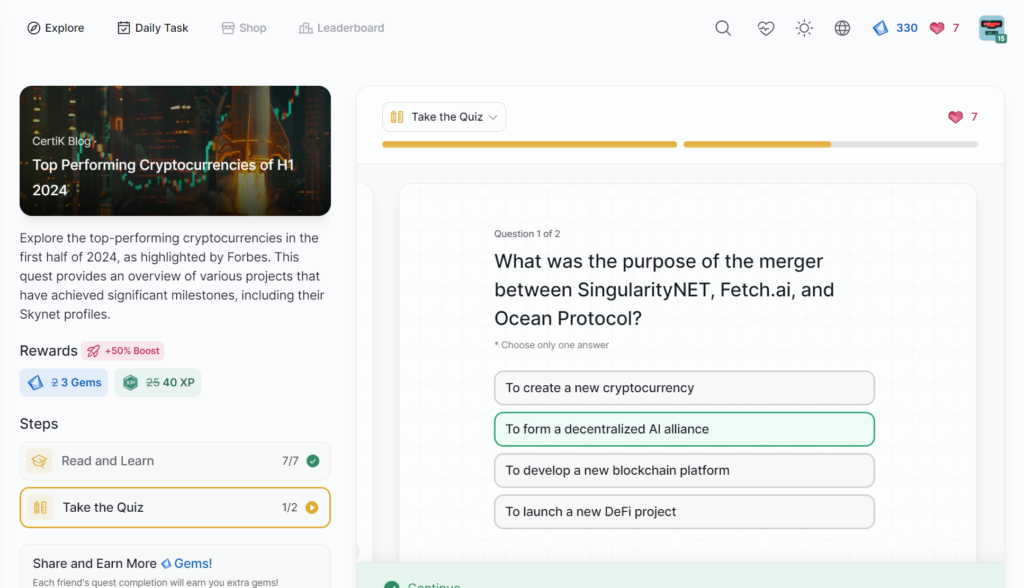
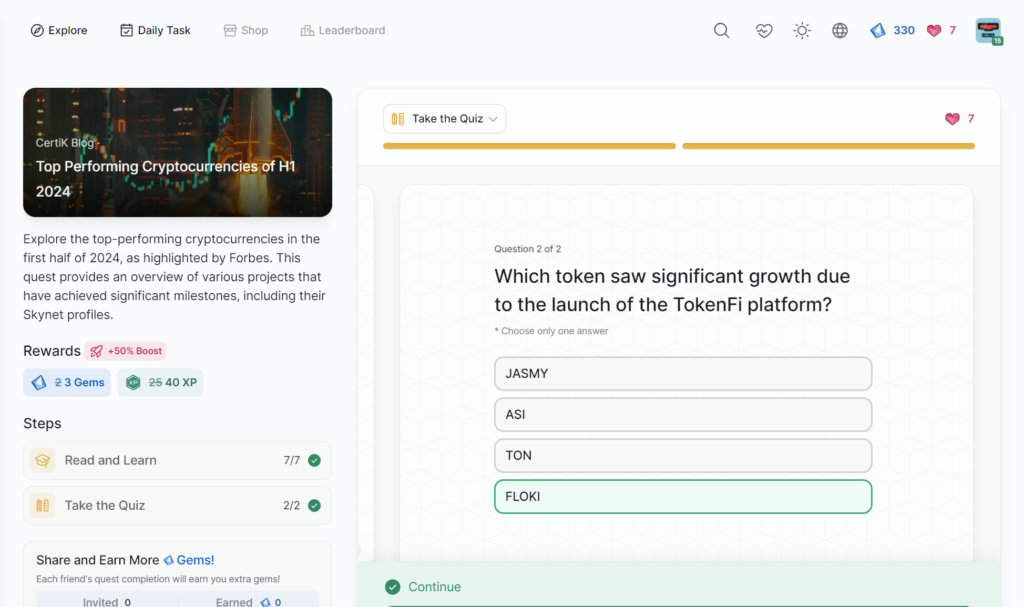
- Top Performing Cryptocurrencies of H1 2024
- Trap Phishing on Trusted Platforms
- Ordinals and the BRC-20 Standard
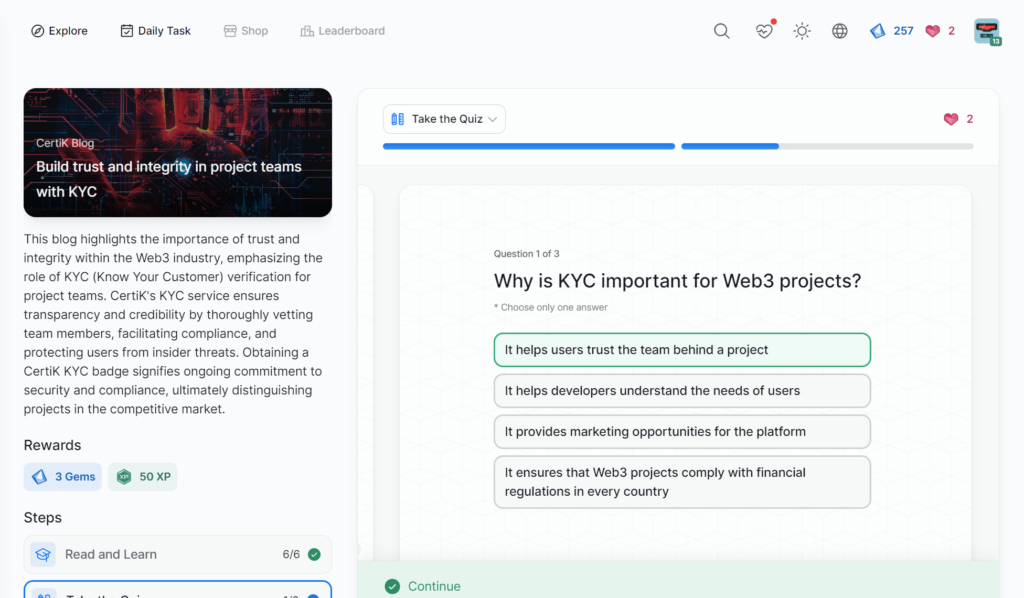
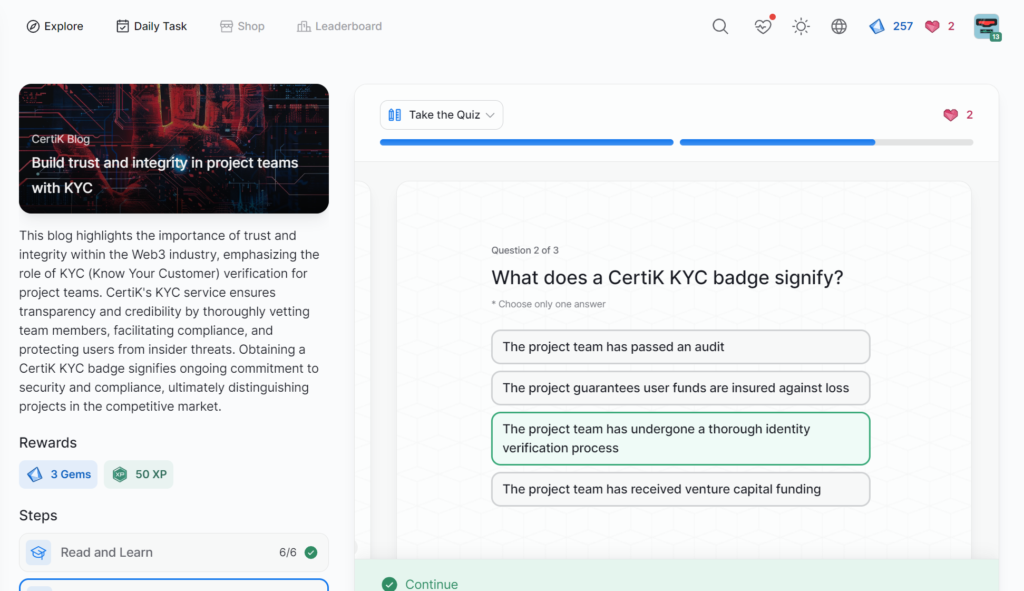
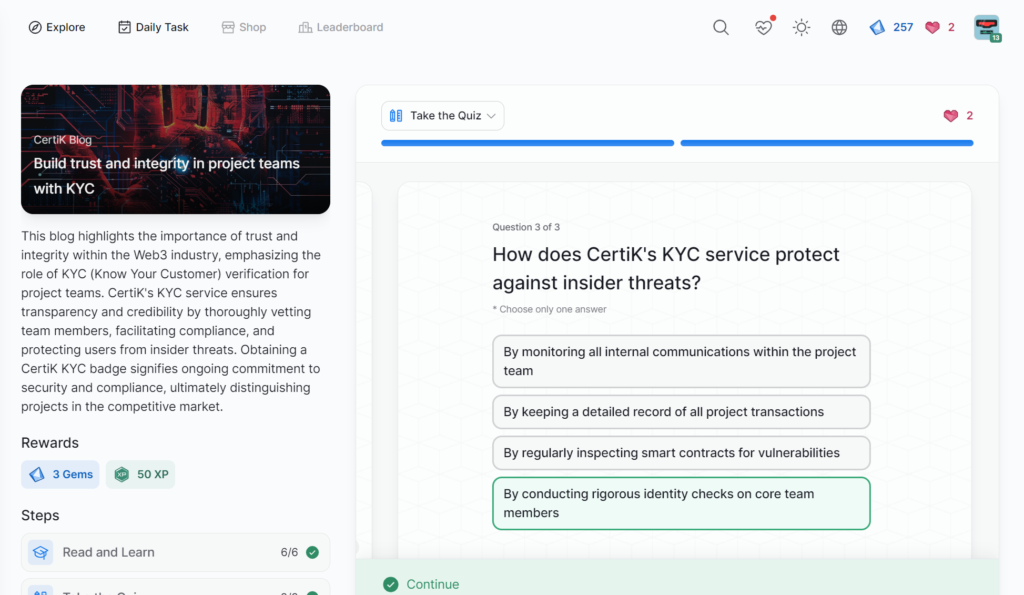
- Build trust and integrity in project teams with KYC
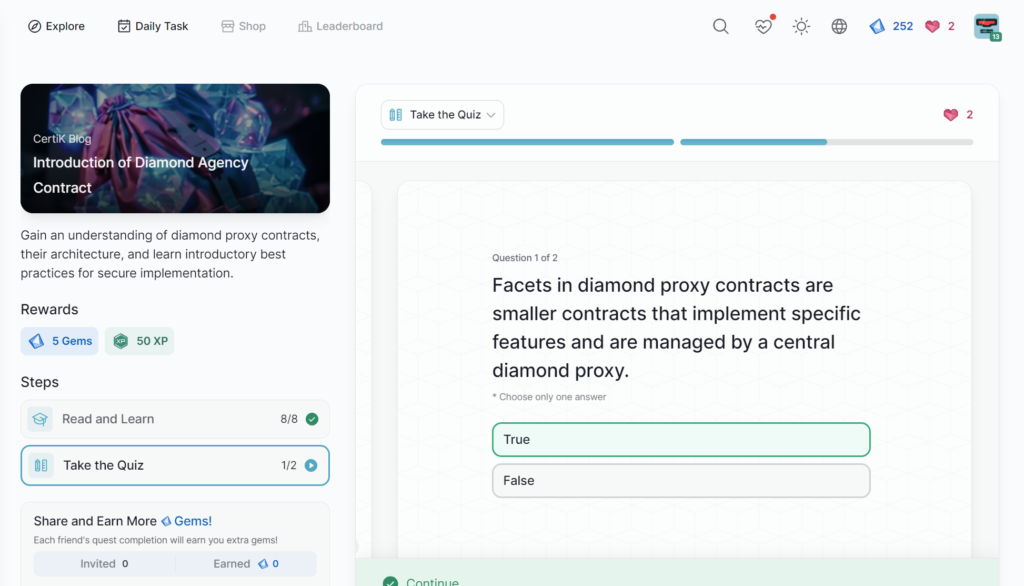
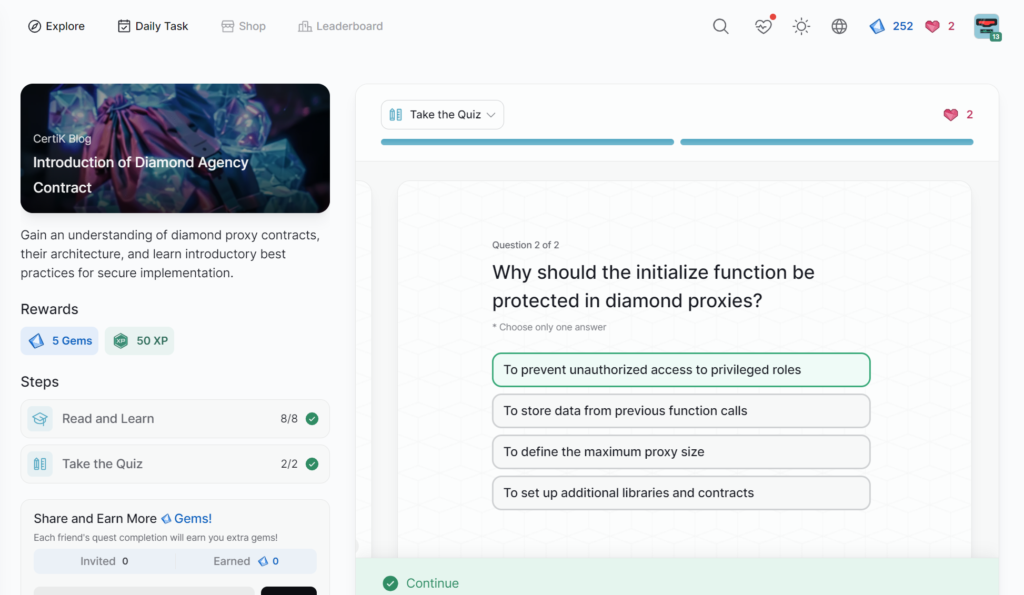
- Introduction of Diamond Agency Contract
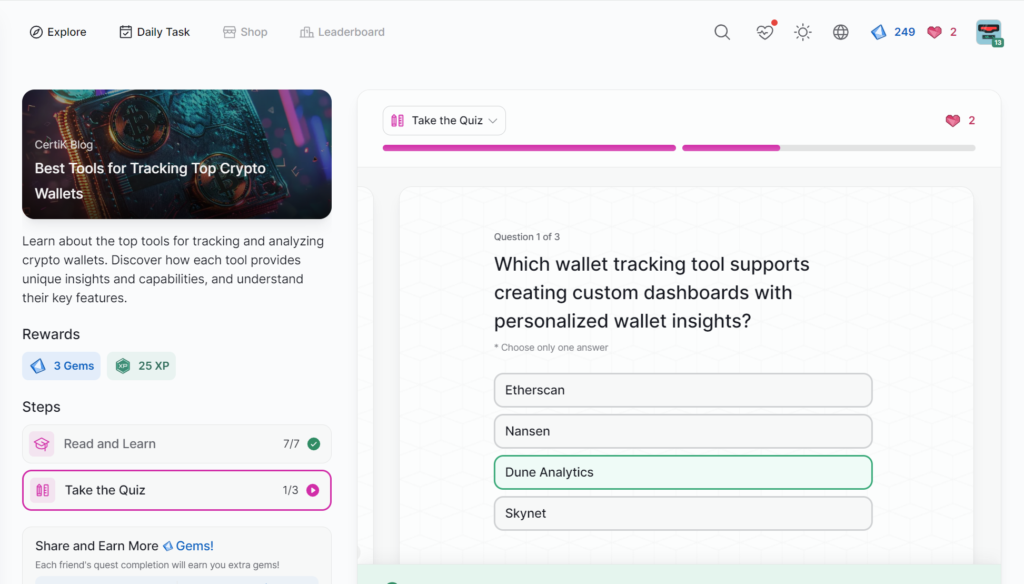
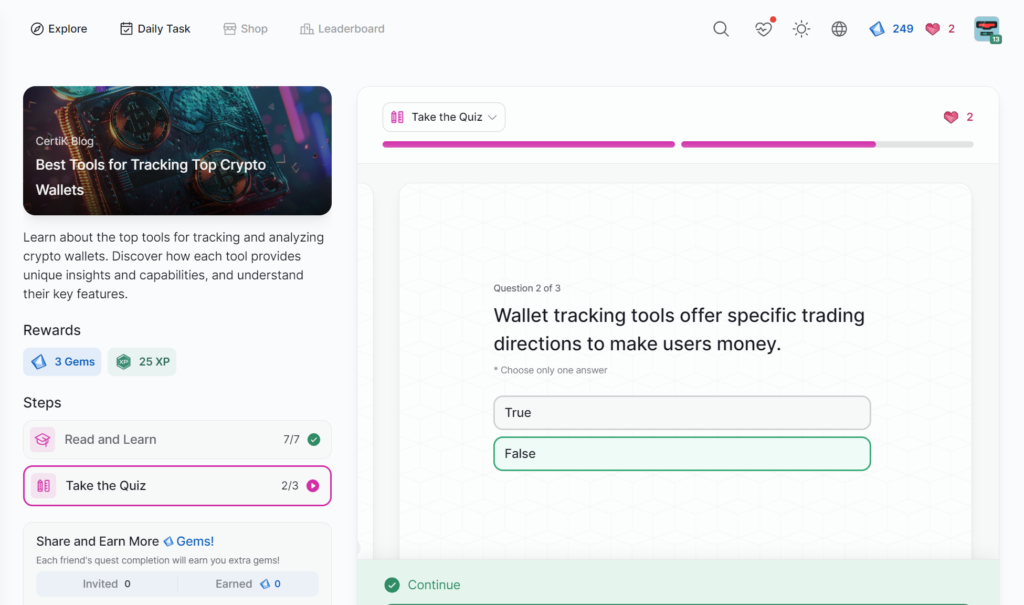
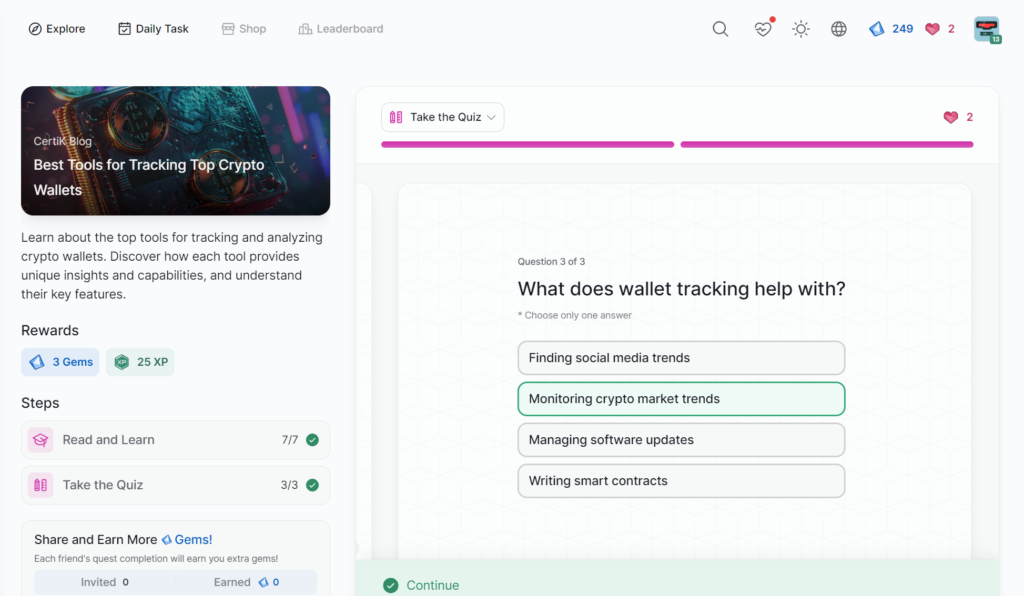
- Best Tools for Tracking Top Crypto Wallets
- Basics of Hackathons
- Normie Incident Analysis
- Bot-Driven Wash Trading in Exit Scams
- Advanced Formal Verification of ZK Proofs
- Sonne Finance Incident Analysis
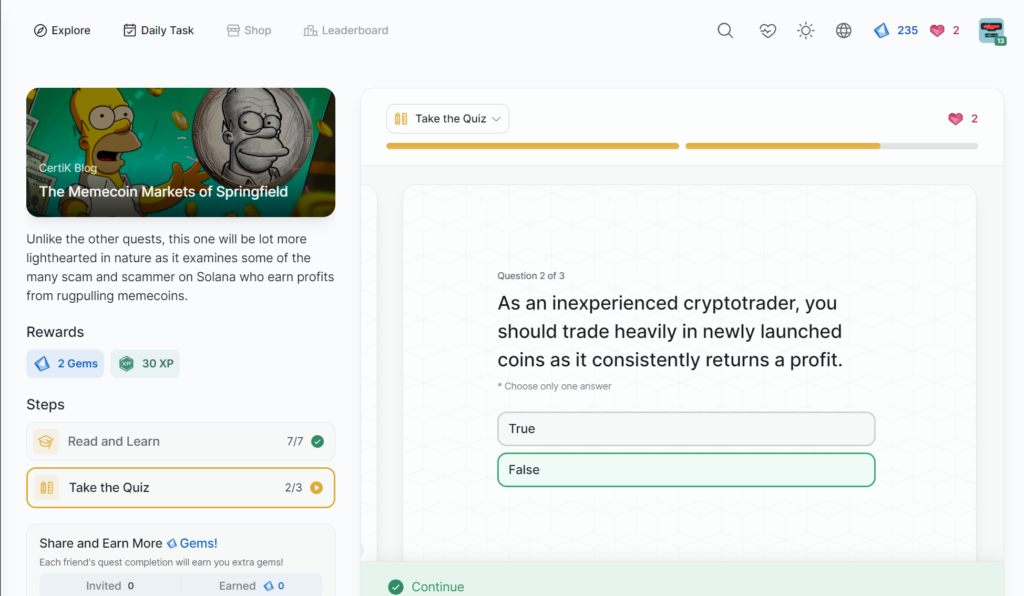
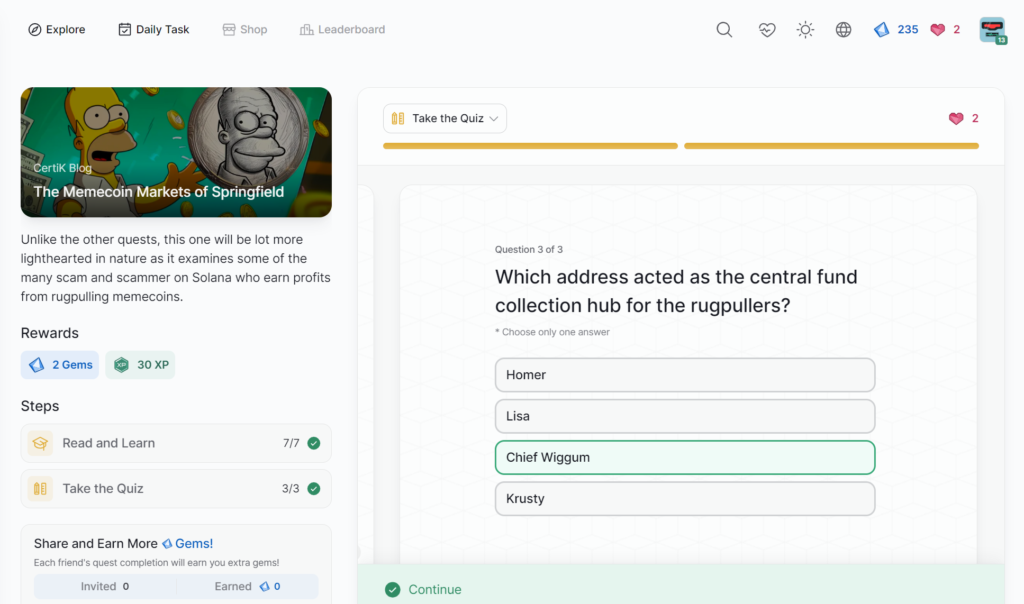
- The Memecoin Markets of Springfield
- Different Mechanisms for Honeypot Scams
- HACK3D Part 1: Top Incident Analyses
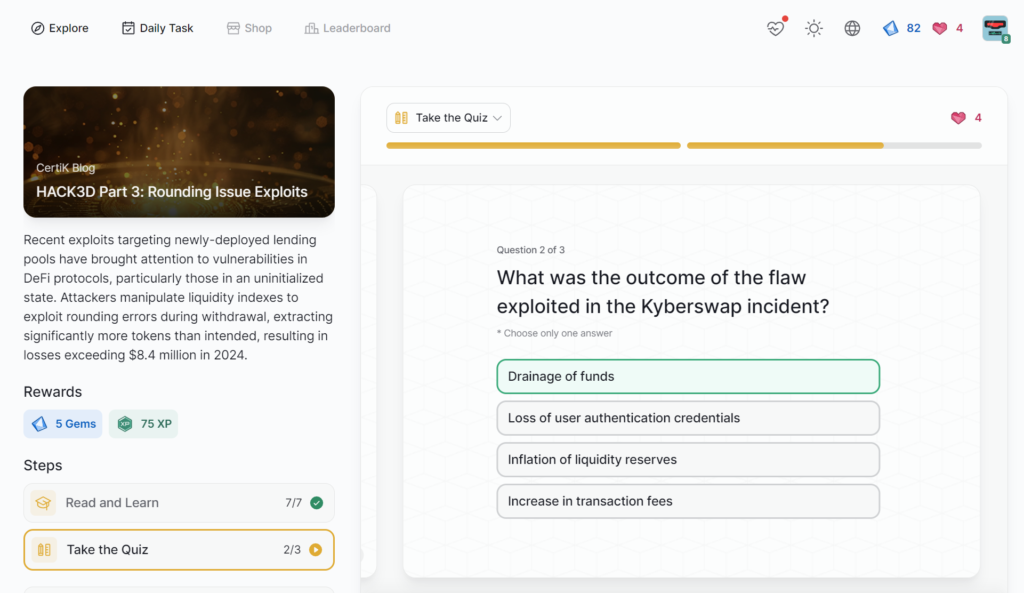
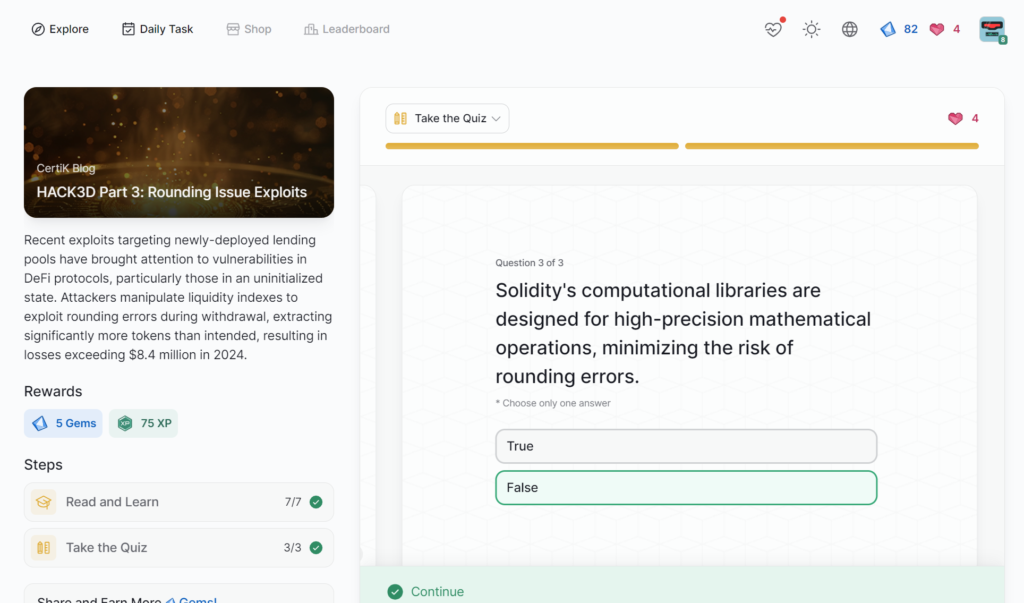
- HACK3D Part 3: Rounding Issue Exploits
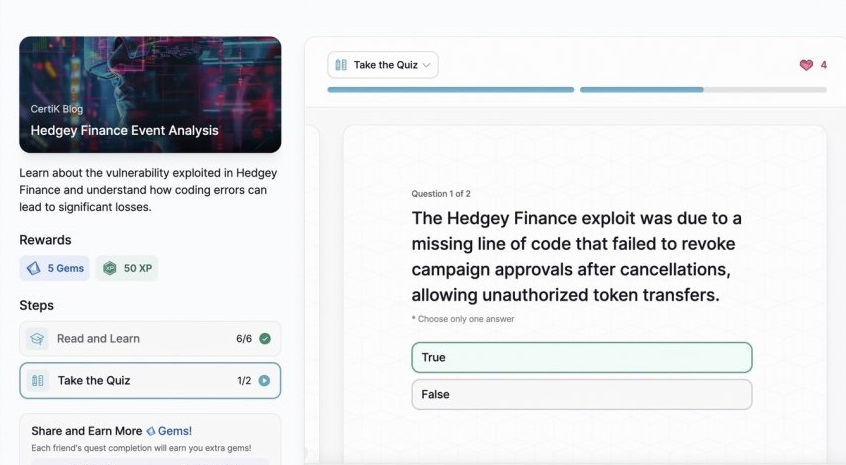
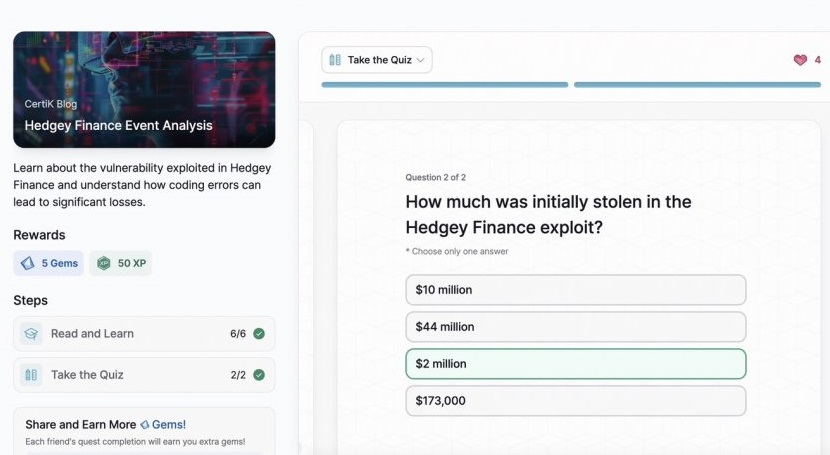
- Hedgey Finance Event Analysis
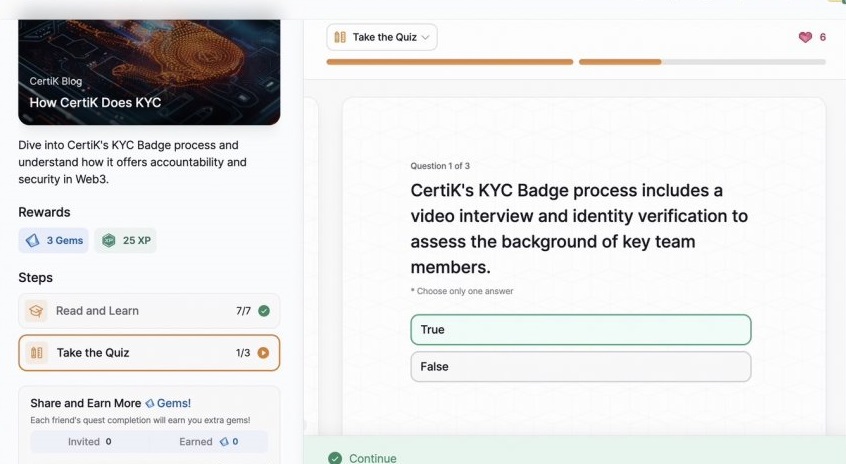
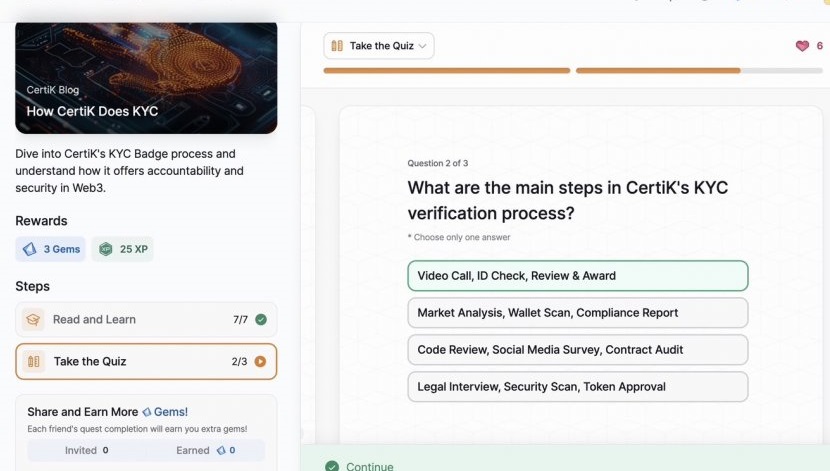
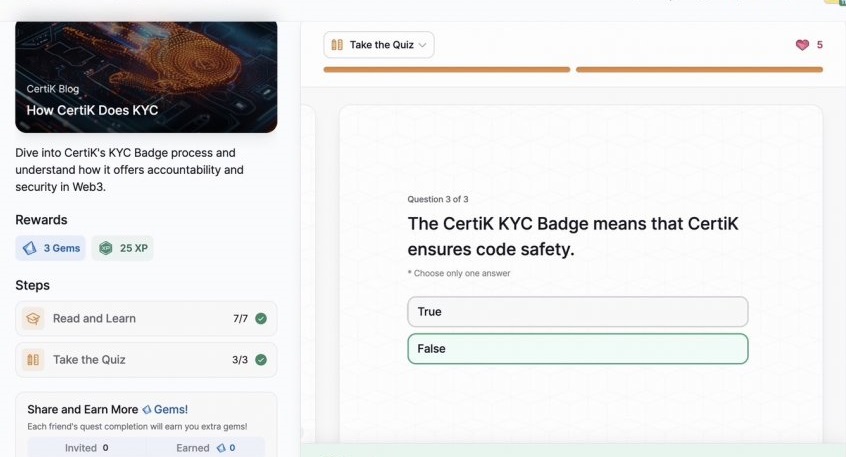
- How CertiK Does KYC
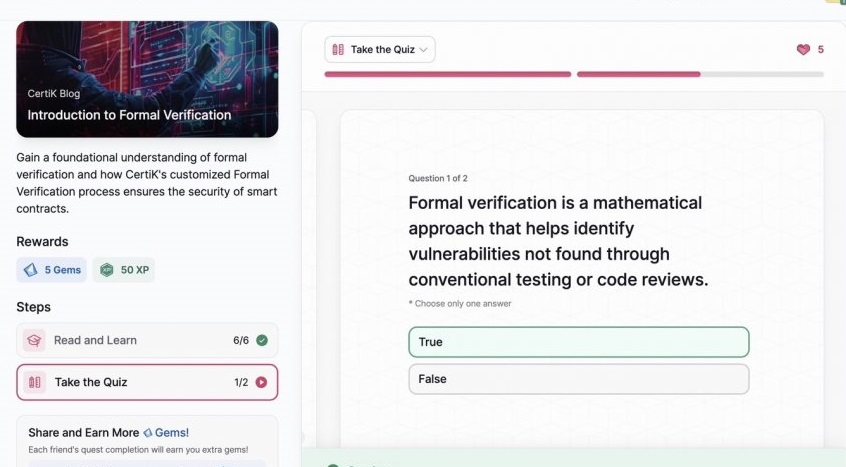
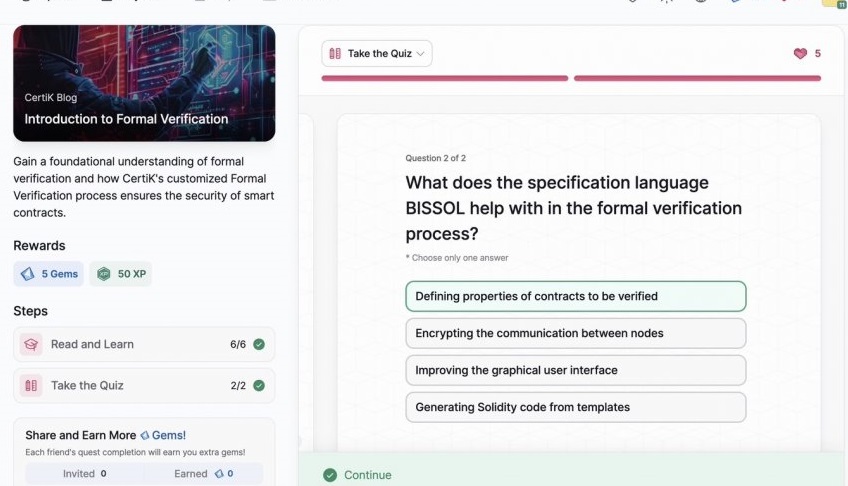
- Introduction to Formal Verification
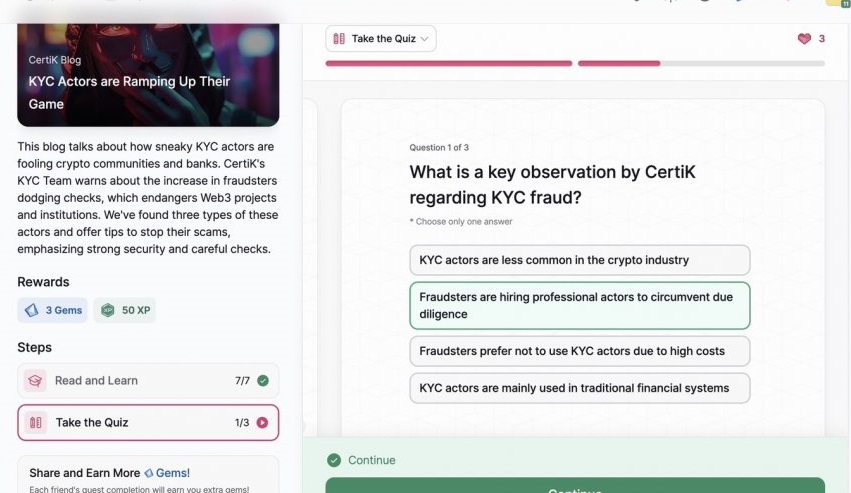
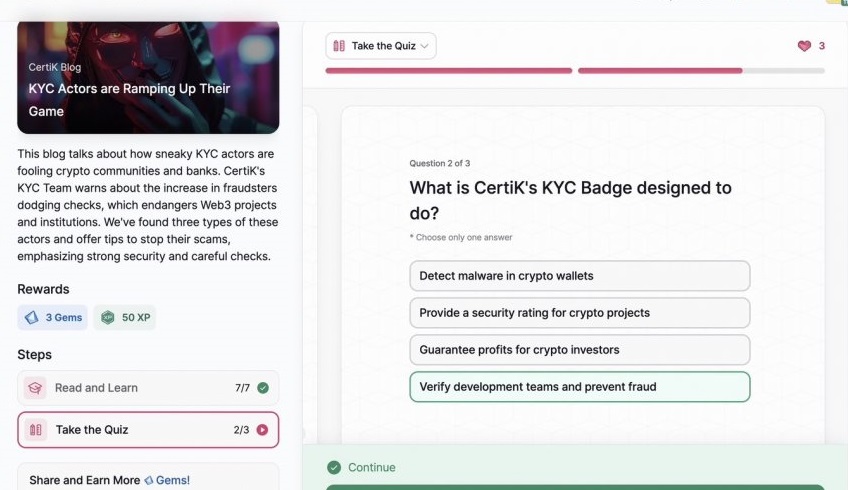
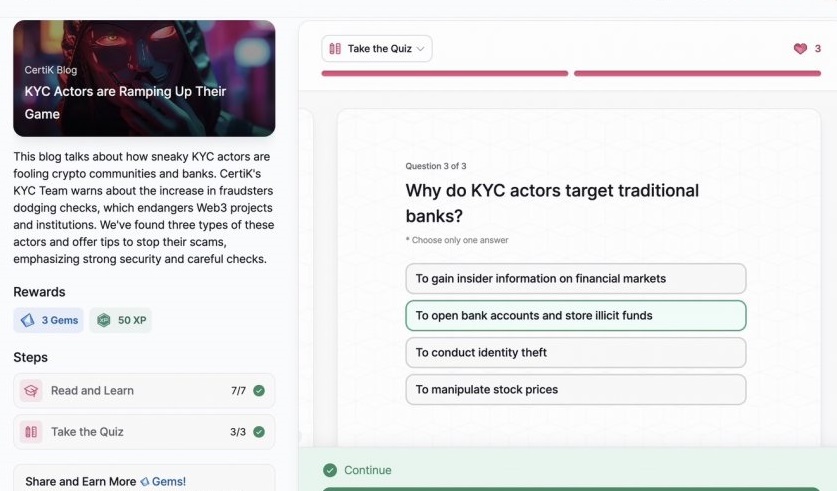
- KYC Actors are Ramping Up Their Game
- Recognizing the Misuse of CertiK’s Brand
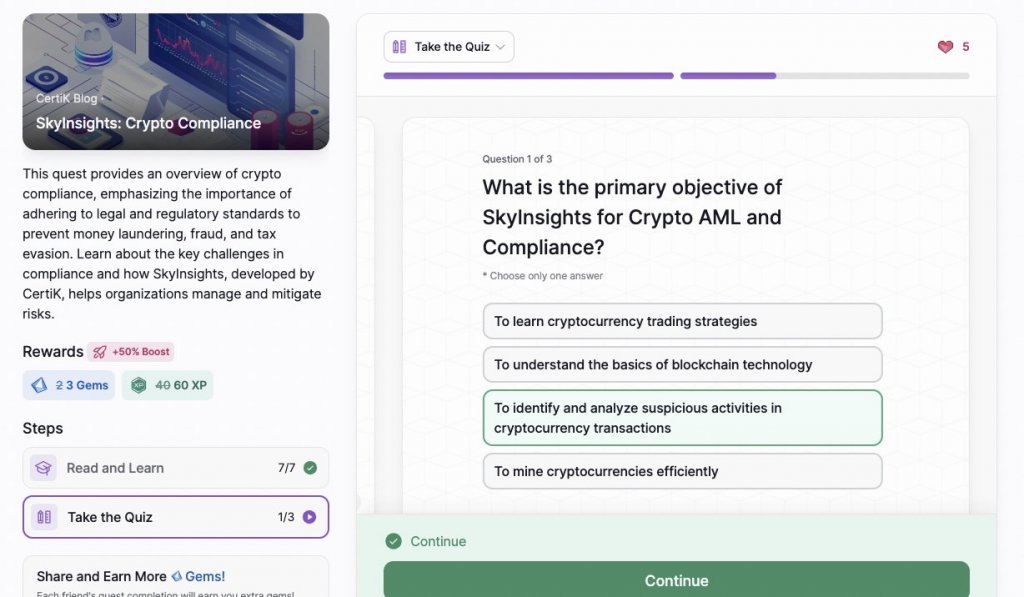
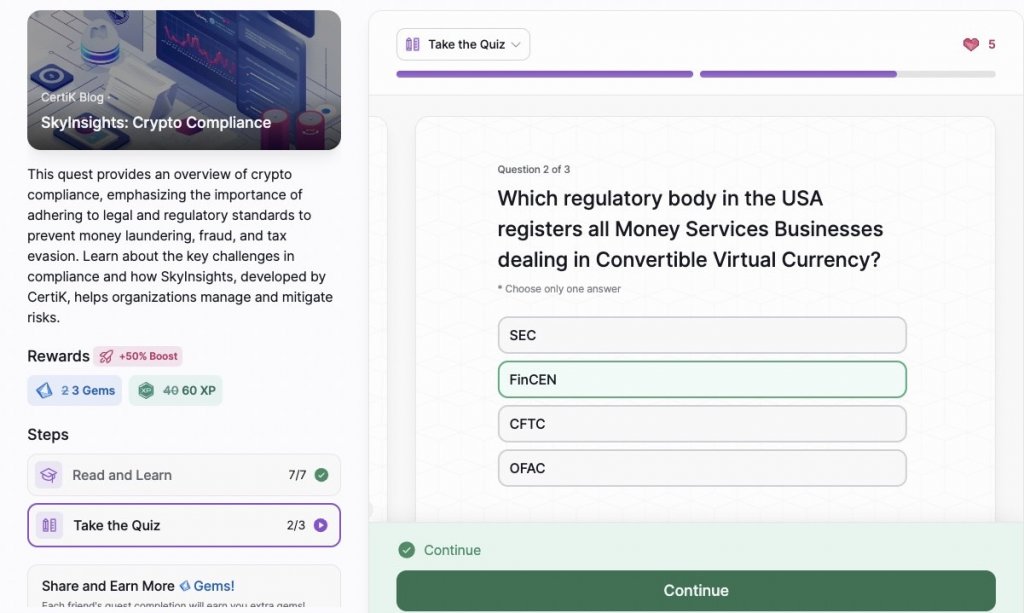
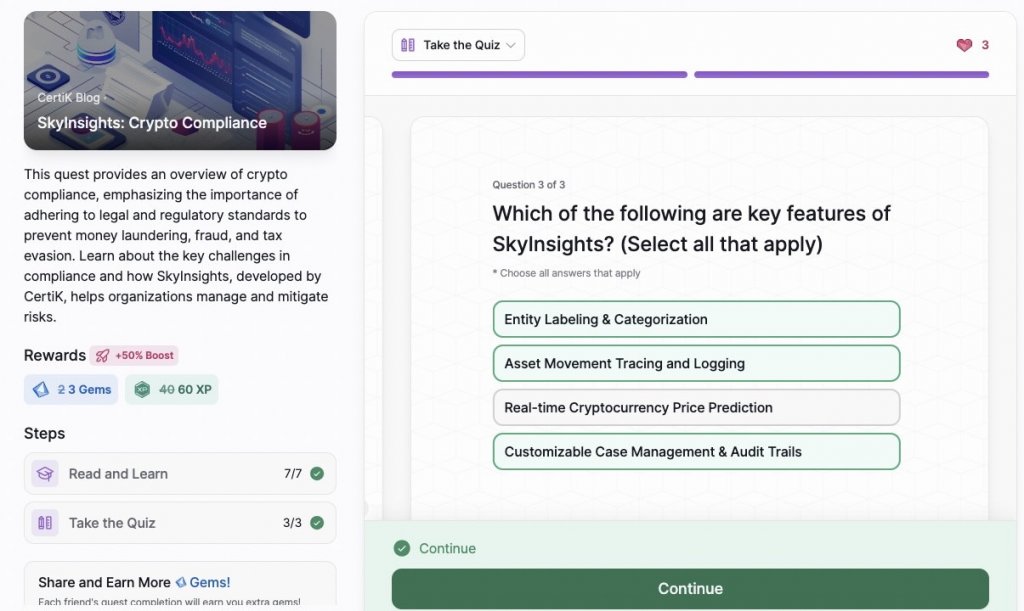
- SkyInsights: Crypto Compliance
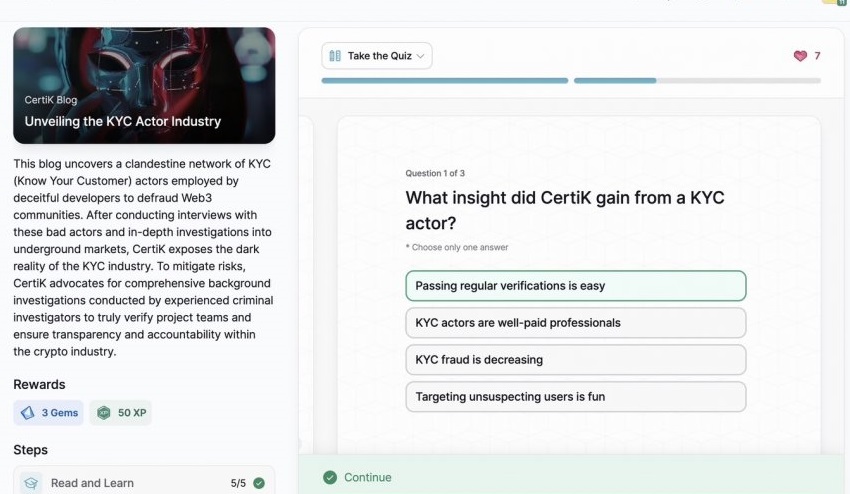
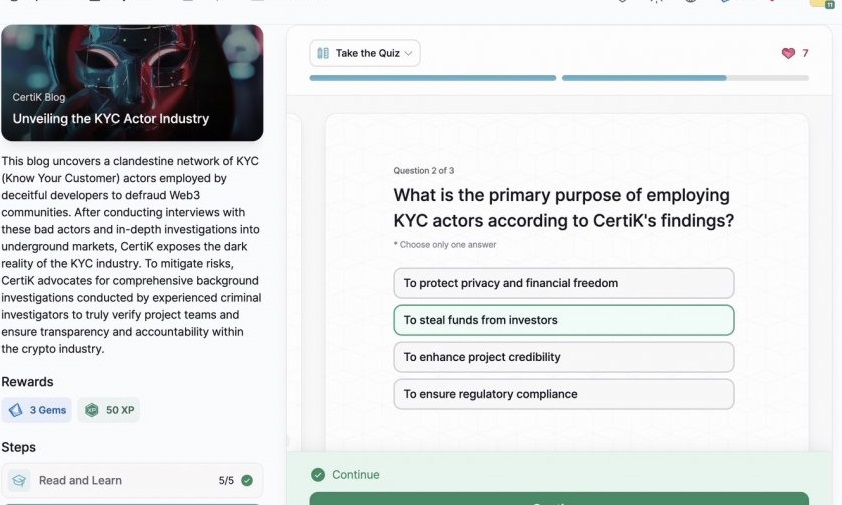
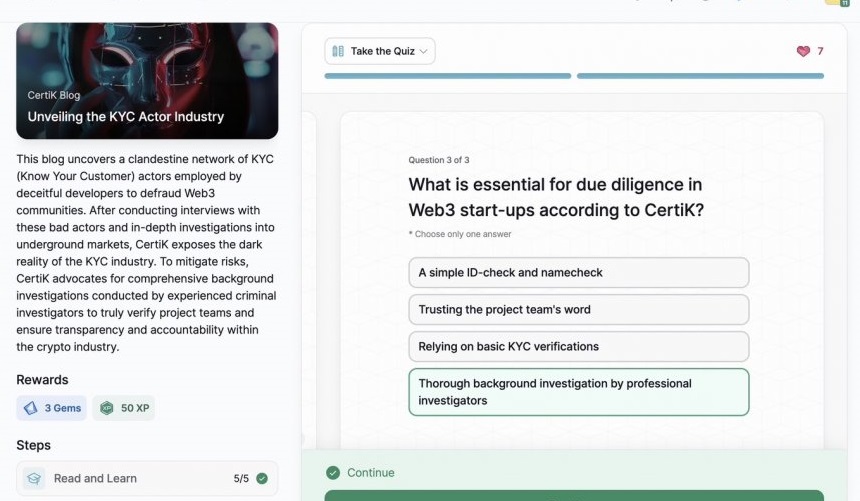
- Unveiling the KYC Actor Industry
- SkyKnight
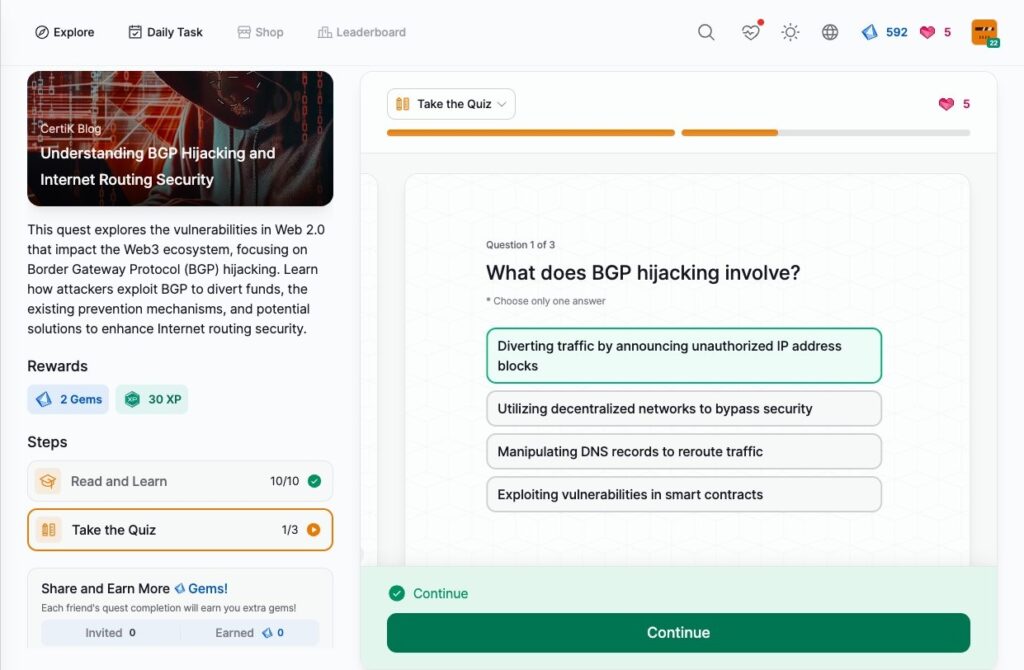
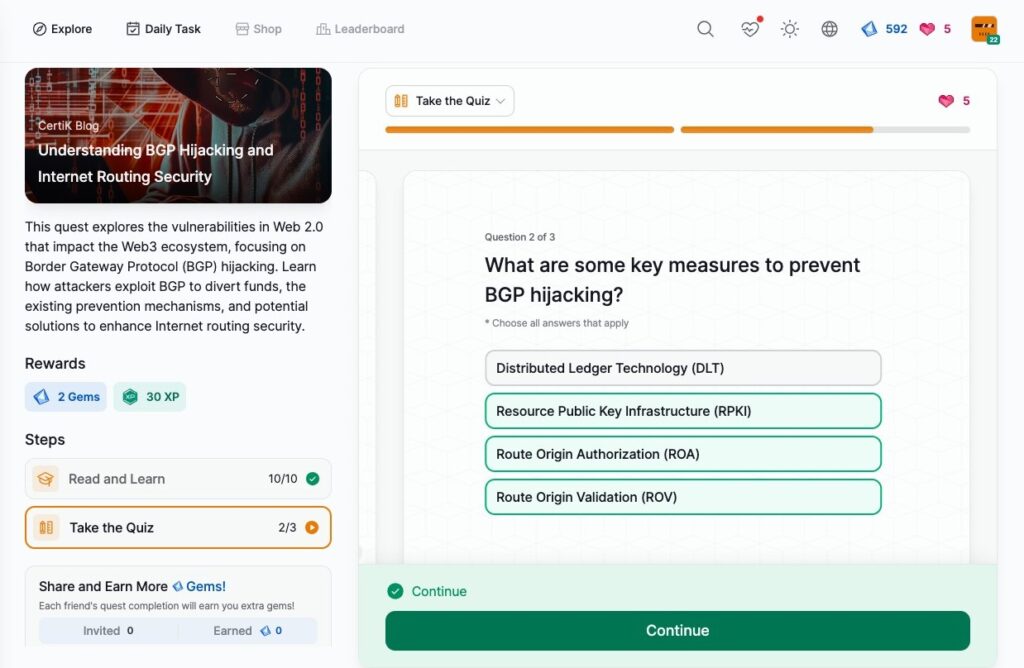
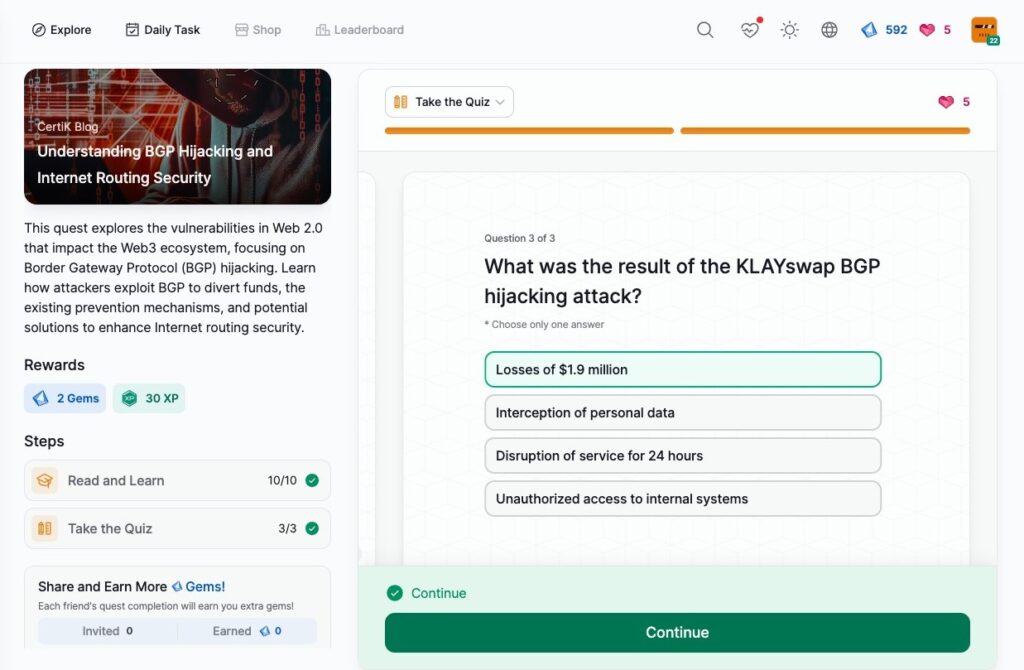
- Understanding BGP Hijacking and Internet Routing Security
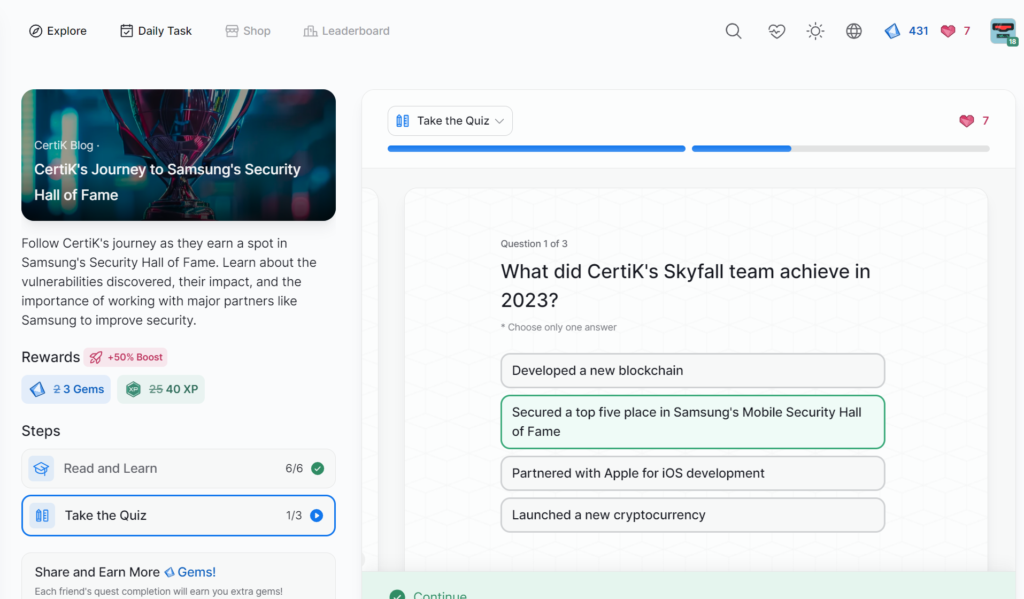
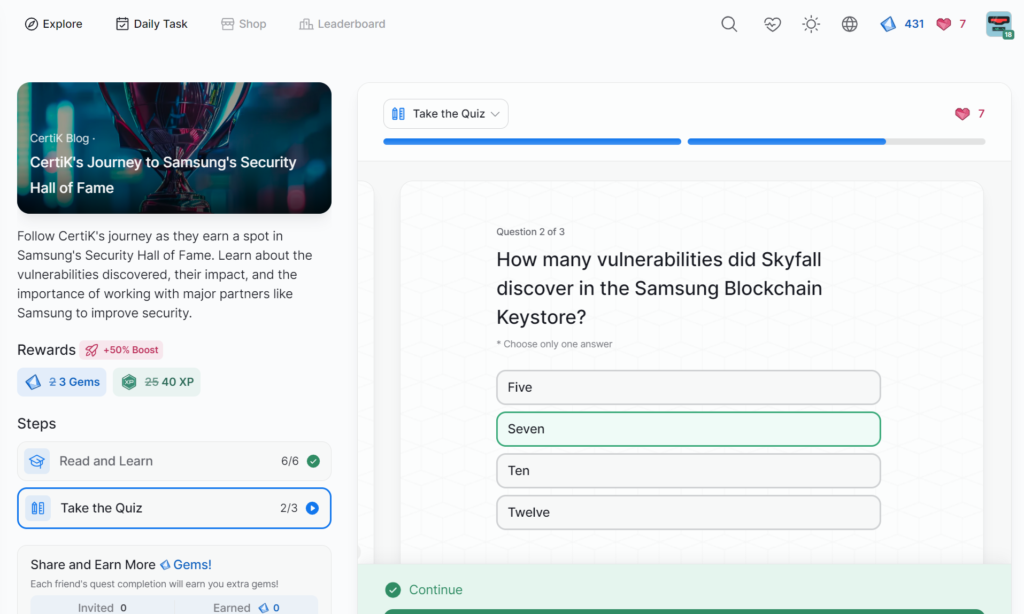
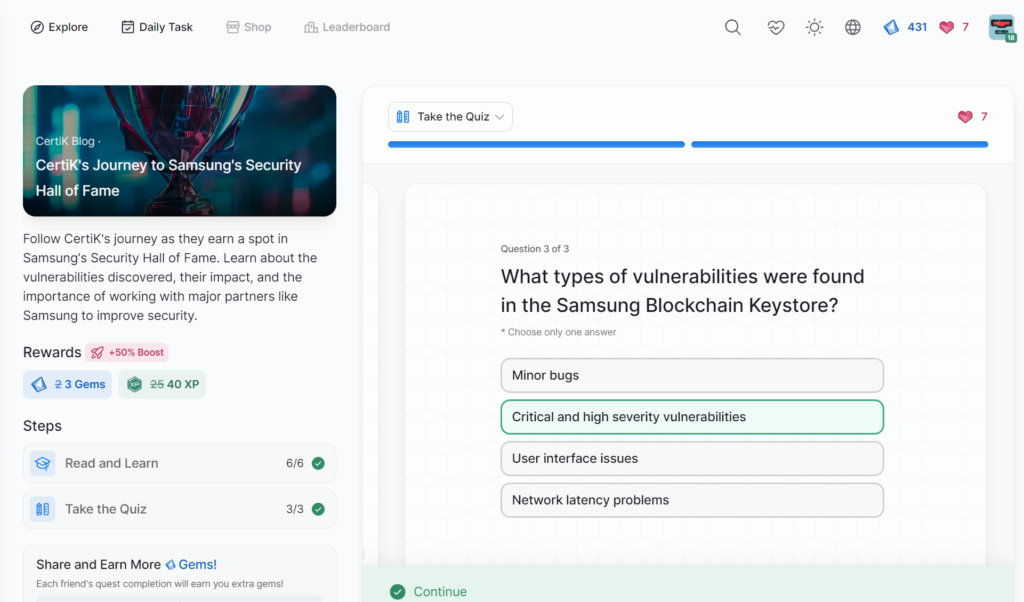
- CertiK’s Journey to Samsung’s Security Hall of Fame
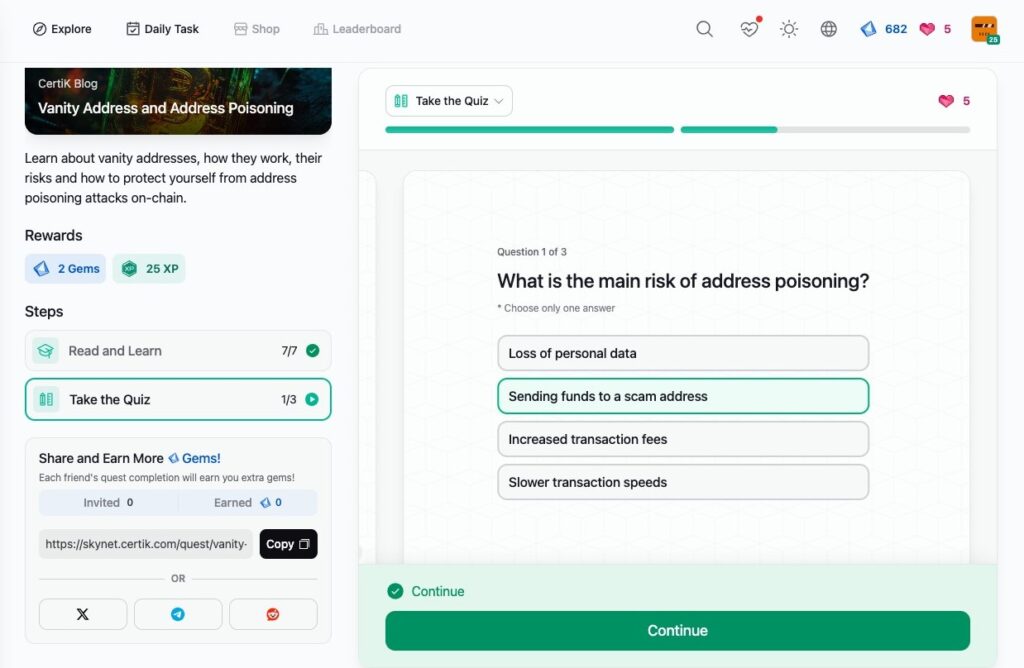
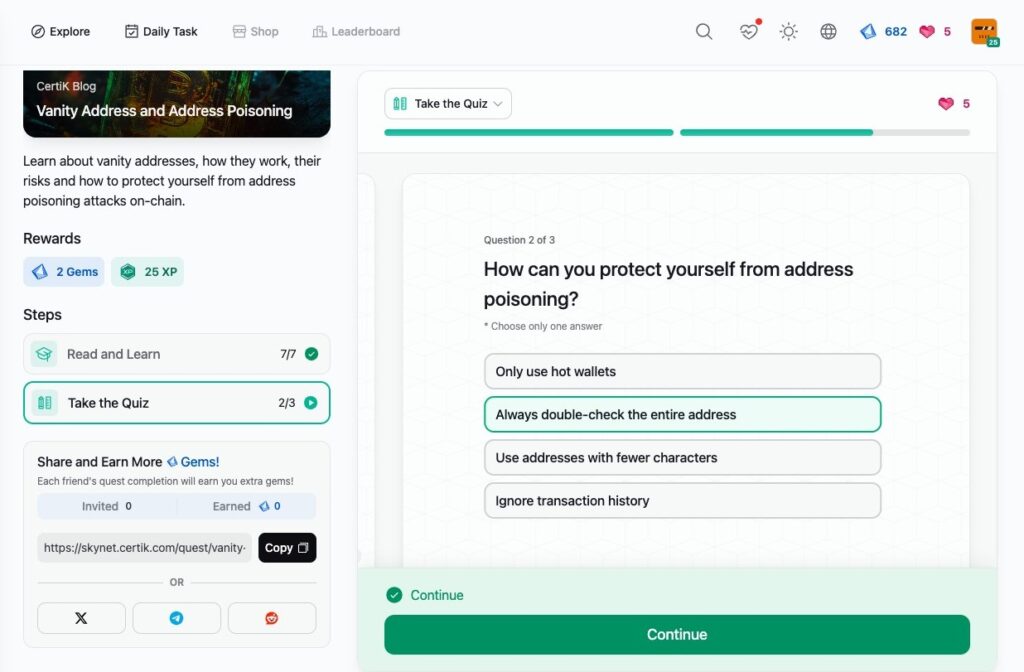
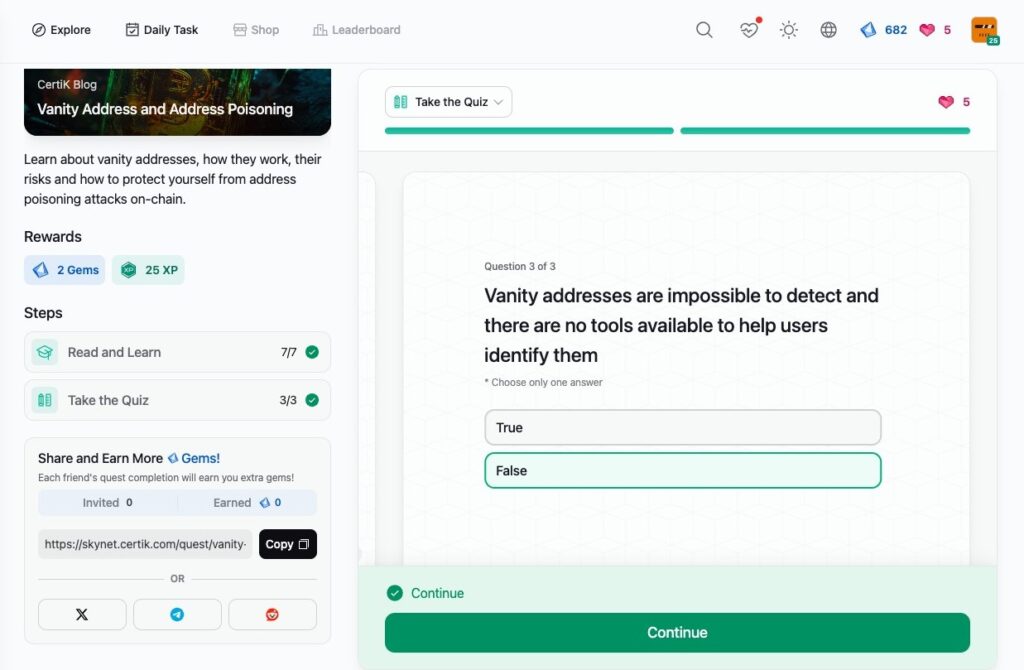
- Vanity Address and Address Poisoning
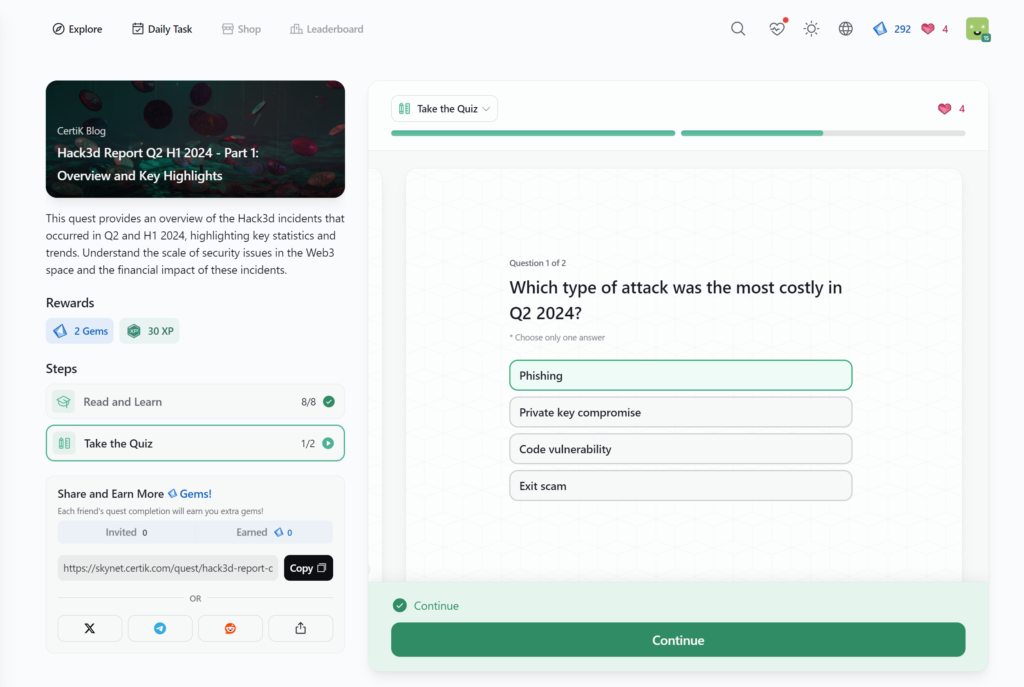
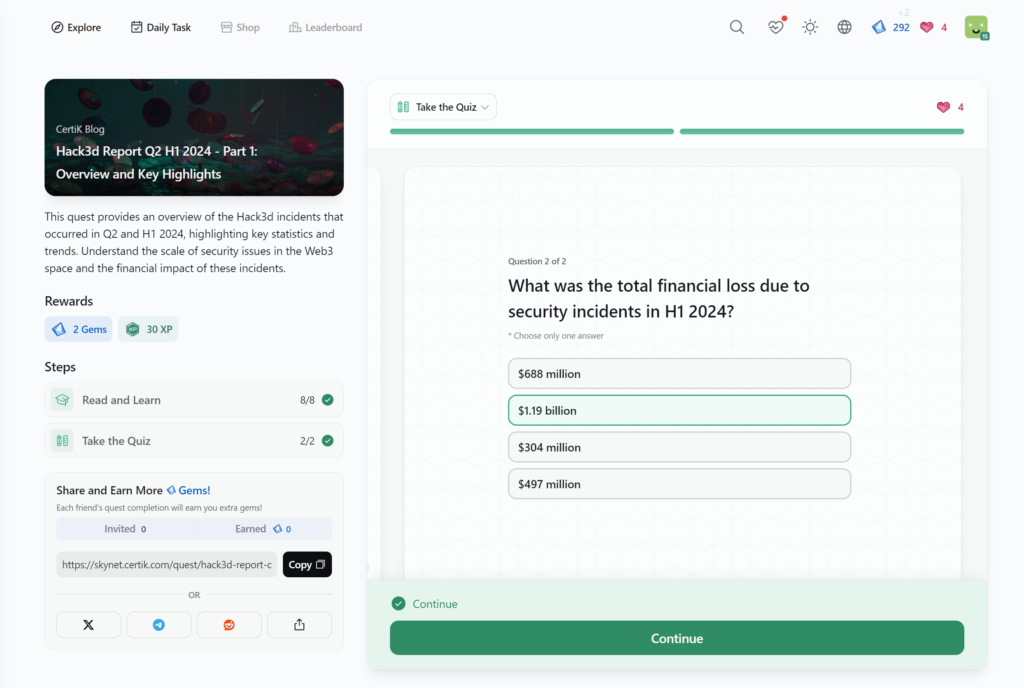
- Hack3d Report Q2 H1 2024 – Part 1: Overview and Key Highlights
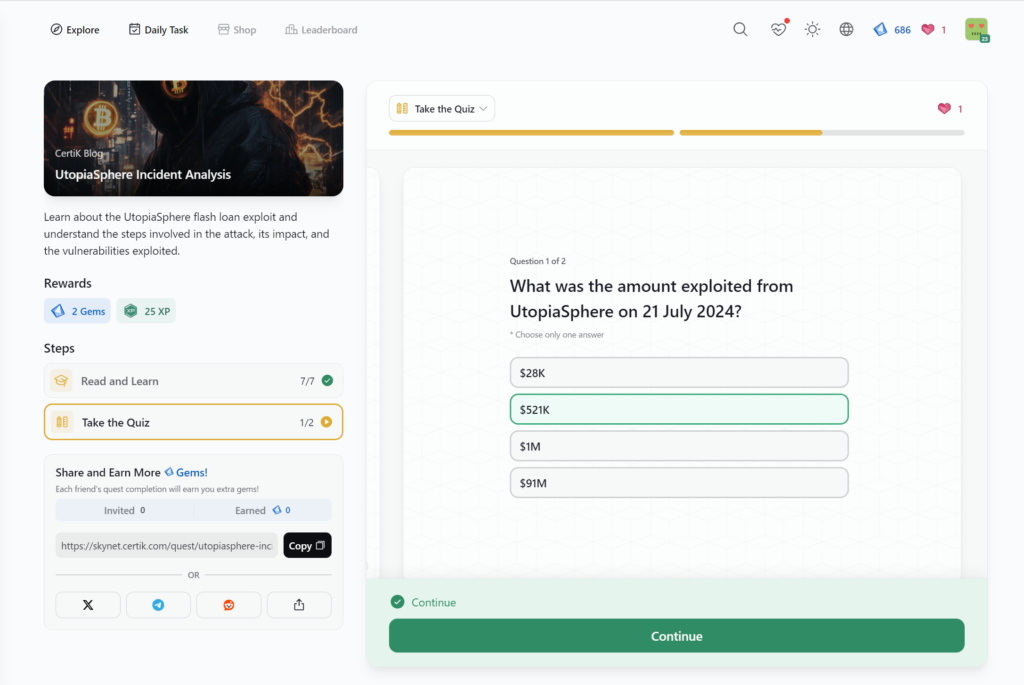
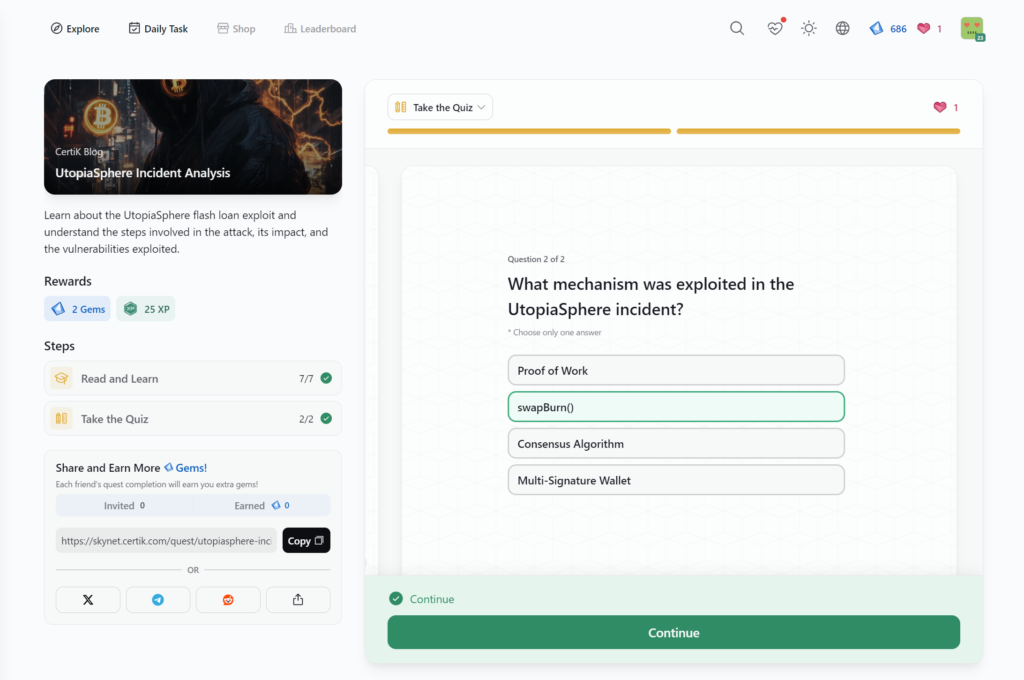
- UtopiaSphere Incident Analysis
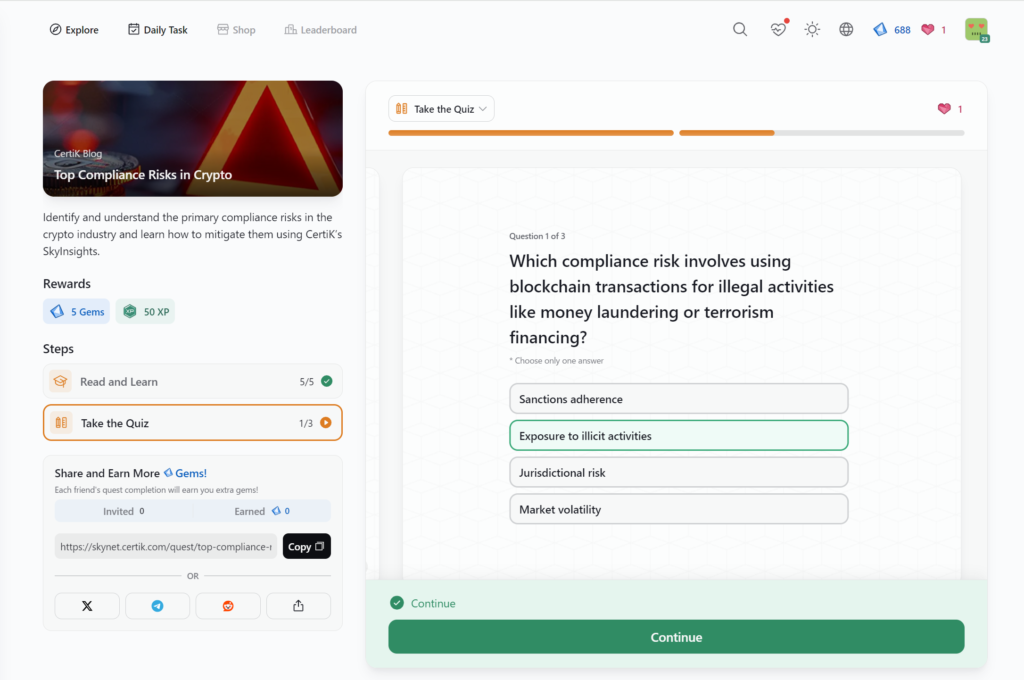
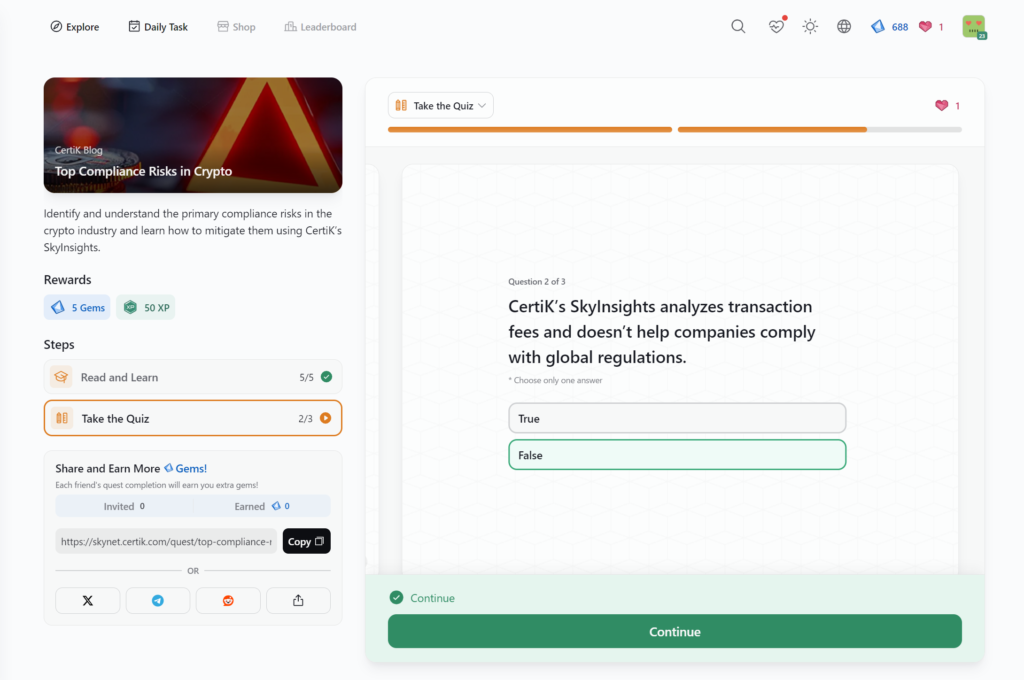
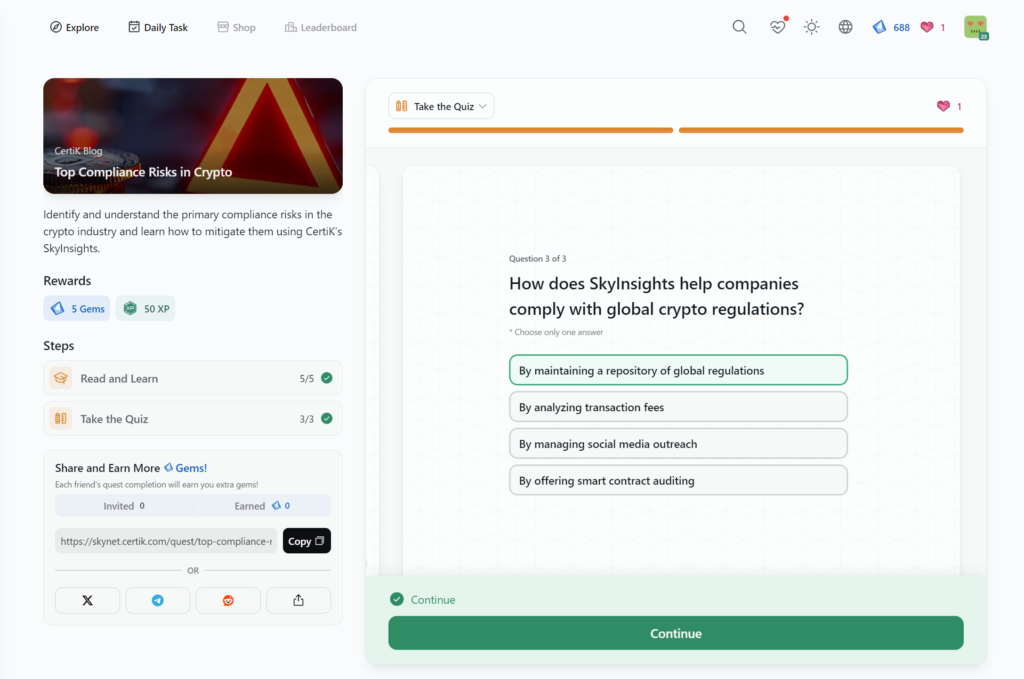
- Top Compliance Risks in Crypto
- HACK3D Part 2: Private Key Compromise
- Hack3d Report Q2 H1 2024 – Part 2: Insights and Future Security Enhancements
- How AI is Transforming KYC for Crypto Project Teams
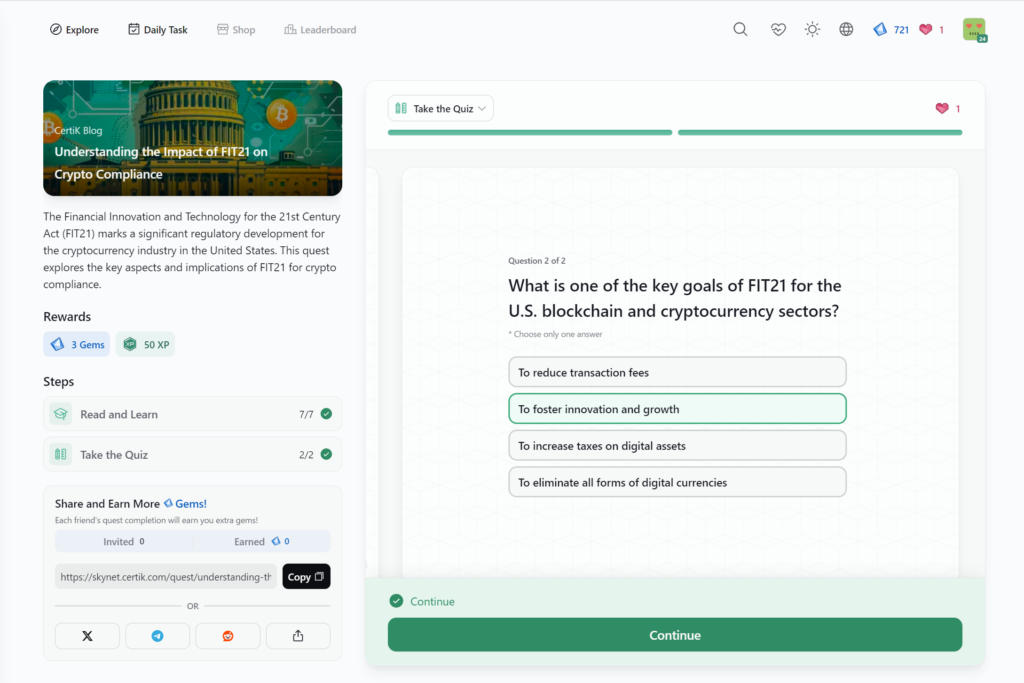
- Understanding the Impact of FIT21 on Crypto Compliance
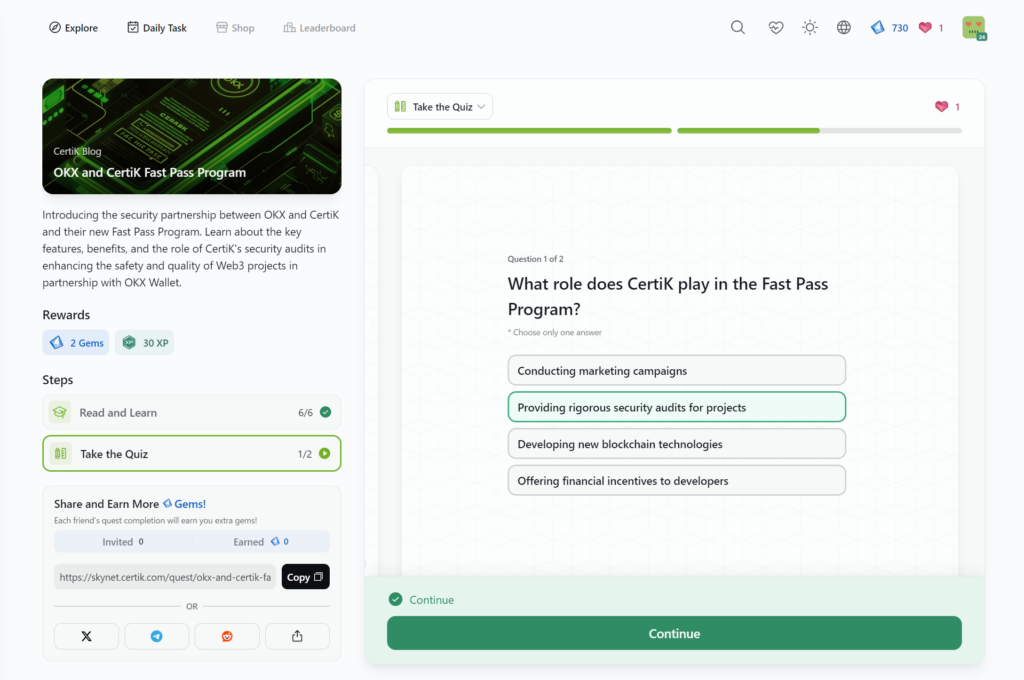
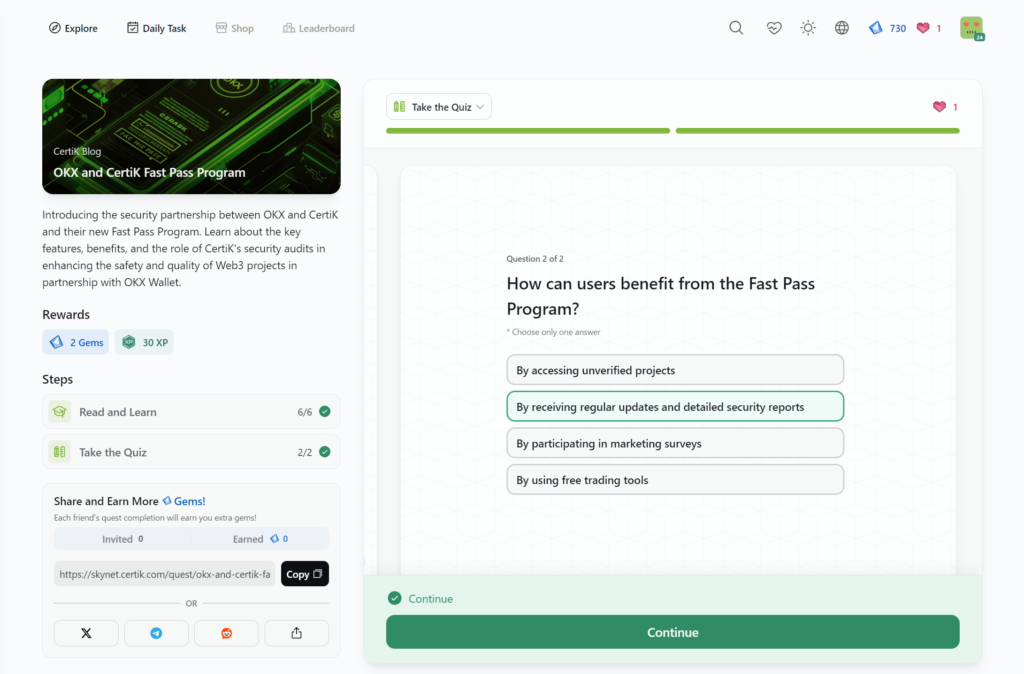
- OKX and CertiK Fast Pass Program
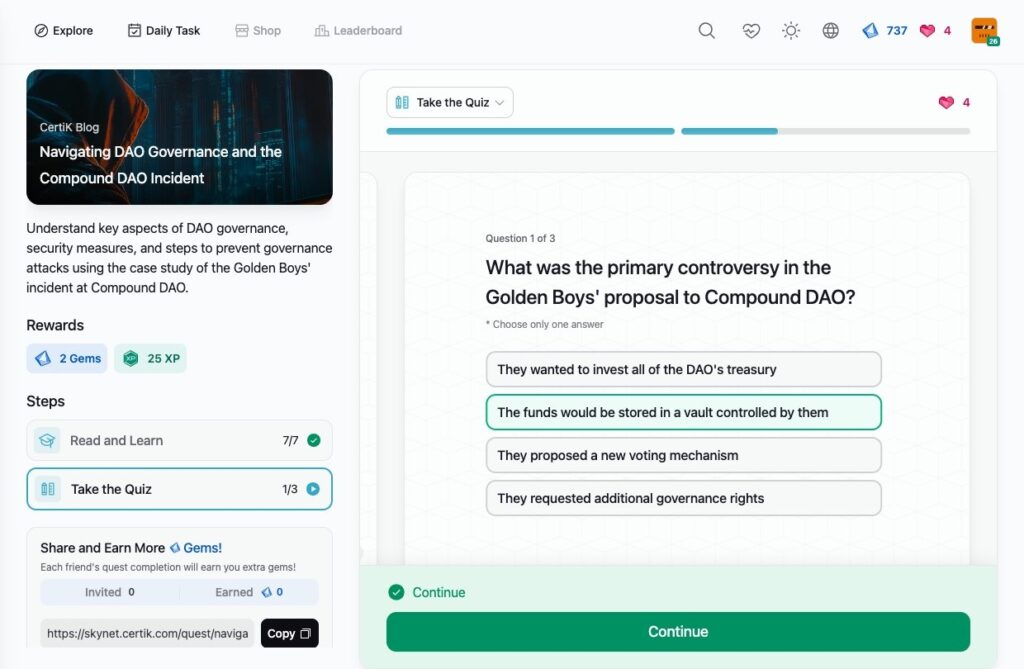
- Navigating DAO Governance and the Compound DAO Incident
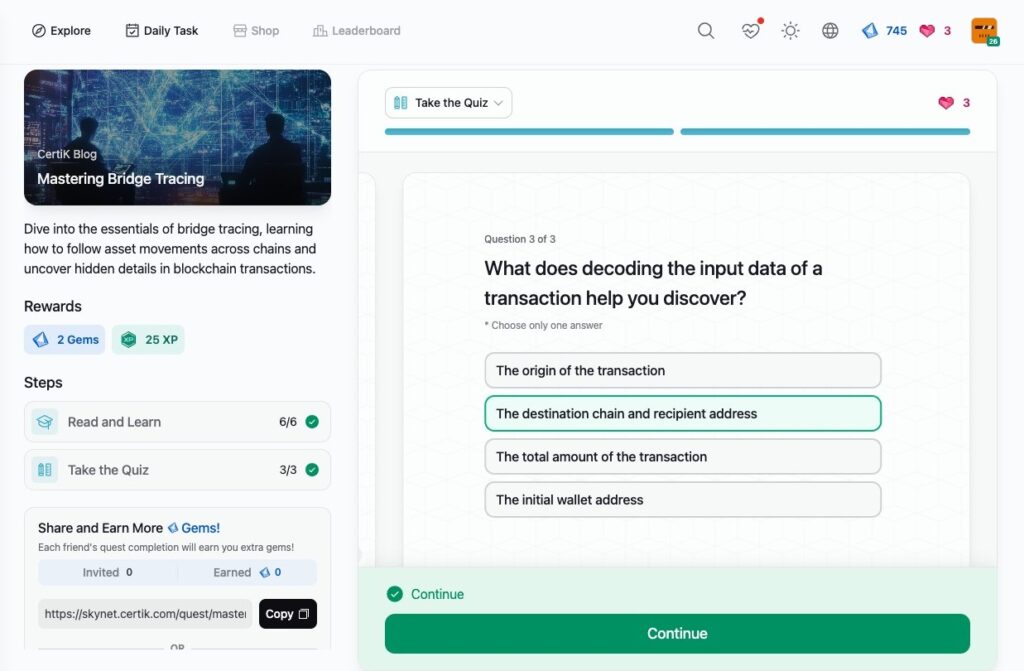
- Mastering Bridge Tracing
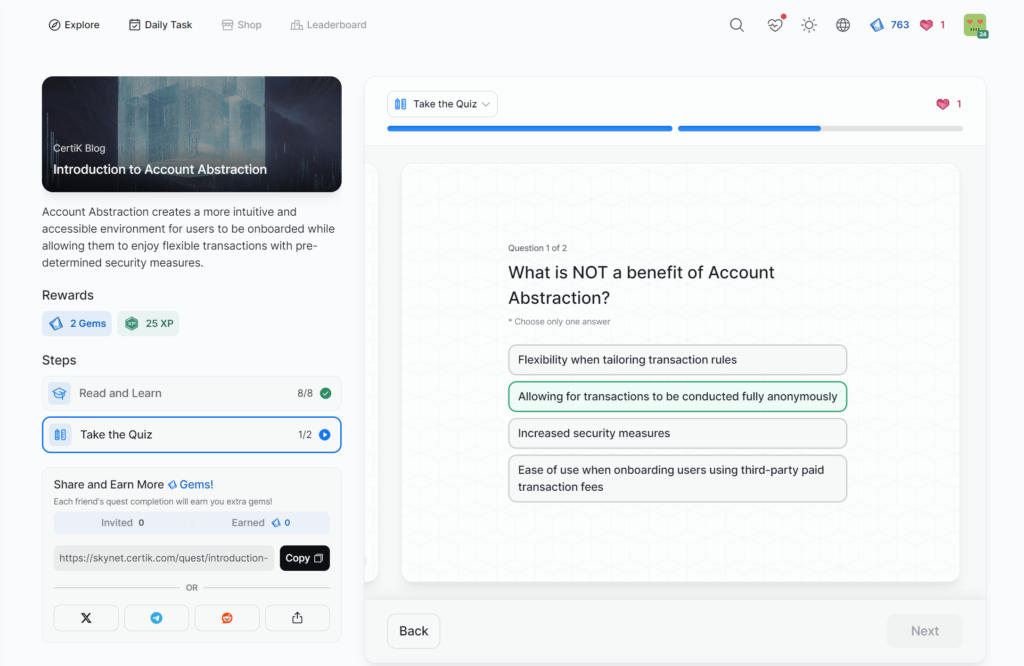
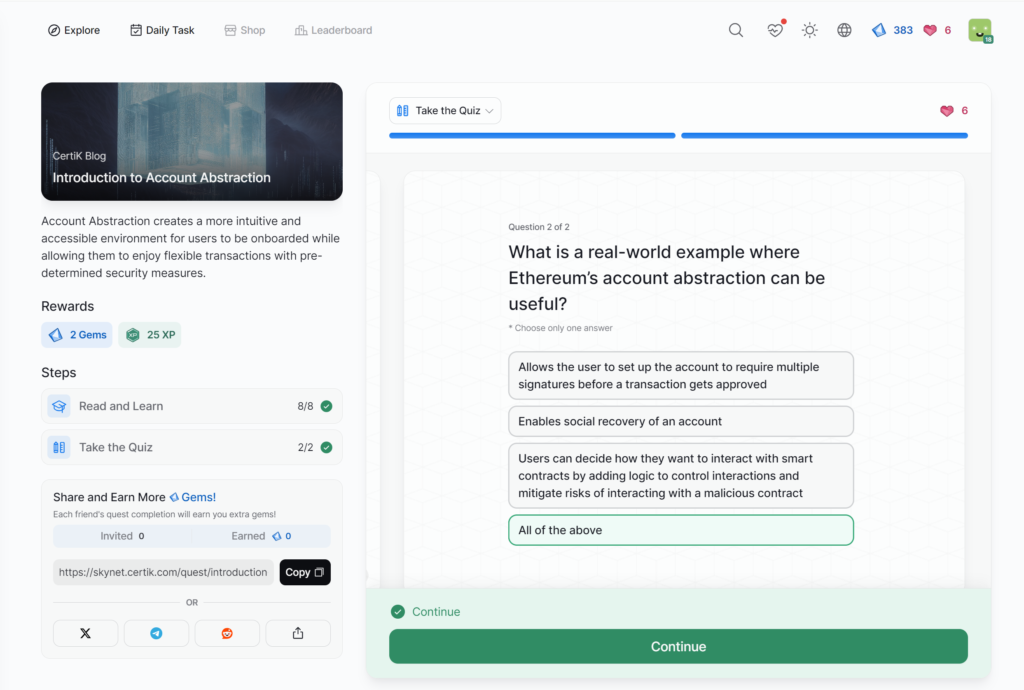
- Introduction to Account Abstraction
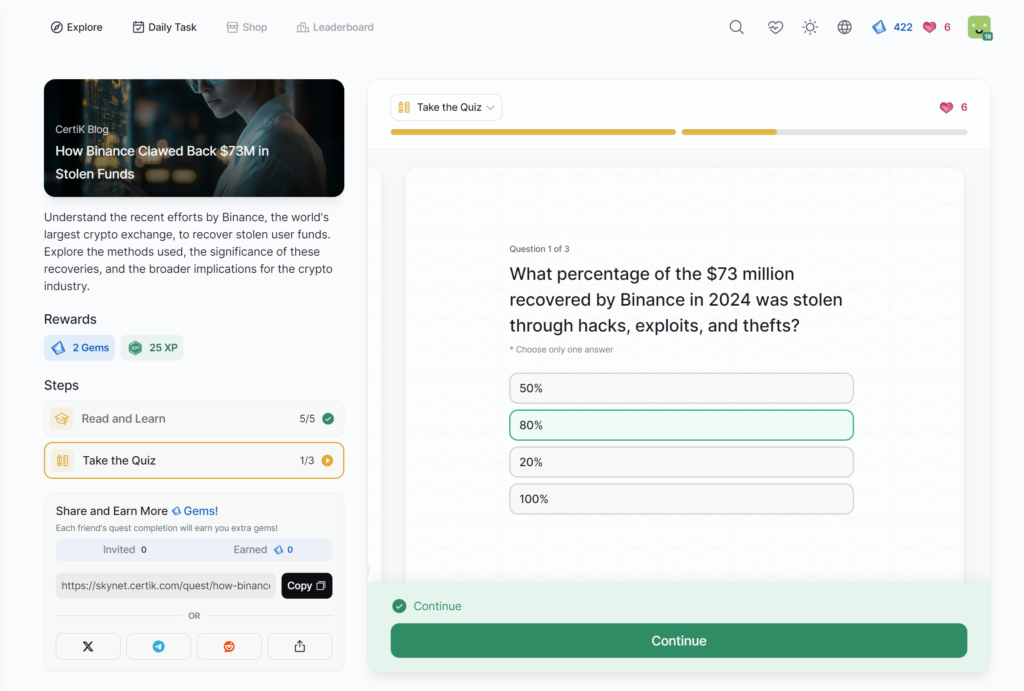
- How Binance Clawed Back M in Stolen Funds
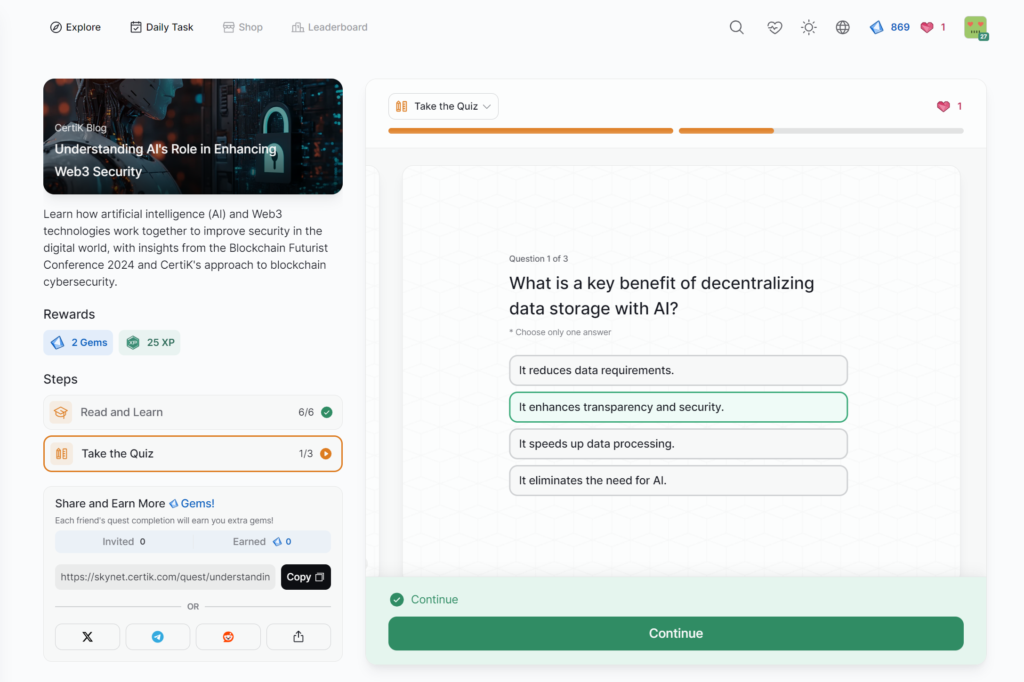
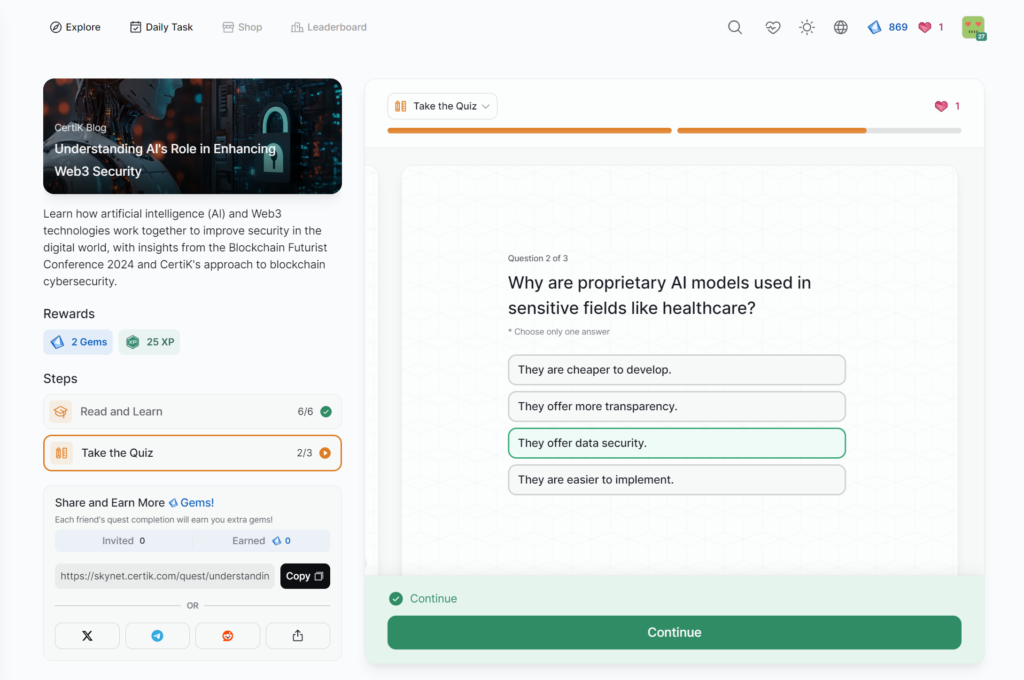
- Understanding AI’s Role in Enhancing Web3 Security
- Evaluating Popular Web3 Messaging Apps
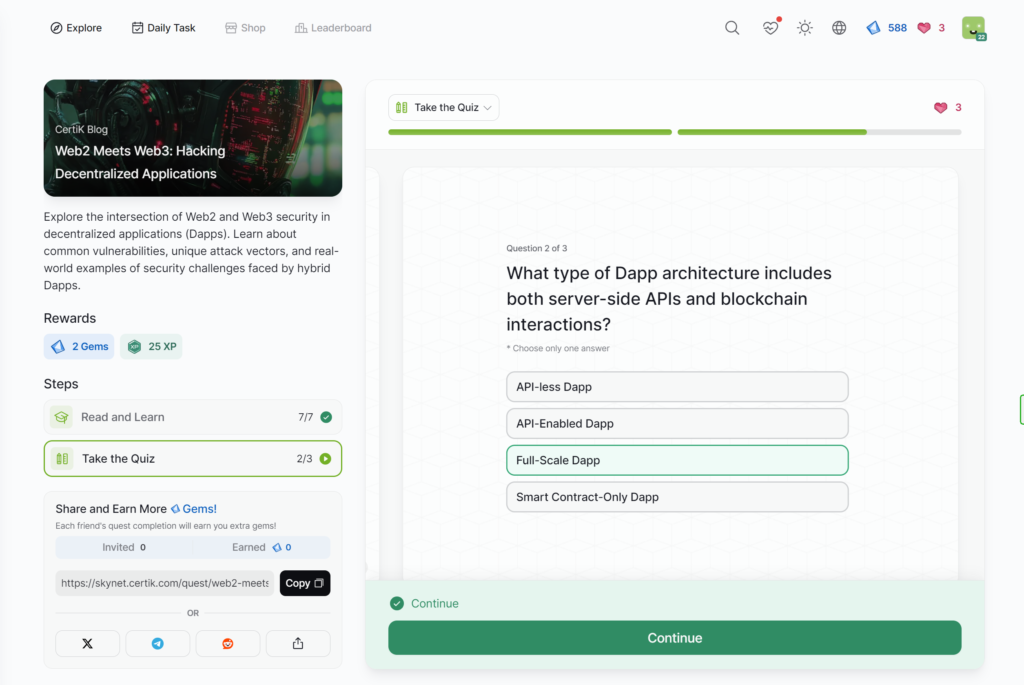
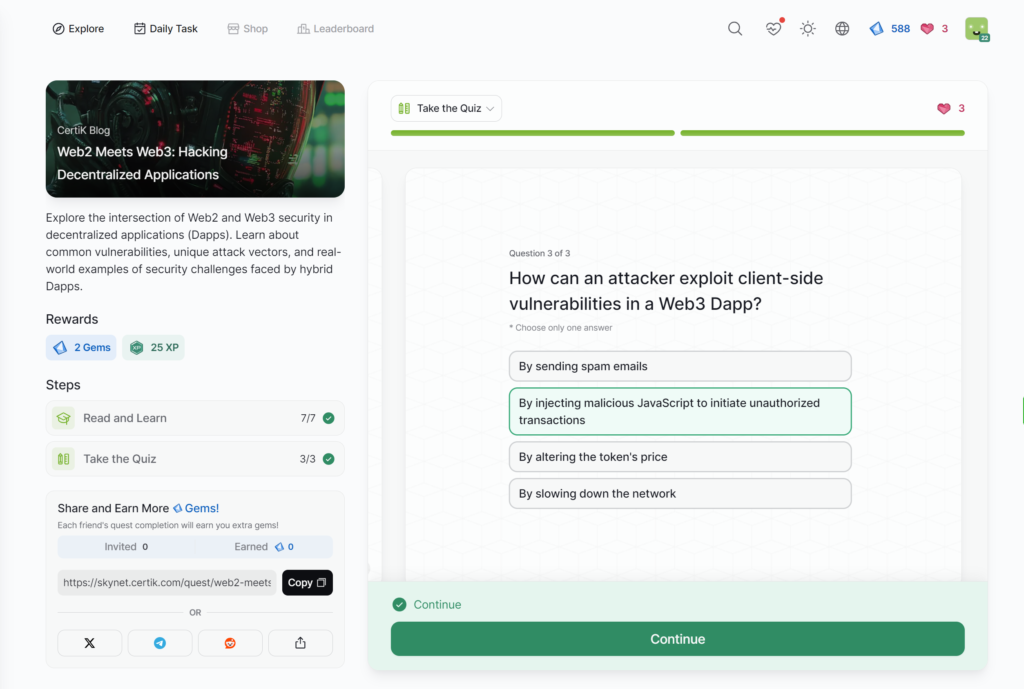
- Web2 Meets Web3: Hacking Decentralized Applications
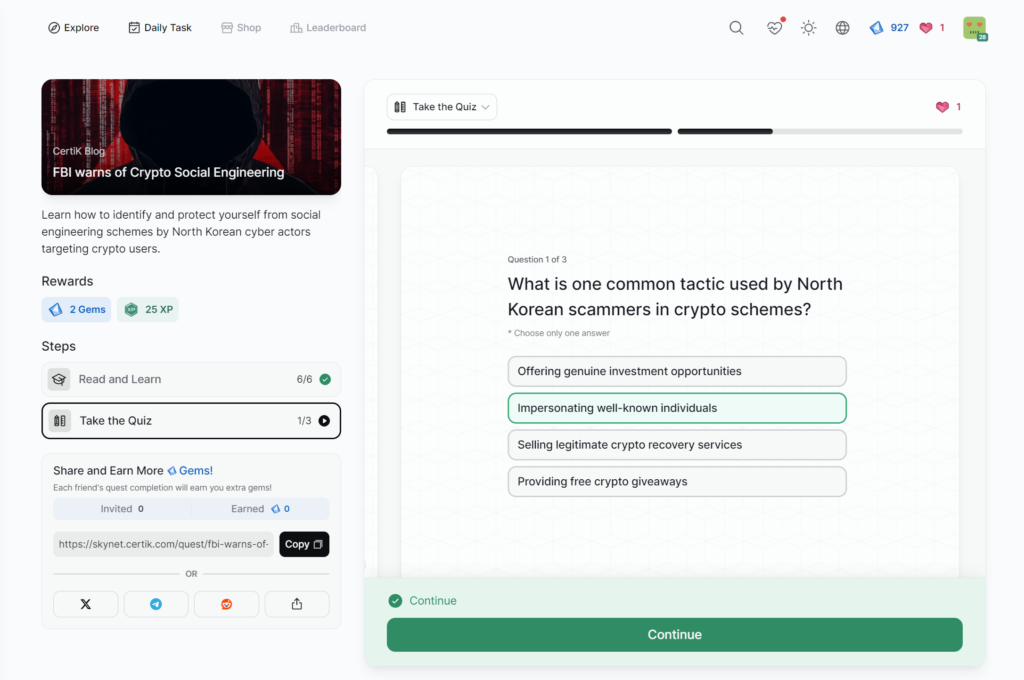
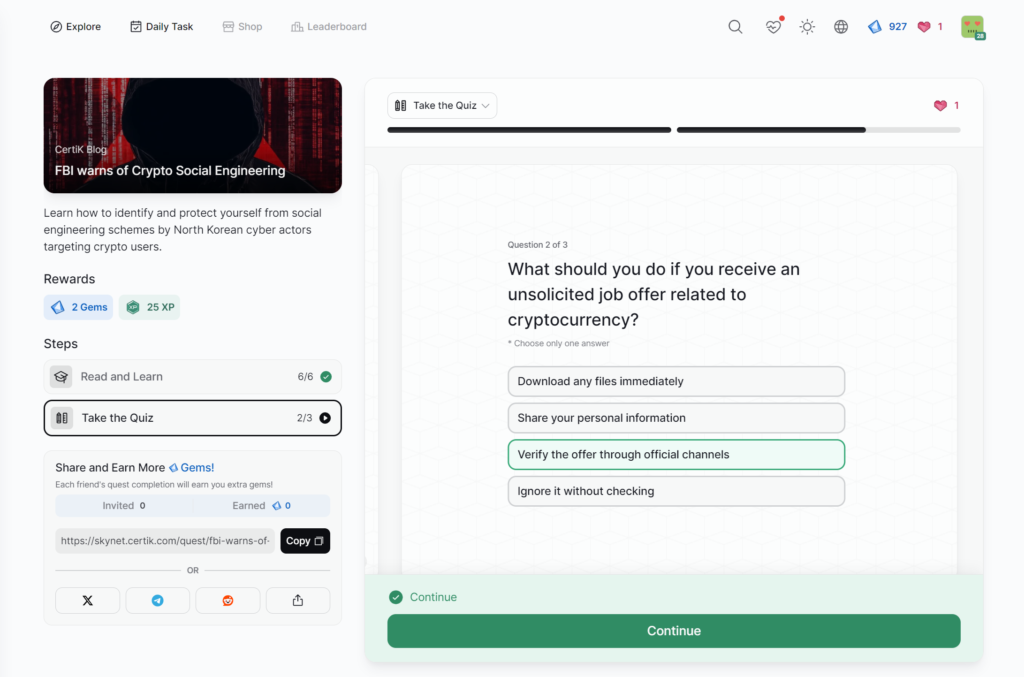
- FBI warns of Crypto Social Engineering
- Understanding the Android SpyAgent Campaign
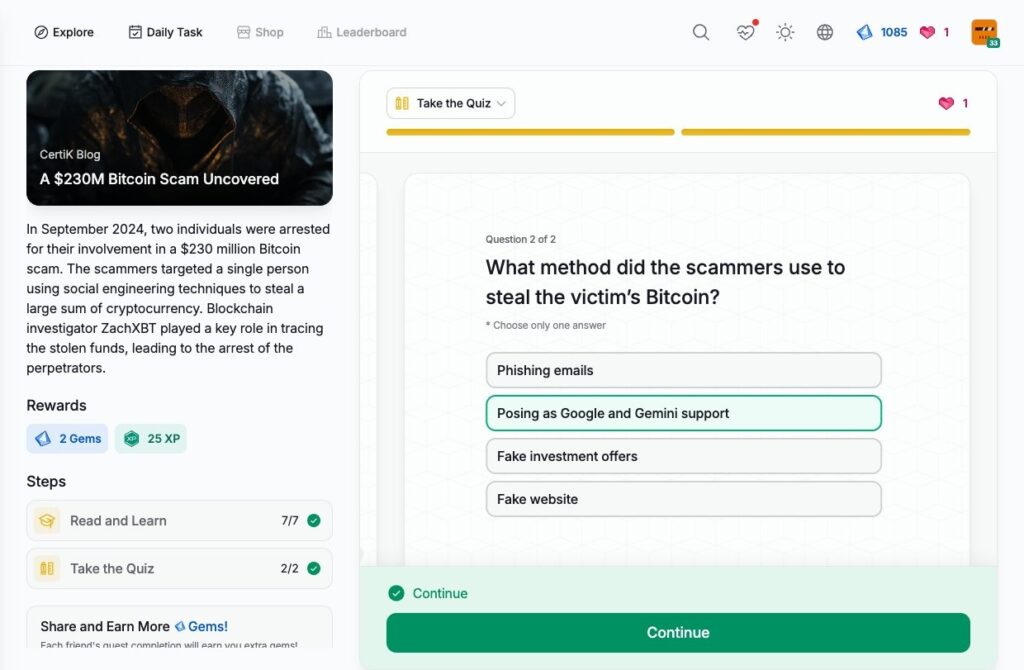
- A 0M Bitcoin Scam Uncovered
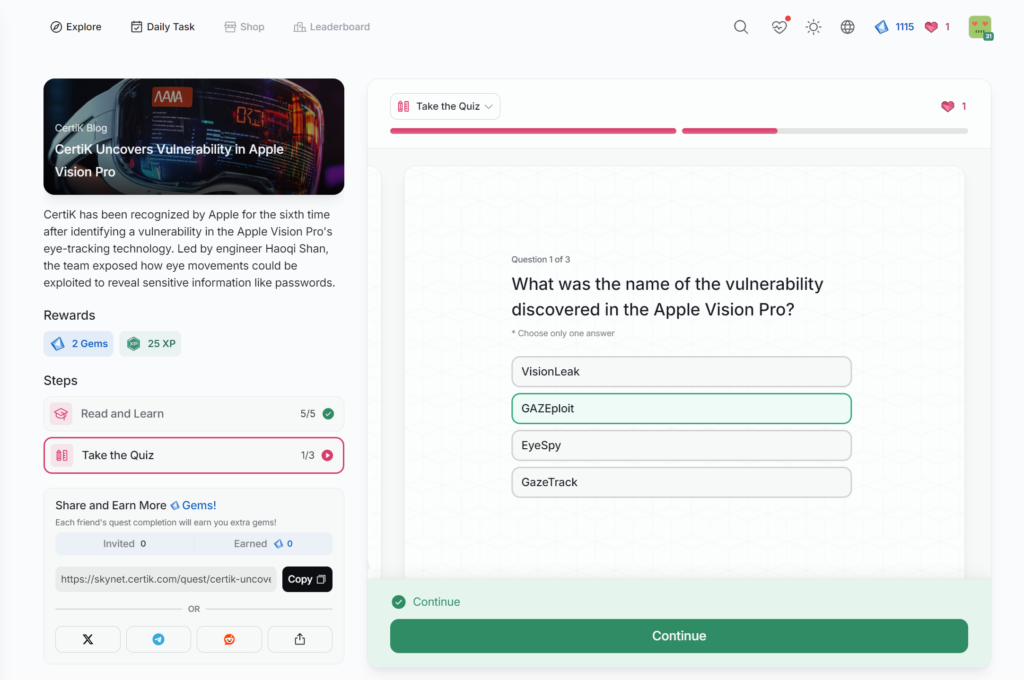
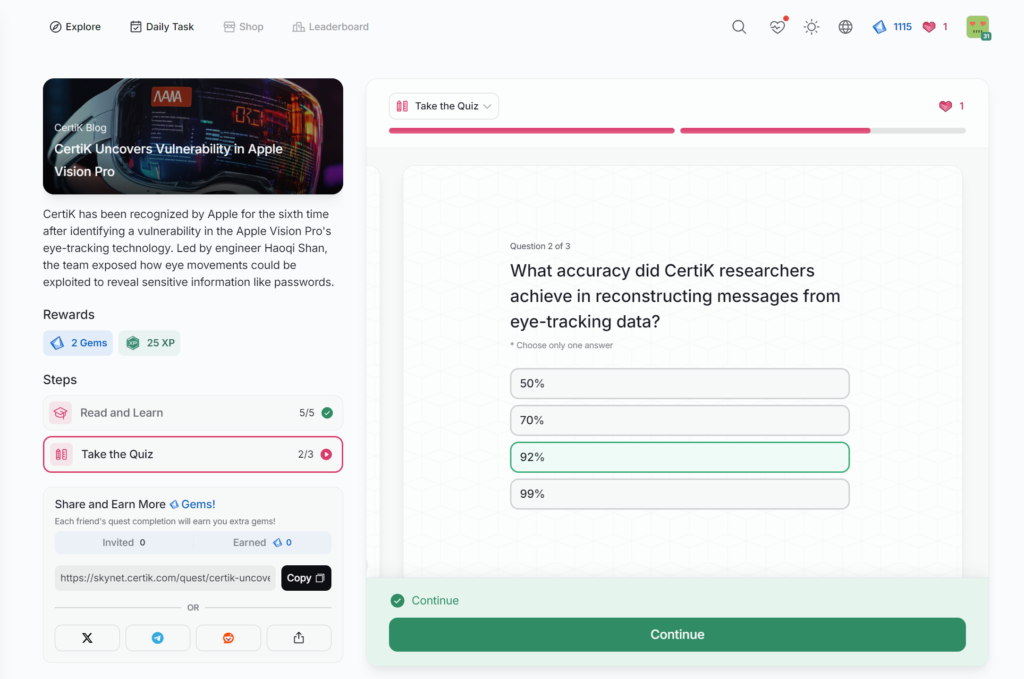
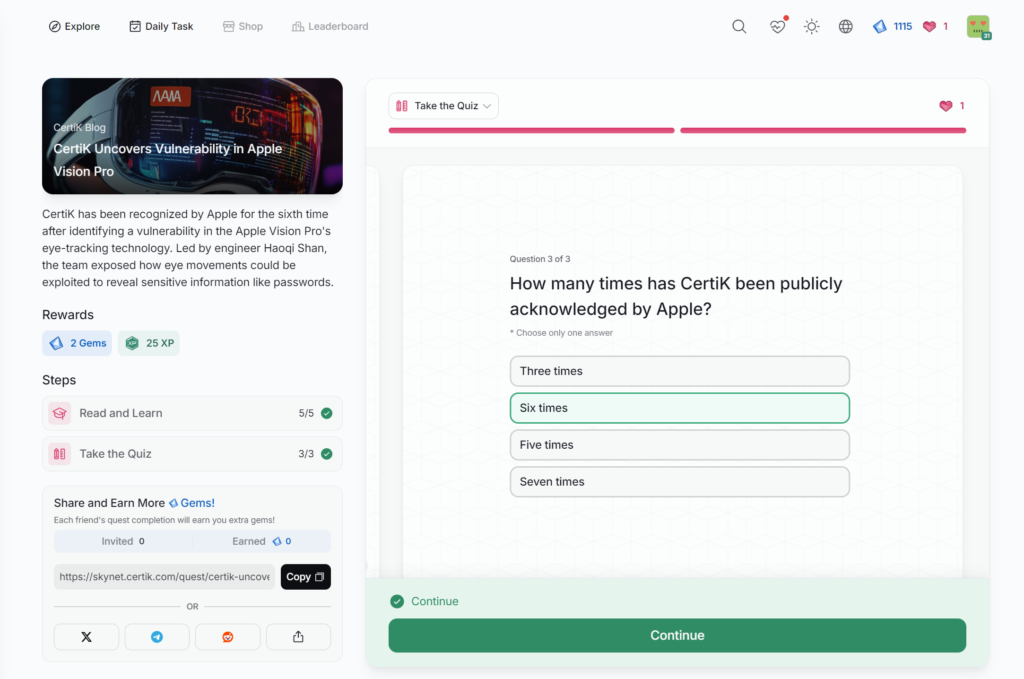
- CertiK Uncovers Vulnerability in Apple Vision Pro
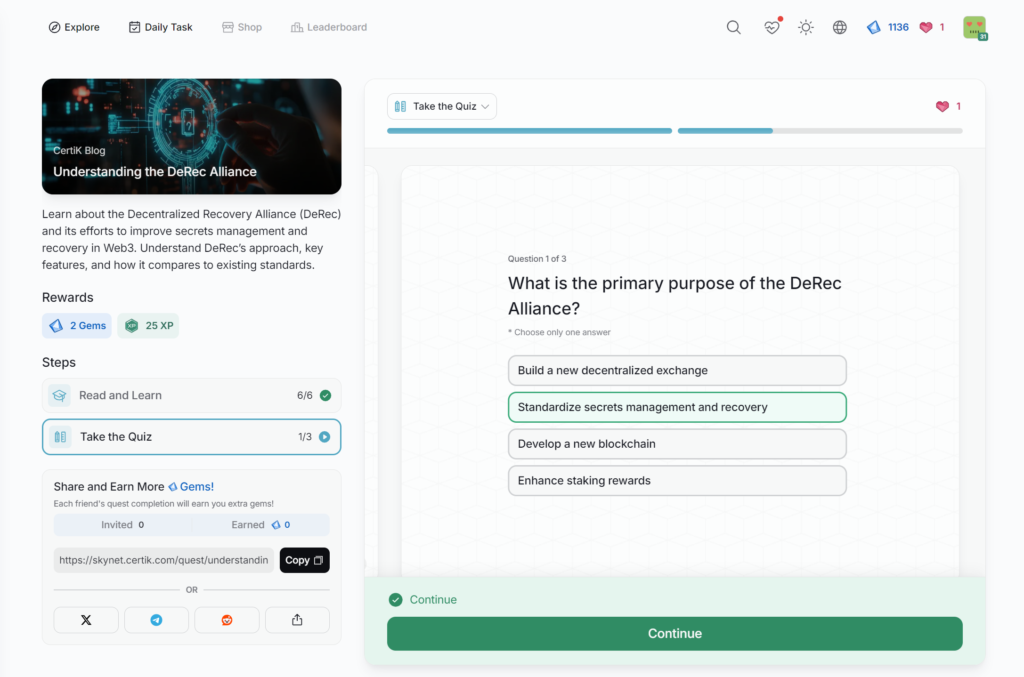
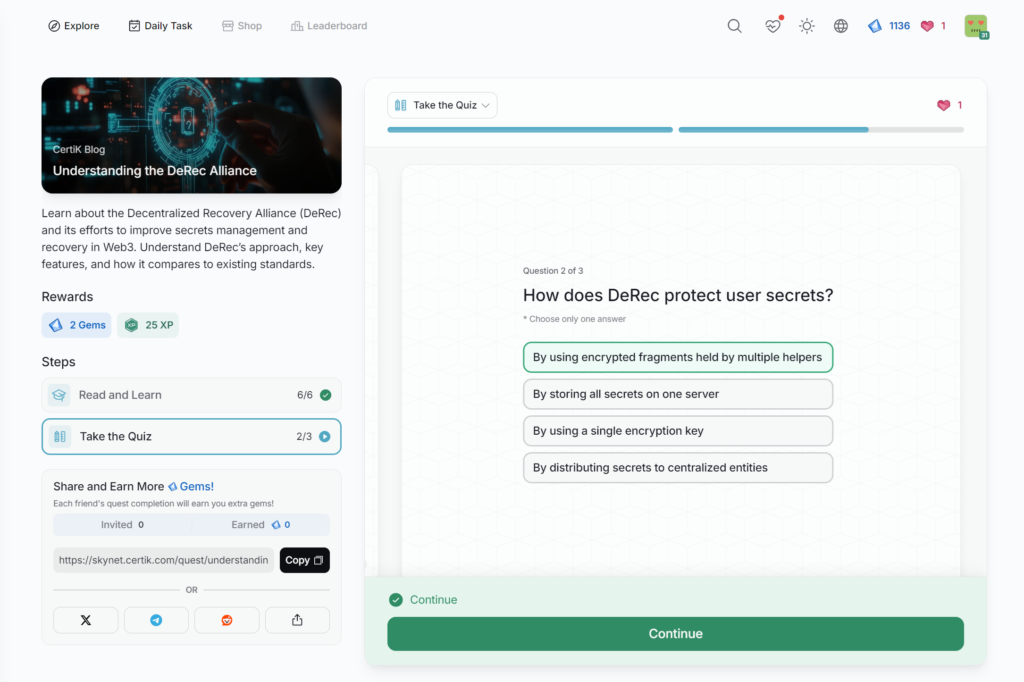
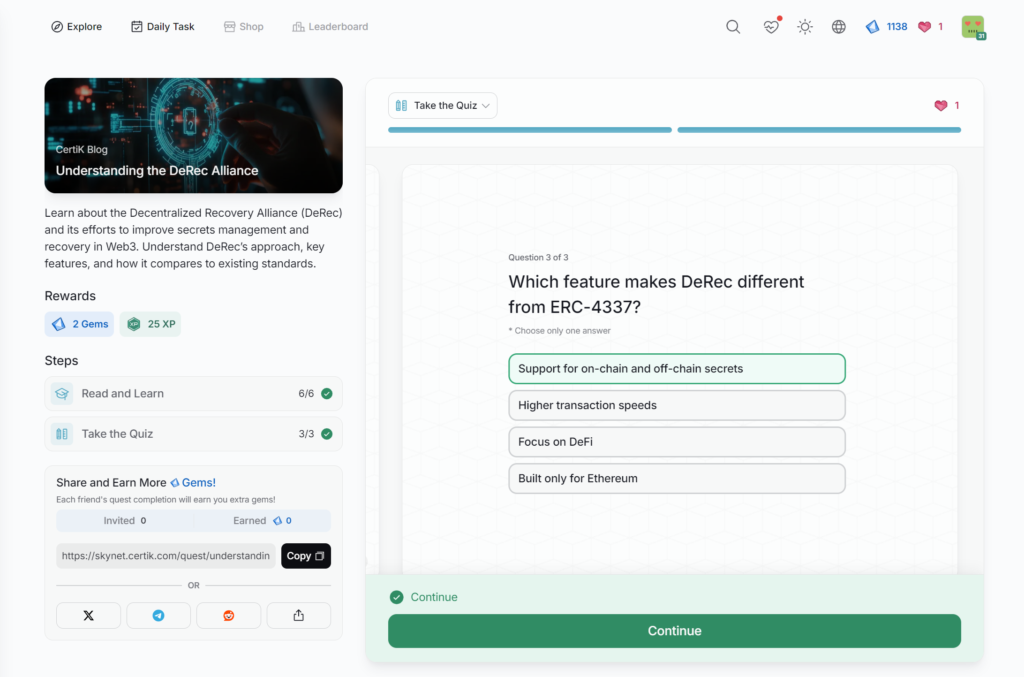
- Understanding the DeRec Alliance
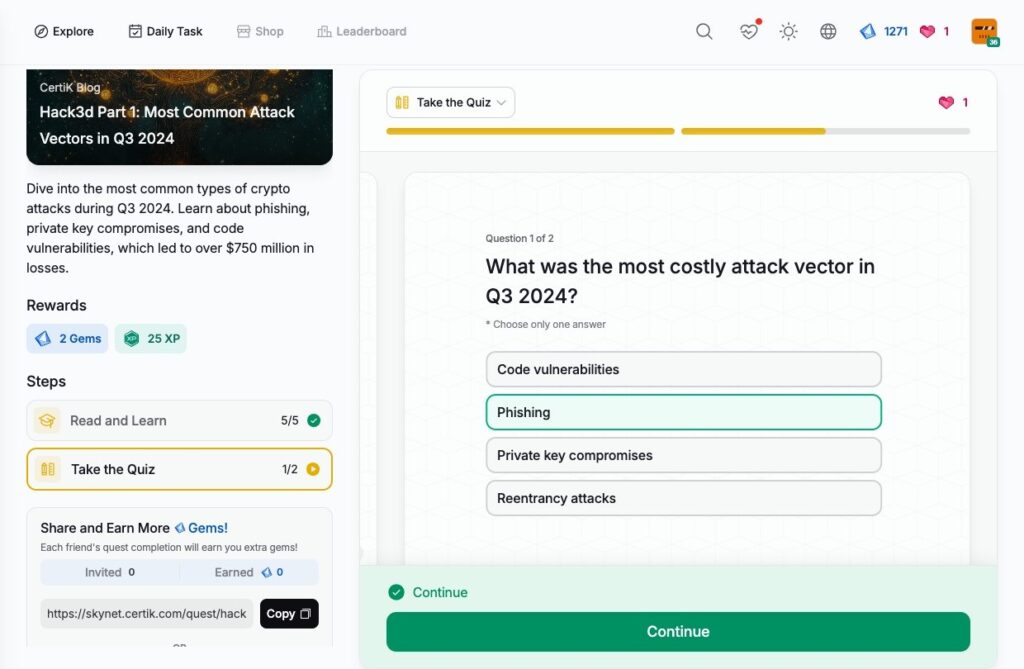
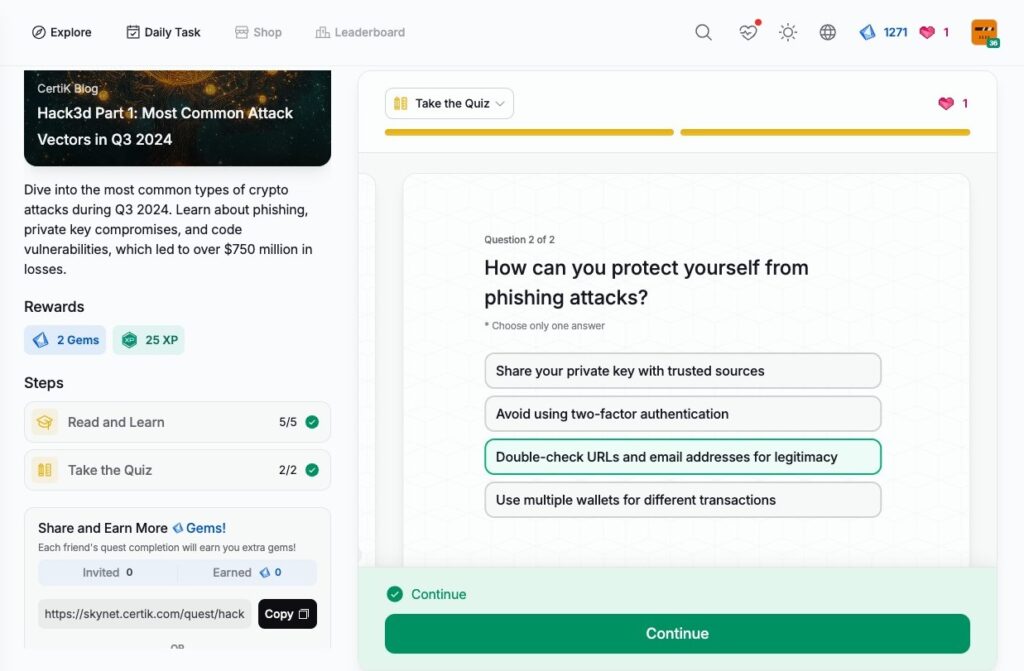
- Hack3d Part 1: Most Common Attack Vectors in Q3 2024
- Interview with Professor Ronghui Gu: “Who Monitors the Monitors?”
- Hack3d Part 2: Major Hacks of Q3 2024
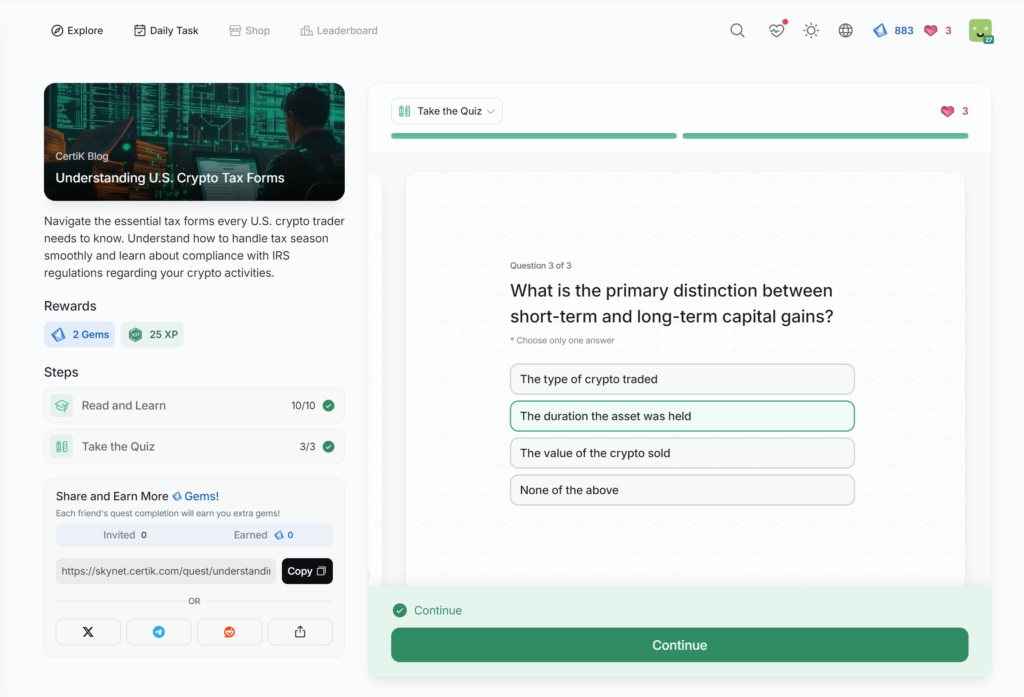
- Understanding U.S. Crypto Tax Forms
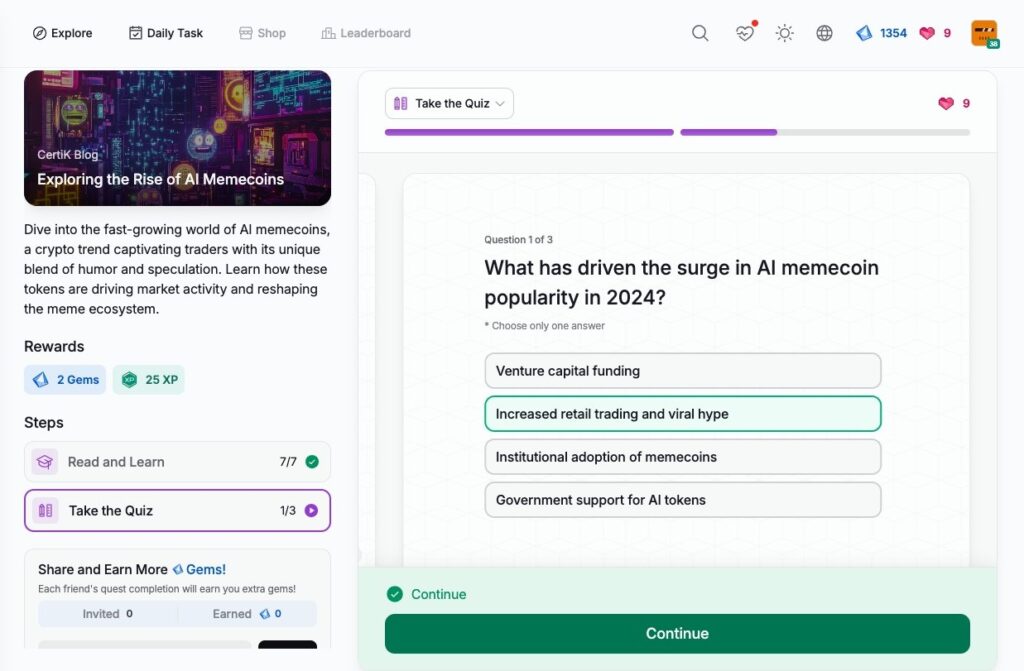
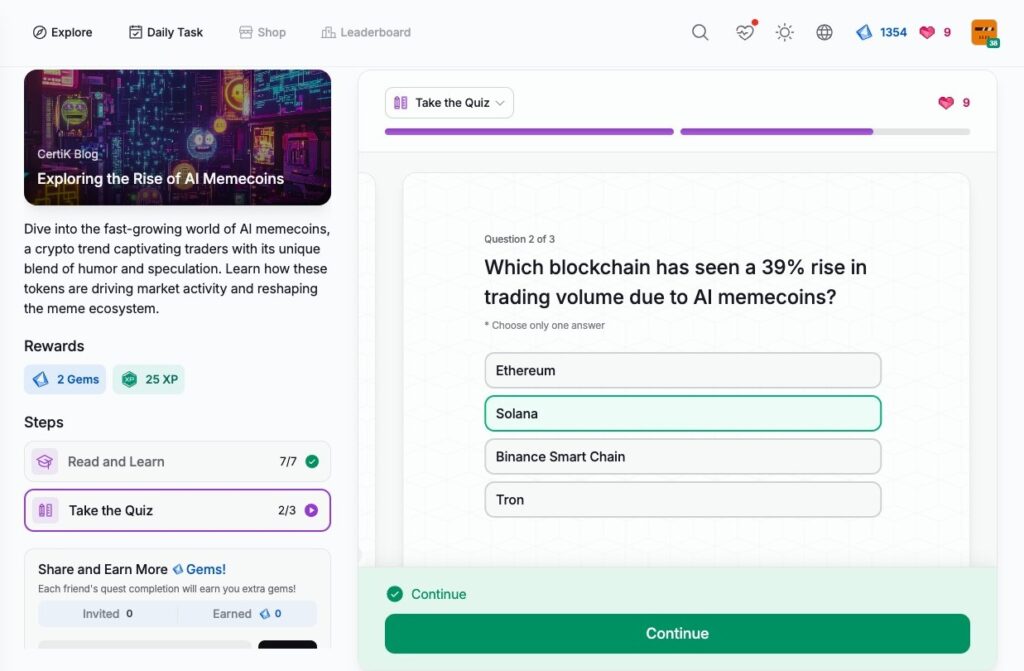
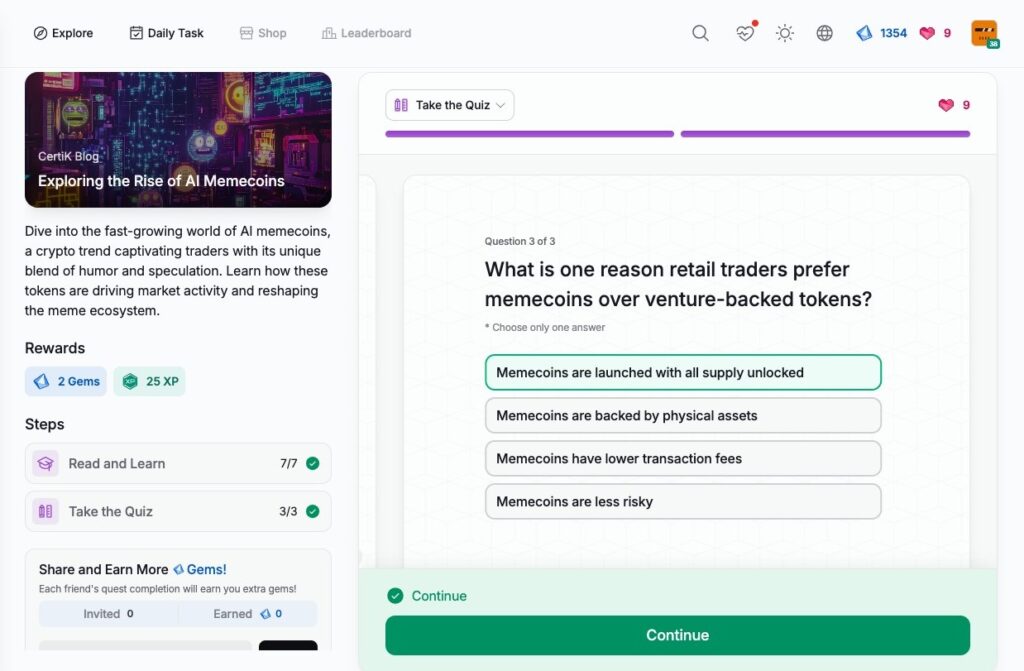
- Exploring the Rise of AI Memecoins
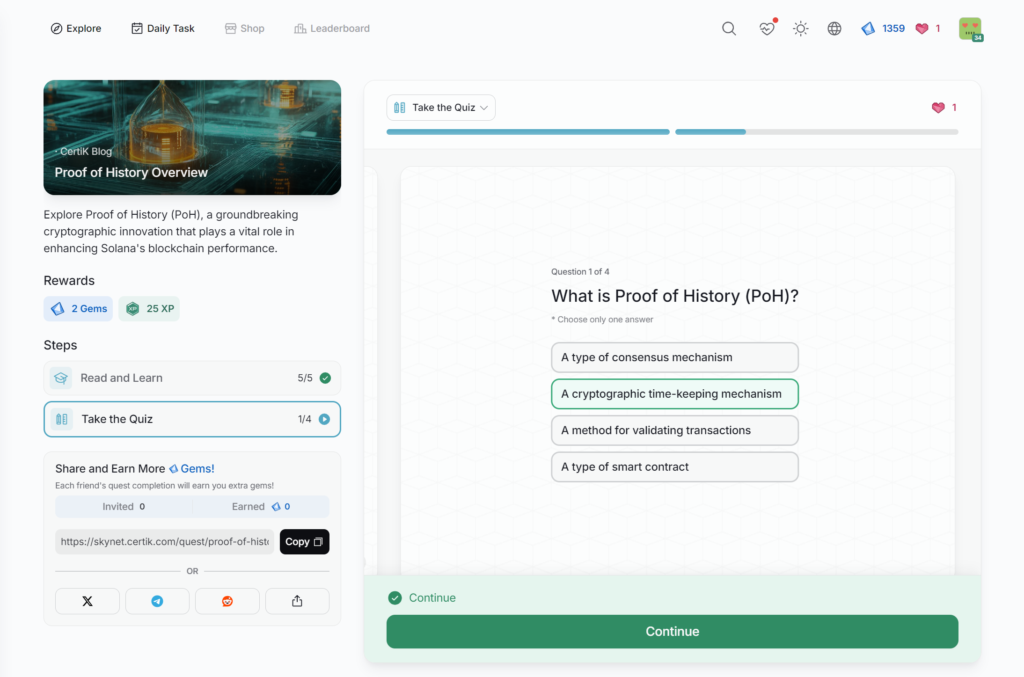
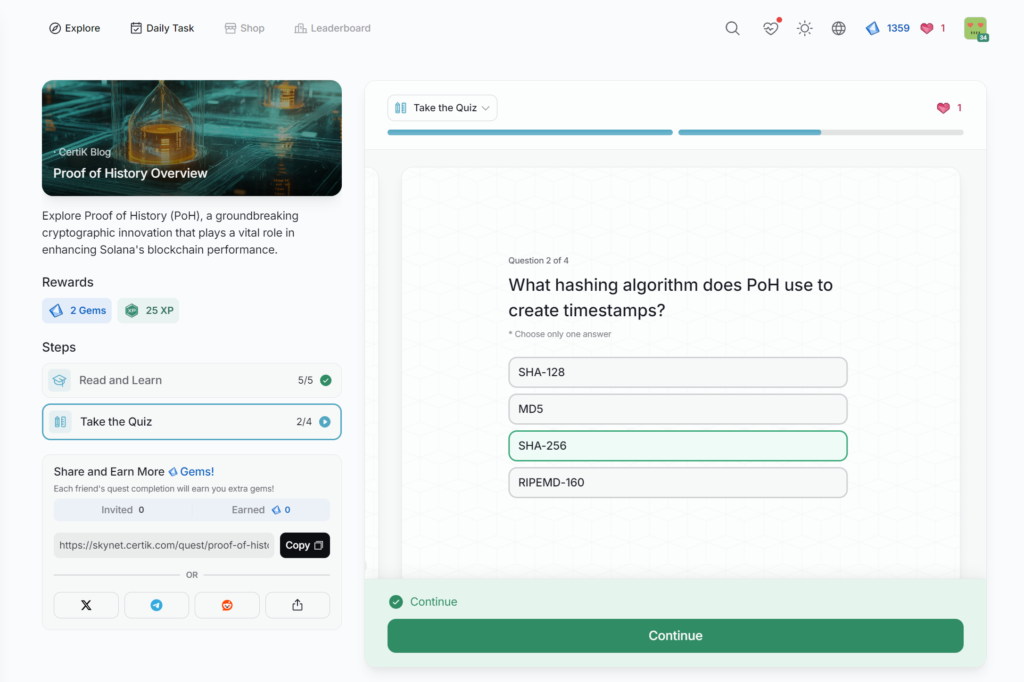
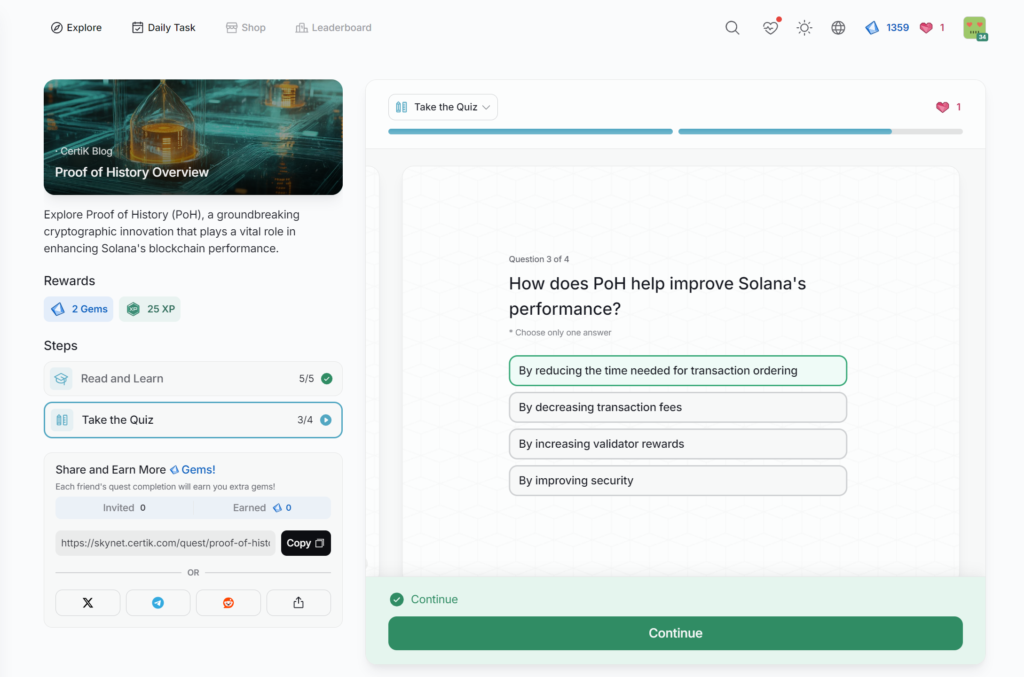
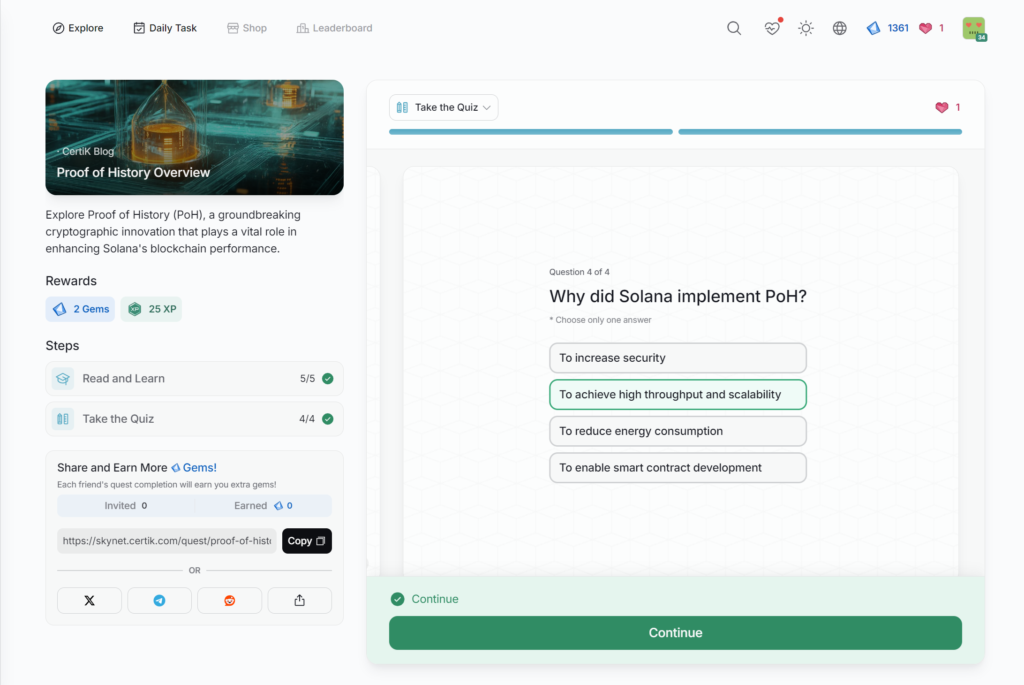
- Proof of History Overview
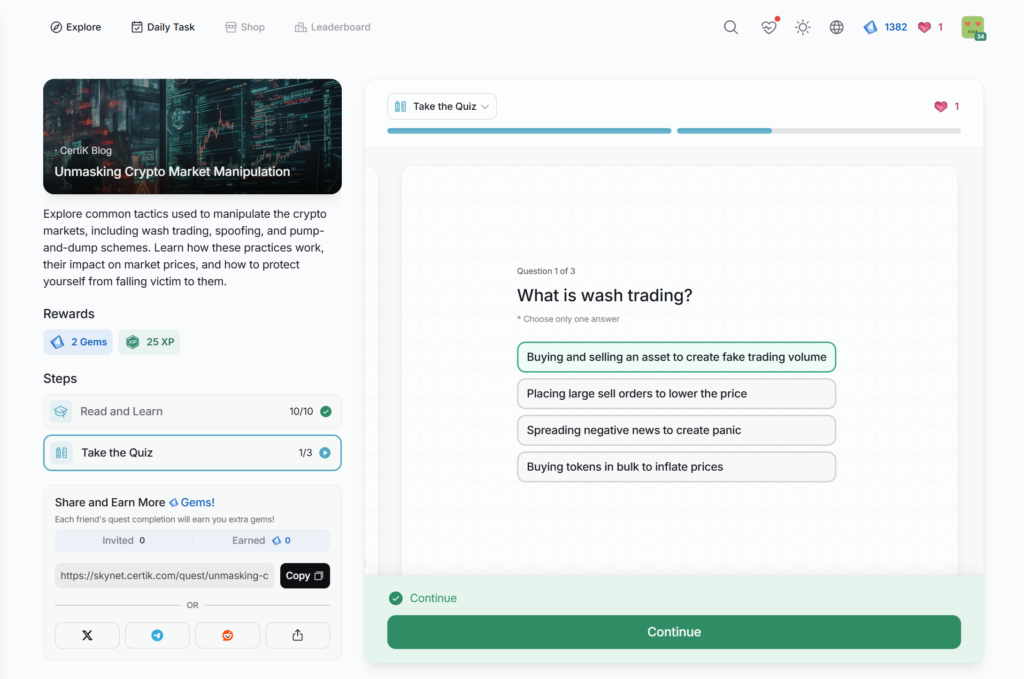
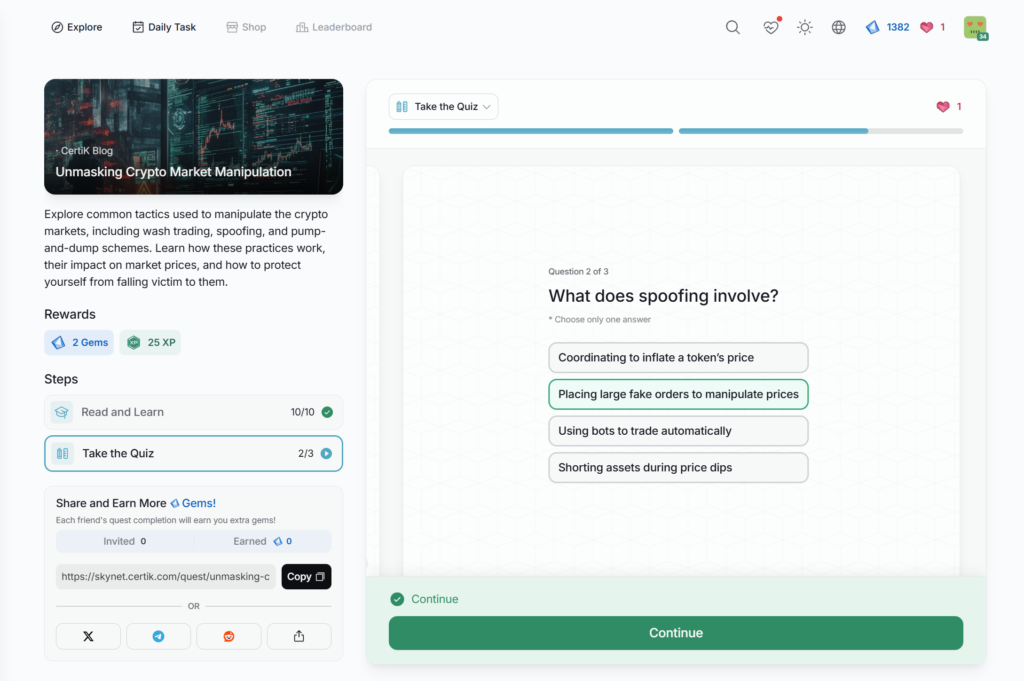
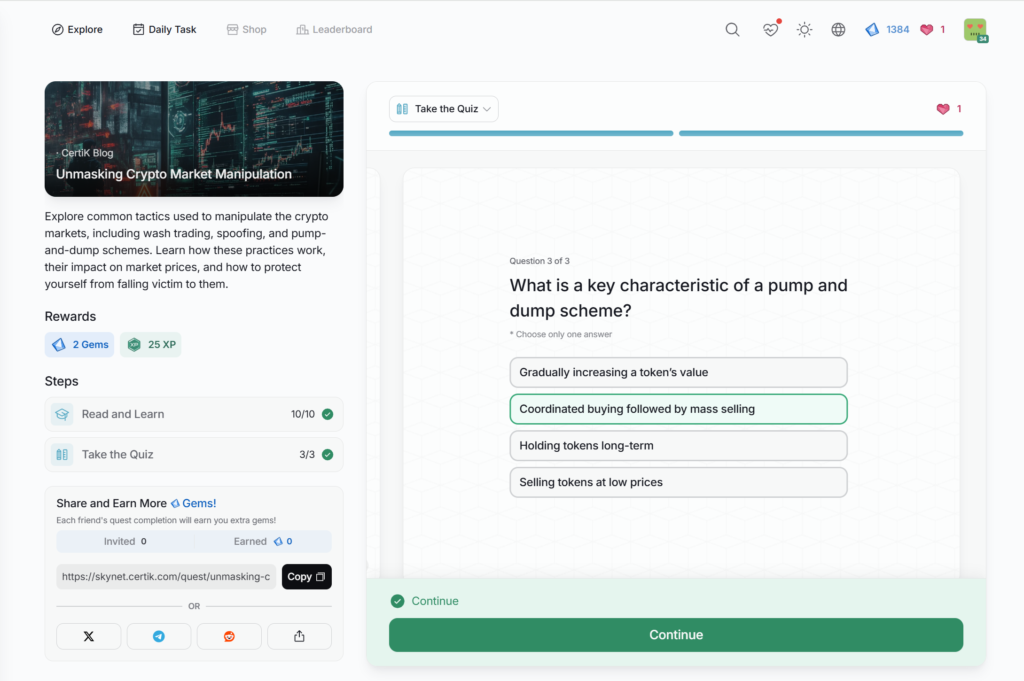
- Unmasking Crypto Market Manipulation
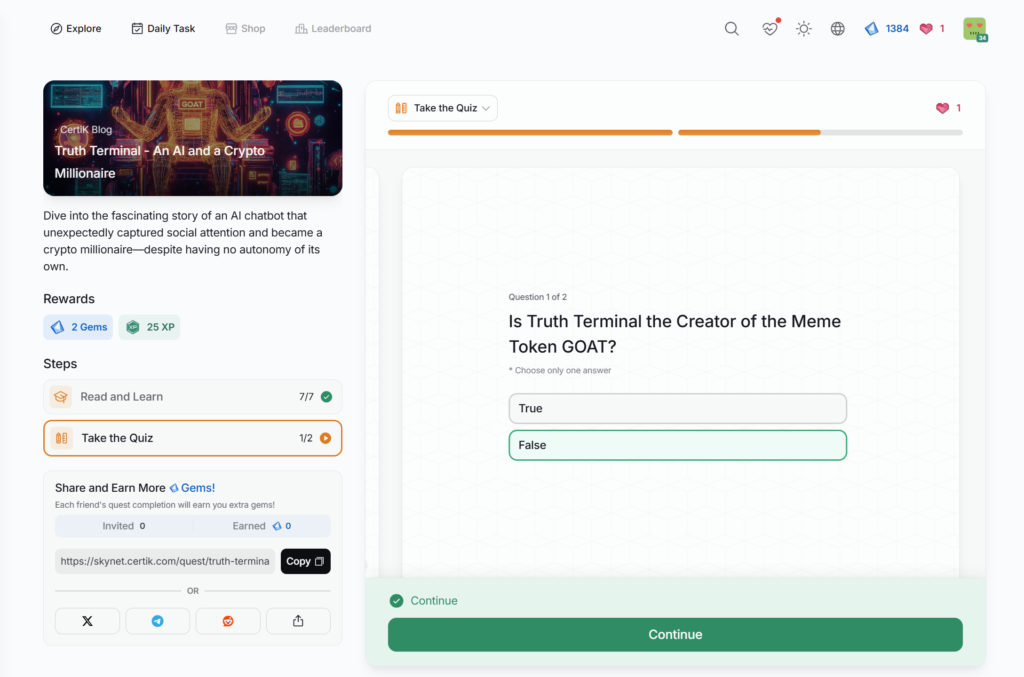
- Truth Terminal – An AI and a Crypto Millionaire
- AI Memecoins Explained: The New Craze in Crypto
- The Power of Hashing
- Evaluating Memecoin Liquidity
- Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan – Part 1
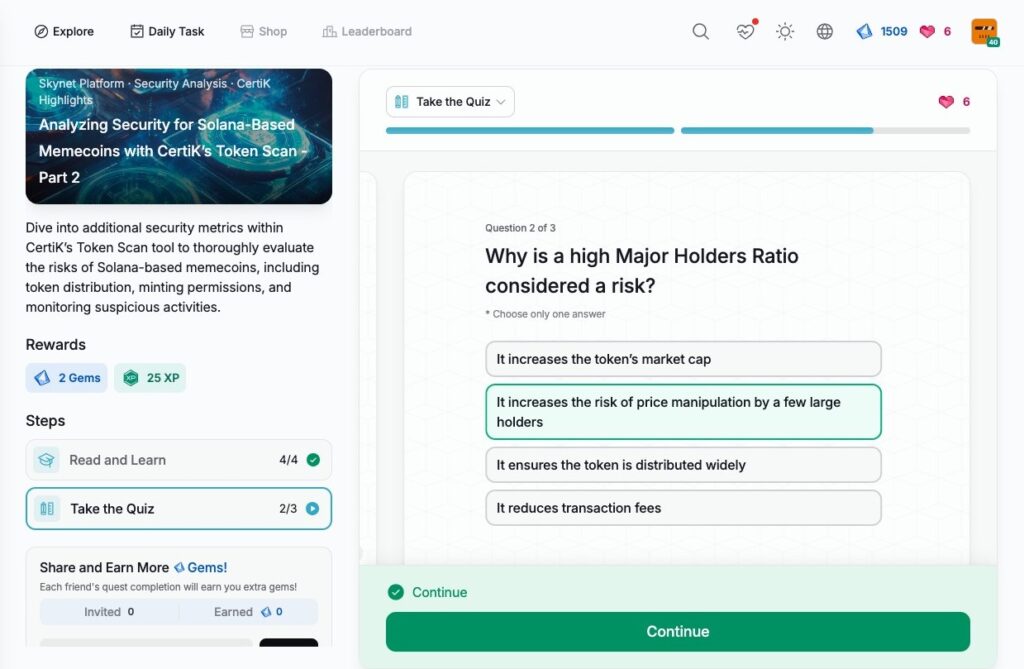
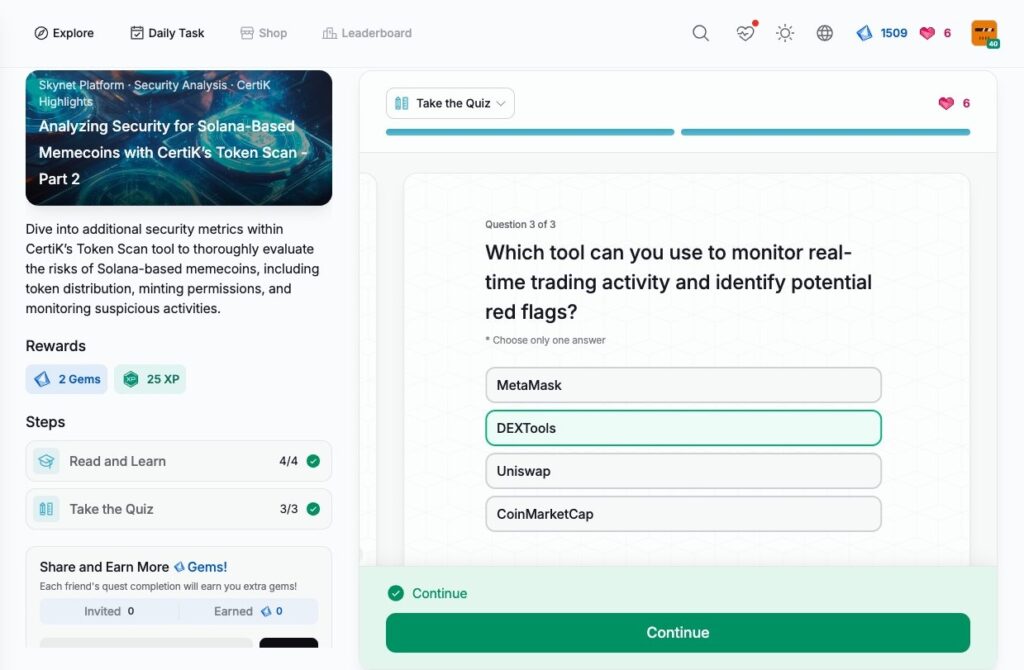
- Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan – Part 2
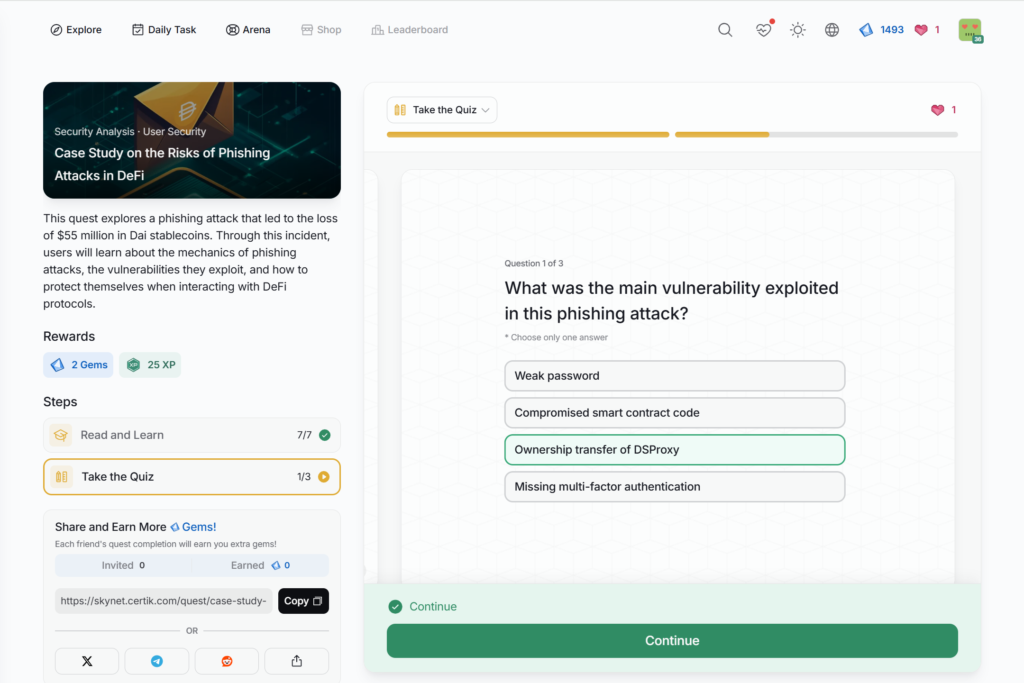
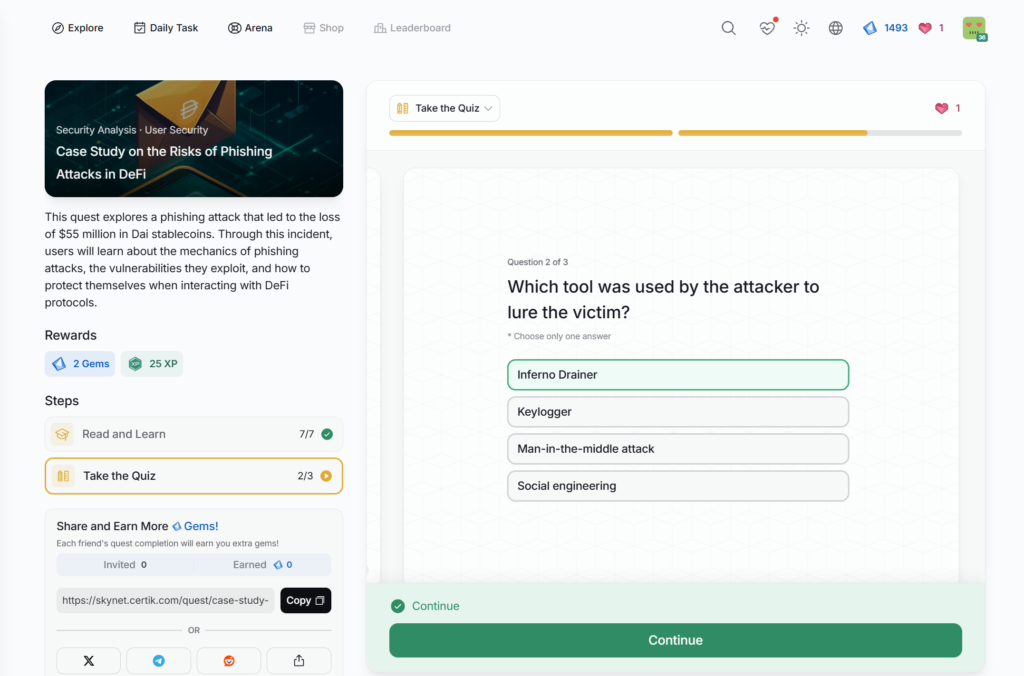
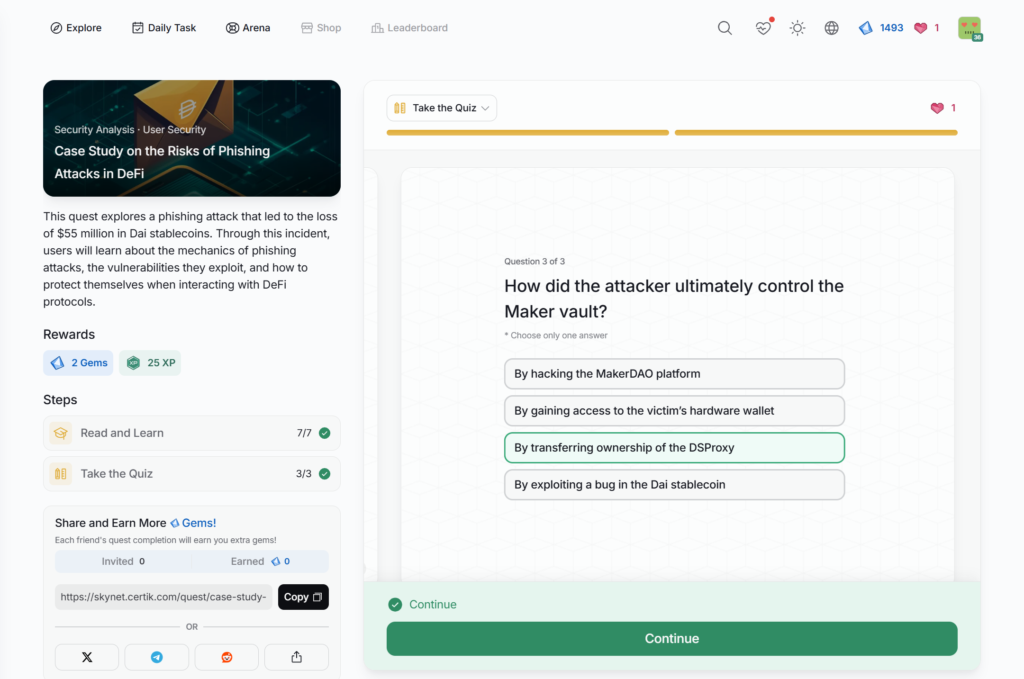
- Case Study on the Risks of Phishing Attacks in DeFi
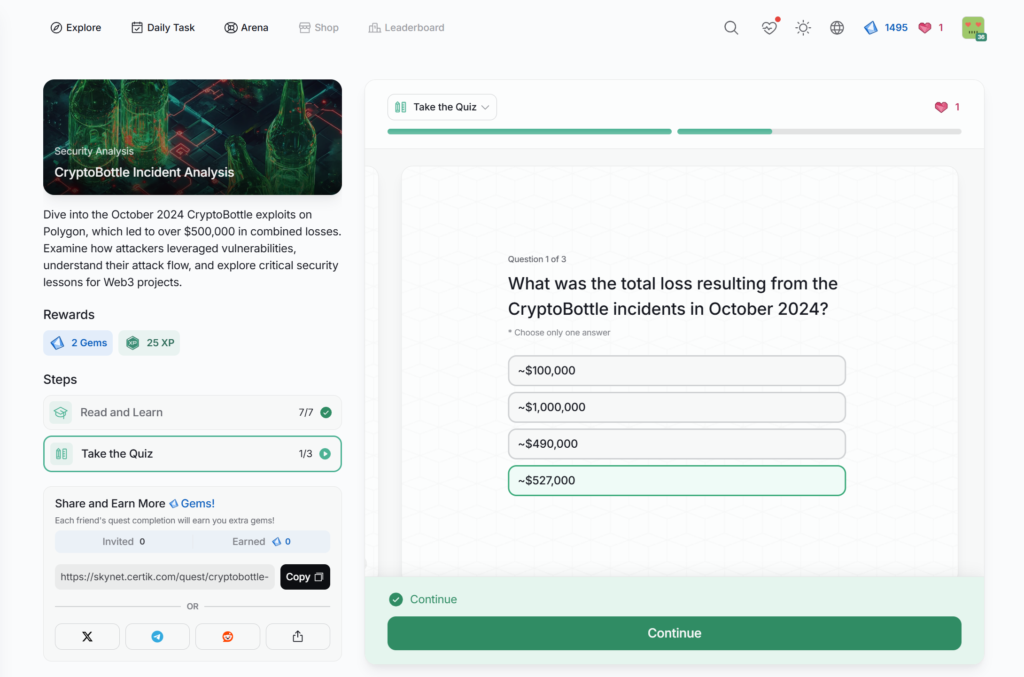
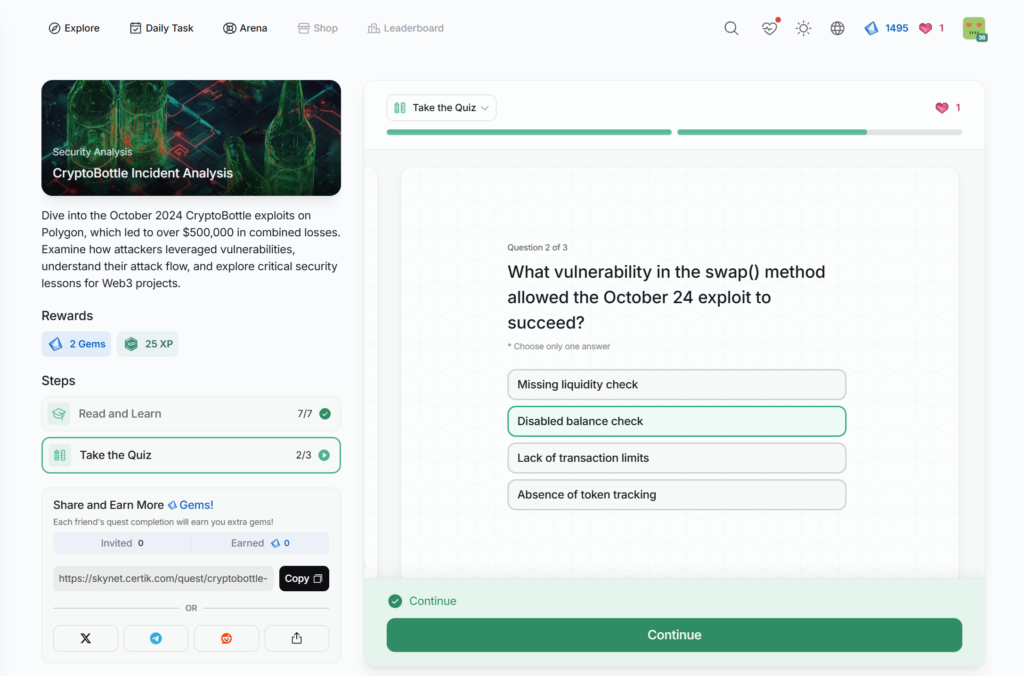
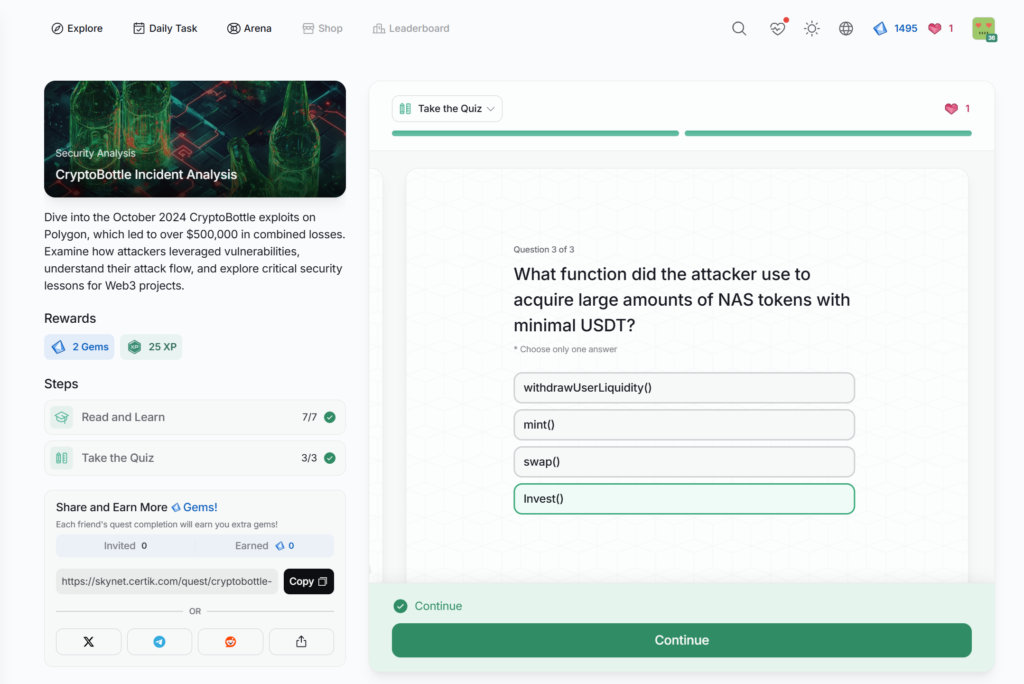
- CryptoBottle Incident Analysis
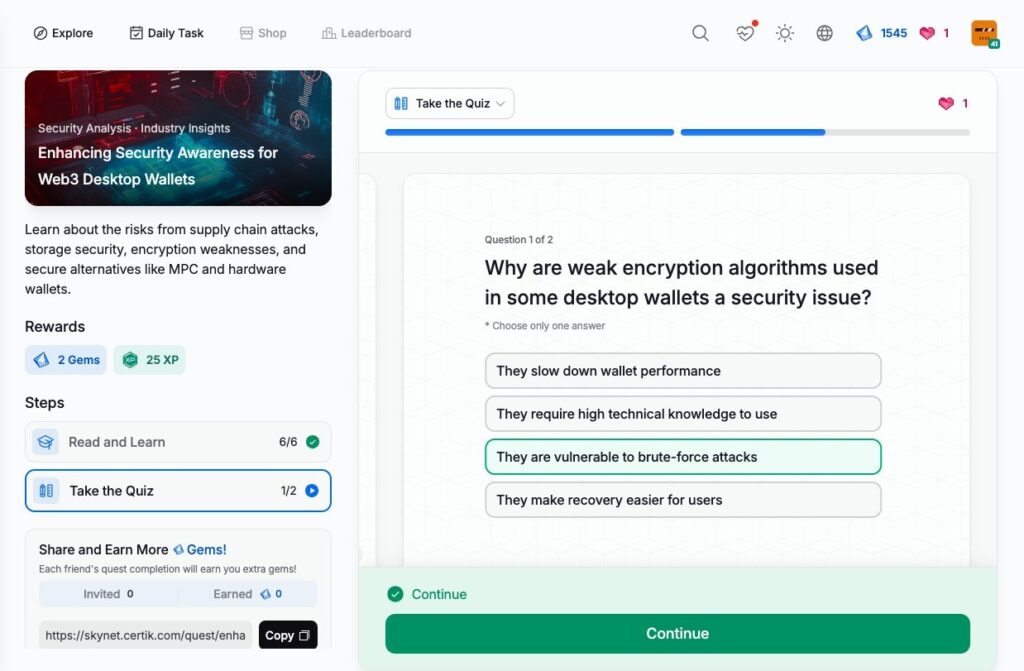
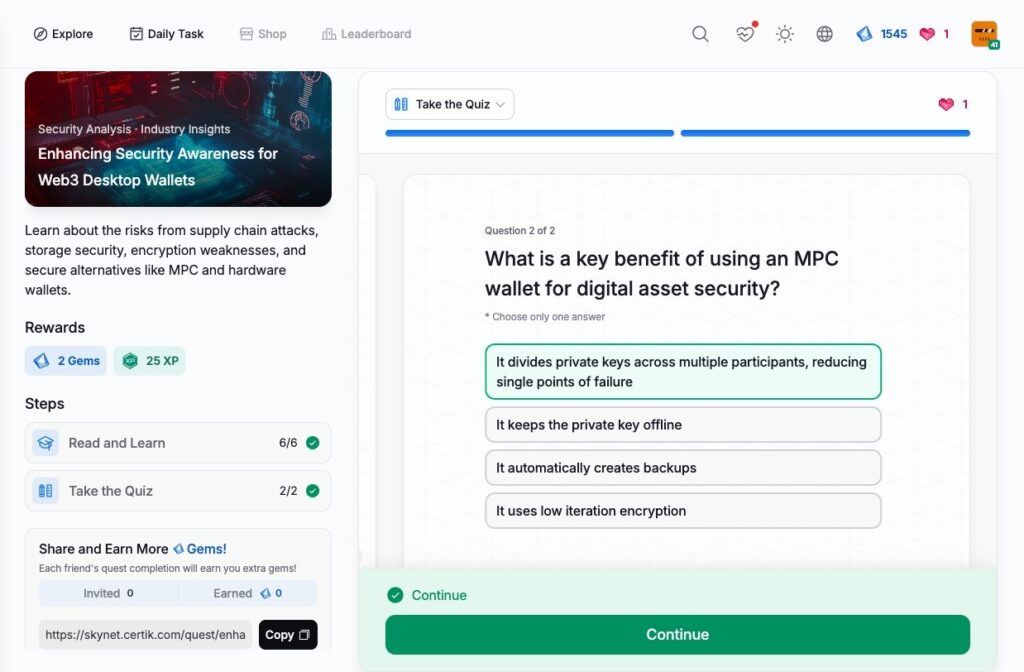
- Enhancing Security Awareness for Web3 Desktop Wallets
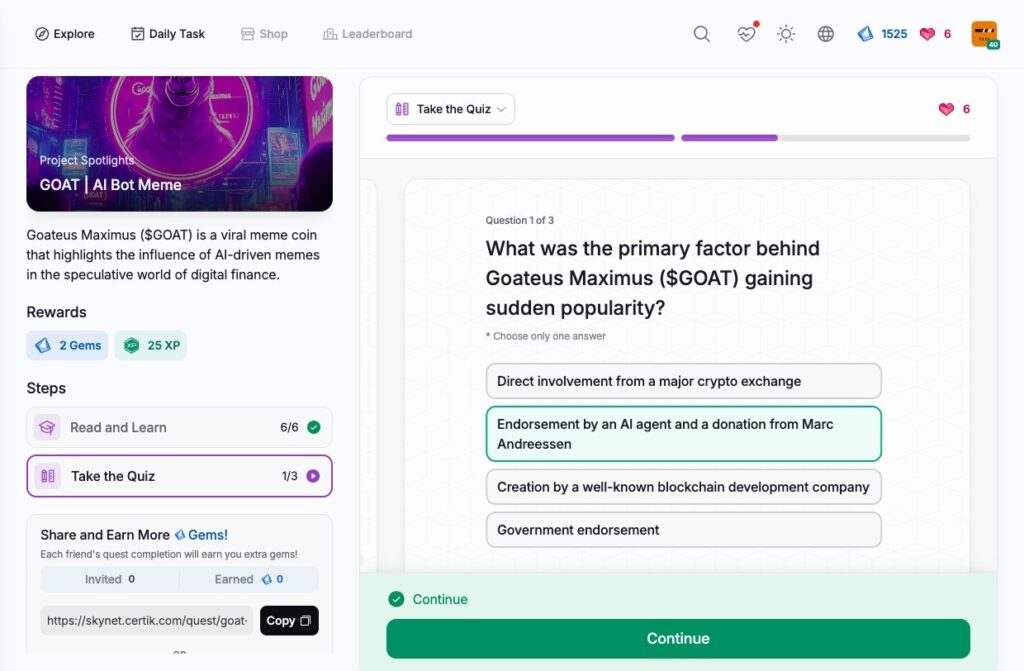
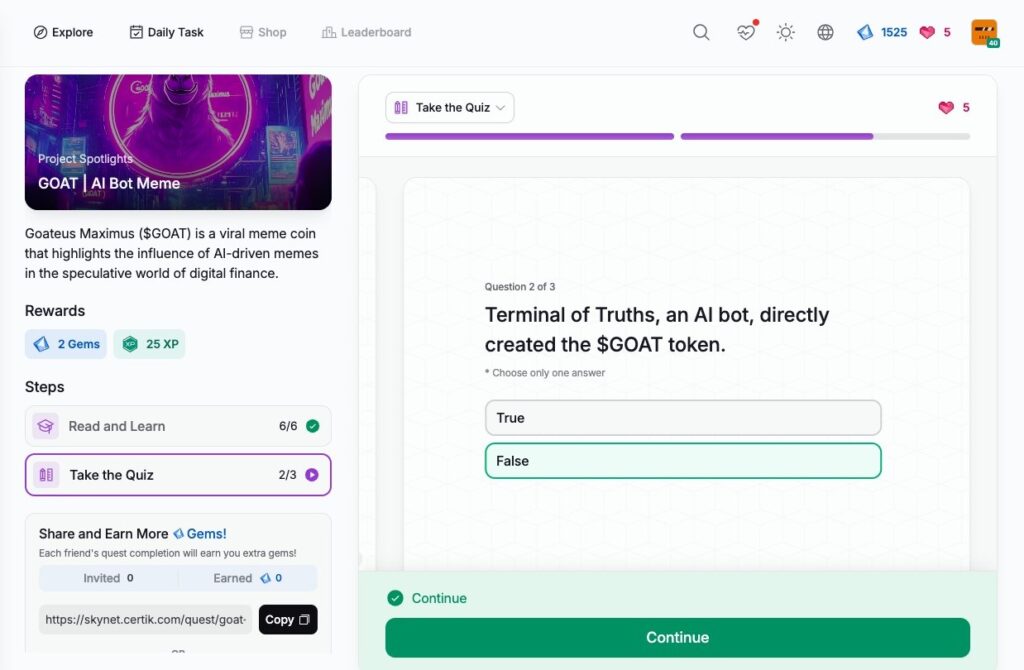
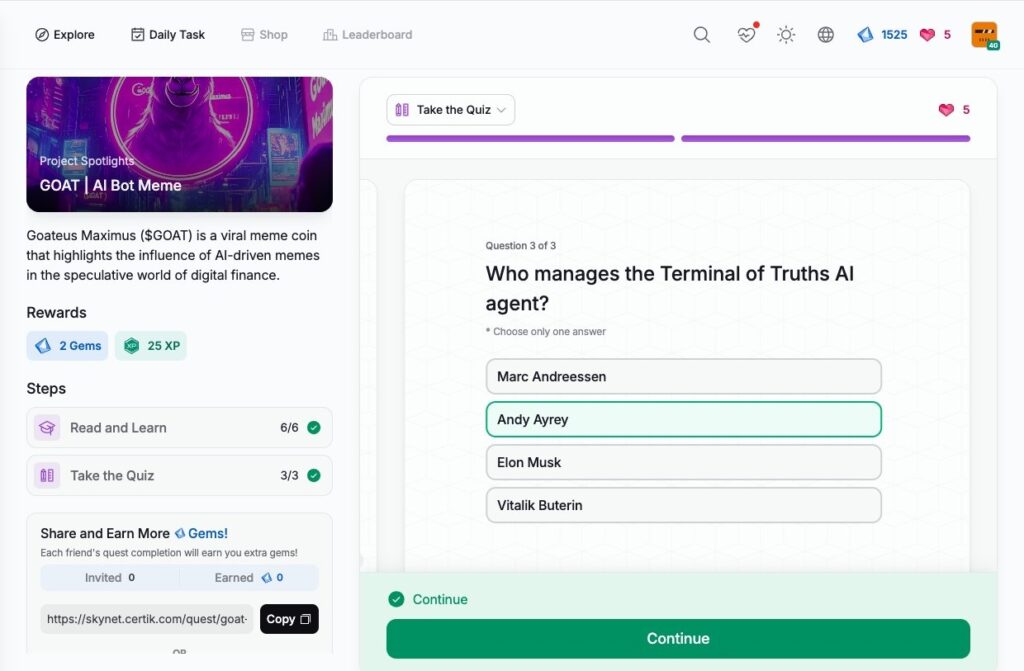
- GOAT | AI Bot Meme
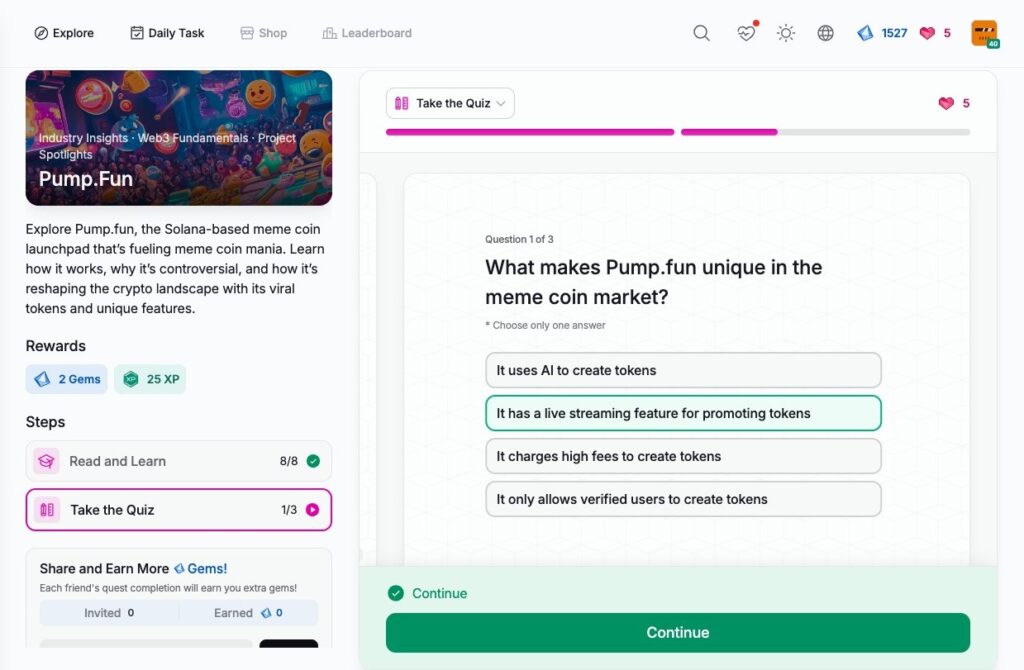
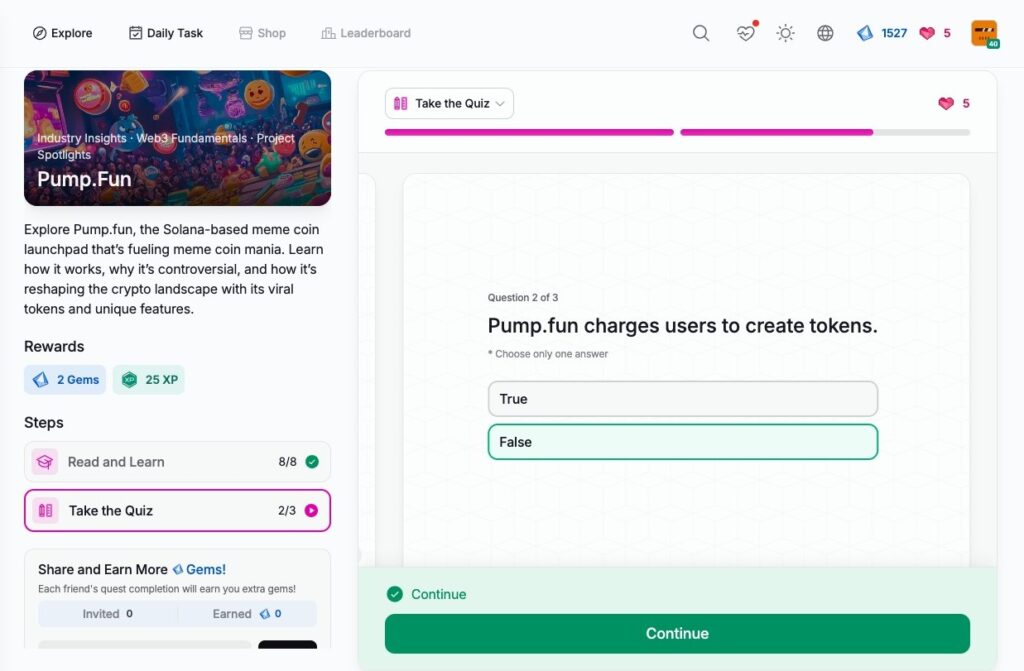
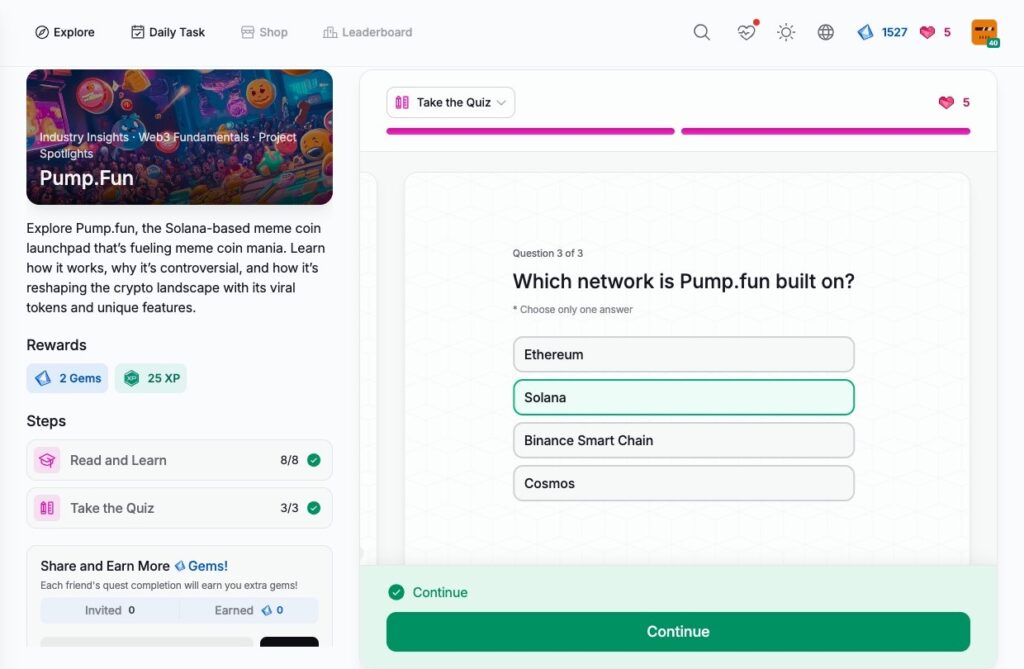
- Pump.Fun
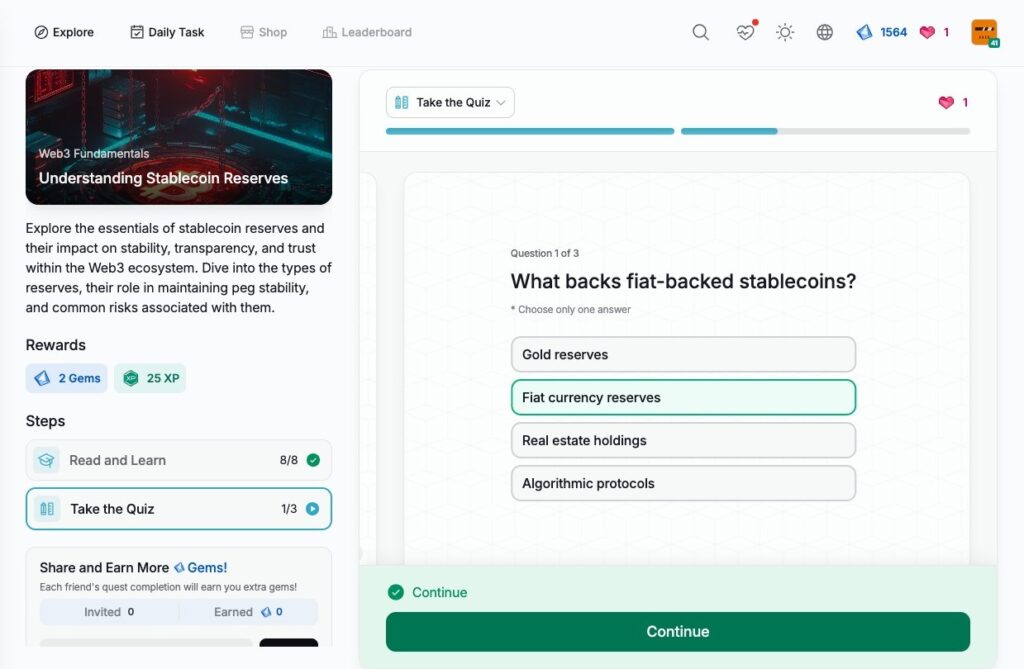
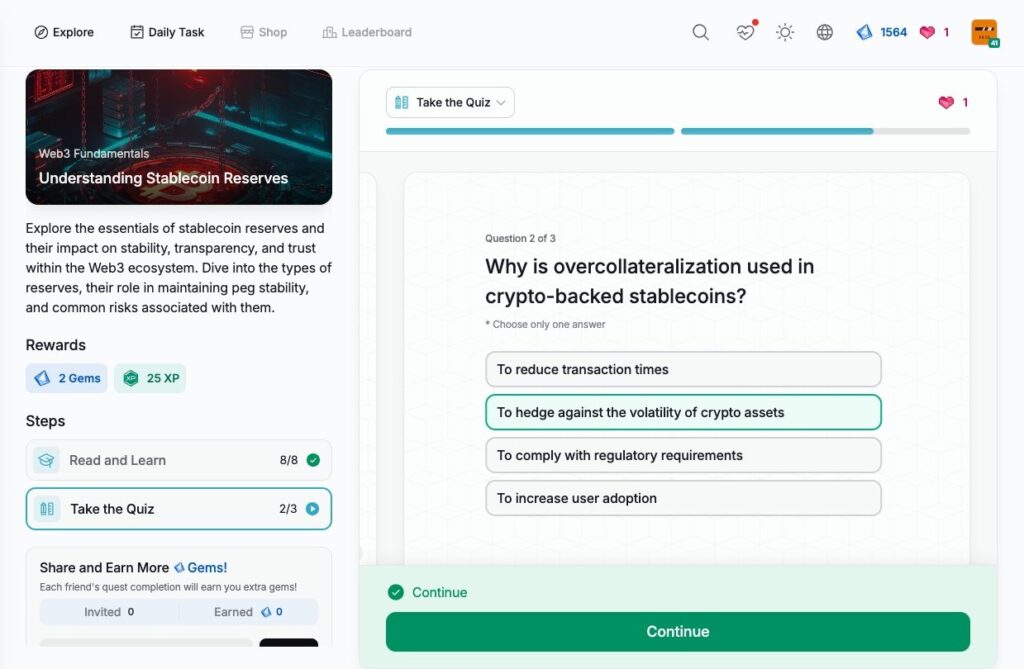
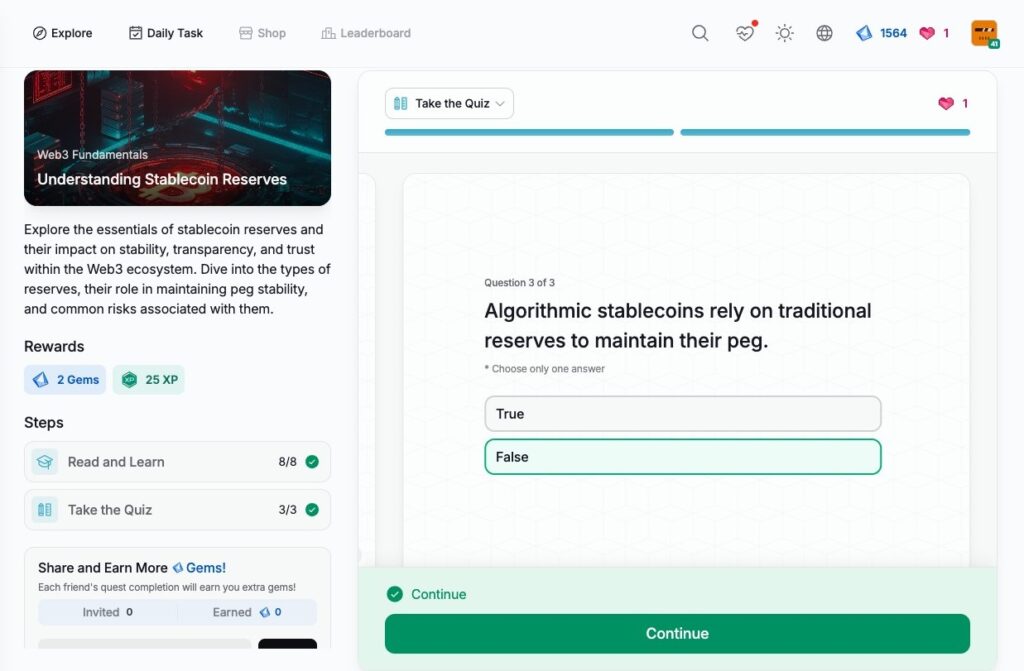
- Understanding Stablecoin Reserves
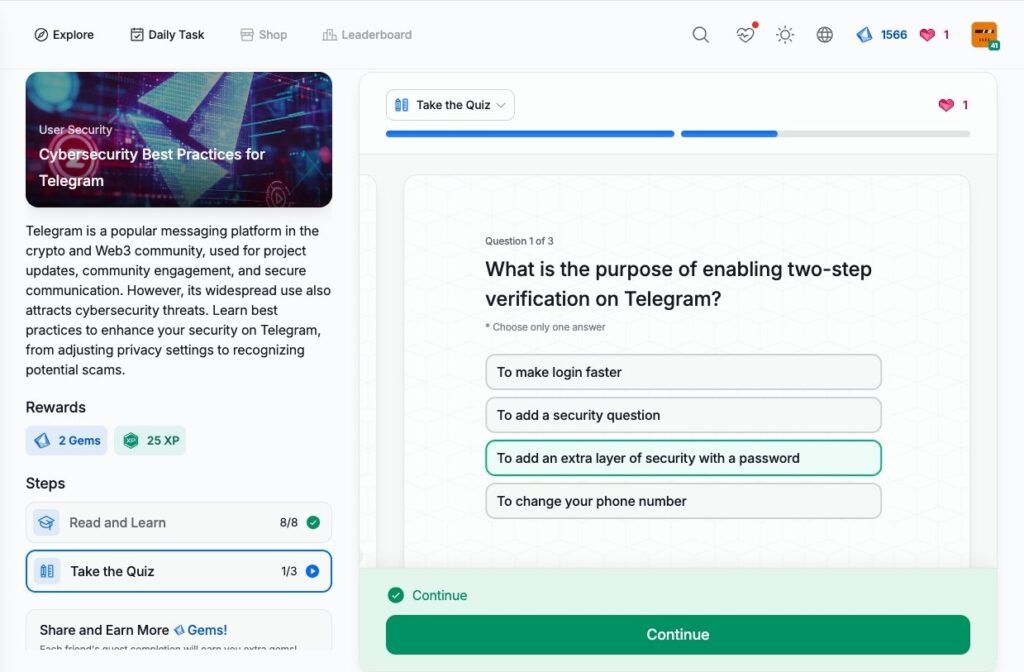
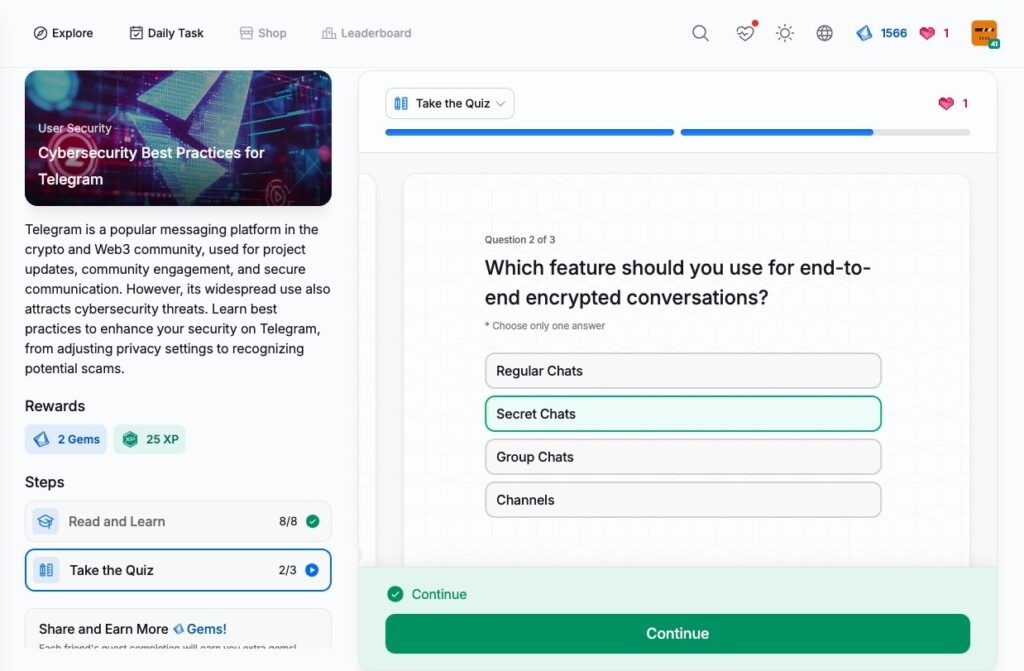
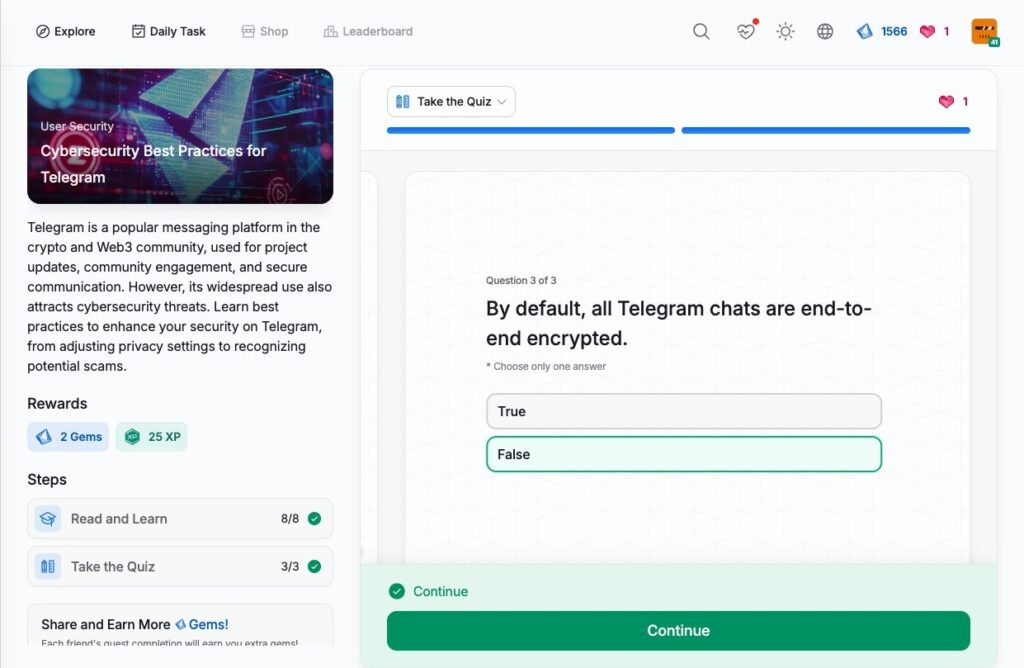
- Cybersecurity Best Practices for Telegram
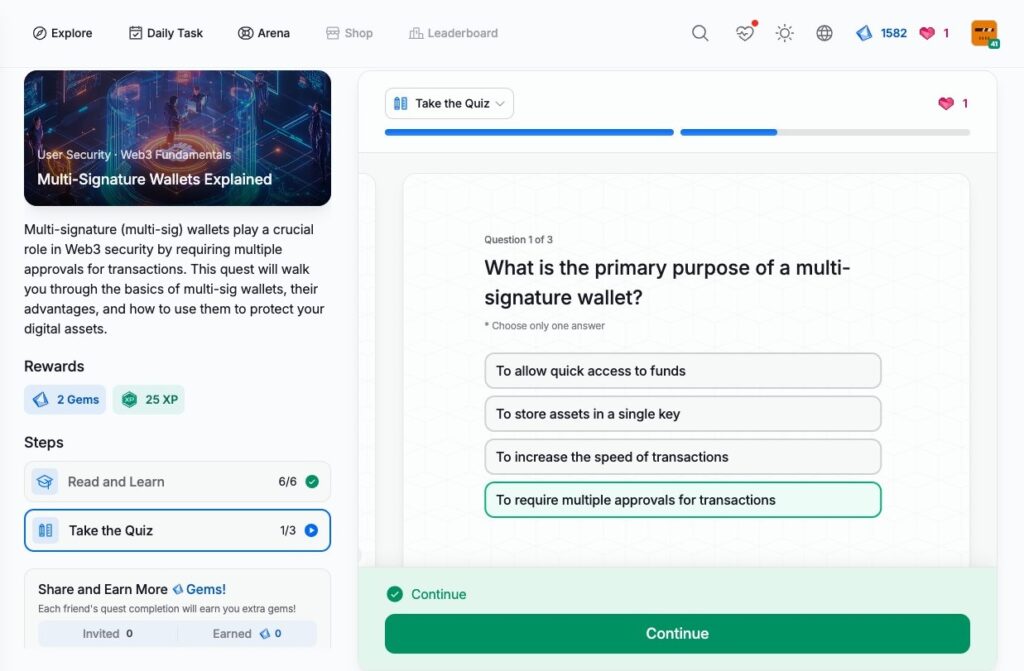
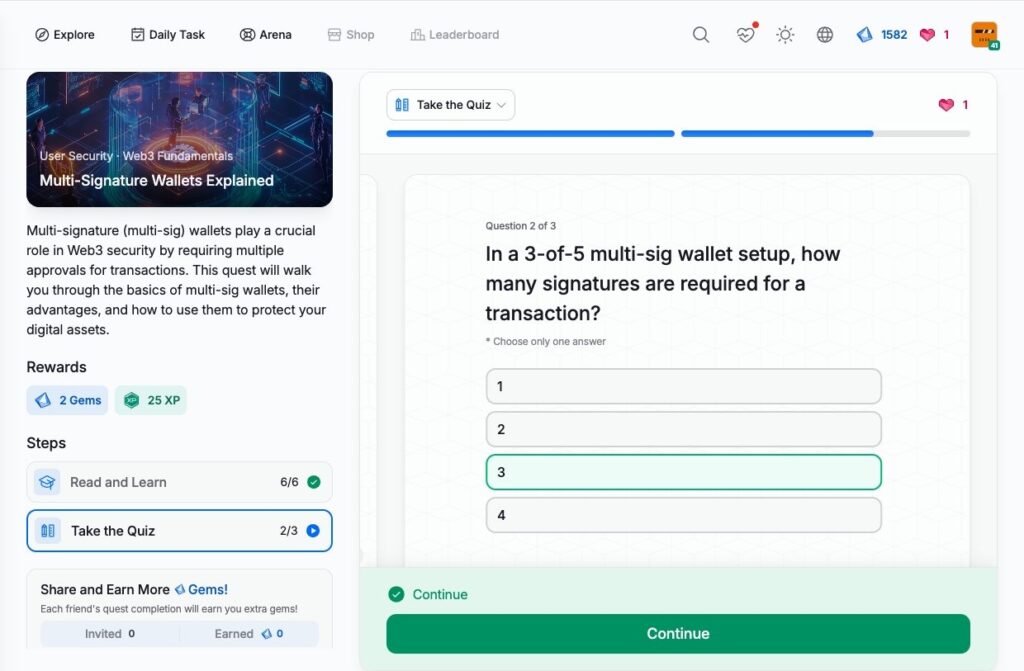
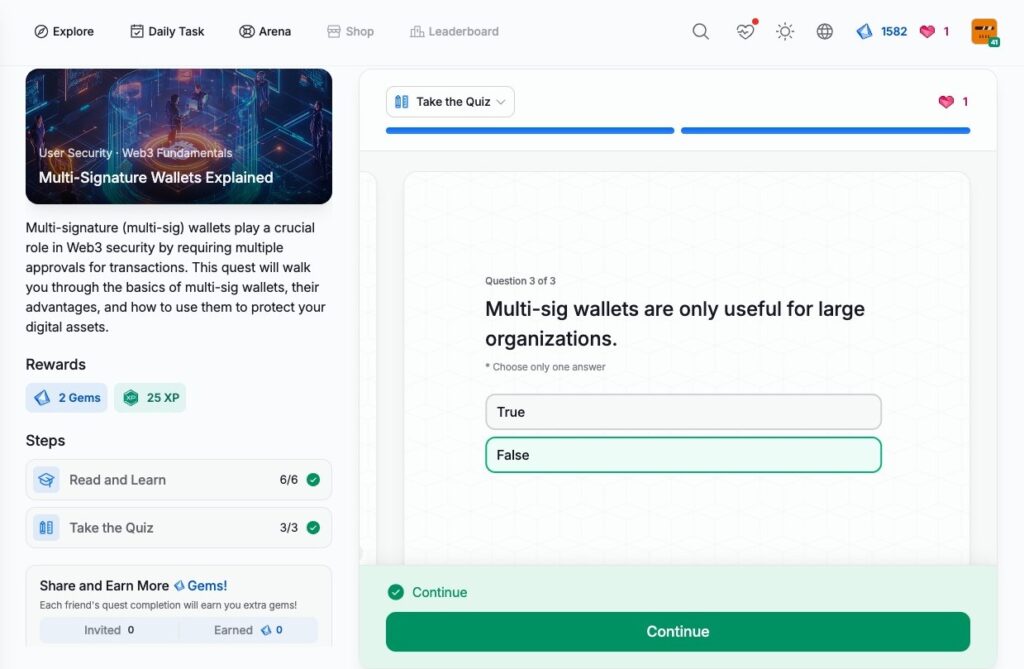
- Multi-Signature Wallets Explained
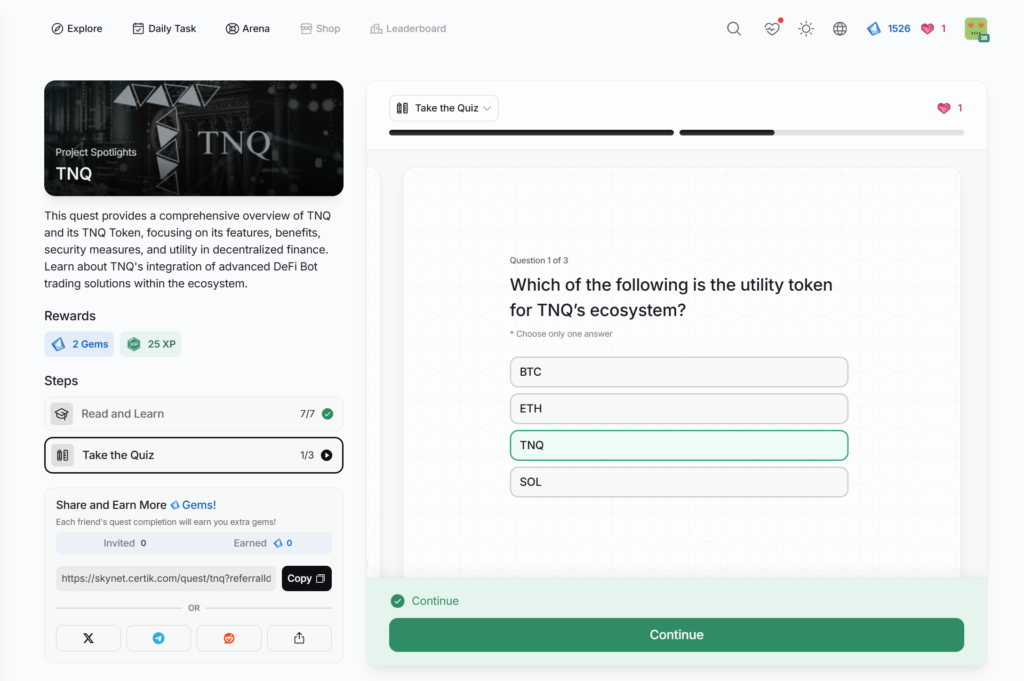
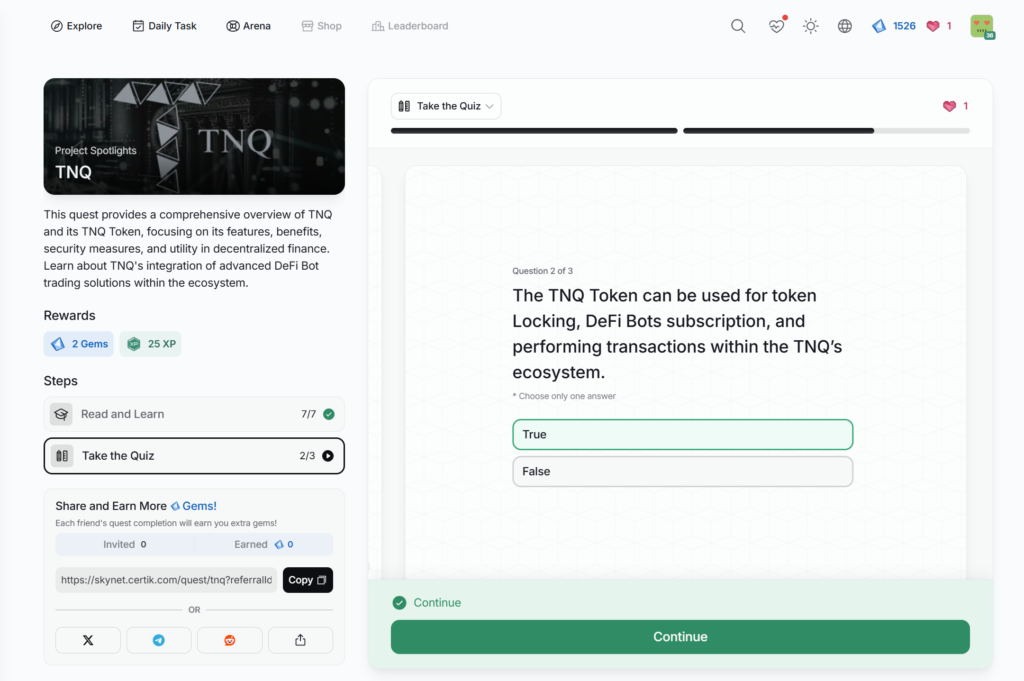
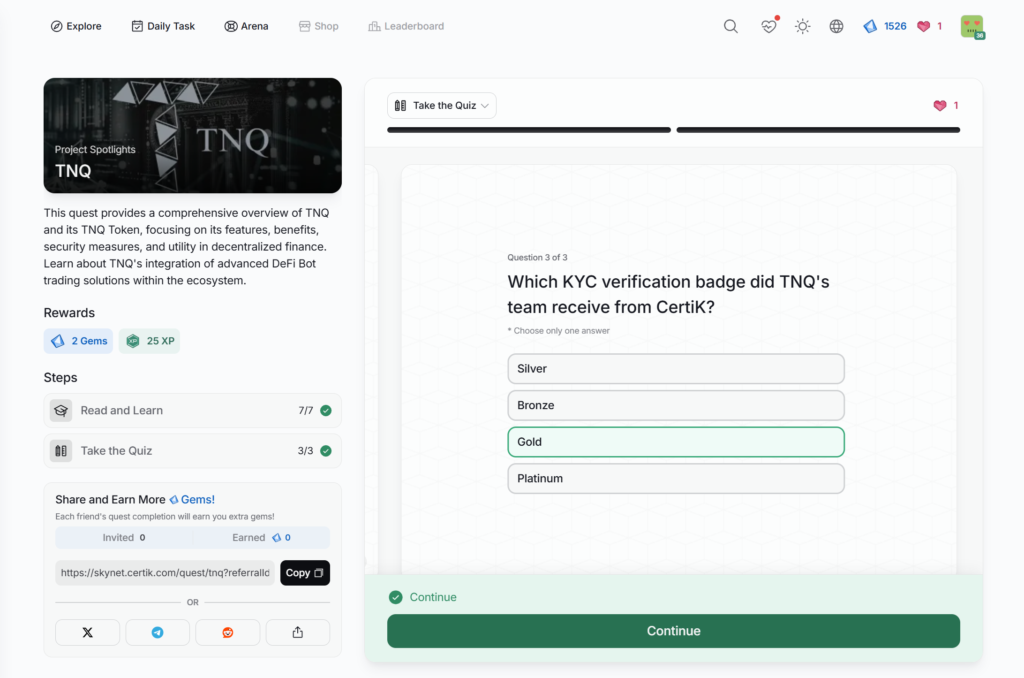
- TNQ
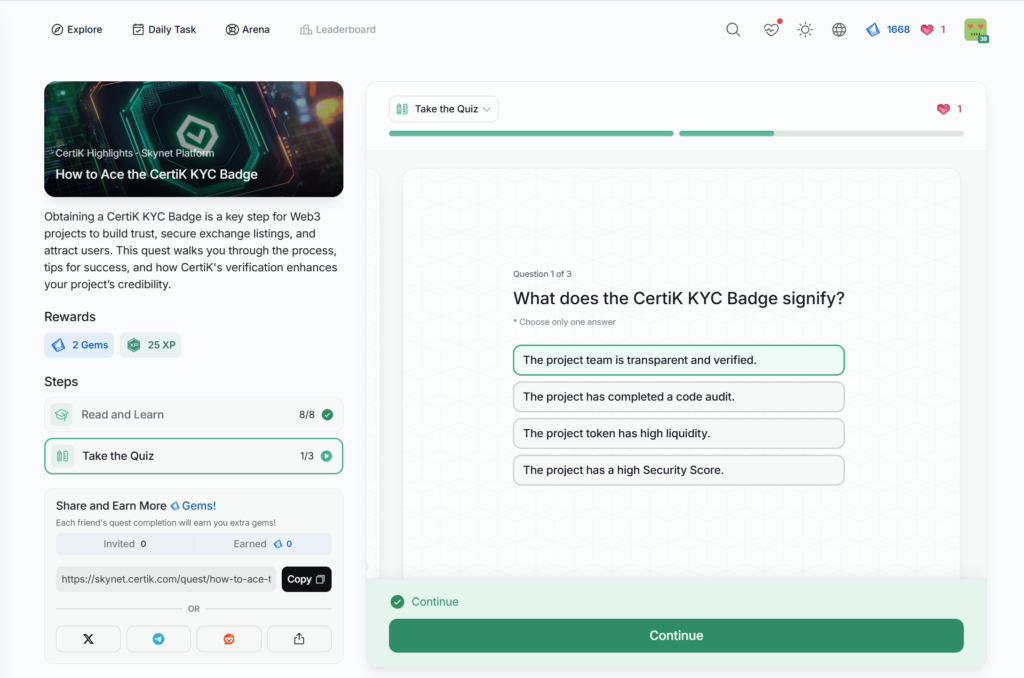
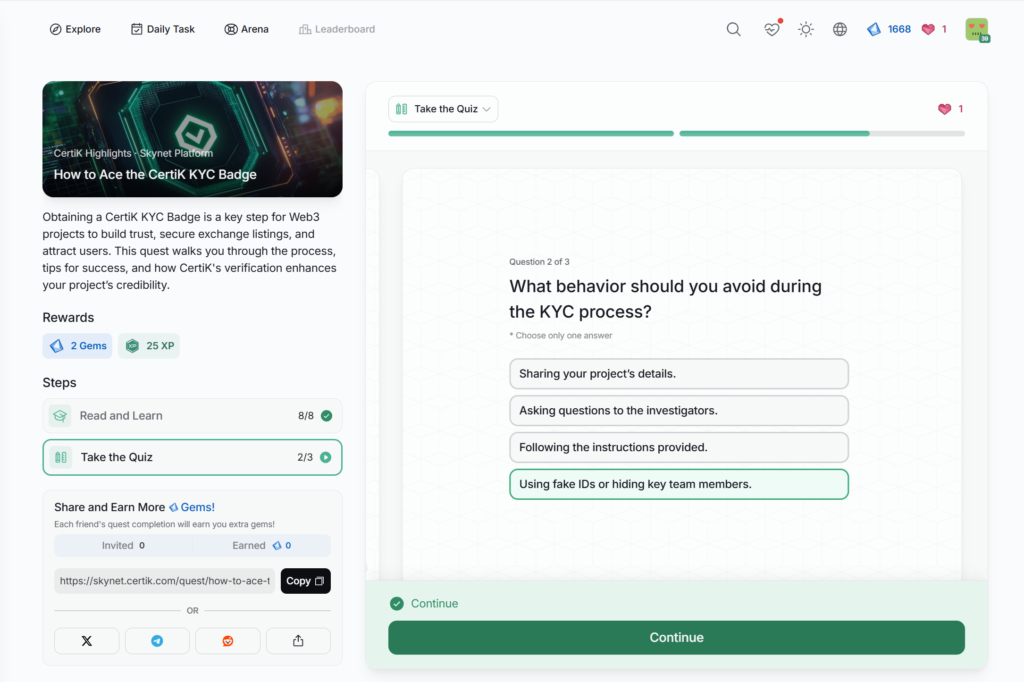
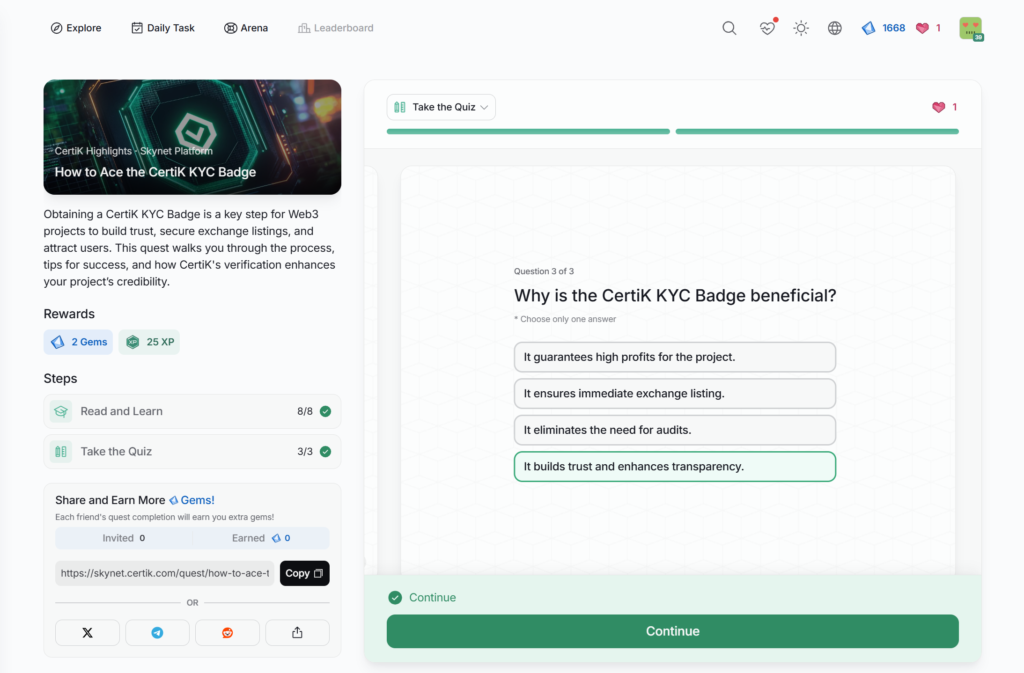
- How to Ace the CertiK KYC Badge
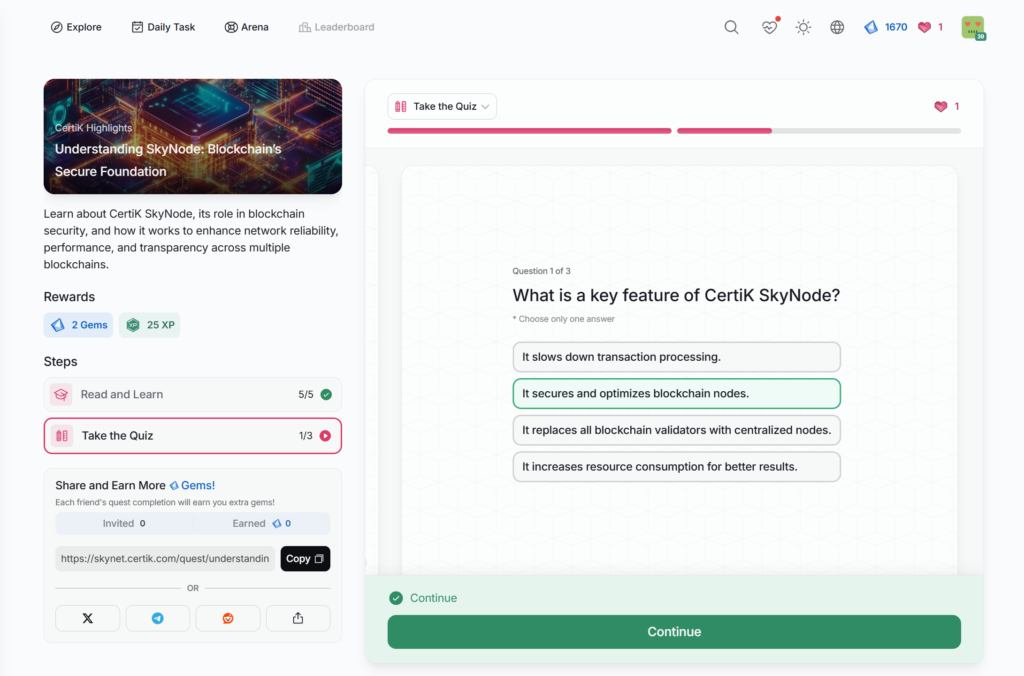
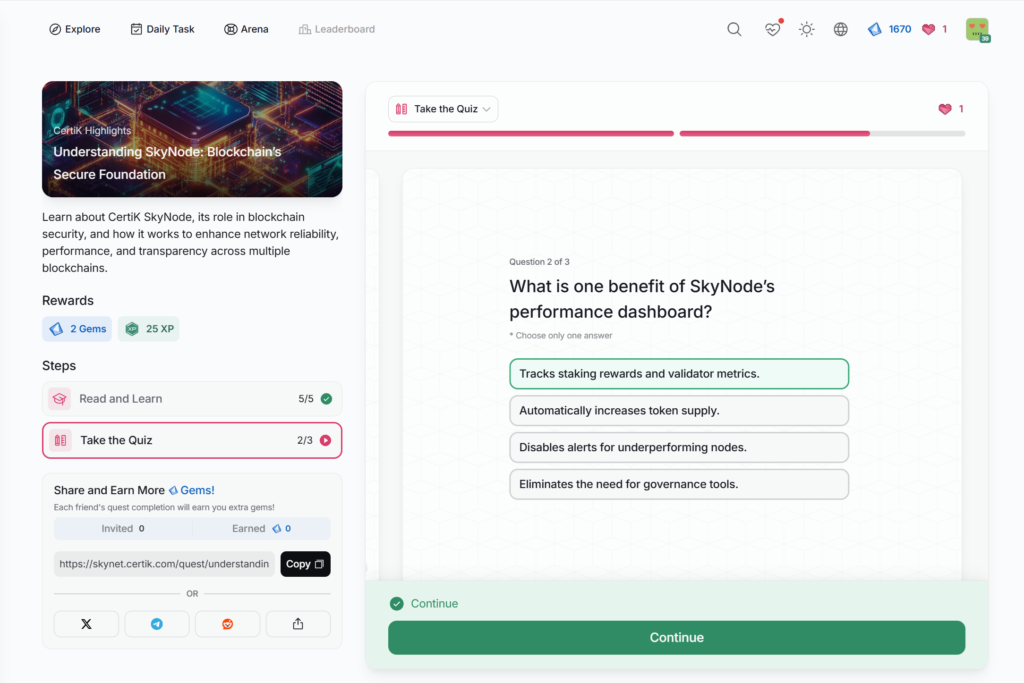
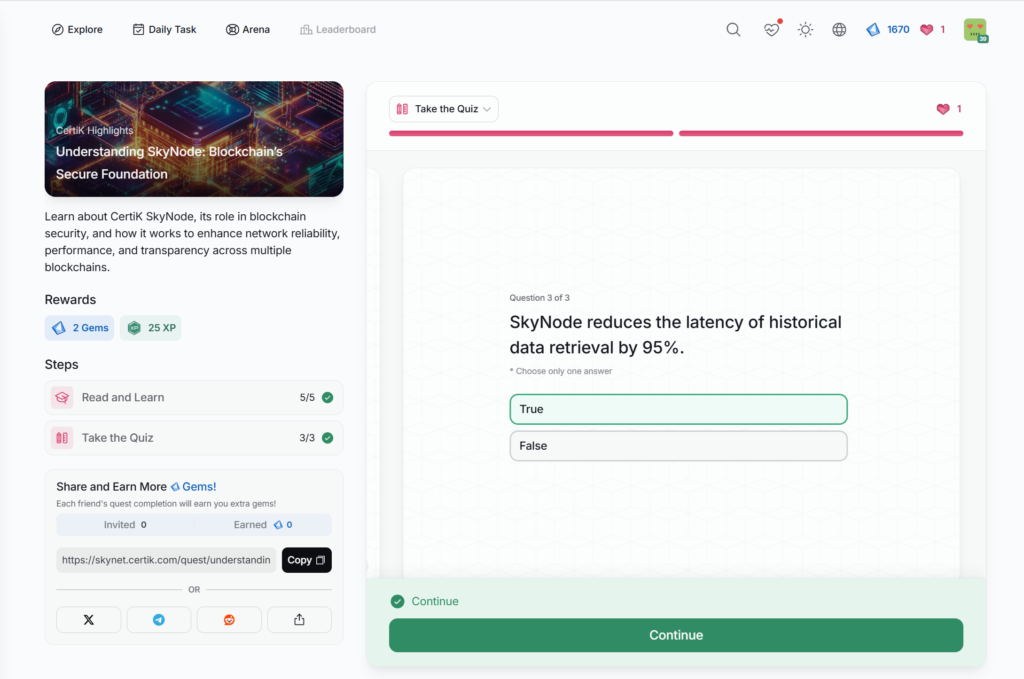
- Understanding SkyNode: Blockchain’s Secure Foundation
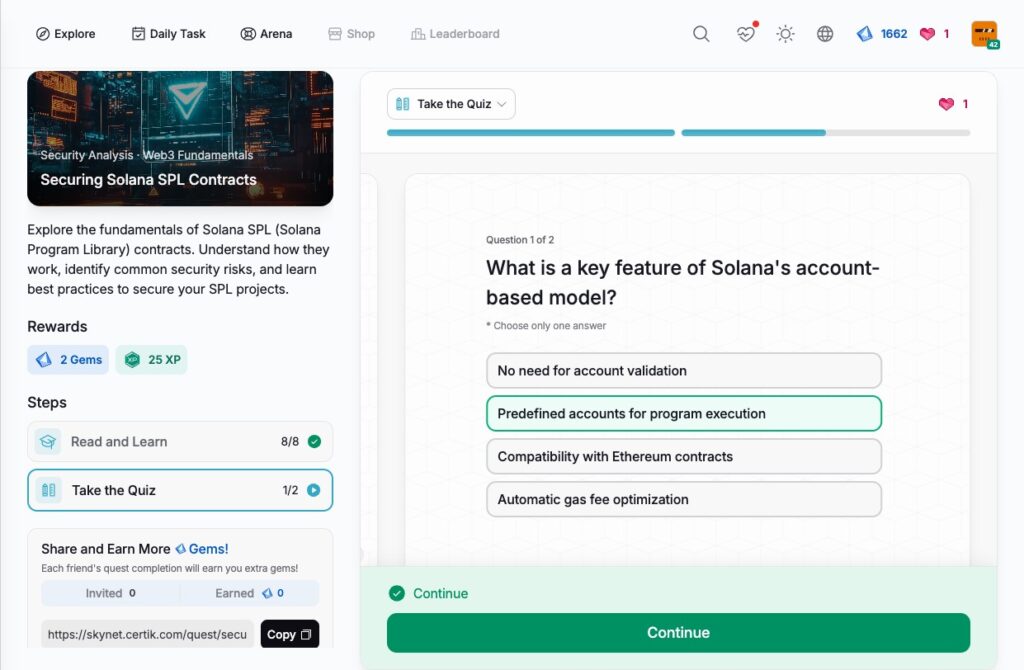
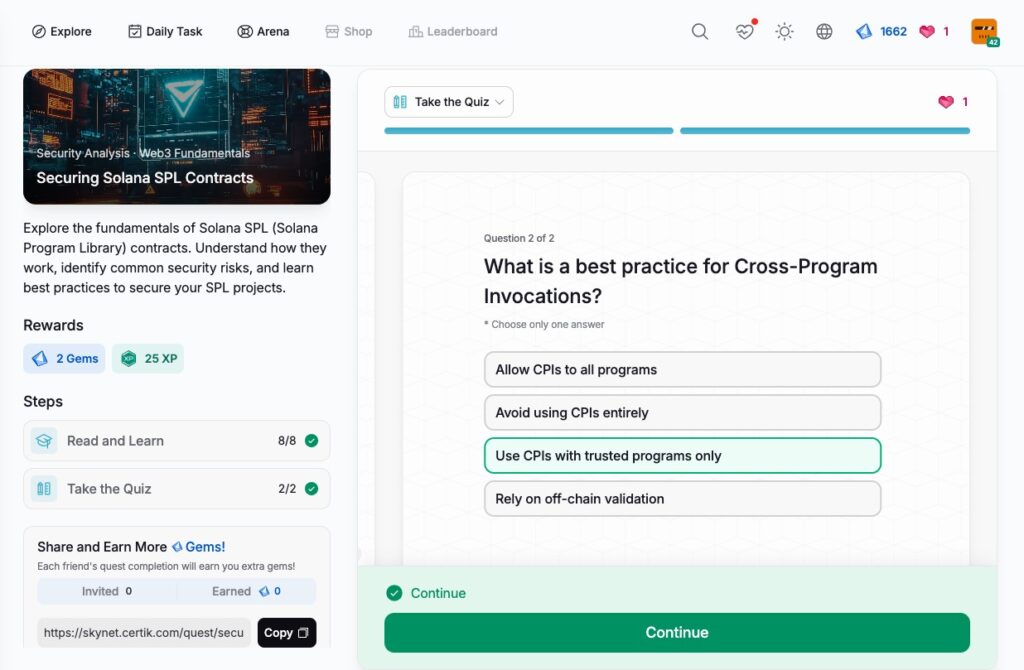
- Securing Solana SPL Contracts
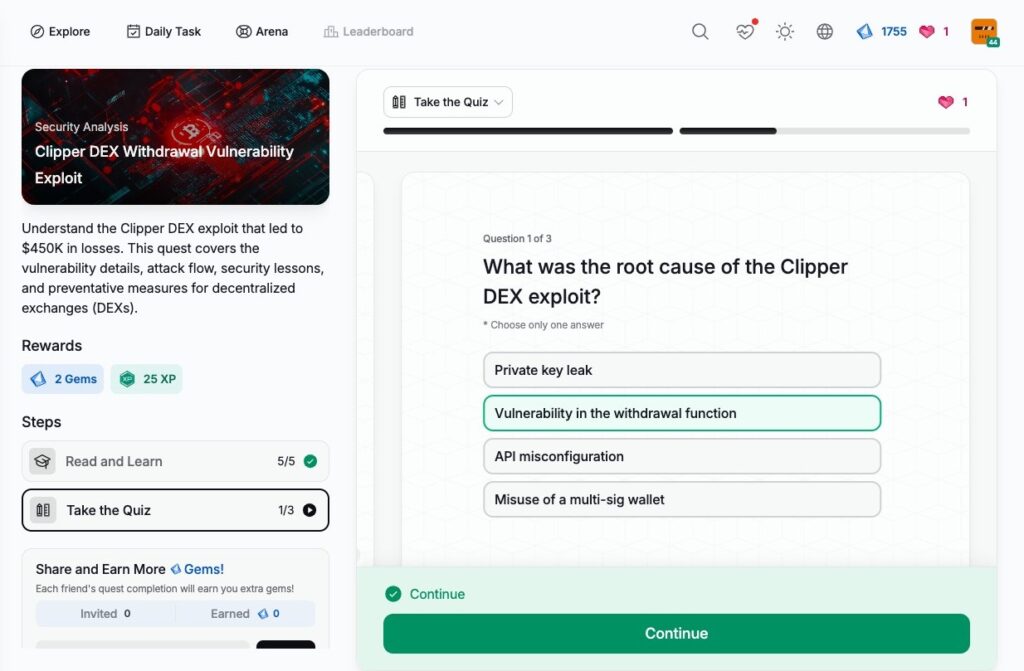
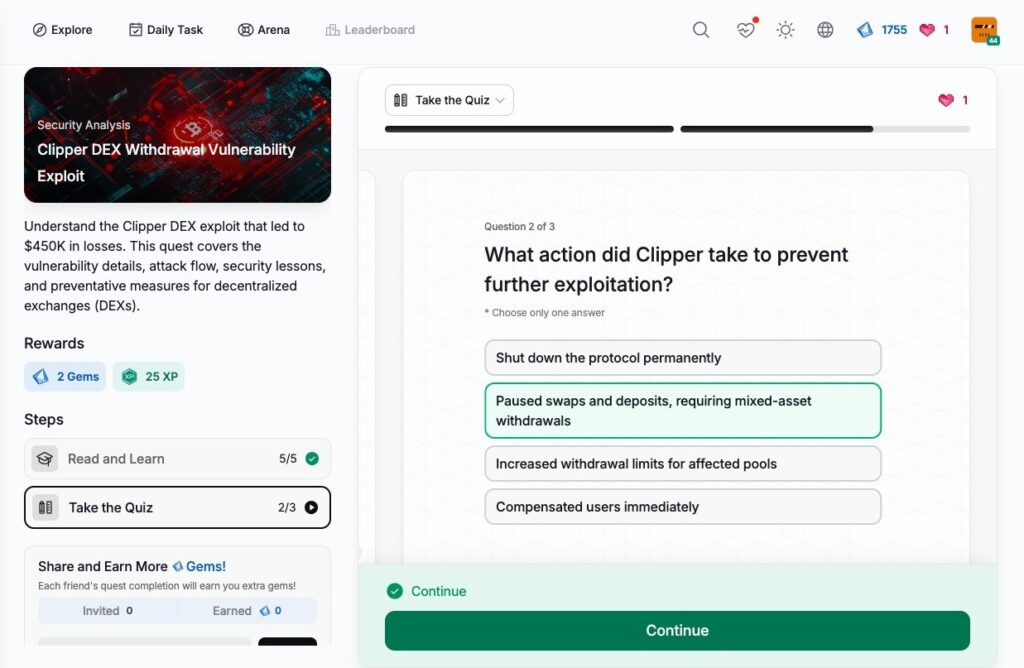
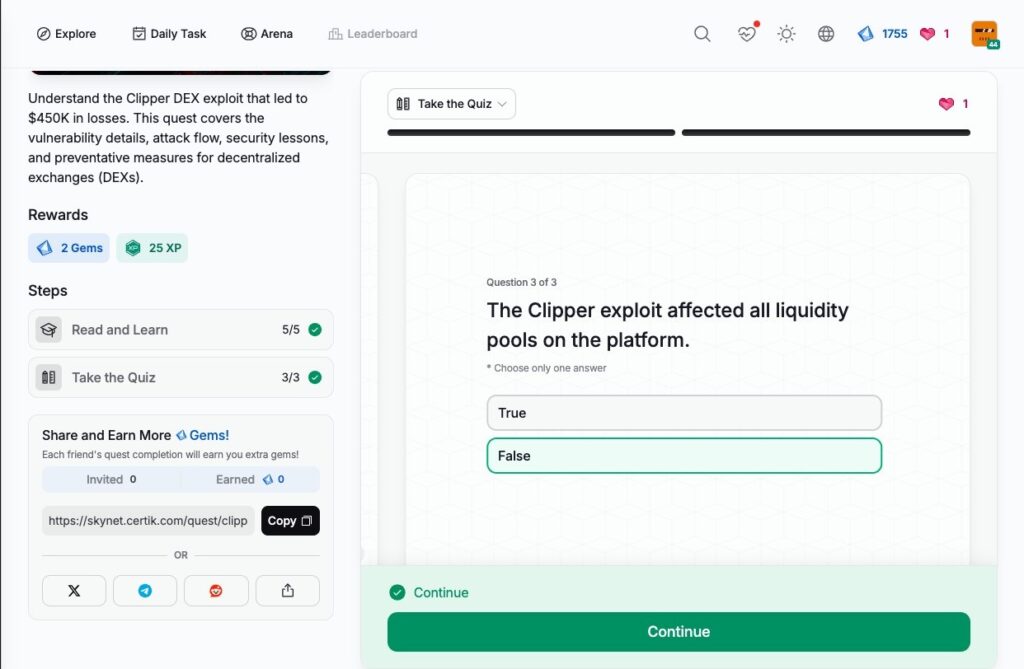
- Clipper DEX Withdrawal Vulnerability Exploit
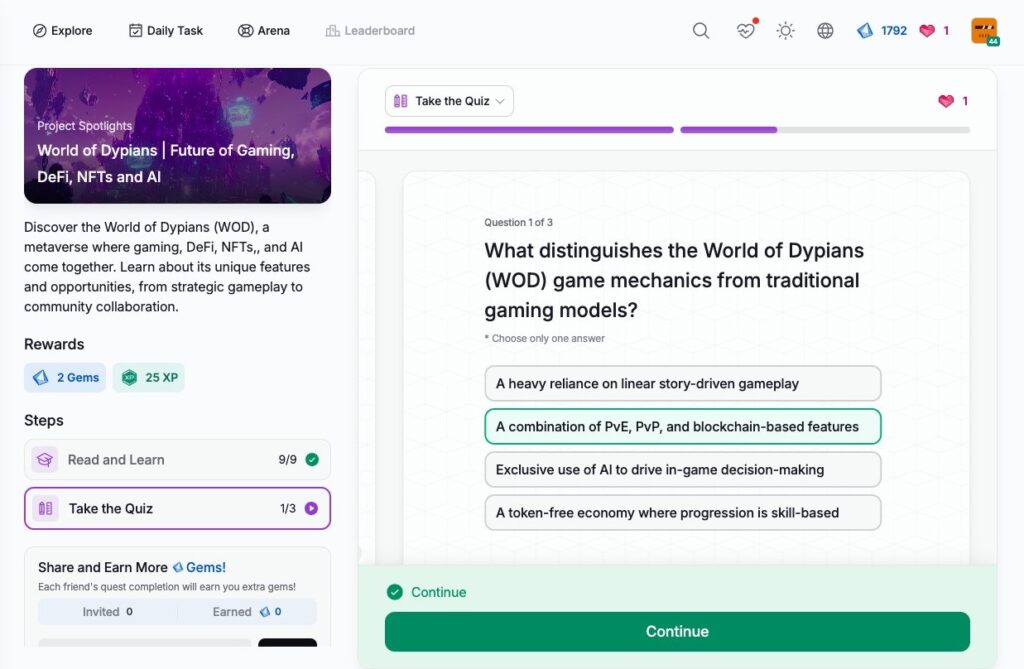
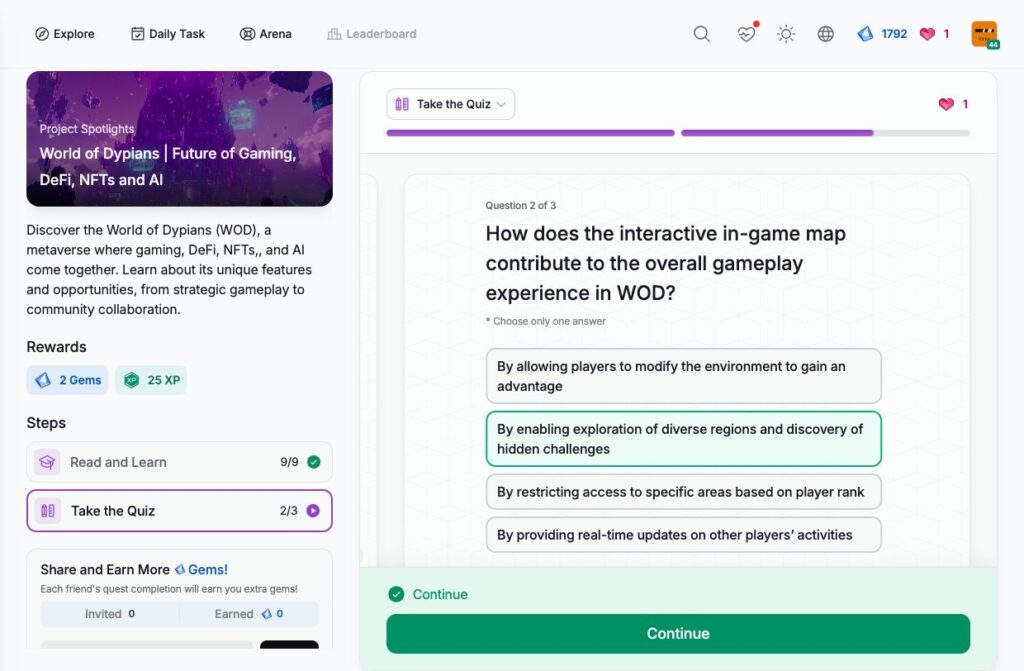
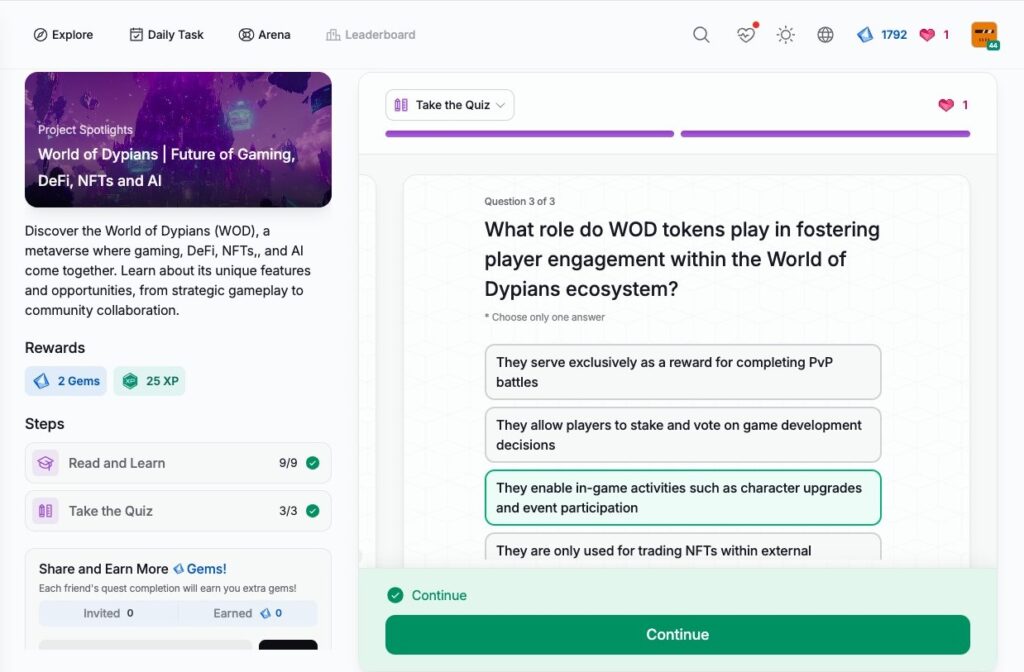
- World of Dypians | Future of Gaming, DeFi, NFTs and AI
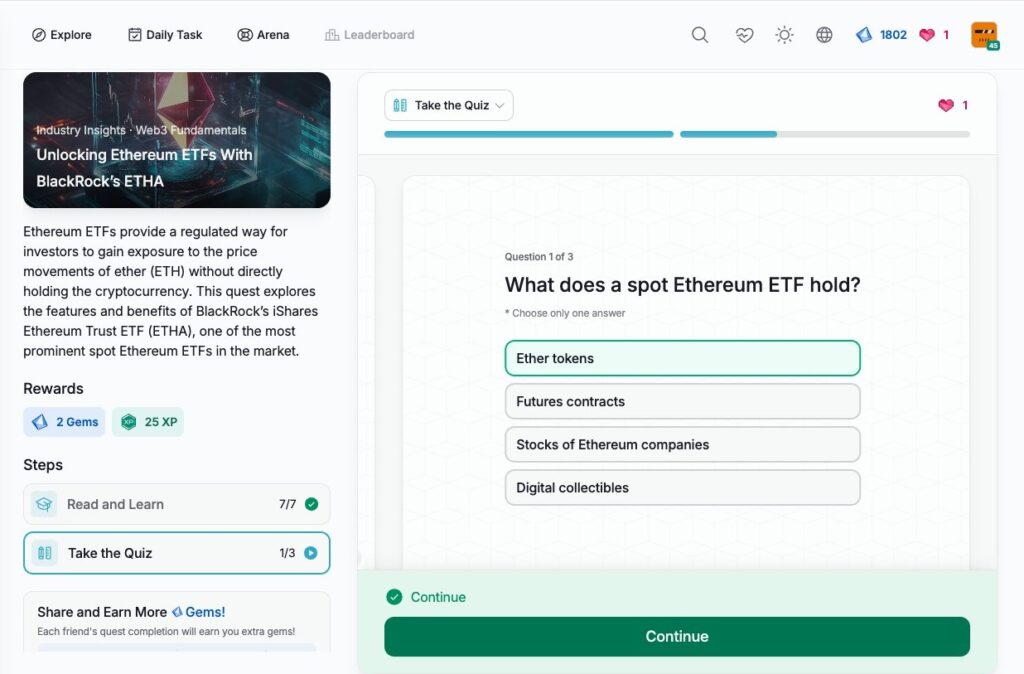
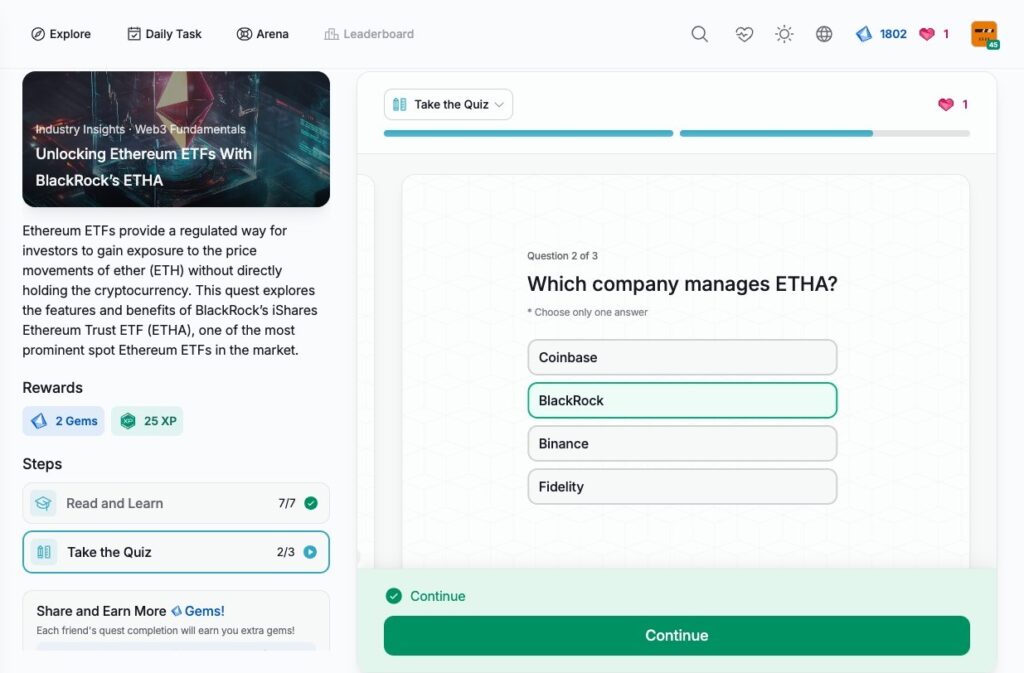
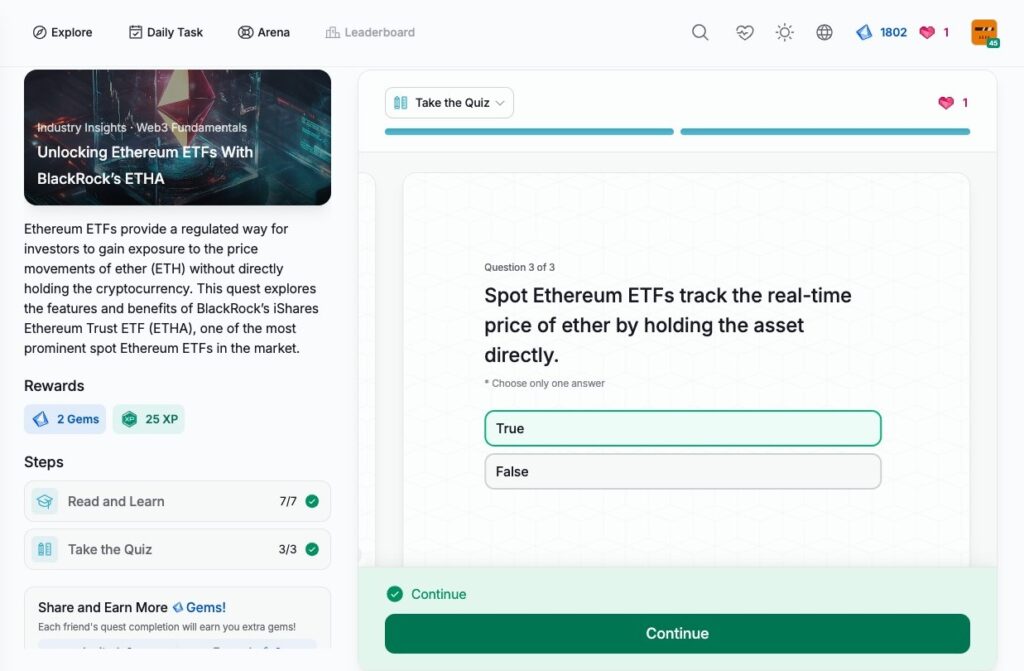
- Unlocking Ethereum ETFs With BlackRock’s ETHA
- Understanding the Polter Finance Exploit
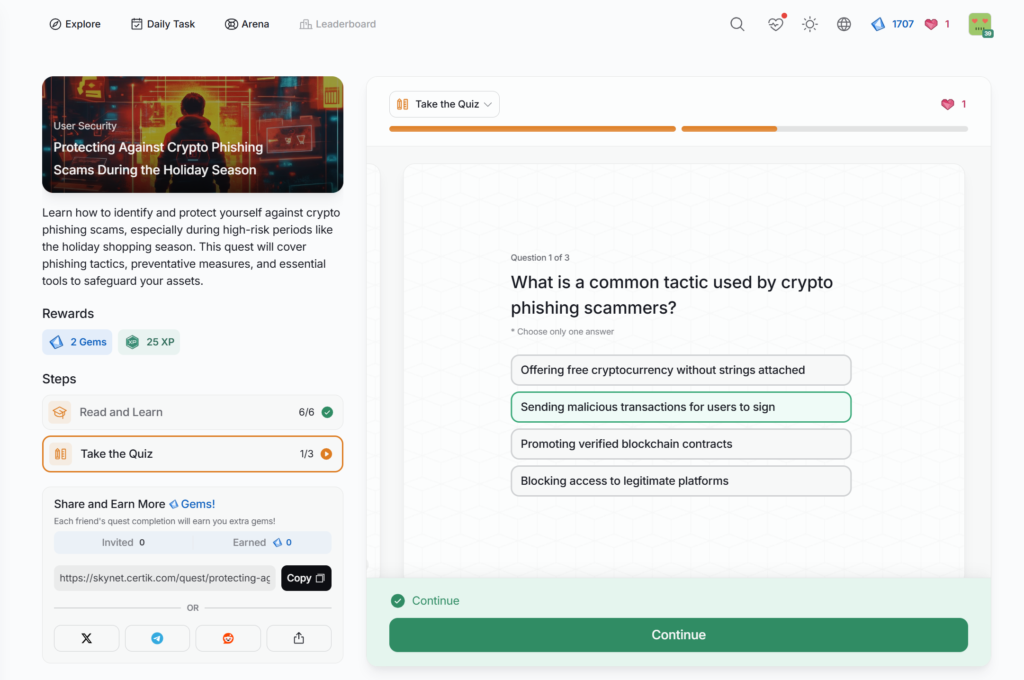
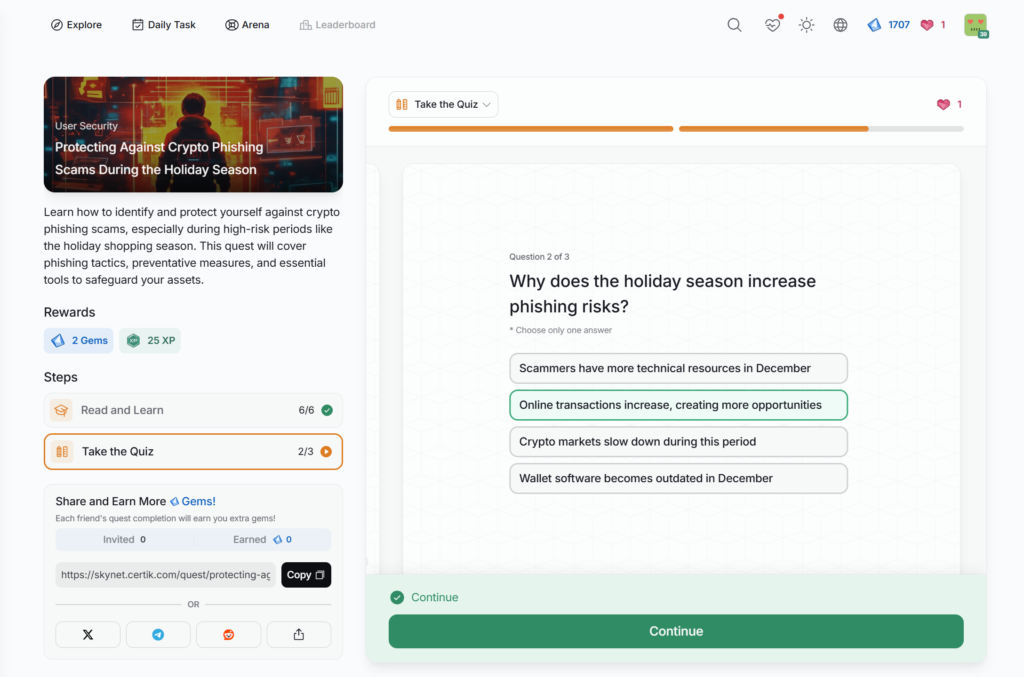
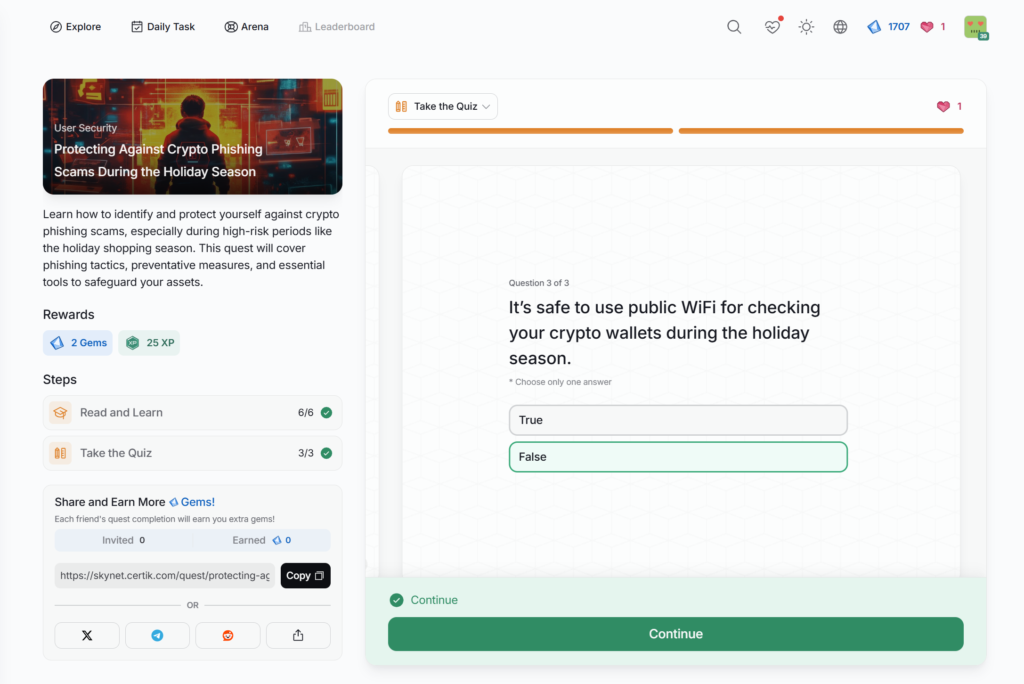
- Protecting Against Crypto Phishing Scams During the Holiday Season
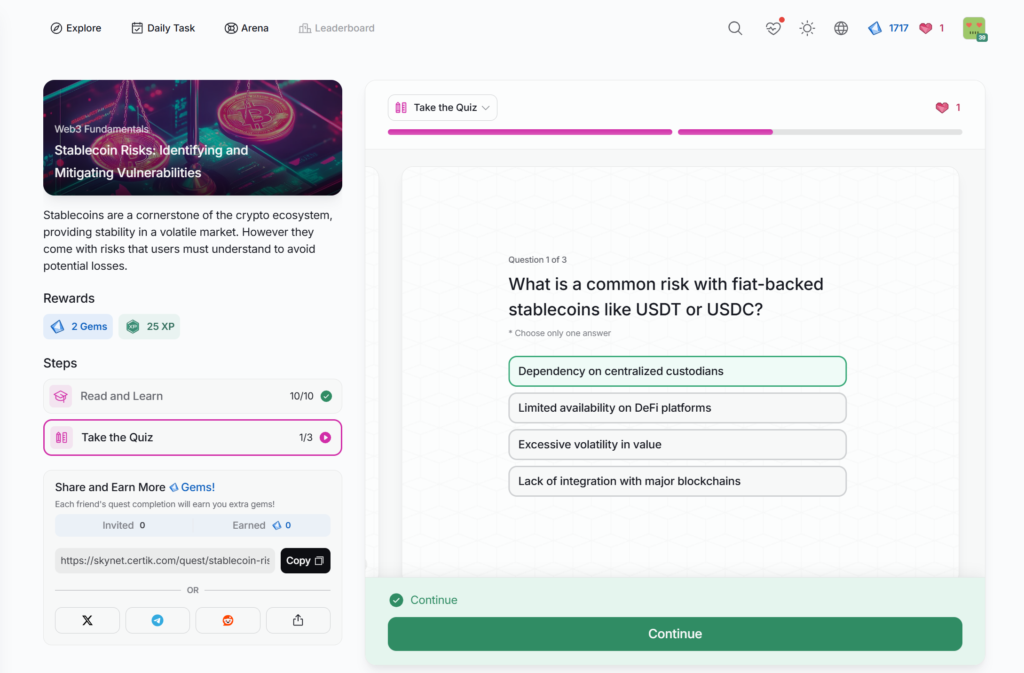
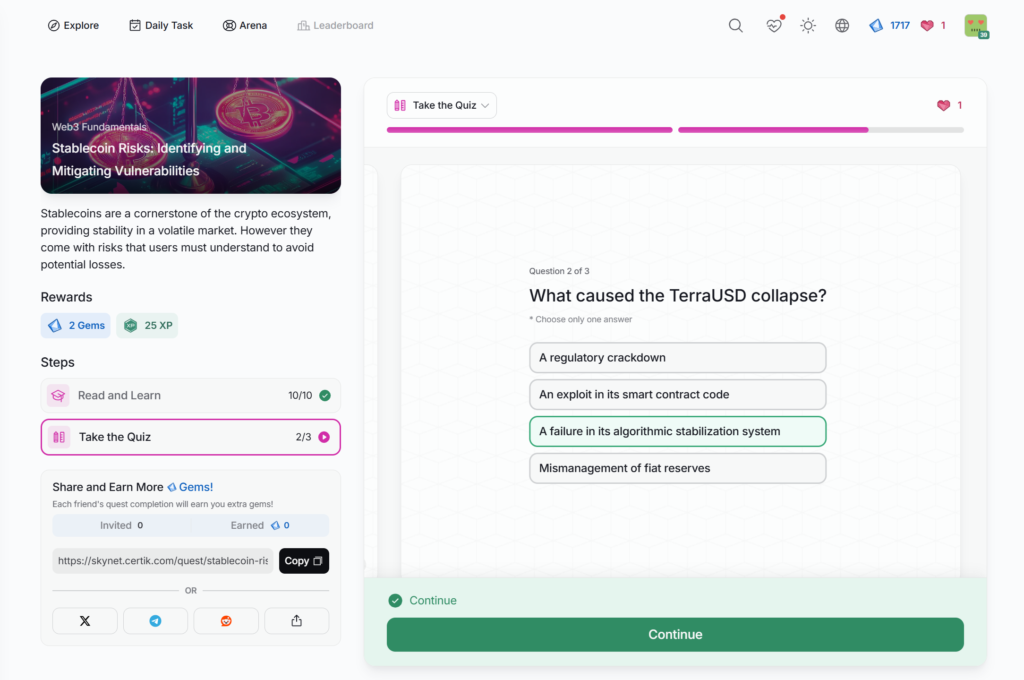
- Stablecoin Risks: Identifying and Mitigating Vulnerabilities
- Blockchain Data Protection and Privacy Compliance
- Quantum Computing and the Future of Cryptocurrency Security
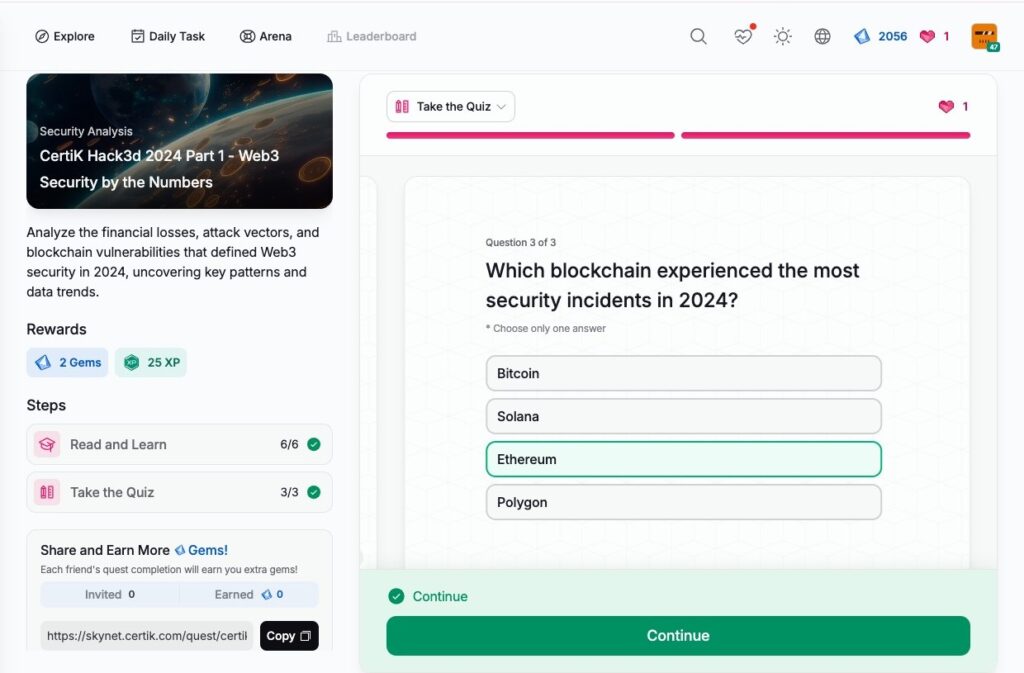
- CertiK Hack3d 2024 Part 1 – Web3 Security by the Numbers
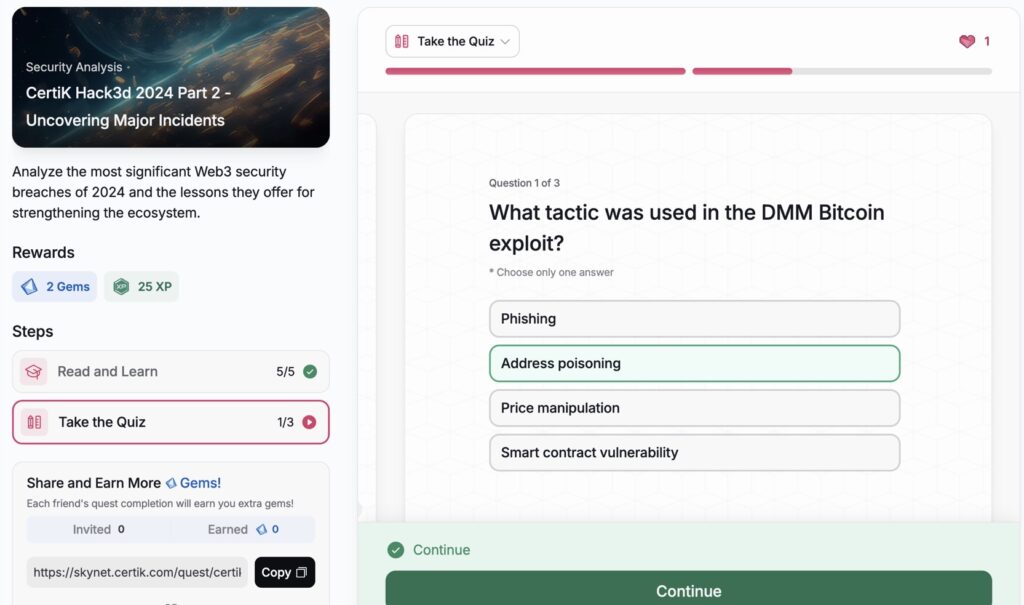
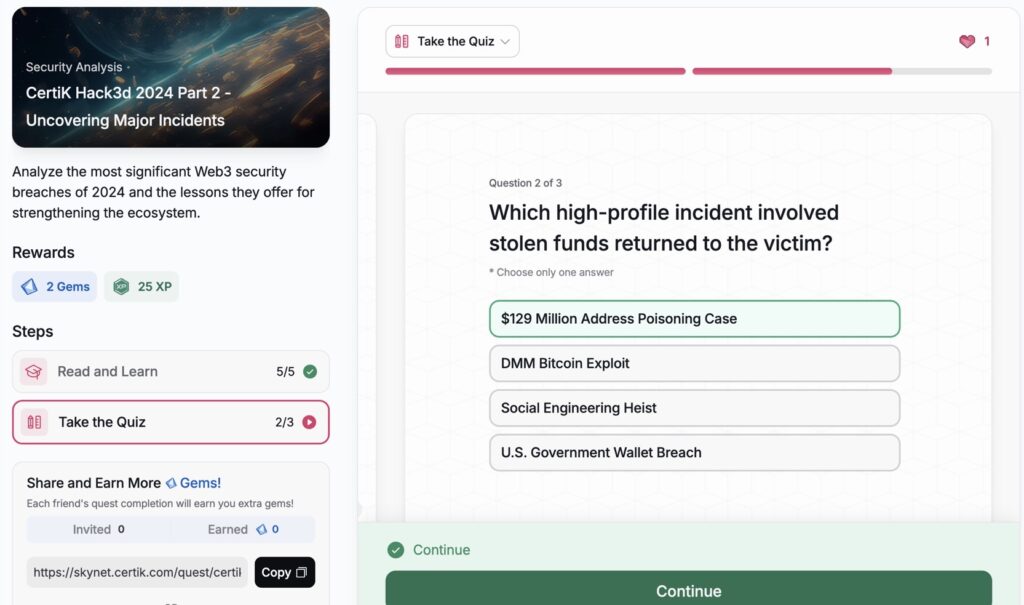
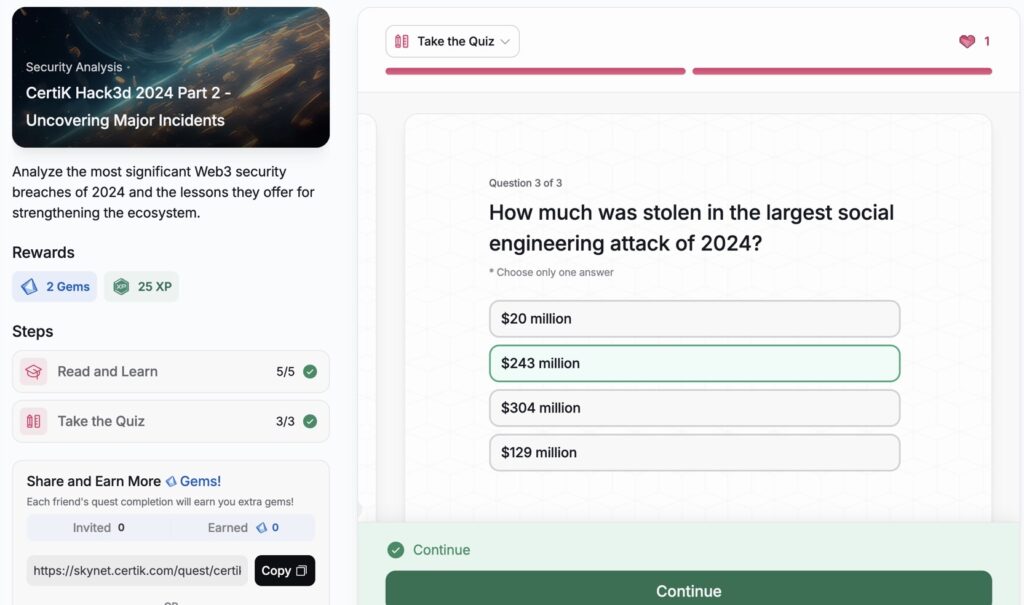
- CertiK Hack3d 2024 Part 2 – Uncovering Major Incidents
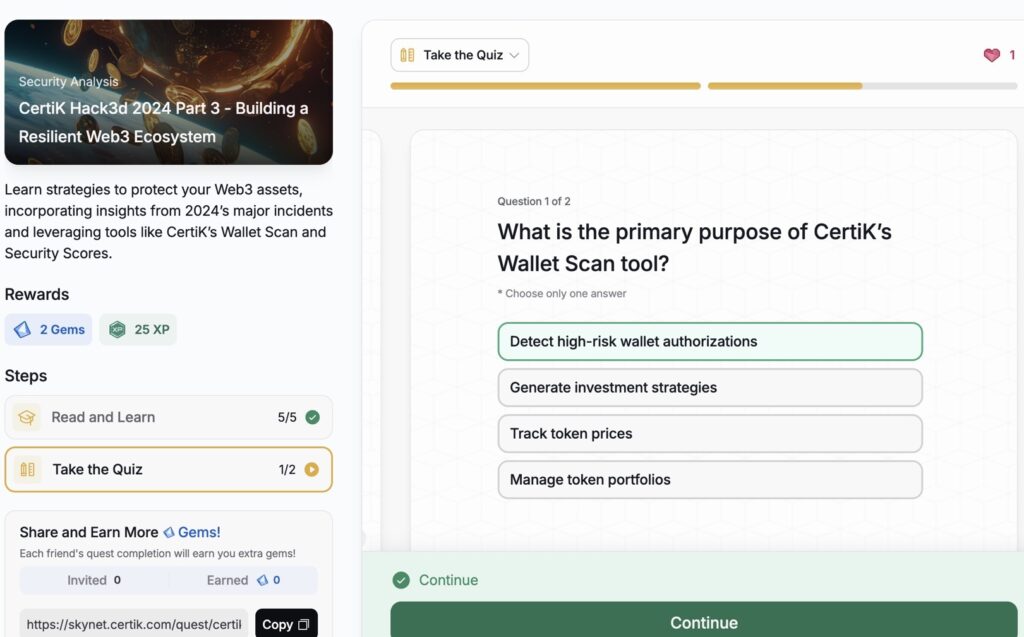
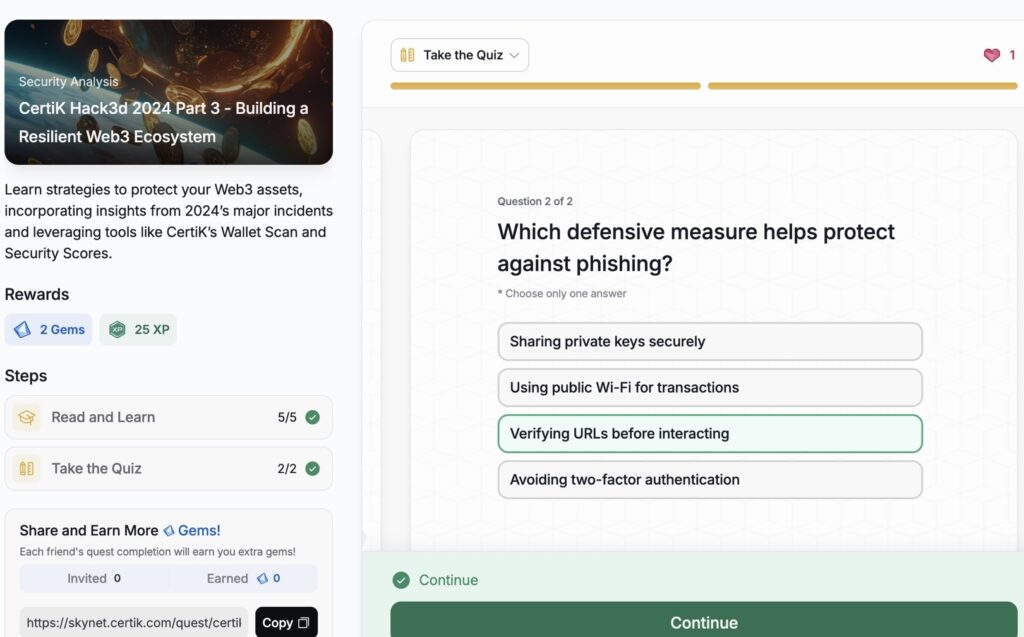
- CertiK Hack3d 2024 Part 3 – Building a Resilient Web3 Ecosystem
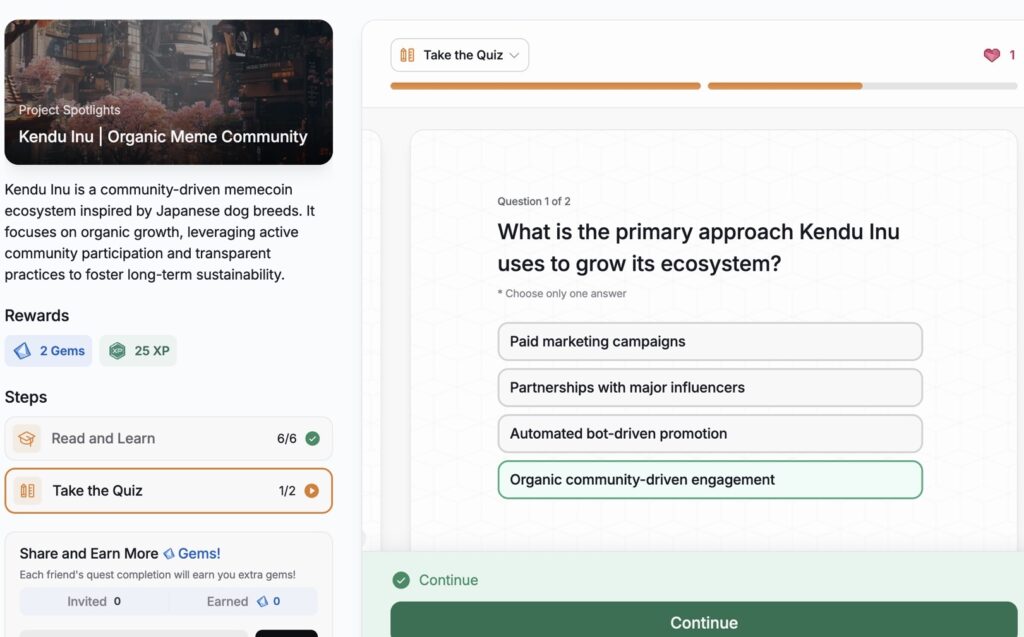
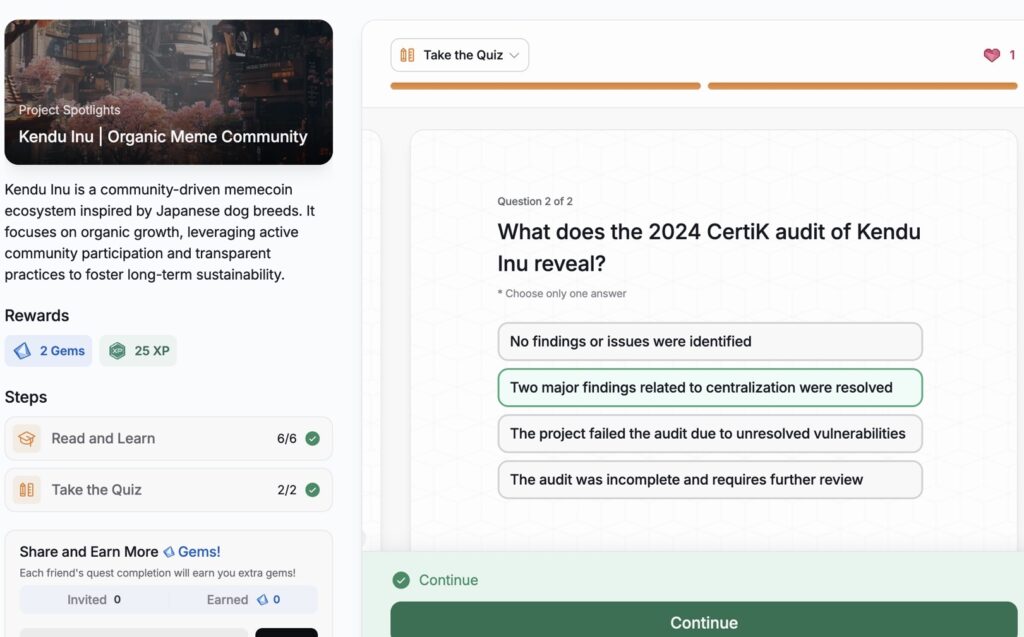
- Kendu Inu | Organic Meme Community
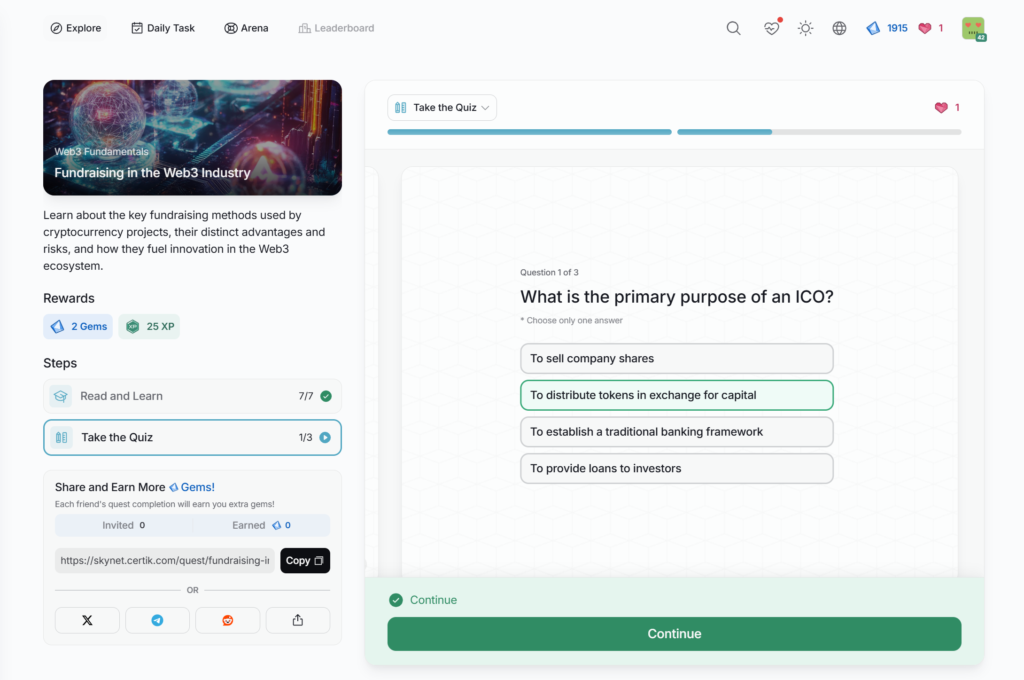
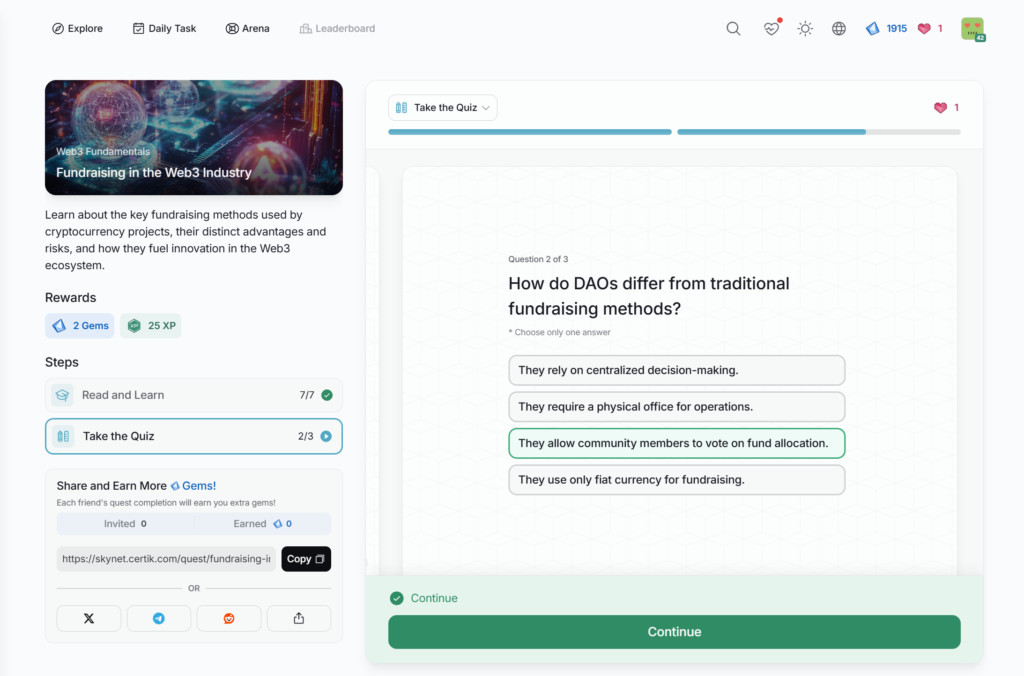
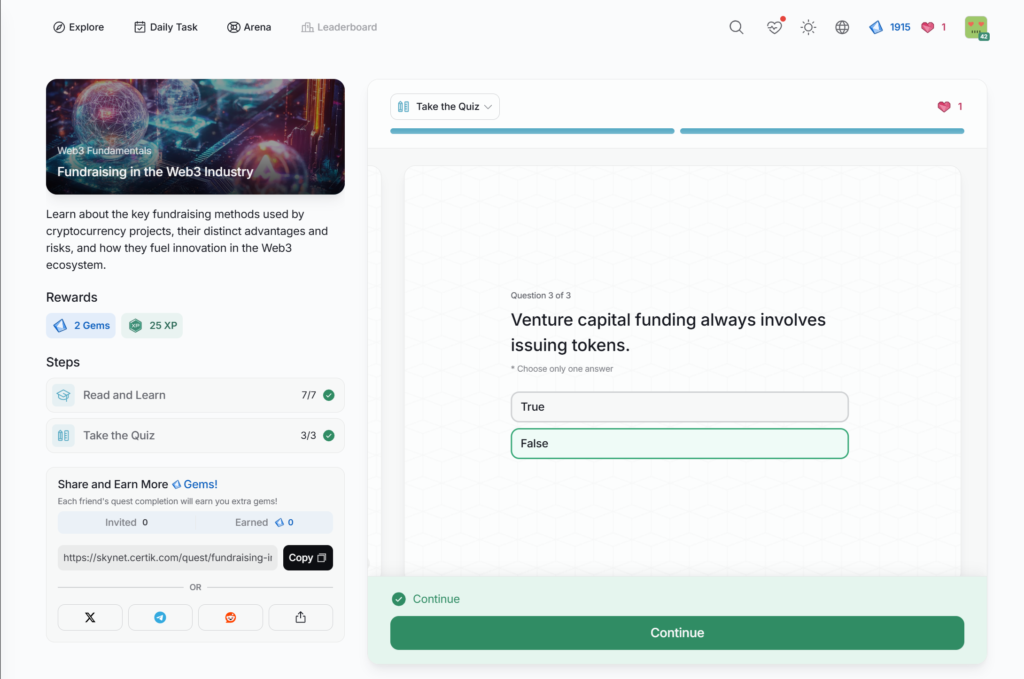
- Fundraising in the Web3 Industry
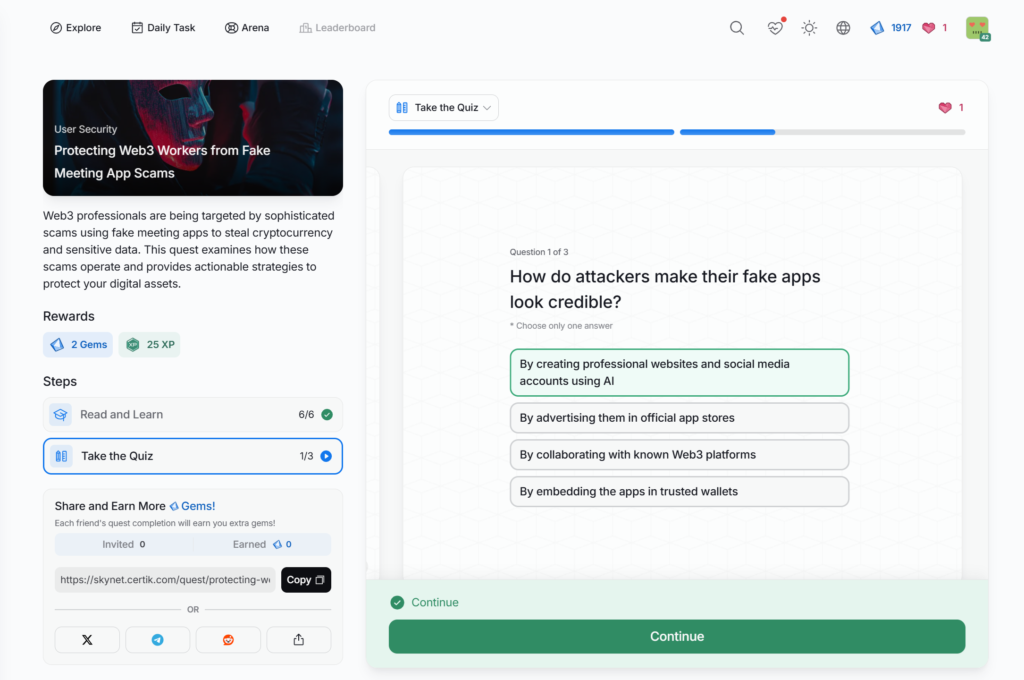
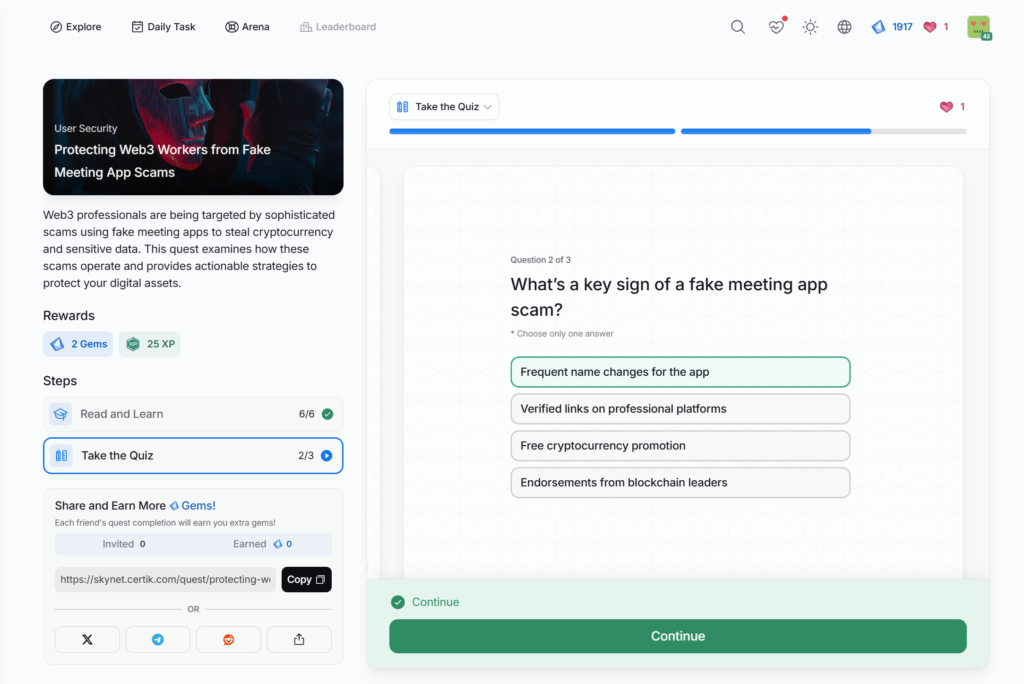
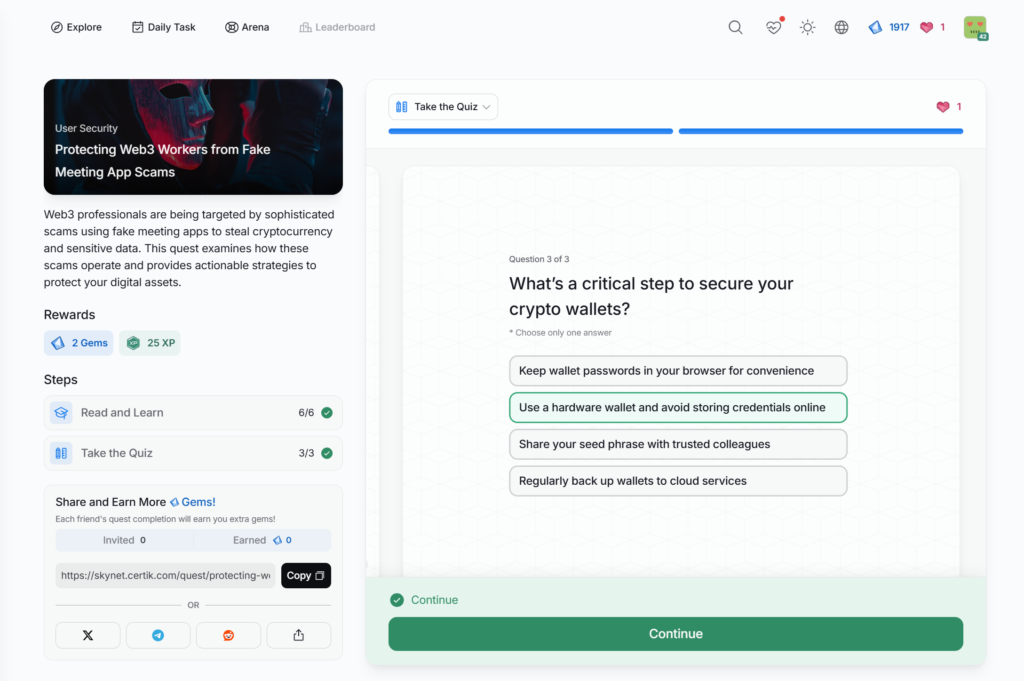
- Protecting Web3 Workers from Fake Meeting App Scams
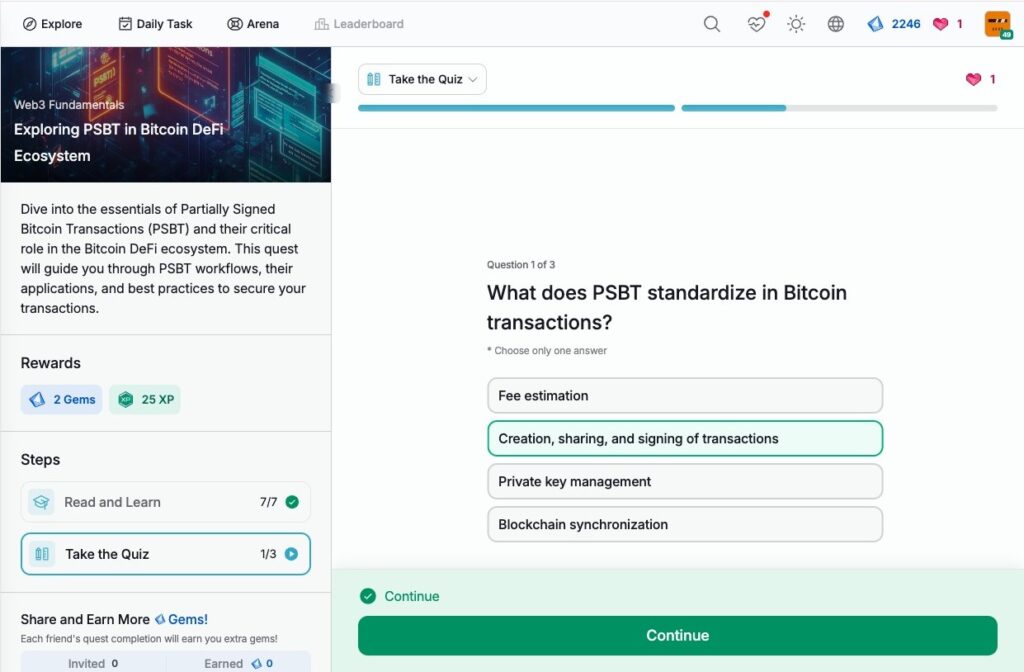
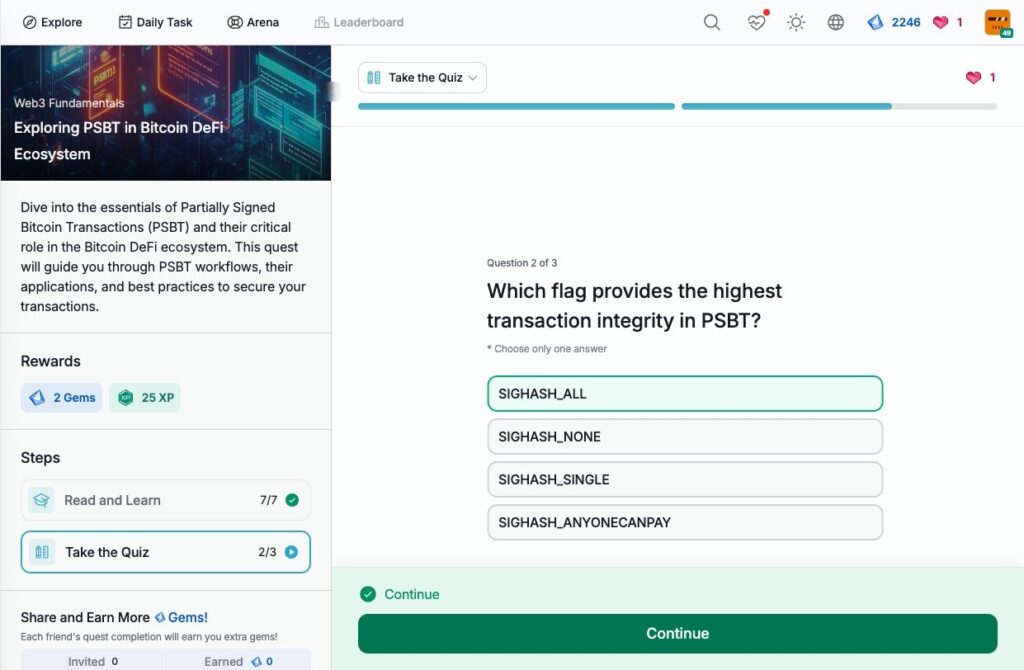
- Exploring PSBT in Bitcoin DeFi Ecosystem
- SpunkySDX | Revolutionizing Commerce with Blockchain and AI
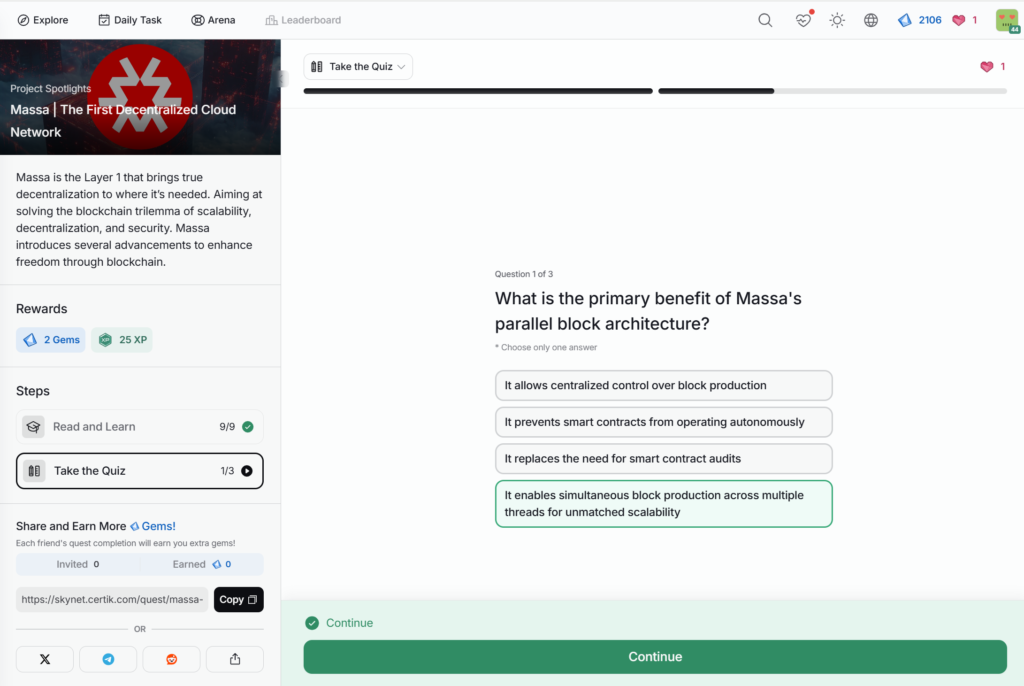
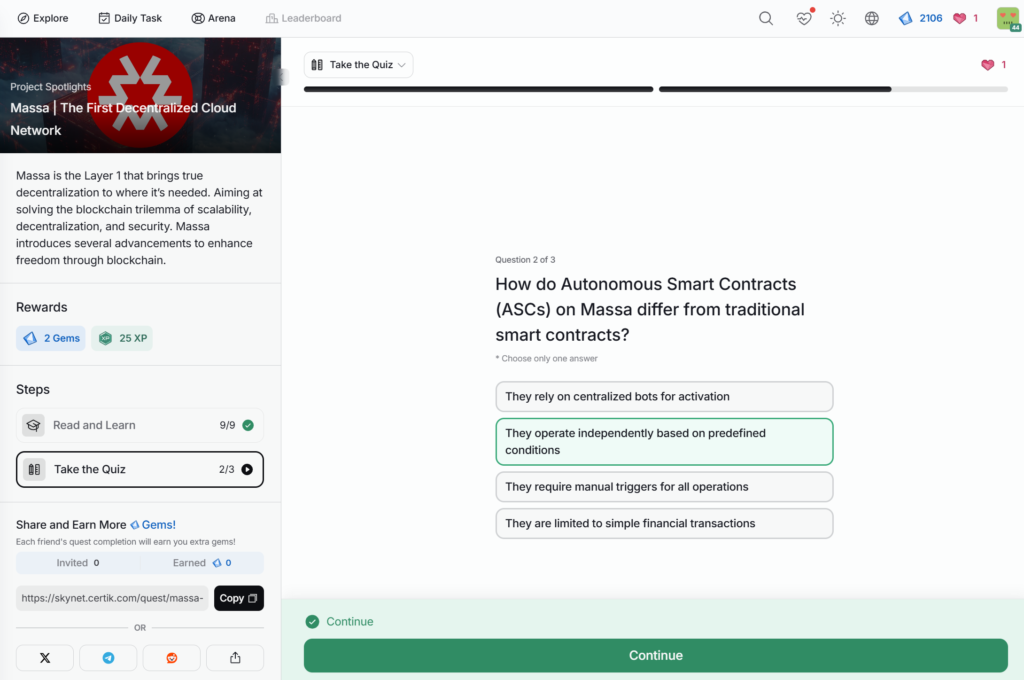
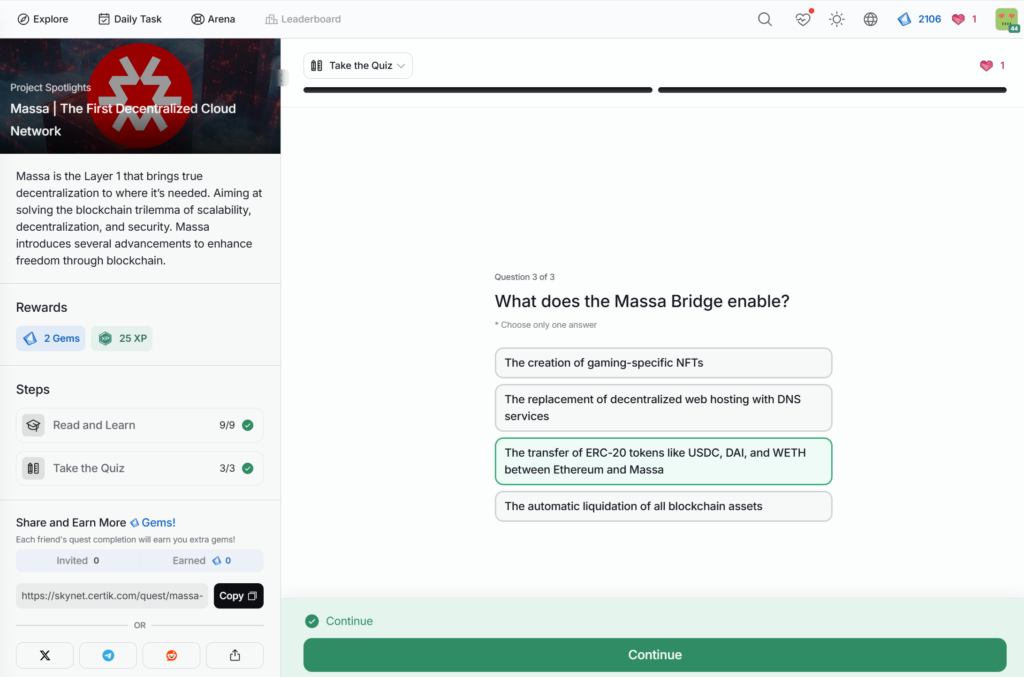
- Massa | The First Decentralized Cloud Network
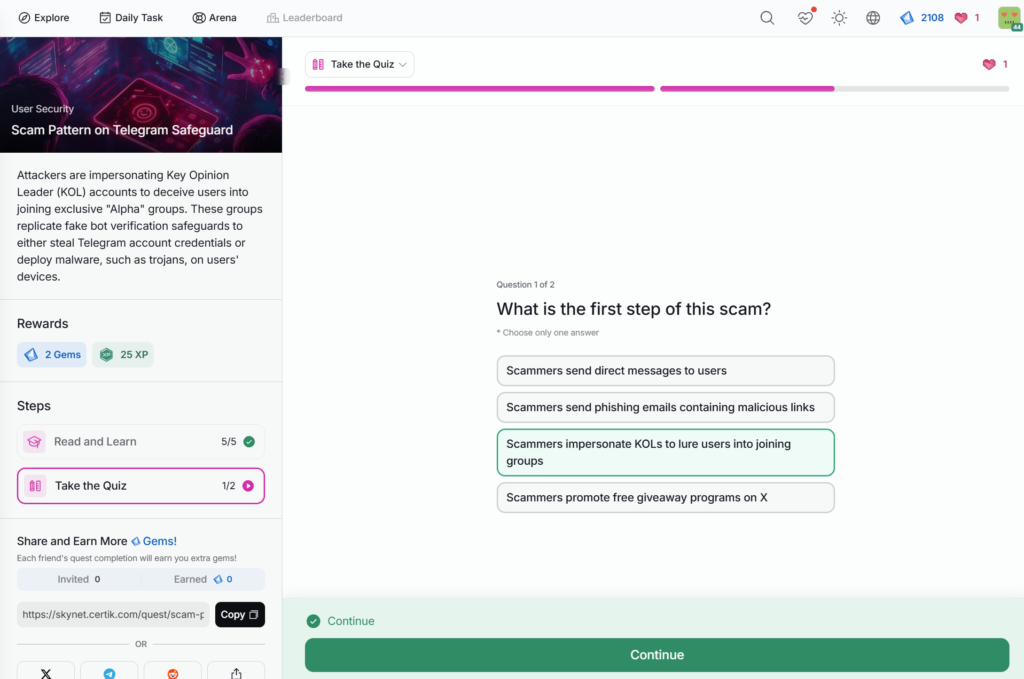
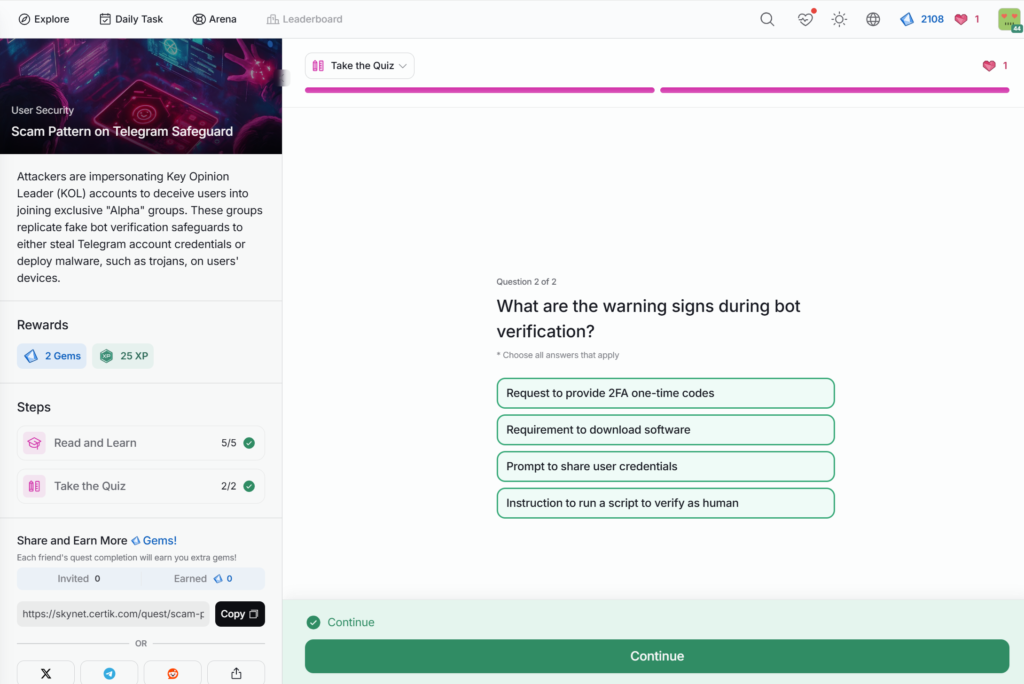
- Scam Pattern on Telegram Safeguard
Industry Insights
A $230M Bitcoin Scam Uncovered
About Satoshi Nakamoto
Advanced Formal Verification of ZK Proofs
AI Memecoins Explained: The New Craze in Crypto
Basics of Hackathons
Blockchain Data Protection and Privacy Compliance
Bot-Driven Wash Trading in Exit Scams
Build trust and integrity in project teams with KYC
Enhancing Security Awareness for Web3 Desktop Wallets
Evaluating Popular Web3 Messaging Apps
FBI warns of Crypto Social Engineering
Hack3d Part 1: Most Common Attack Vectors in Q3 2024
HACK3D Part 1: Top Incident Analyses
Hack3d Part 2: Major Hacks of Q3 2024
HACK3D Part 2: Private Key Compromise
HACK3D Part 3: Rounding Issue Exploits
Hack3d Report Q2 H1 2024 – Part 1: Overview and Key Highlights
Hack3d Report Q2 H1 2024 – Part 2: Insights and Future Security Enhancements
How AI is Transforming KYC for Crypto Project Teams
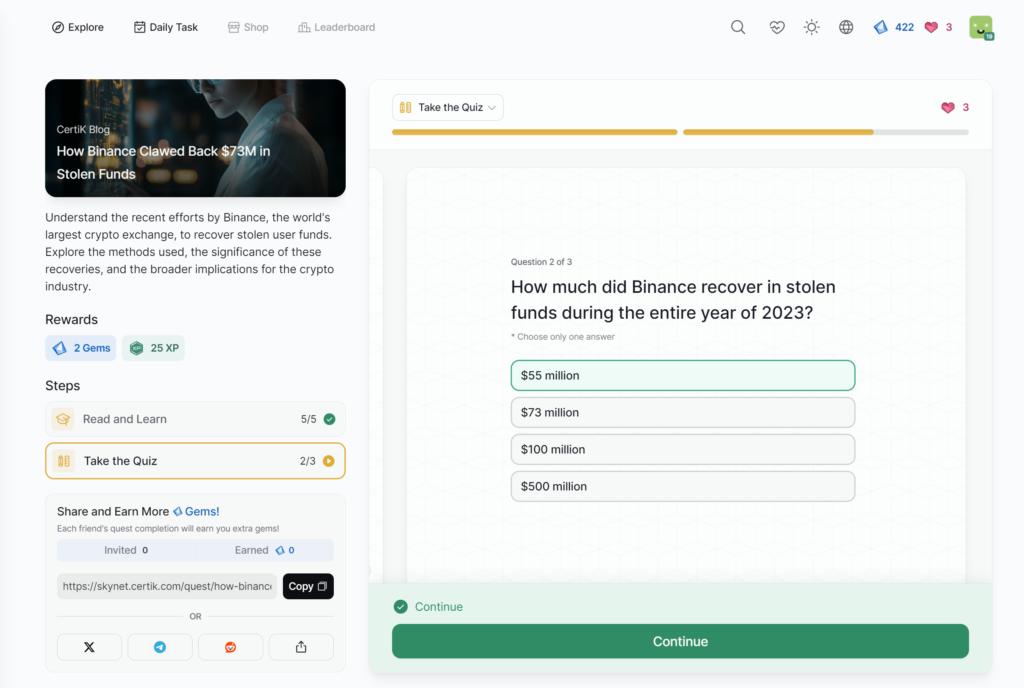
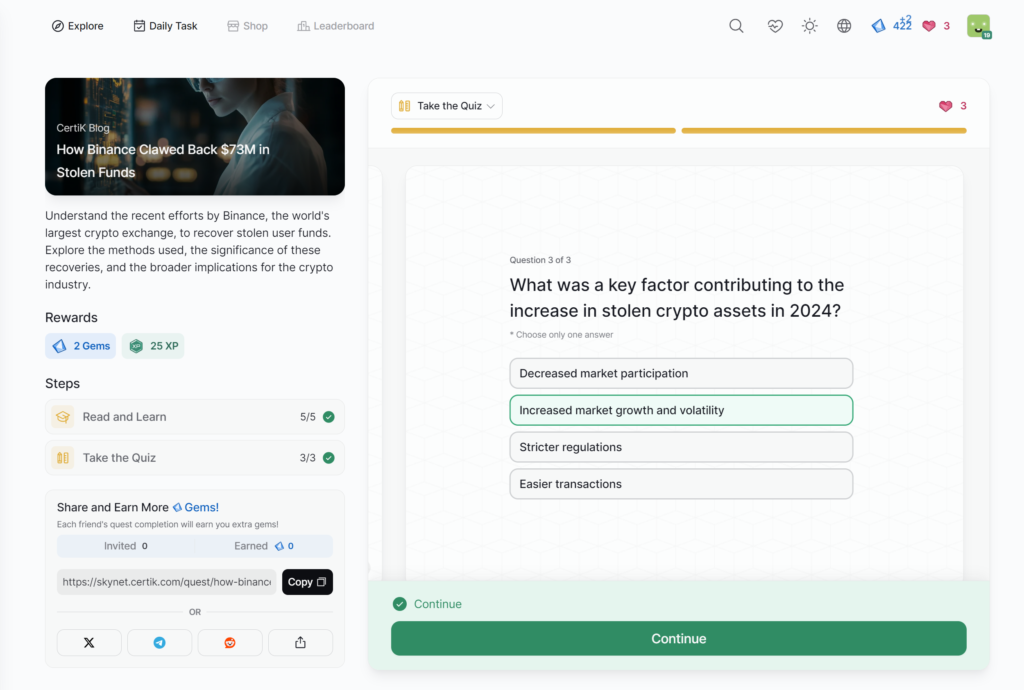
How Binance Clawed Back $73M in Stolen Funds
How Exit Scammers Mint Tokens Undetected
KYC Actors are Ramping Up Their Game
Mastering Bridge Tracing
Navigating DAO Governance and the Compound DAO Incident
OKX and CertiK Fast Pass Program
Ordinals and the BRC-20 Standard
Pump.Fun
Quantum Computing and the Future of Cryptocurrency Security
Radiant Capital’s $50M DeFi Hack Response
SkyInsights: Crypto Compliance
The Memecoin Markets of Springfield
Top Performing Cryptocurrencies of H1 2024
Trap Phishing on Trusted Platforms
Truth Terminal – An AI and a Crypto Millionaire
Understanding AI’s Role in Enhancing Web3 Security
Understanding BGP Hijacking and Internet Routing Security
Understanding the Android SpyAgent Campaign
Understanding the DeRec Alliance
Understanding the Impact of FIT21 on Crypto Compliance
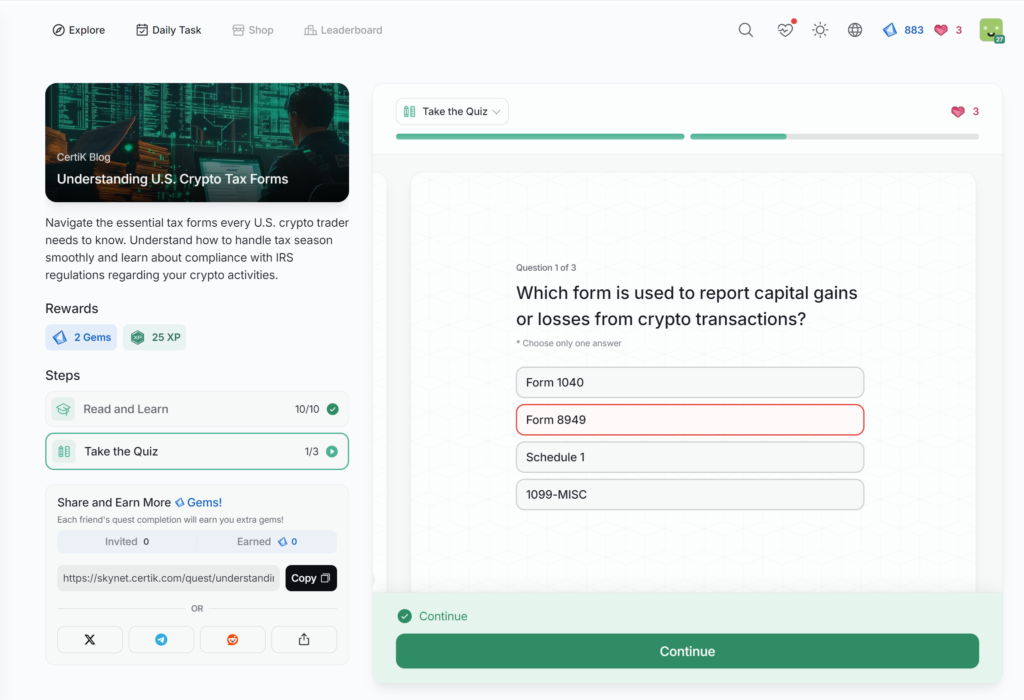
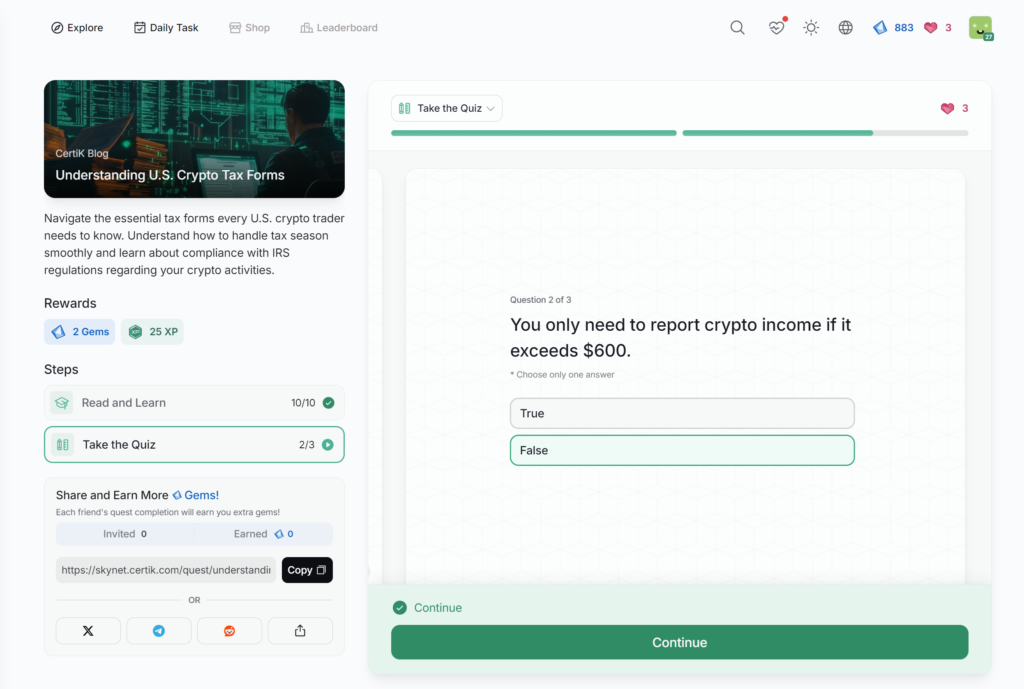
Understanding U.S. Crypto Tax Forms
Unlocking Ethereum ETFs With BlackRock’s ETHA
Unmasking Crypto Market Manipulation
Unveiling the KYC Actor Industry
UtopiaSphere Incident Analysis
Vanity Address and Address Poisoning
WazirX Hack Incident Analysis
Web2 Meets Web3: Hacking Decentralized Applications
User Security
Best Practices for Wallet Security
Best Tools for Tracking Top Crypto Wallets
Case Study on Enhancing Security for App Chains
Case Study on the Risks of Phishing Attacks in DeFi
Choosing a Secure Exchange
Code Security
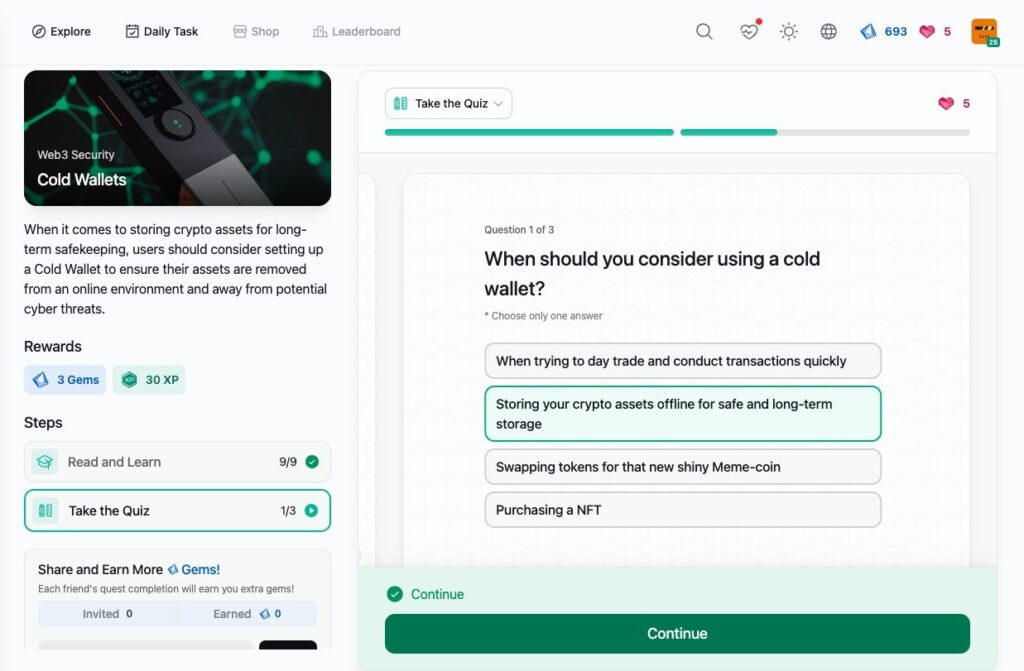
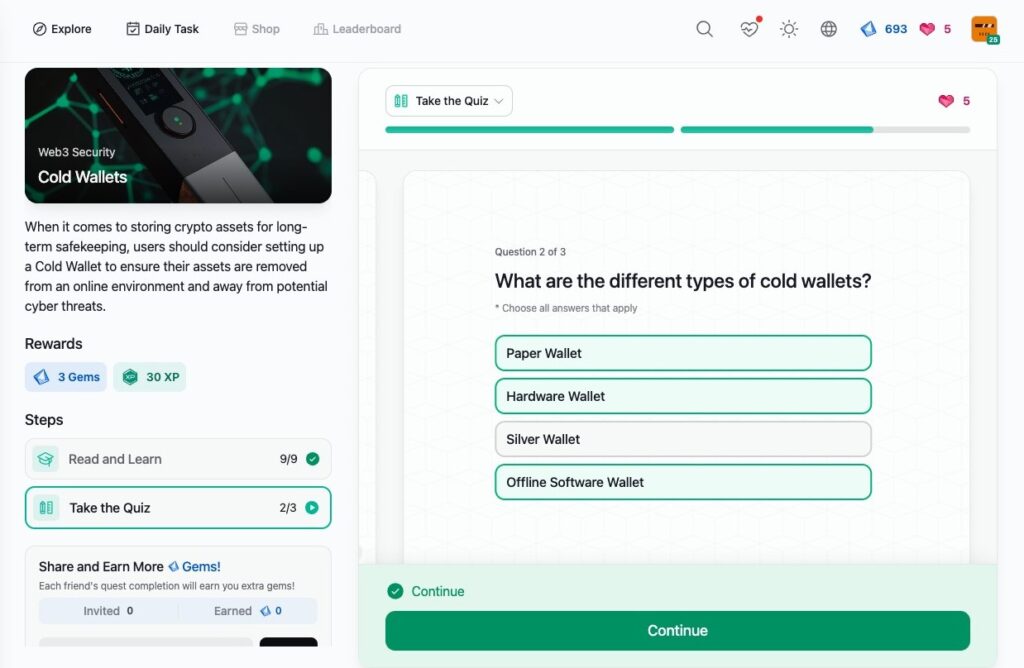
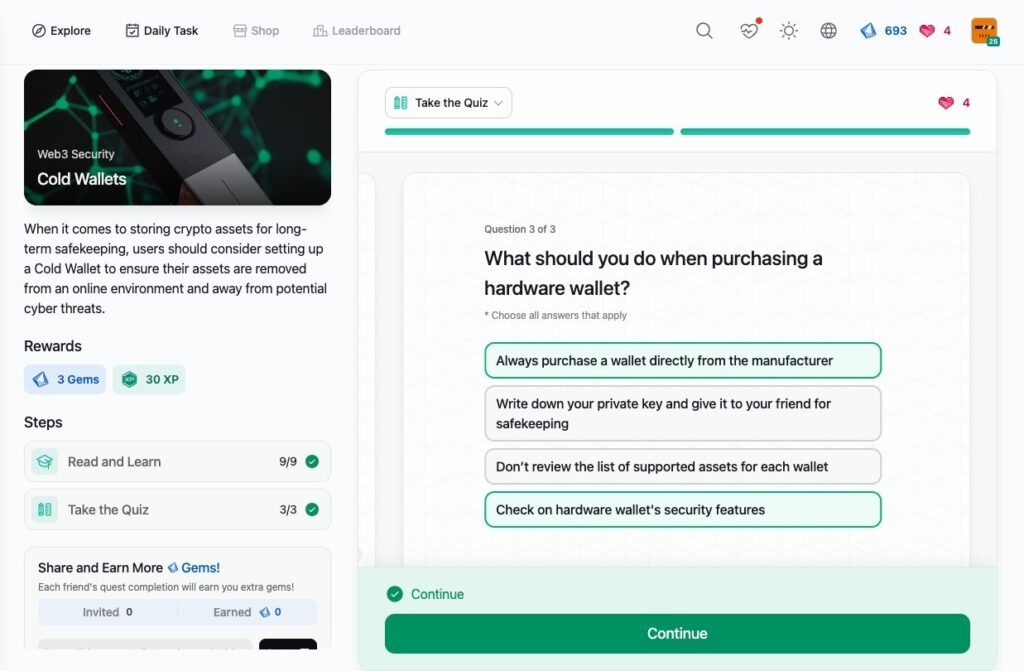
Cold Wallets
Common Web3 Phishing Methods
Community and Security Risks in Web3
Cybersecurity Best Practices for Telegram
DEXTools | Real-Time Trading Insights
Different Mechanisms for Honeypot Scams
Empowering Your Web3 Journey with Advanced Security Tools
Evaluating Cryptocurrency News Sources
Evaluating Security with Skynet Token Scan
Exploring Etherscan
GitHub Monitoring for Better Code Security
Governance Activity Monitoring
Governance and Security in DAOs
Hackers Infiltrating Crypto Job Boards
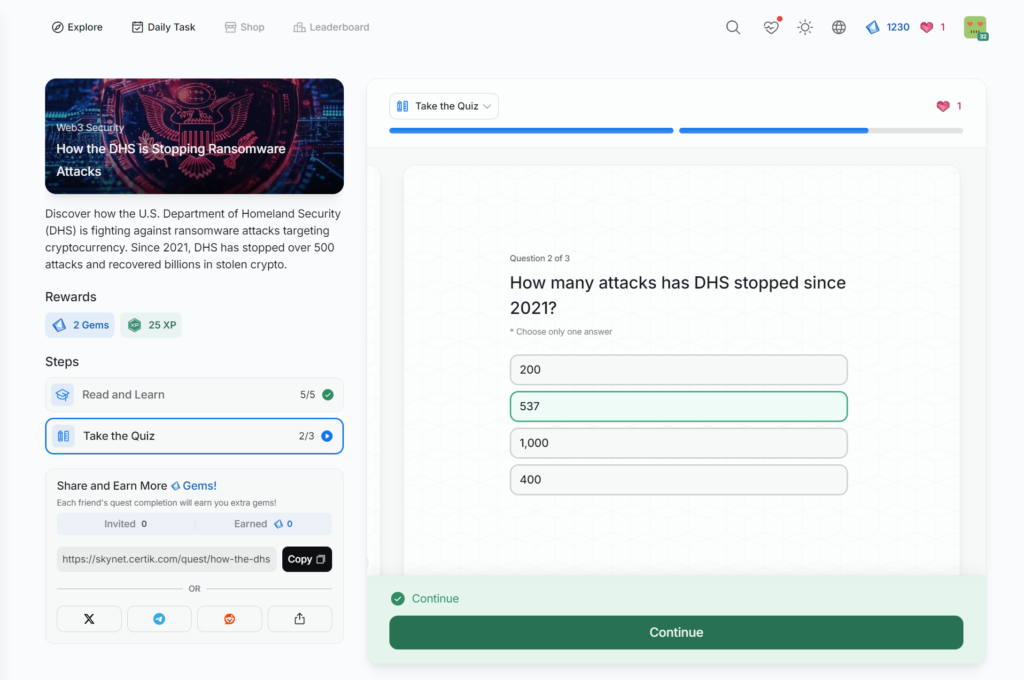
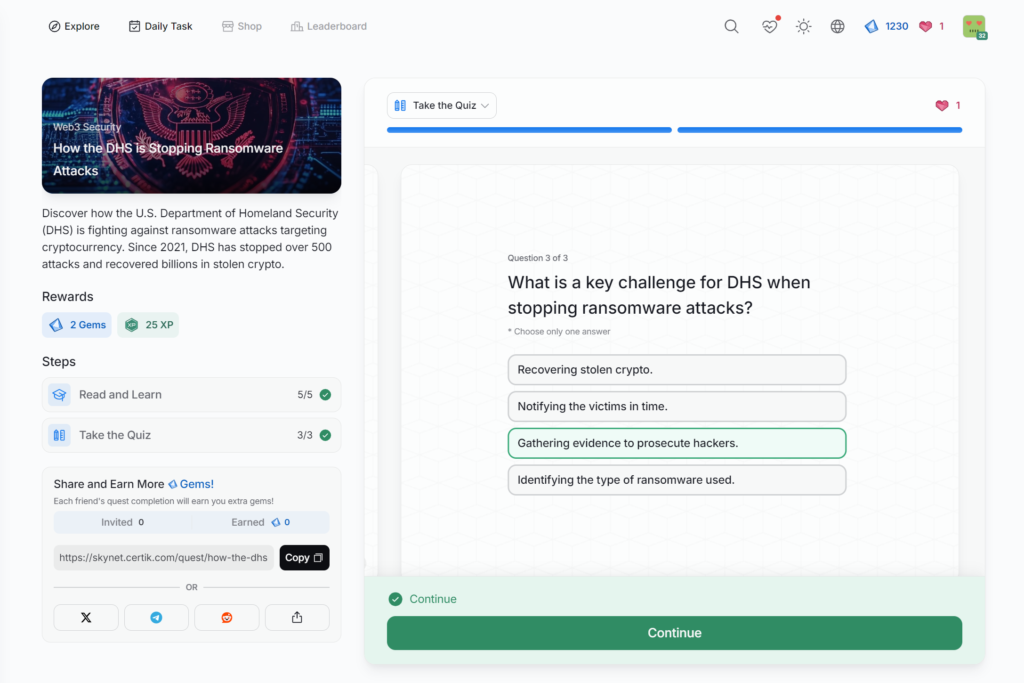
How the DHS is Stopping Ransomware Attacks
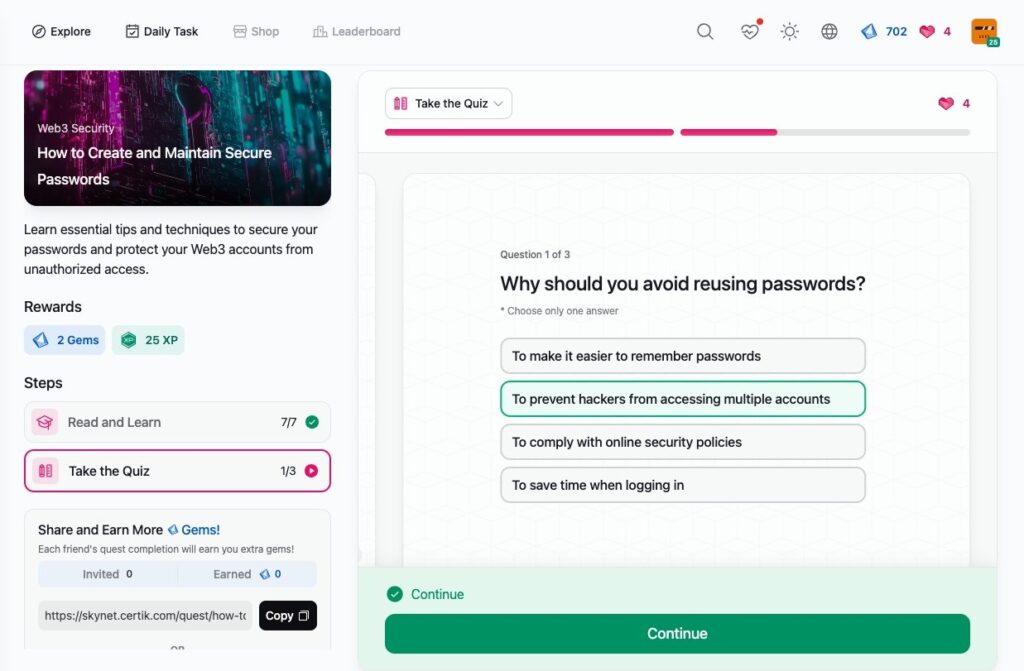
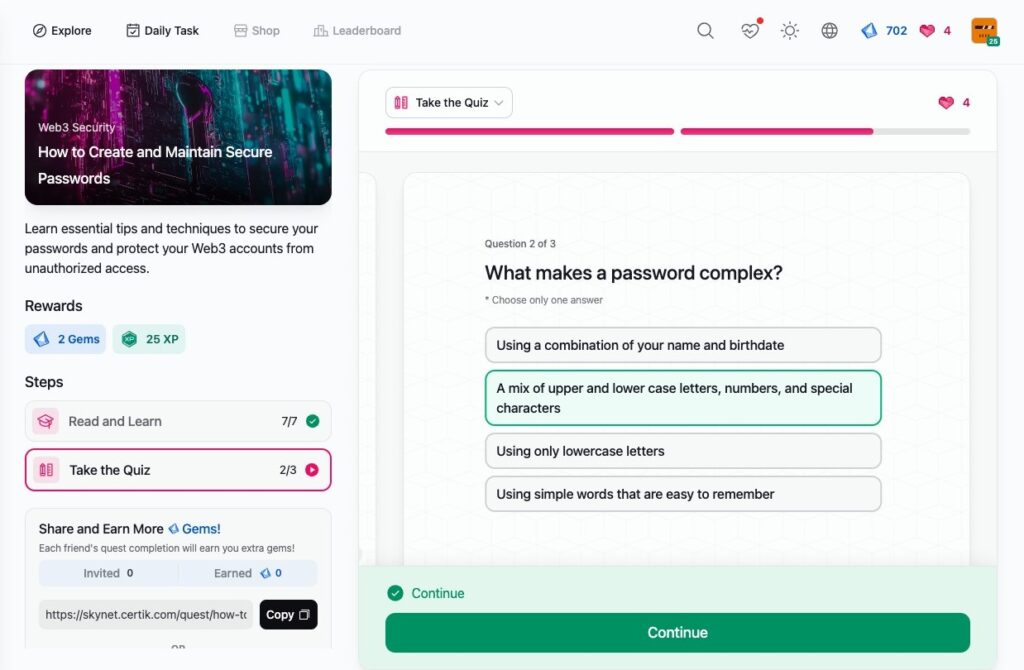
How to Create and Maintain Secure Passwords
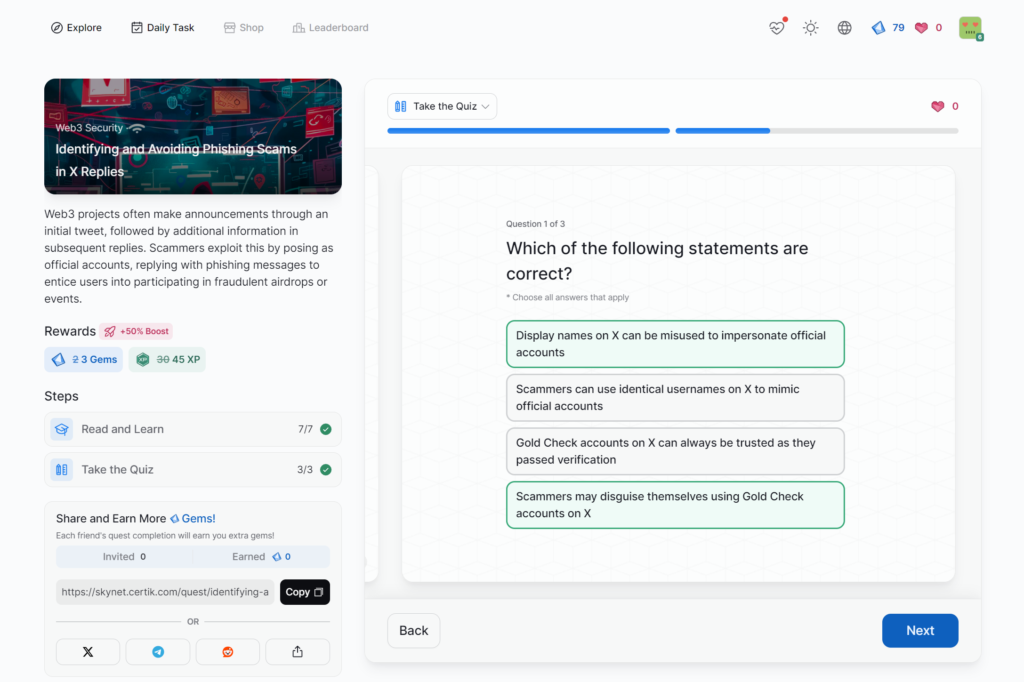
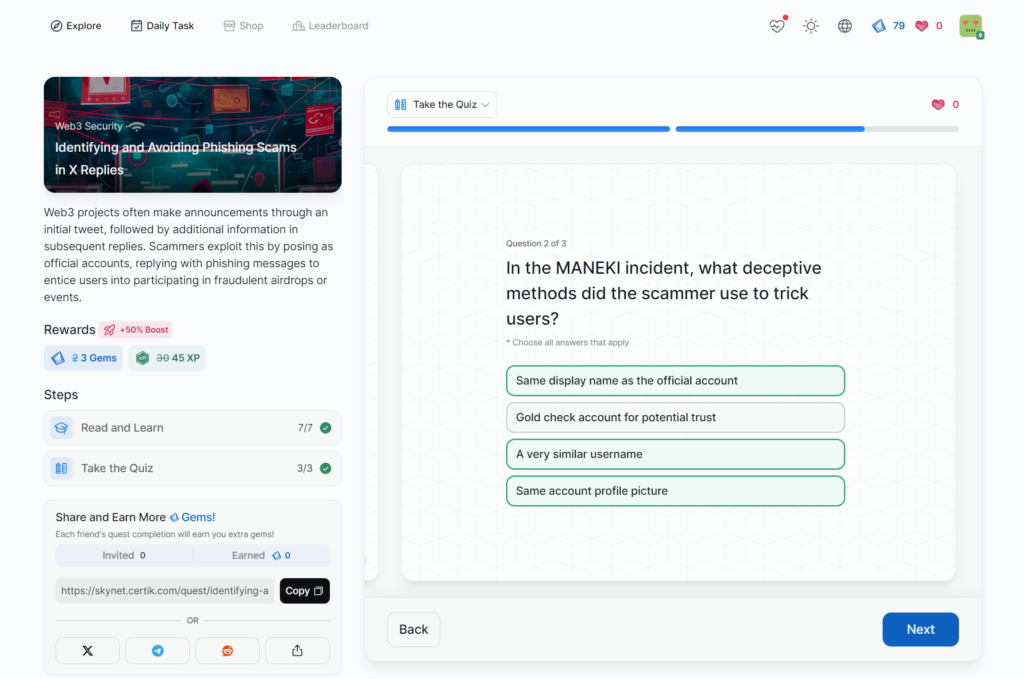
Identifying and Avoiding Phishing Scams in X Replies
Identifying Malicious Activity on Websites & dApps
Importance of Bug Bounty Programs in Web3
Important Exchange Security Features
Insights on Market Analytics
Insights on Token Holder Analysis
Intro to Airdrop Scams
Intro to AML and its Role in Crypto
Intro to Crypto Drainers
Introduction of Diamond Agency Contract
Introduction to Account Abstraction
Introduction to Formal Verification
Introduction to User Security
Introduction to Wallet Security
KYC Leaderboard Showcase
Losses Related to Private Key Compromises
Market-Related Risks
Multi-Signature Wallets Explained
Navigating NFT Security and Avoiding Scams
Operational Security
Operational Security via Website Scan
Prioritize Wallet Security with Skynet Wallet Scanning
Private Key Security
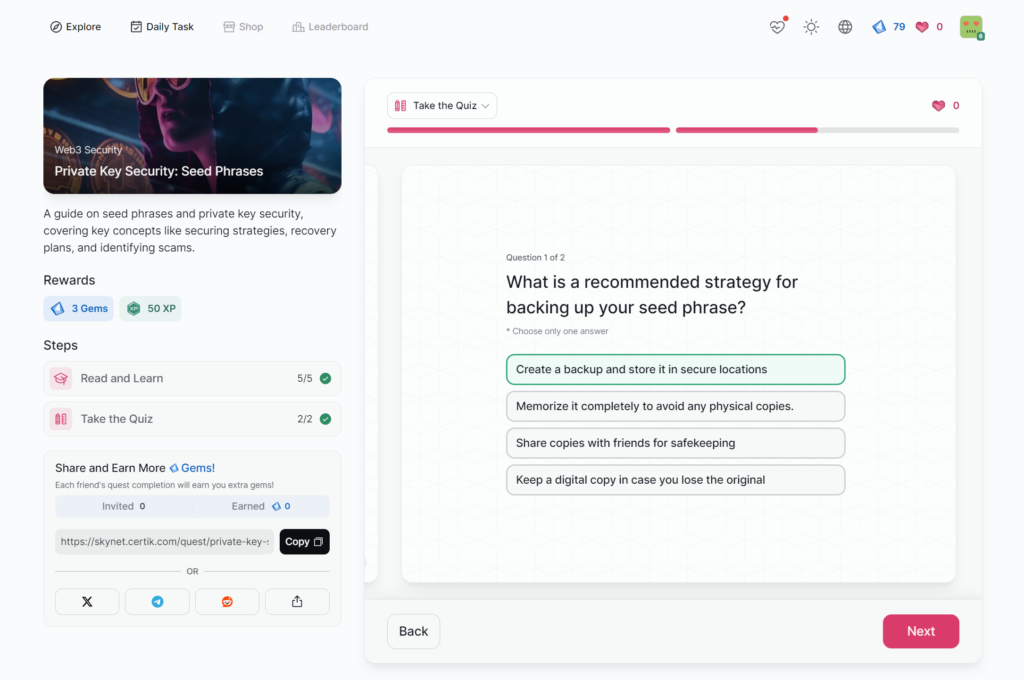
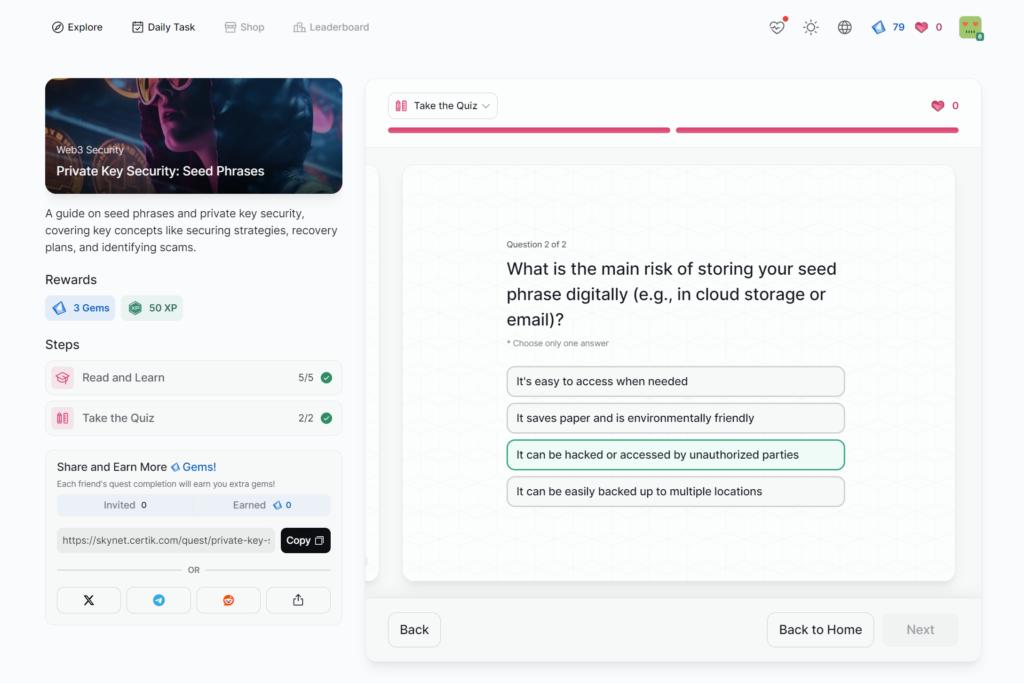
Private Key Security: Seed Phrases
Proof of Reserve
Protecting Against Crypto Phishing Scams During the Holiday Season
Protecting Against Social Engineering Attacks
Protecting Web3 Workers from Fake Meeting App Scams
Protecting Your PostgreSQL Database from Cryptojacking
Protecting Yourself from Discord Scams
Recognizing Risk Signals on the Exchange
Recognizing the Misuse of CertiK’s Brand
Scam Pattern on Telegram Safeguard
Secure Use of Exchanges
Security Rating for Pre-Launch Projects
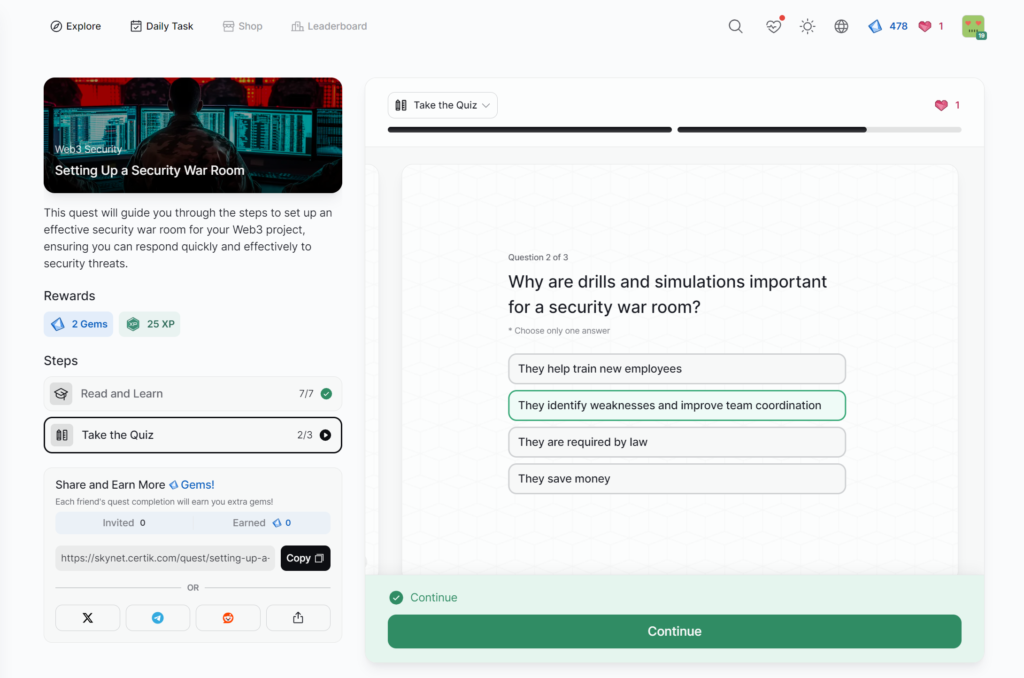
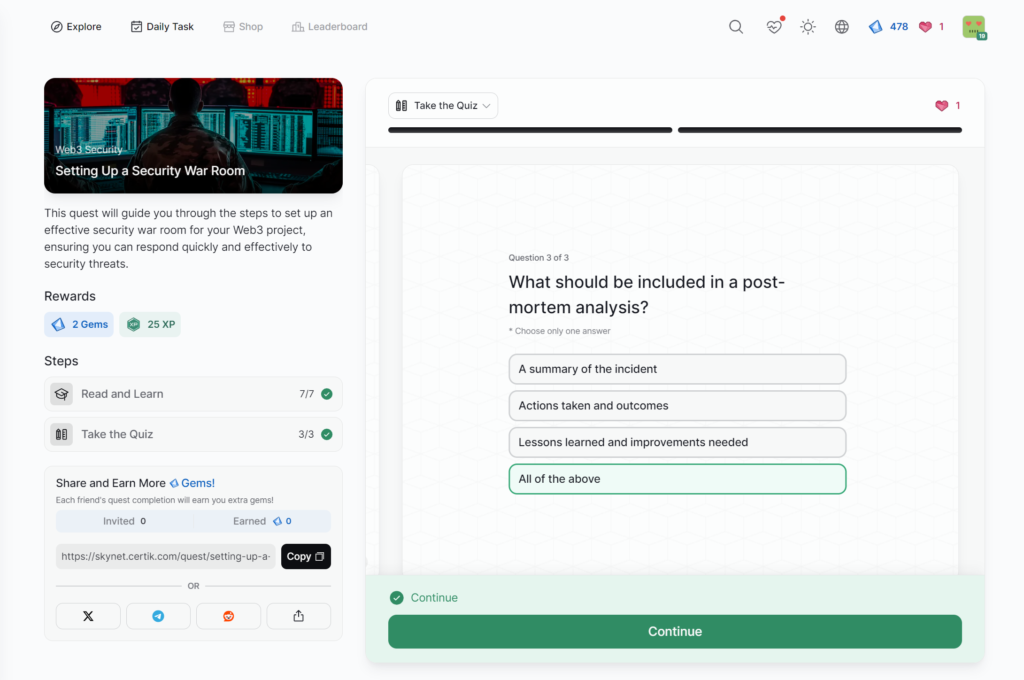
Setting Up a Security War Room
SIM Swap Attacks
Skynet Pulse – Real-Time Insights by Security Experts
SOC 2 Compliance for Crypto Companies
Stay Vigilant on Browser Plugins
Team and Insider Risks
The Power of Hashing
Top Compliance Risks in Crypto
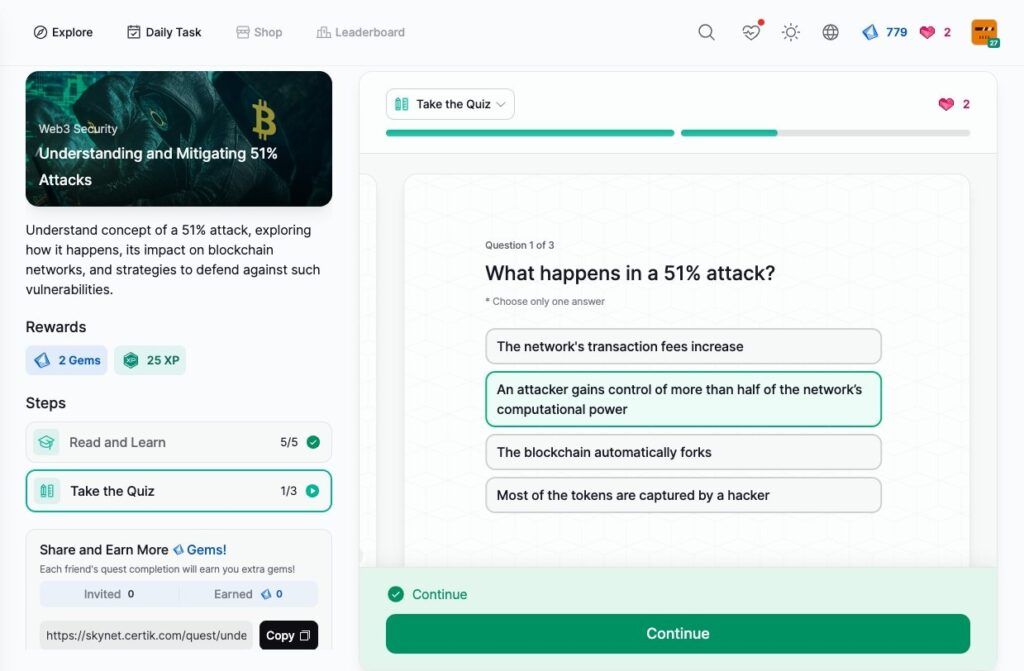
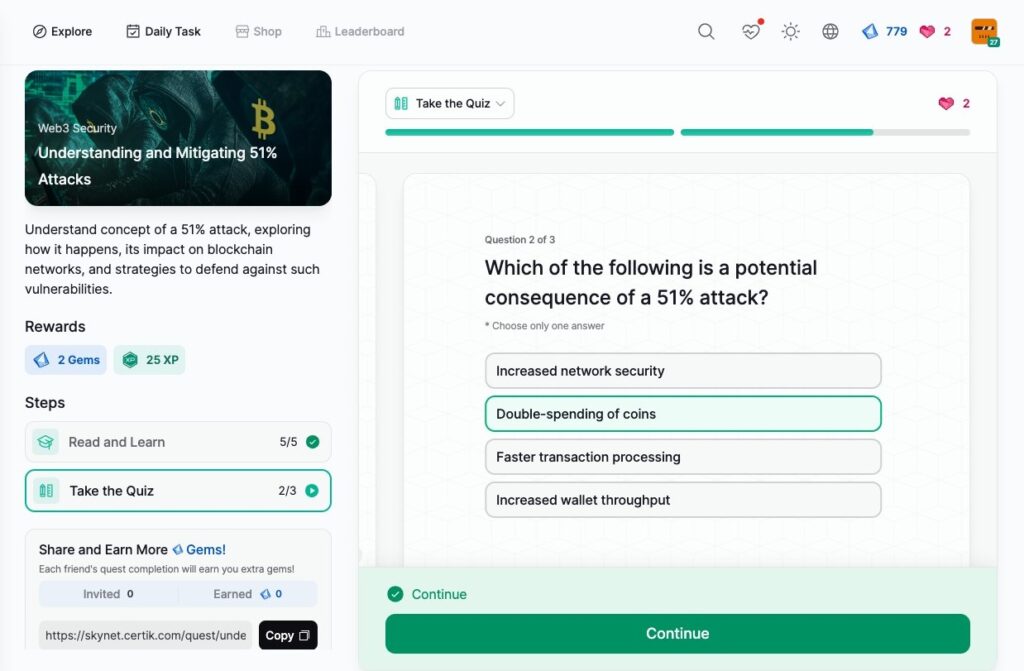
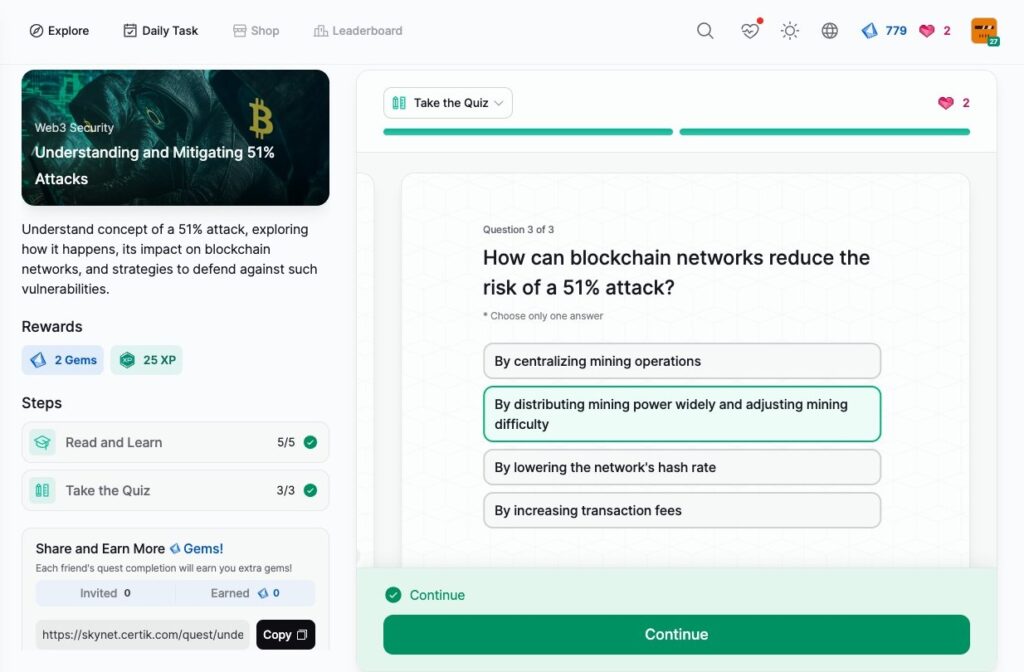
Understanding and Mitigating 51% Attacks
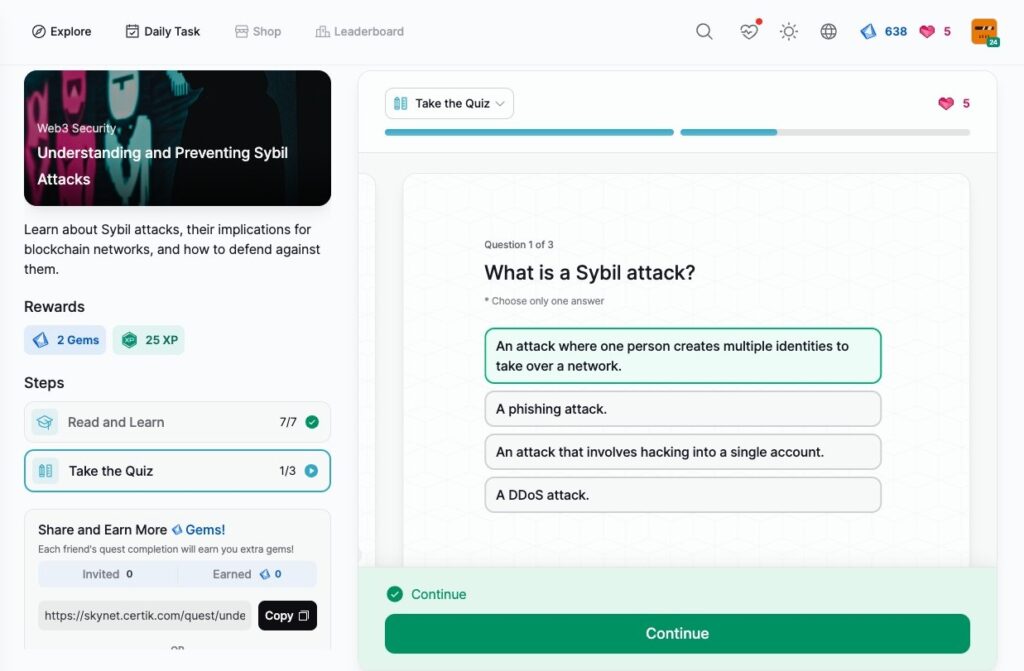
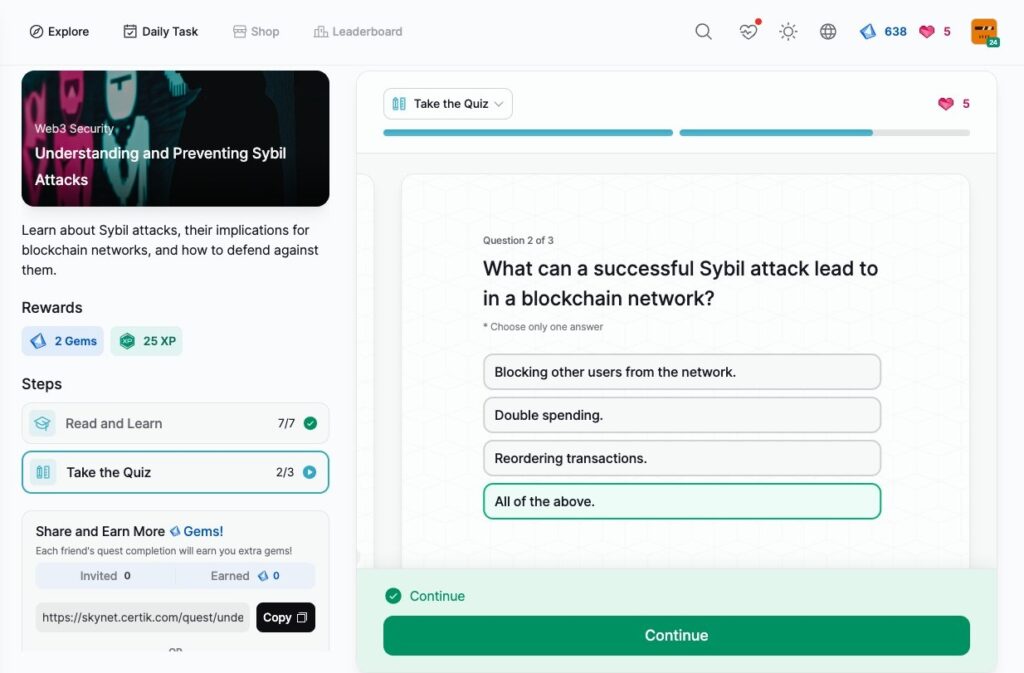
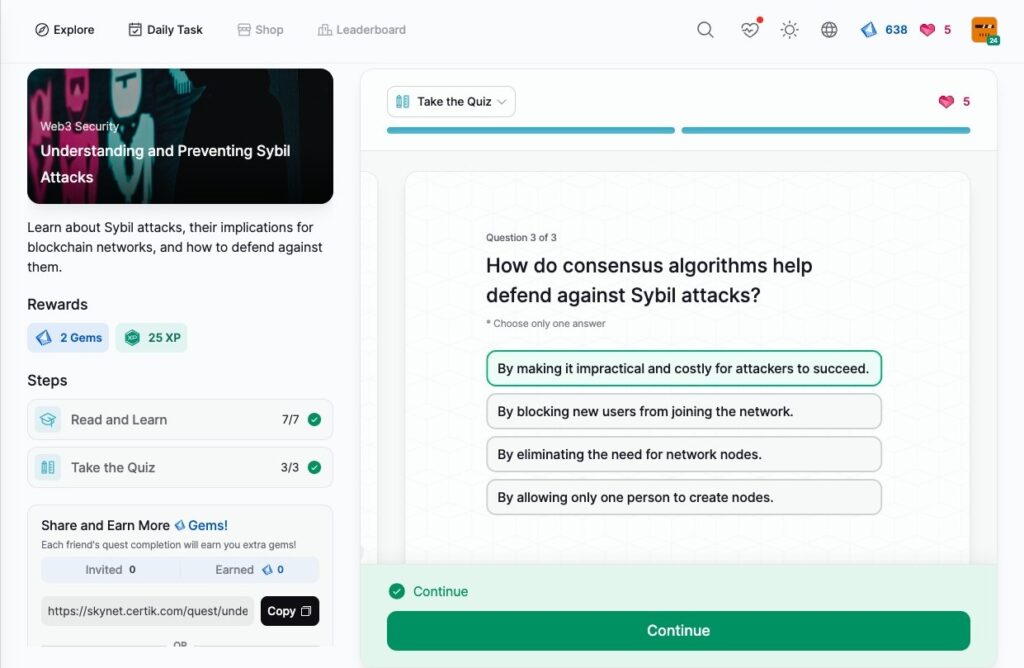
Understanding and Preventing Sybil Attacks
Understanding Chain Hopping and Crypto Money Laundering
Understanding Economic Exploits and Tokenomics
Understanding Soft Rug vs. Hard Rug Pulls
Understanding the Peel Chain Technique
Web3 Security with Skynet
Website & dApp Security
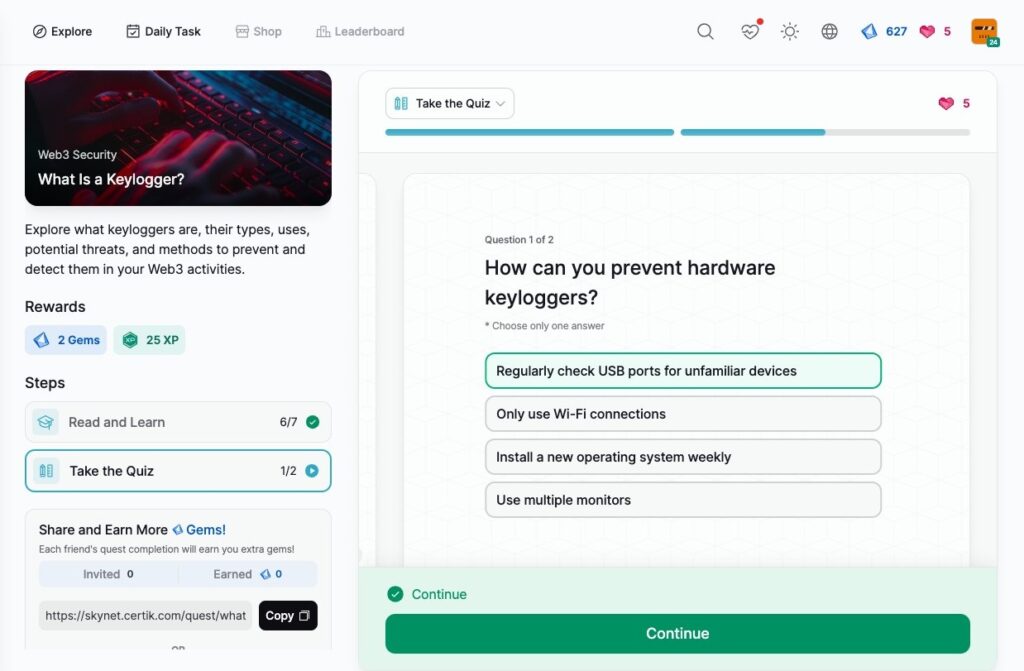
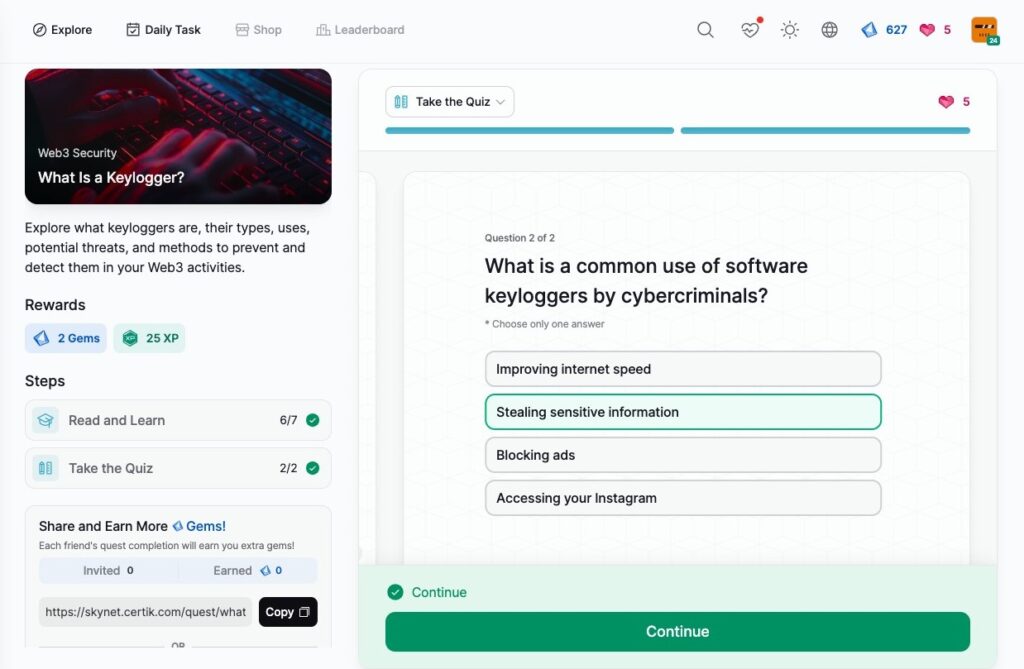
What Is a Keylogger?
Security Analysis
Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan – Part 1
Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan – Part 2
Blockchain Data Protection and Privacy Compliance
Case Study on the Risks of Phishing Attacks in DeFi
CertiK Hack3d 2024 Part 1 – Web3 Security by the Numbers
CertiK Hack3d 2024 Part 2 – Uncovering Major Incidents
CertiK Hack3d 2024 Part 3 – Building a Resilient Web3 Ecosystem
Clipper DEX Withdrawal Vulnerability Exploit
CryptoBottle Incident Analysis
Defending Against Clipper Malware
Enhancing Security Awareness for Web3 Desktop Wallets
Evaluating Popular Web3 Messaging Apps
Exploring the Security Model for Optimism’s Superchain
HACK3D Part 1: Top Incident Analyses
HACK3D Part 2: Private Key Compromise
HACK3D Part 3: Rounding Issue Exploits
Hedgey Finance Event Analysis
Identifying Crypto Market Manipulation
Navigating DAO Governance and the Compound DAO Incident
Normie Incident Analysis
Private Key Security
Private Key Security: Seed Phrases
Quantum Computing and the Future of Cryptocurrency Security
Securing Solana SPL Contracts
Sonne Finance Incident Analysis
The Memecoin Markets of Springfield
Understanding the Polter Finance Exploit
UtopiaSphere Incident Analysis
WazirX Hack Incident Analysis
Project Spotlights
Aptos | Layer 1
Arbitrum | Layer 2
Core DAO | Infrastructure
Diamante Blockchain | Infrastructure
Edu3Labs | The Future of Education
EigenLayer | Infrastructure
Ethena | Stablecoin
FriendTech | Social
GOAT | AI Bot Meme
HanChain | Transforming Music Copyright
Kendu Inu | Organic Meme Community
Massa | The First Decentralized Cloud Network
MetaMask Overview
Mint Club | Building Your Bonding Curve
Mintlayer | Build on Bitcoin
OKX Wallet | Multi-Chain Web3 Wallet
Ondo Finance | RWA
OpenGPU | Harnessing Decentralized GPU Computing
Patex | Latin American Blockchain Ecosystems
PAW Chain | Ecosystem
PEPE | Meme
Phantom Wallet | Solana and Web3 Wallet
Polymarket | Prediction Markets
Pump.Fun
Ripple (XRP Ledger) | Layer 1
Script Network | Open Source Video Protocol
Solidus AI Tech | High-Performance Computing
SpunkySDX | Revolutionizing Commerce with Blockchain and AI
TNQ
TON | Layer 1
Trinique | RAT
WEXO | Global Payment Infrastructure
World of Dypians | Future of Gaming, DeFi, NFTs and AI
Worldcoin | Store of Value
Wormhole | Infrastructure
zkSwap Finance | DeFi
Skynet Platform
Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan – Part 1
Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan – Part 2
Best Practices for Wallet Security
Best Tools for Tracking Top Crypto Wallets
Choosing a Secure Exchange
Code Security
Community and Security Risks in Web3
Empowering Your Web3 Journey with Advanced Security Tools
Evaluating Security with Skynet Token Scan
GitHub Monitoring for Better Code Security
Governance Activity Monitoring
Governance and Security in DAOs
How CertiK Does KYC
How to Ace the CertiK KYC Badge
Identifying Malicious Activity on Websites & dApps
Important Exchange Security Features
Insights on Market Analytics
Insights on Token Holder Analysis
Introduction to Formal Verification
Introduction to User Security
Introduction to Wallet Security
KYC Leaderboard Showcase
Losses Related to Private Key Compromises
Market-Related Risks
Operational Security
Operational Security via Website Scan
Prioritize Wallet Security with Skynet Wallet Scanning
Proof of Reserve
Recognizing Risk Signals on the Exchange
RWA Security and Leaderboard
Security Rating for Pre-Launch Projects
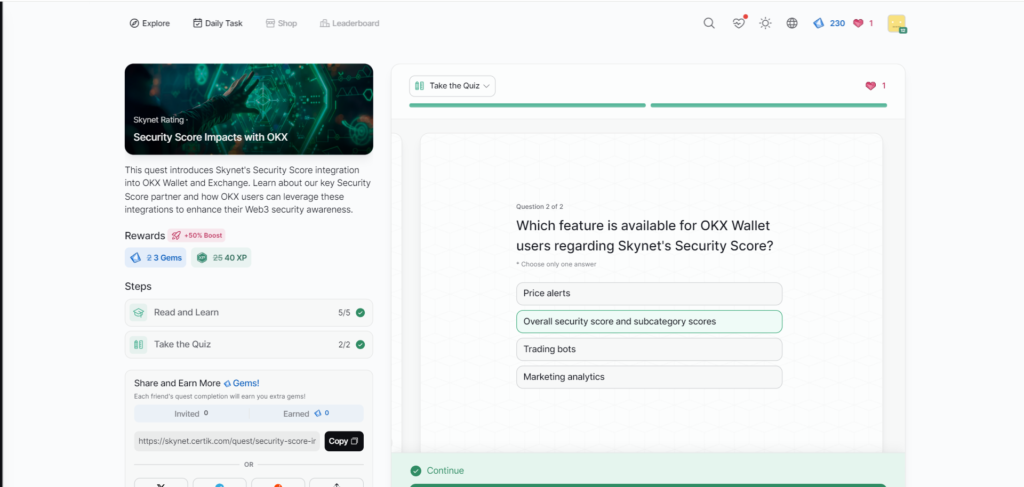
Security Score Impacts with OKX
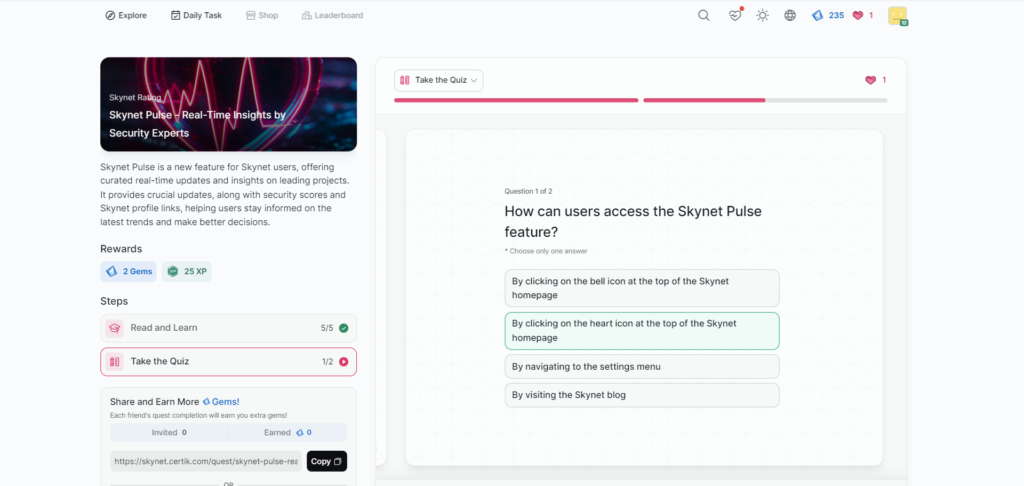
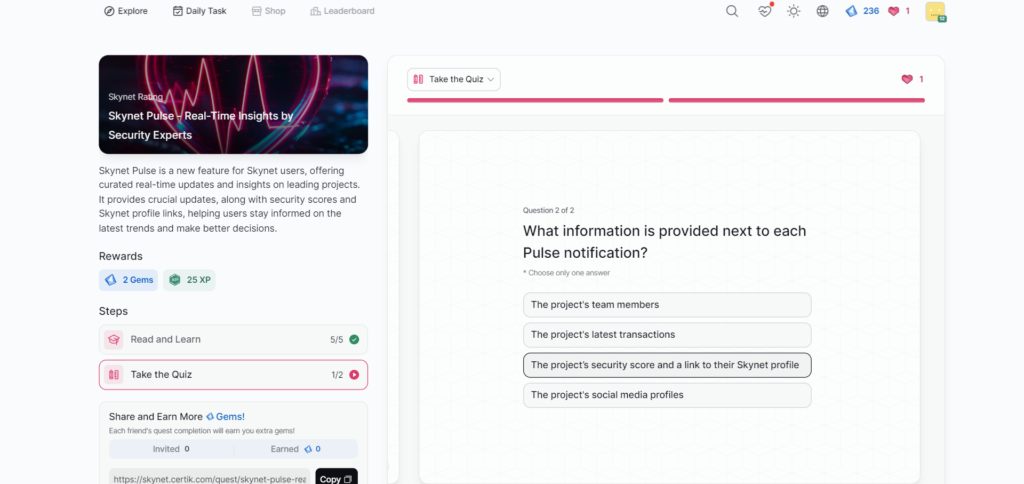
Skynet Pulse – Real-Time Insights by Security Experts
Stay Ahead with Skynet’s Smart Calendar
Team and Insider Risks
Web3 Security with Skynet
Website & dApp Security
CertiK Highlights
Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan – Part 1
Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan – Part 2
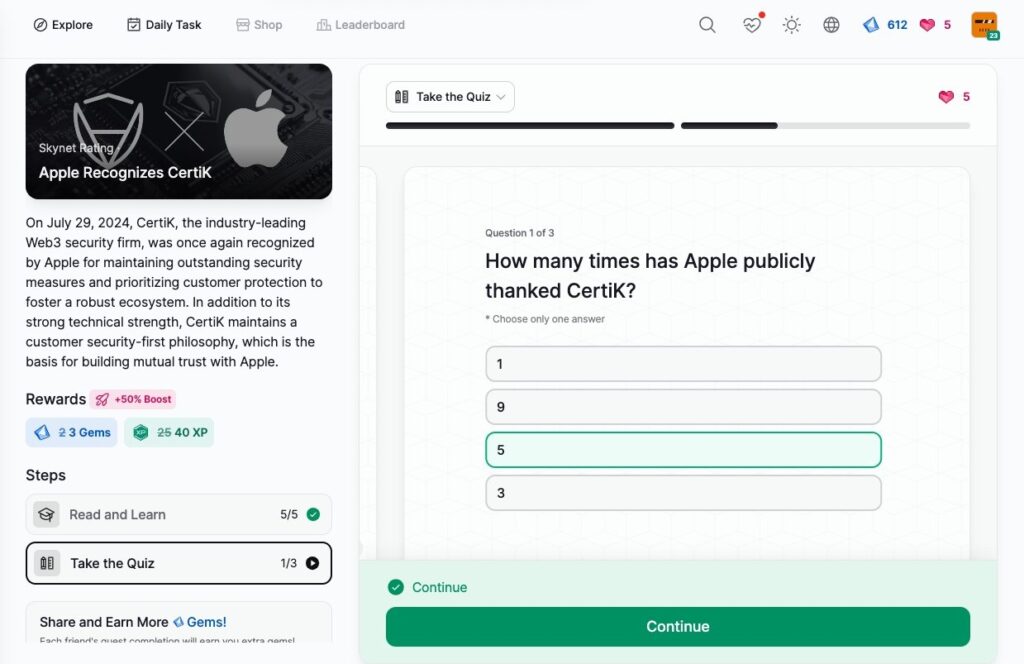
Apple Recognizes CertiK
CertiK Uncovers Vulnerability in Apple Vision Pro
CertiK Ventures
CertiK Ventures Announcement in Singapore
CertiK’s Journey to Samsung’s Security Hall of Fame
Hack3d Part 1: Most Common Attack Vectors in Q3 2024
HACK3D Part 1: Top Incident Analyses
Hack3d Part 2: Major Hacks of Q3 2024
HACK3D Part 2: Private Key Compromise
HACK3D Part 3: Rounding Issue Exploits
Hack3d Report Q2 H1 2024 – Part 1: Overview and Key Highlights
Hack3d Report Q2 H1 2024 – Part 2: Insights and Future Security Enhancements
How CertiK Does KYC
How to Ace the CertiK KYC Badge
Interview with Professor Ronghui Gu: “Who Monitors the Monitors?”
OKX and CertiK Fast Pass Program
Security Score Impacts with OKX
SkyInsights: Crypto Compliance
Understanding SkyNode: Blockchain’s Secure Foundation
Web3 Fundamentals
Best Practices for Wallet Security
Best Tools for Tracking Top Crypto Wallets
Case Study on Enhancing Security for App Chains
Choosing a Secure Exchange
Code Security
Cold Wallets
Common Web3 Phishing Methods
Community and Security Risks in Web3
DEXTools | Real-Time Trading Insights
Different Mechanisms for Honeypot Scams
Empowering Your Web3 Journey with Advanced Security Tools
Evaluating Cryptocurrency News Sources
Evaluating Memecoin Liquidity
Evaluating Security with Skynet Token Scan
Exploring Etherscan
Exploring PSBT in Bitcoin DeFi Ecosystem
Exploring the Rise of AI Memecoins
Fundraising in the Web3 Industry
GitHub Monitoring for Better Code Security
Governance Activity Monitoring
Governance and Security in DAOs
Hackers Infiltrating Crypto Job Boards
How CertiK Does KYC
How the DHS is Stopping Ransomware Attacks
How to Create and Maintain Secure Passwords
Identifying and Avoiding Phishing Scams in X Replies
Identifying Malicious Activity on Websites & dApps
Importance of Bug Bounty Programs in Web3
Important Exchange Security Features
Insights on Market Analytics
Insights on Token Holder Analysis
Intro to Airdrop Scams
Intro to AML and its Role in Crypto
Intro to Crypto Drainers
Introduction of Diamond Agency Contract
Introduction to Account Abstraction
Introduction to Formal Verification
Introduction to User Security
Introduction to Wallet Security
KYC Leaderboard Showcase
Losses Related to Private Key Compromises
Market-Related Risks
Multi-Signature Wallets Explained
Navigating NFT Security and Avoiding Scams
Operational Security
Operational Security via Website Scan
Private Key Security
Private Key Security: Seed Phrases
Proof of History Overview
Proof of Reserve
Proof of Work versus Proof of Stake
Protecting Against Social Engineering Attacks
Protecting Your PostgreSQL Database from Cryptojacking
Protecting Yourself from Discord Scams
Pump.Fun
Recognizing Risk Signals on the Exchange
Recognizing the Misuse of CertiK’s Brand
RWA Security and Leaderboard
Secure Use of Exchanges
Securing Solana SPL Contracts
Security Rating for Pre-Launch Projects
Setting Up a Security War Room
SIM Swap Attacks
SOC 2 Compliance for Crypto Companies
Stablecoin Risks: Identifying and Mitigating Vulnerabilities
Stay Vigilant on Browser Plugins
Team and Insider Risks
Top Compliance Risks in Crypto
Understanding and Mitigating 51% Attacks
Understanding and Preventing Sybil Attacks
Understanding Chain Hopping and Crypto Money Laundering
Understanding Economic Exploits and Tokenomics
Understanding Soft Rug vs. Hard Rug Pulls
Understanding Stablecoin Reserves
Understanding the Peel Chain Technique
Understanding U.S. Crypto Tax Forms
Unlocking Ethereum ETFs With BlackRock’s ETHA
Web3 Security with Skynet
Website & dApp Security
What Is a Keylogger?
What is DePIN?
CertiK Ventures
Web3 Security with Skynet
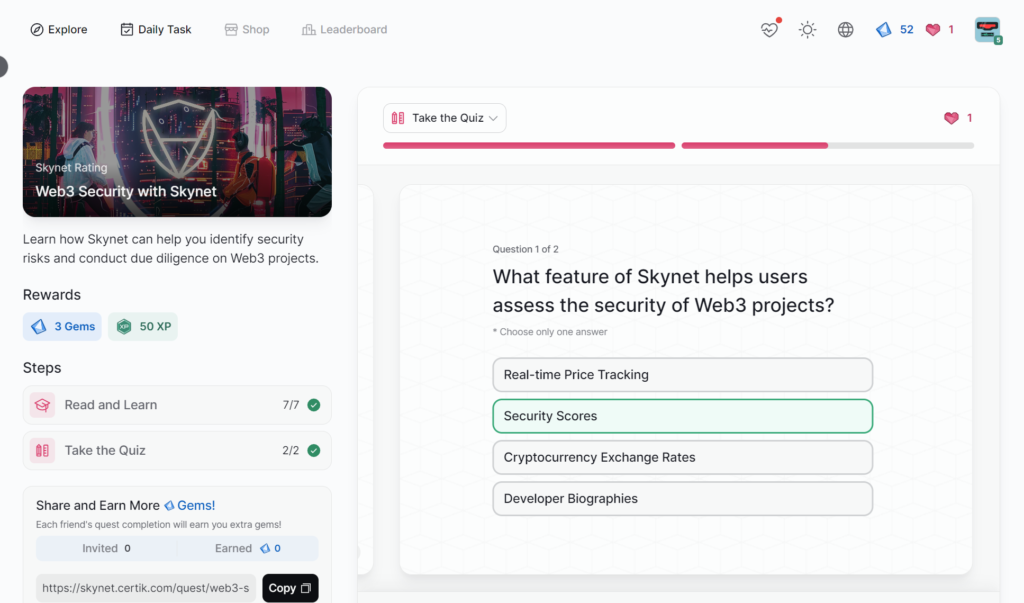
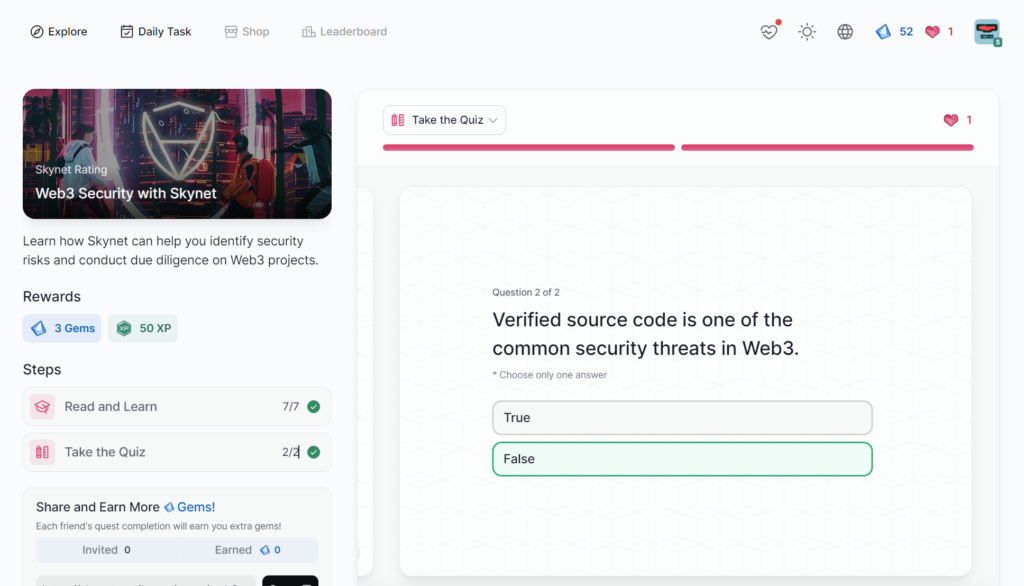
Code Security
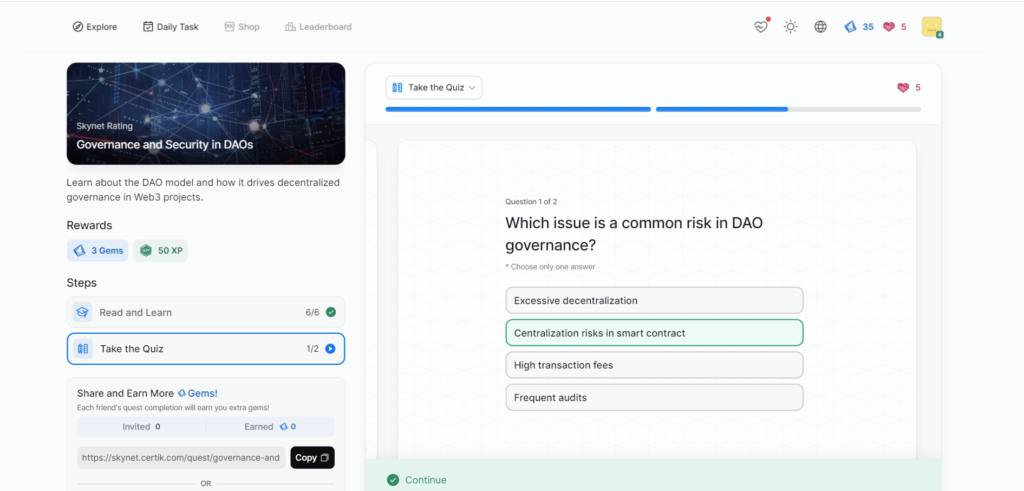
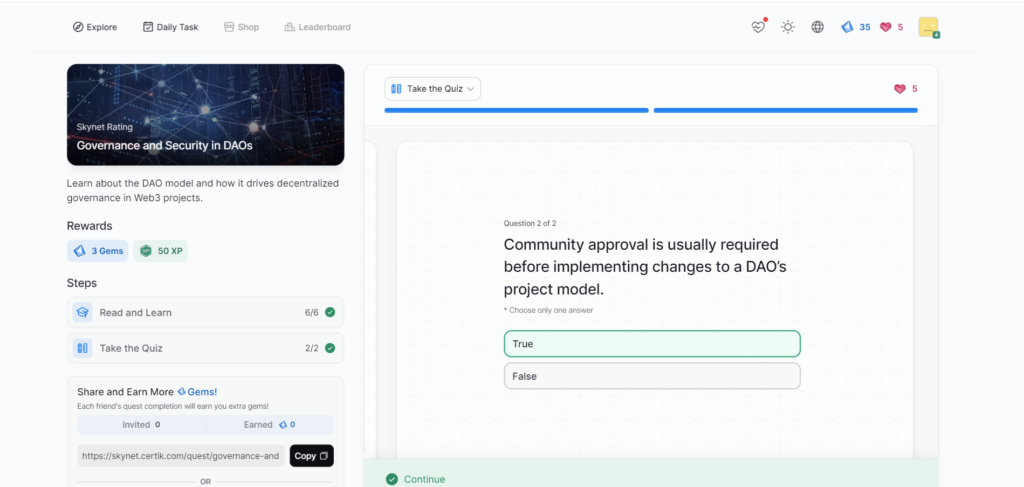
Governance and Security in DAOs
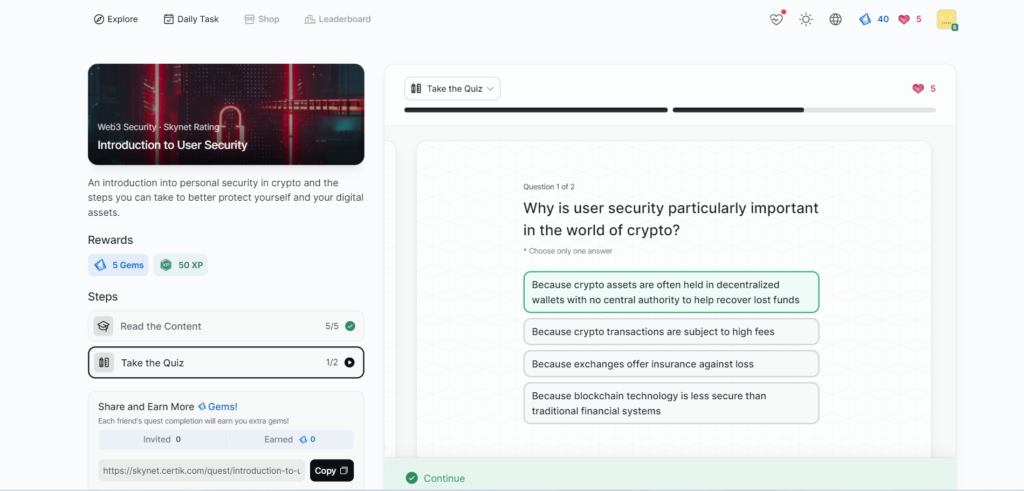
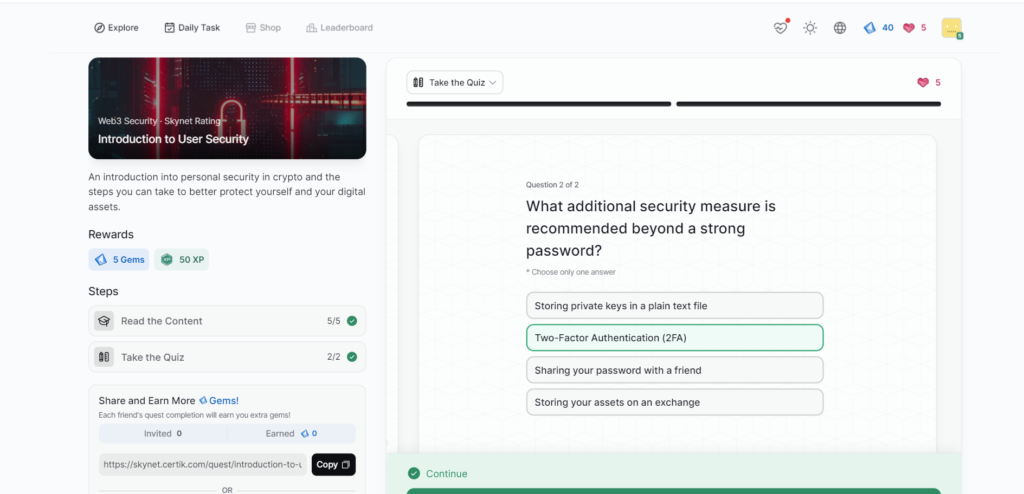
Introduction to User Security
Operational Security
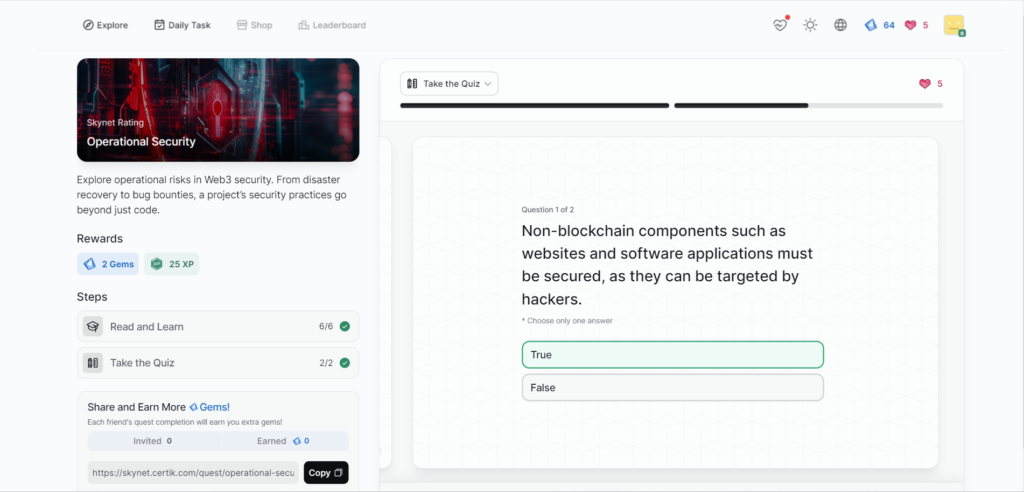
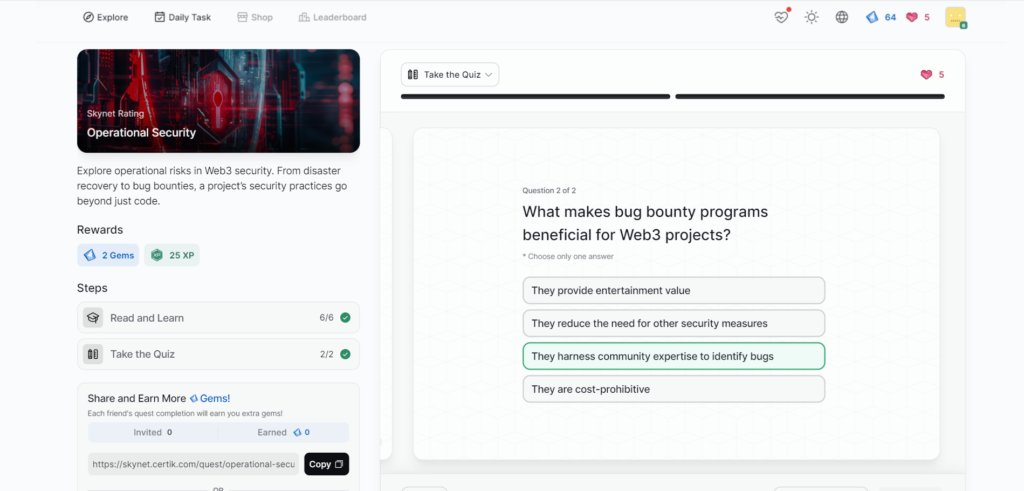
Team and Insider Risks
Market-Related Risks
Community and Security Risks in Web3
Insights on Token Holder Analysis
Security Rating for Pre-Launch Projects
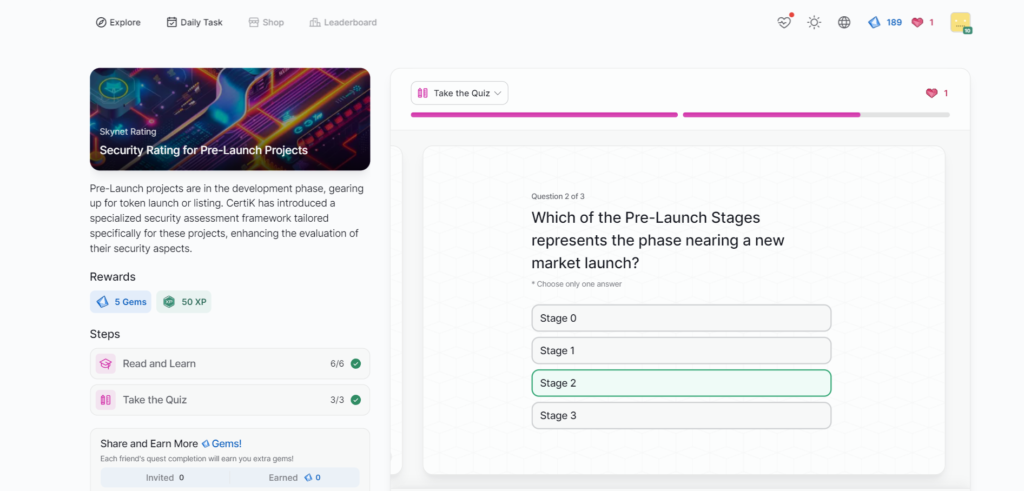
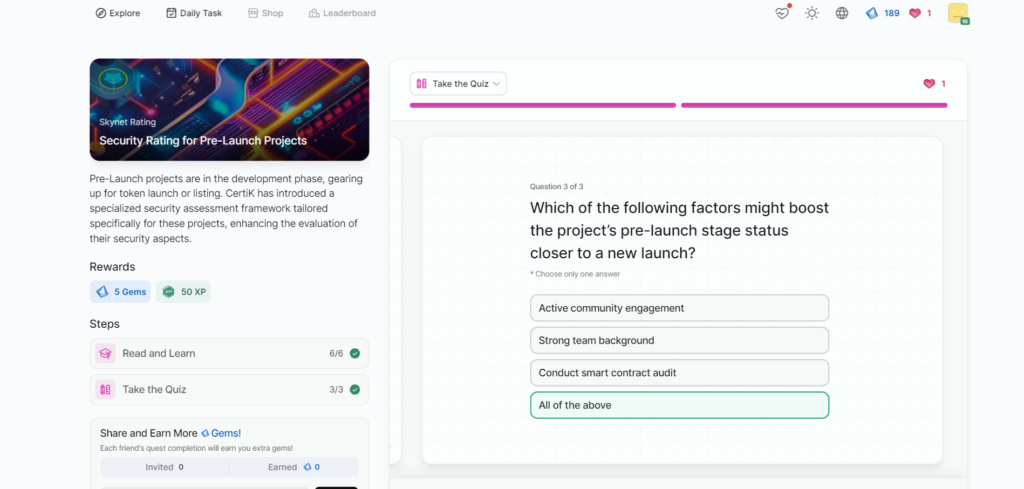
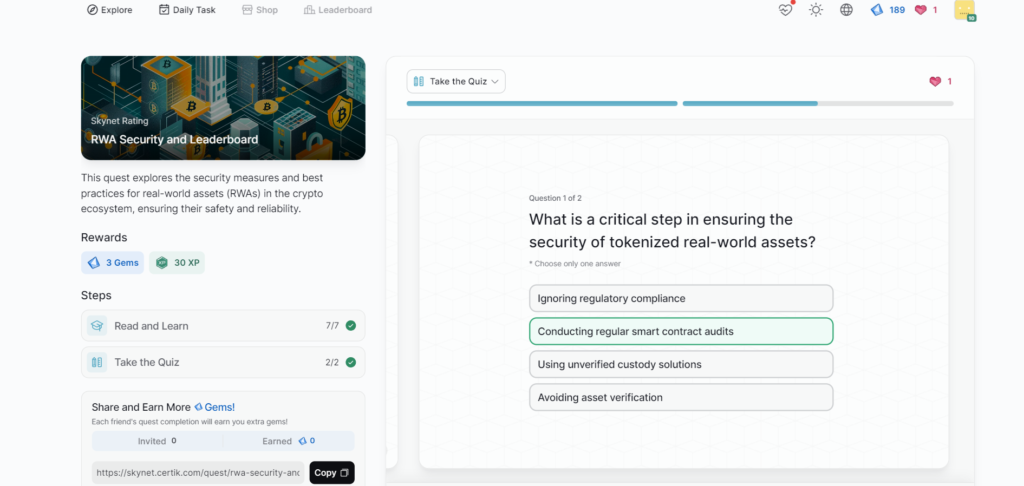
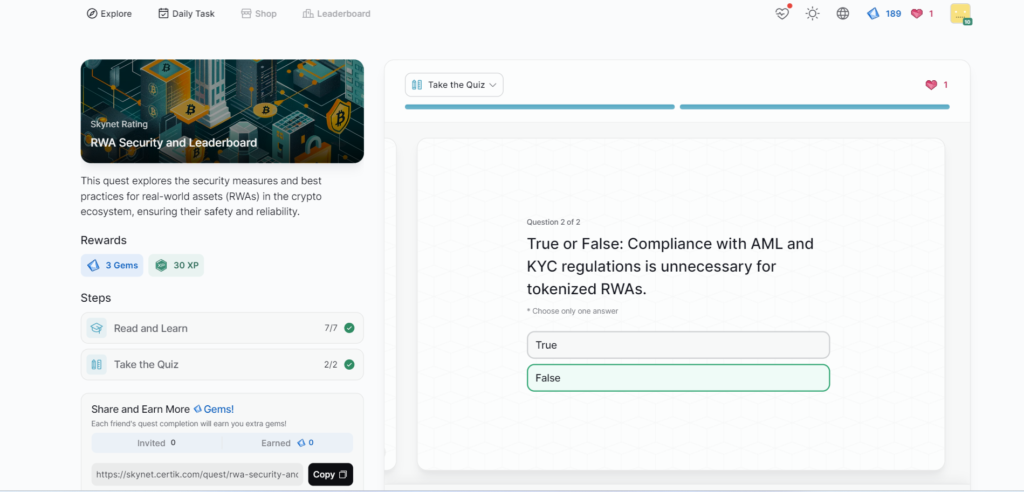
RWA Security and Leaderboard
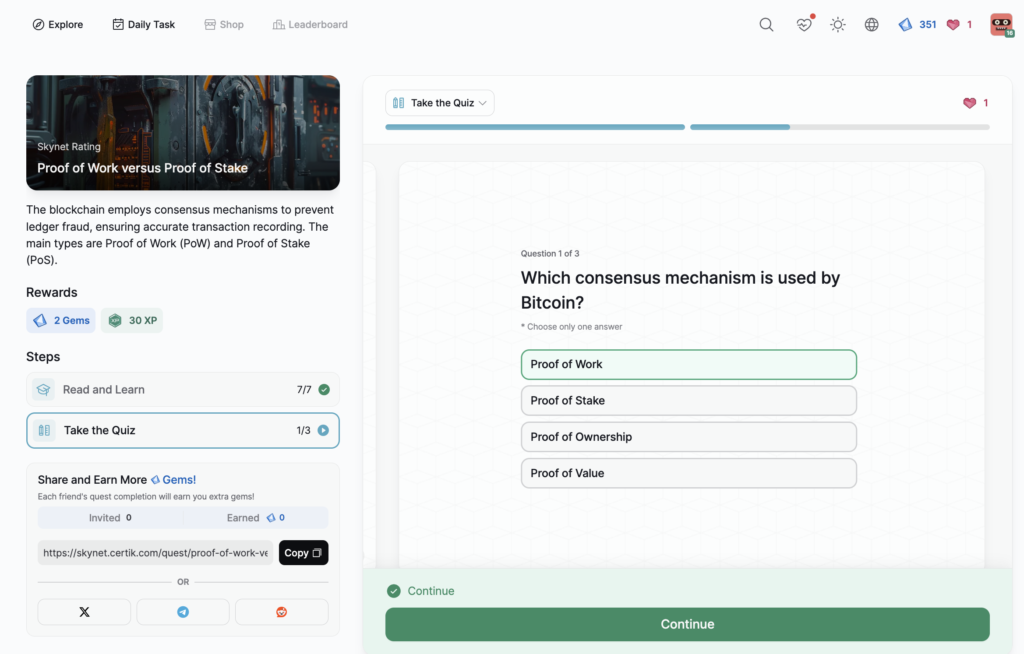
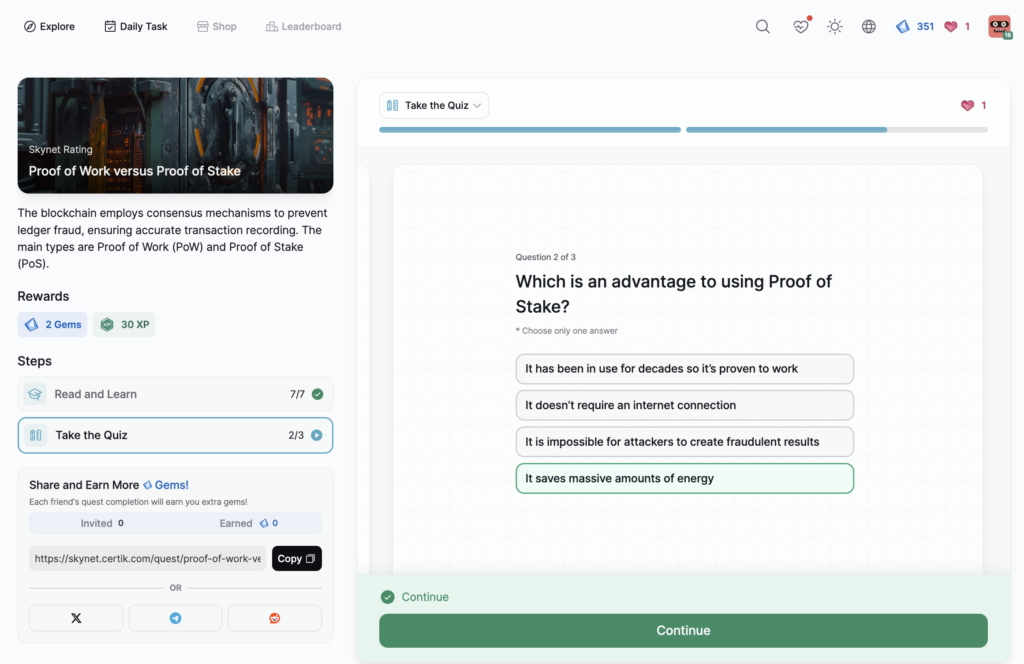
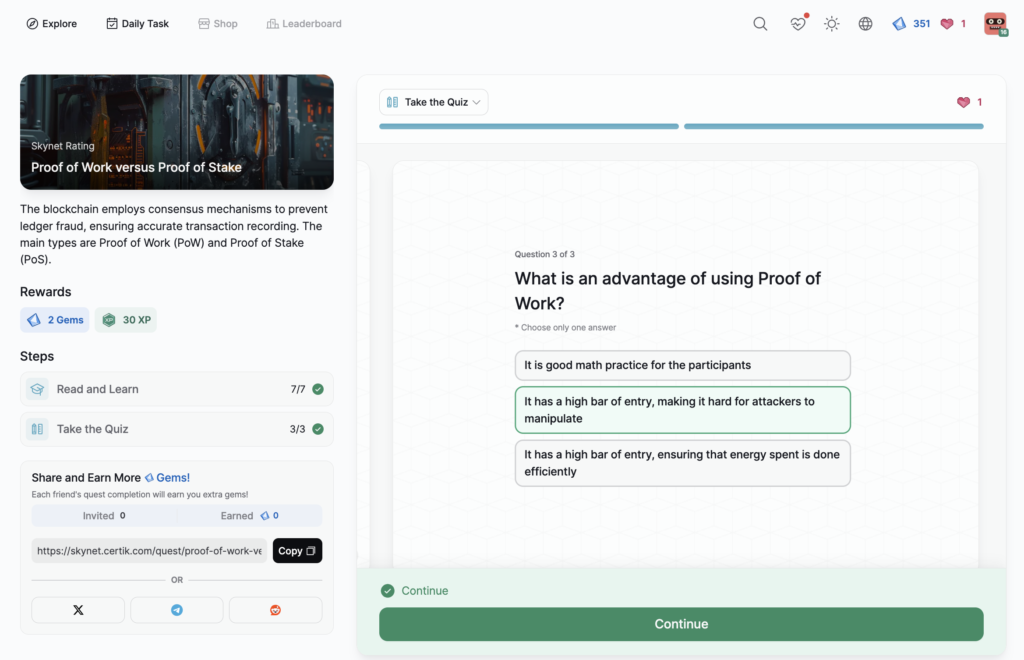
Proof of Work versus Proof of Stake
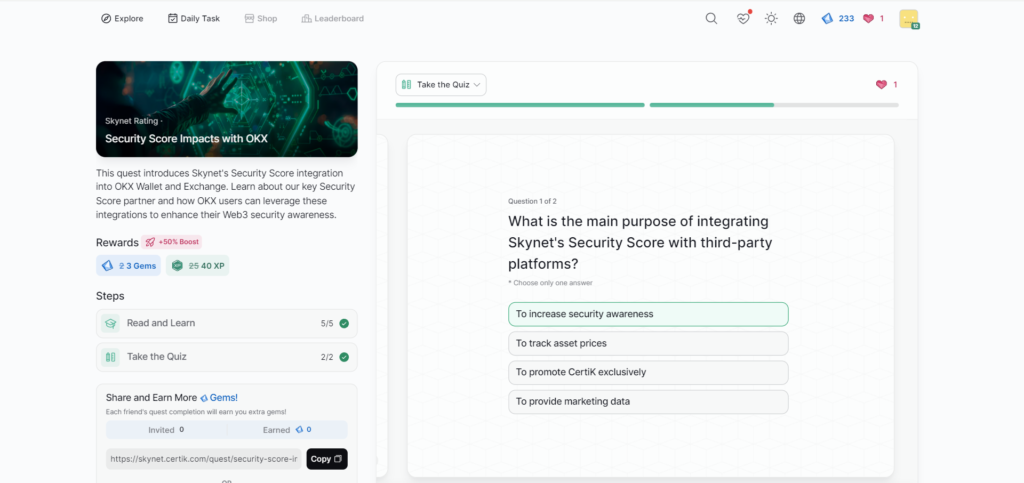
Security Score Impacts with OKX
Skynet Pulse – Real-Time Insights by Security Experts
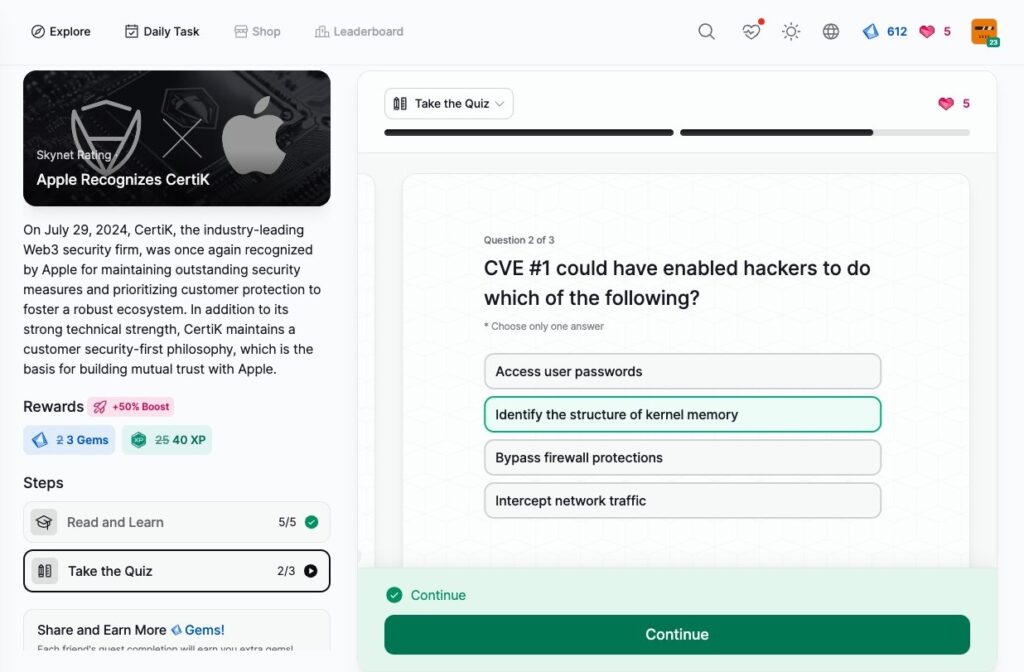
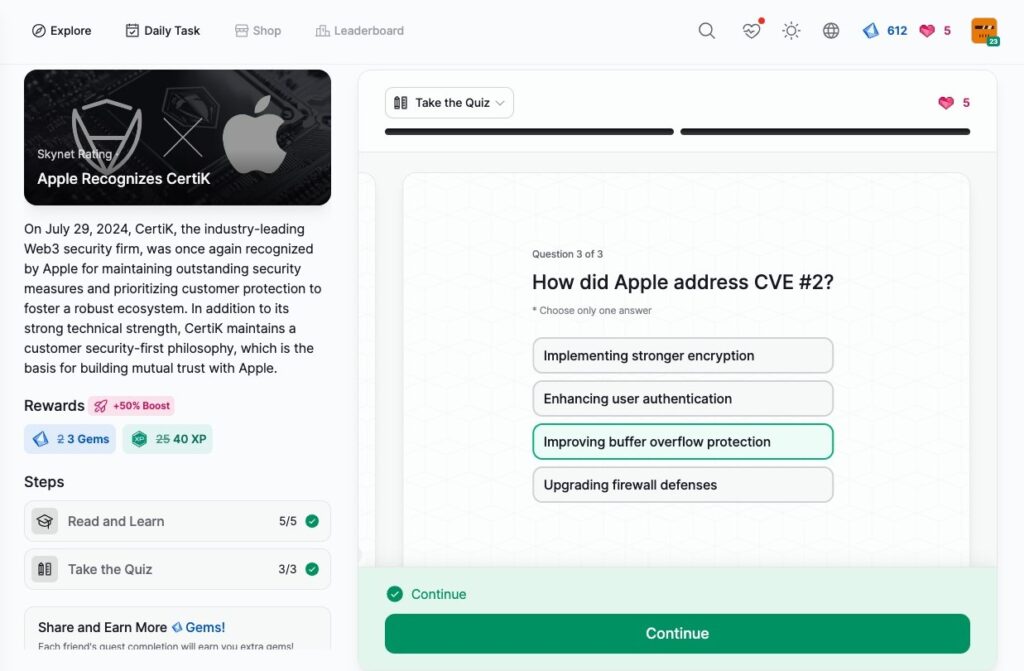
Apple Recognizes CertiK
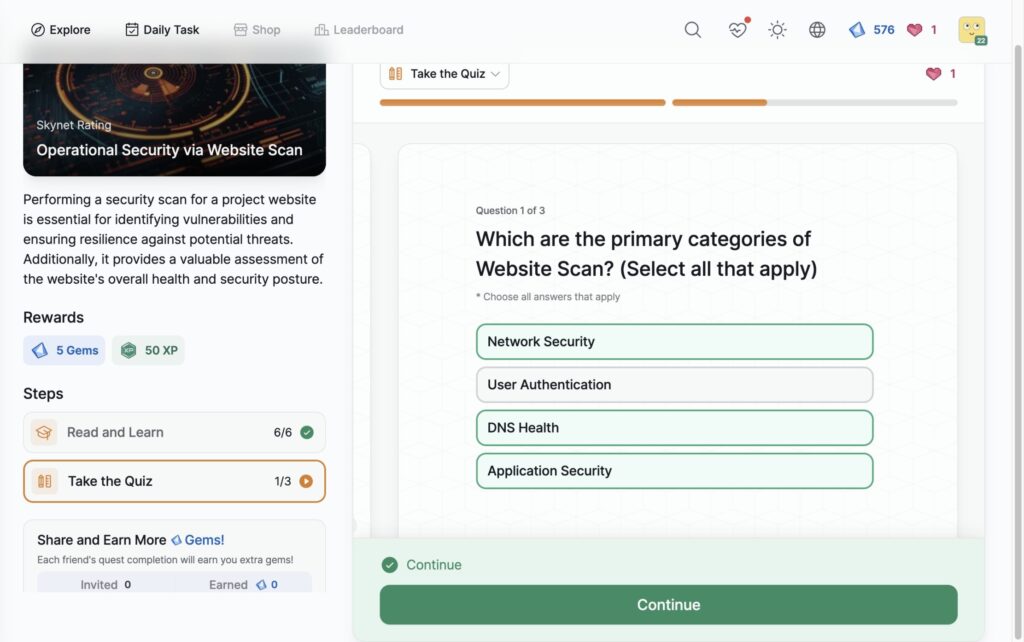
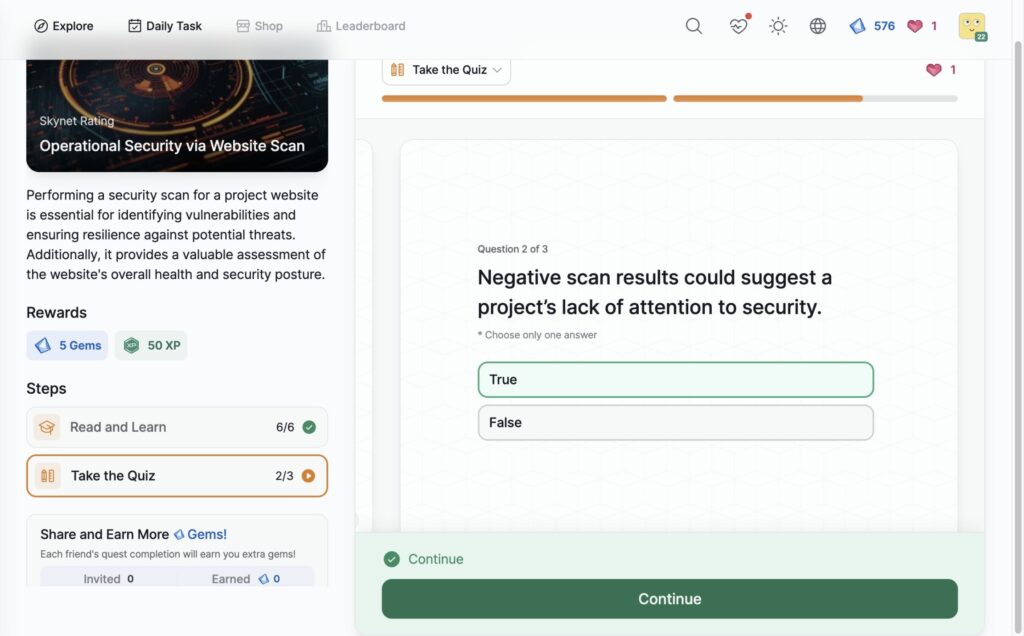
Operational Security via Website Scan
Insights on Market Analytics
GitHub Monitoring for Better Code Security
Governance Activity Monitoring
Apple Recognizes CertiK
Evaluating Security with Skynet Token Scan
Stay Ahead with Skynet’s Smart Calendar
KYC Leaderboard Showcase
Prioritize Wallet Security with Skynet Wallet Scanning
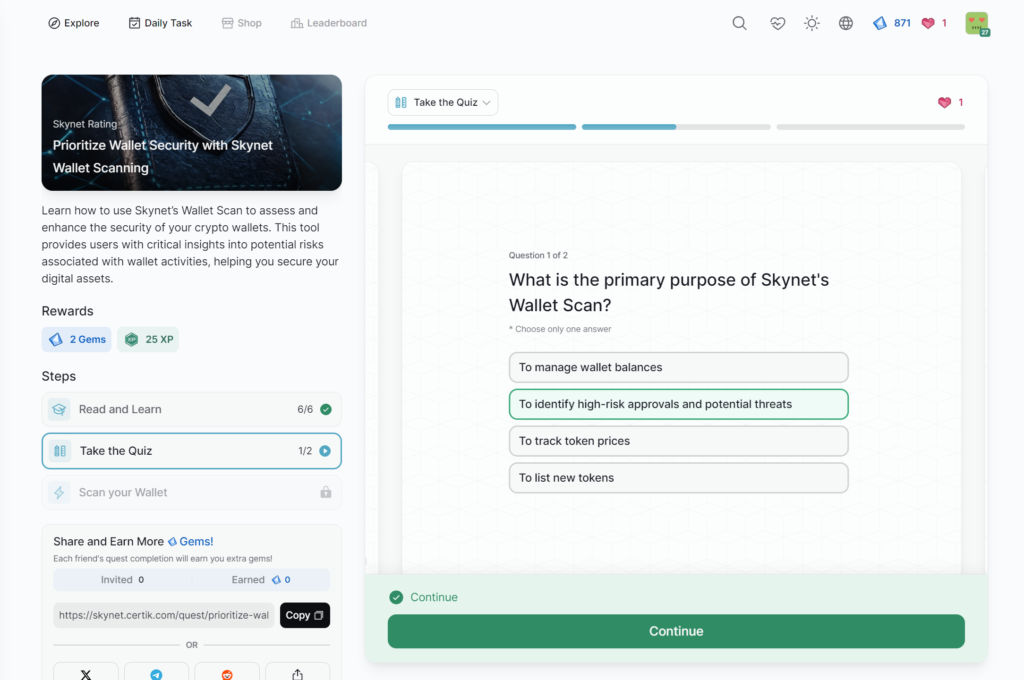
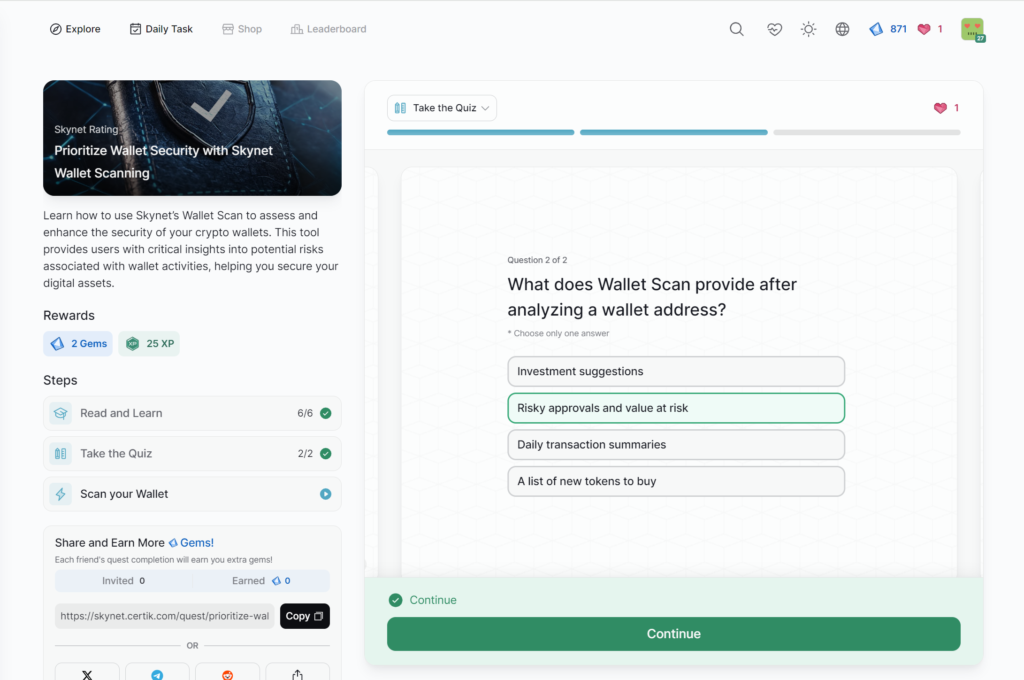
Empowering Your Web3 Journey with Advanced Security Tools
CertiK Ventures Announcement in Singapore
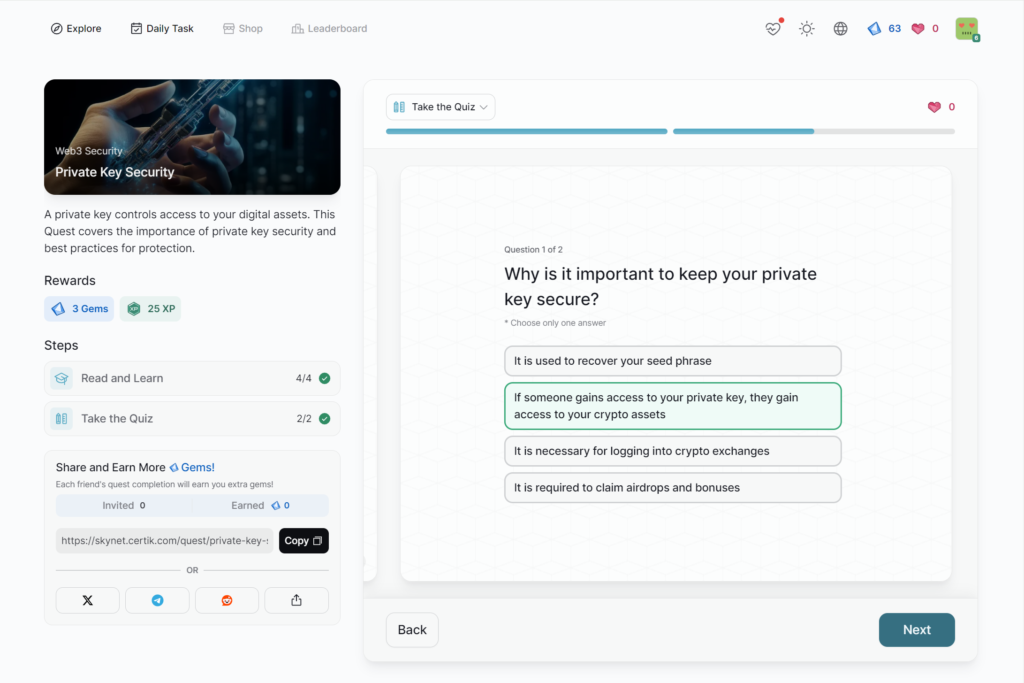
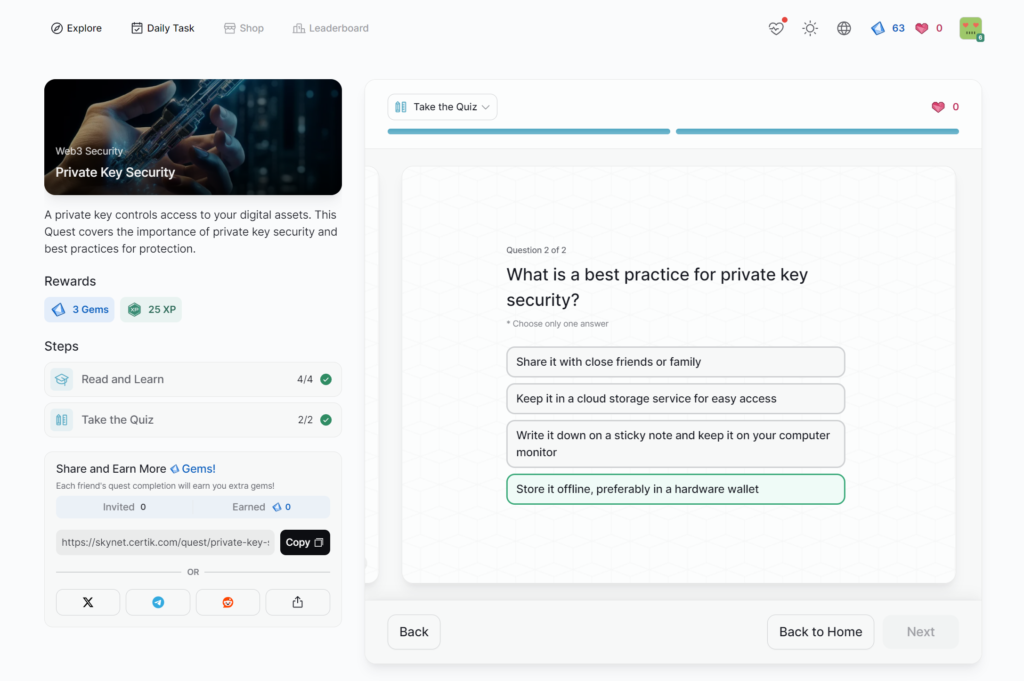
Private Key Security
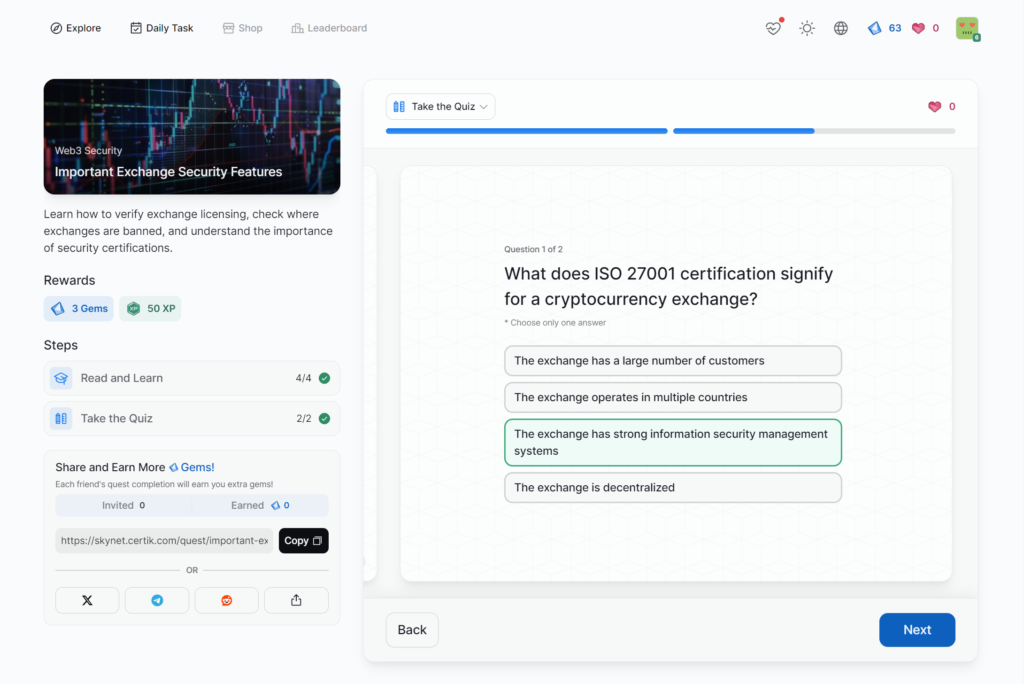
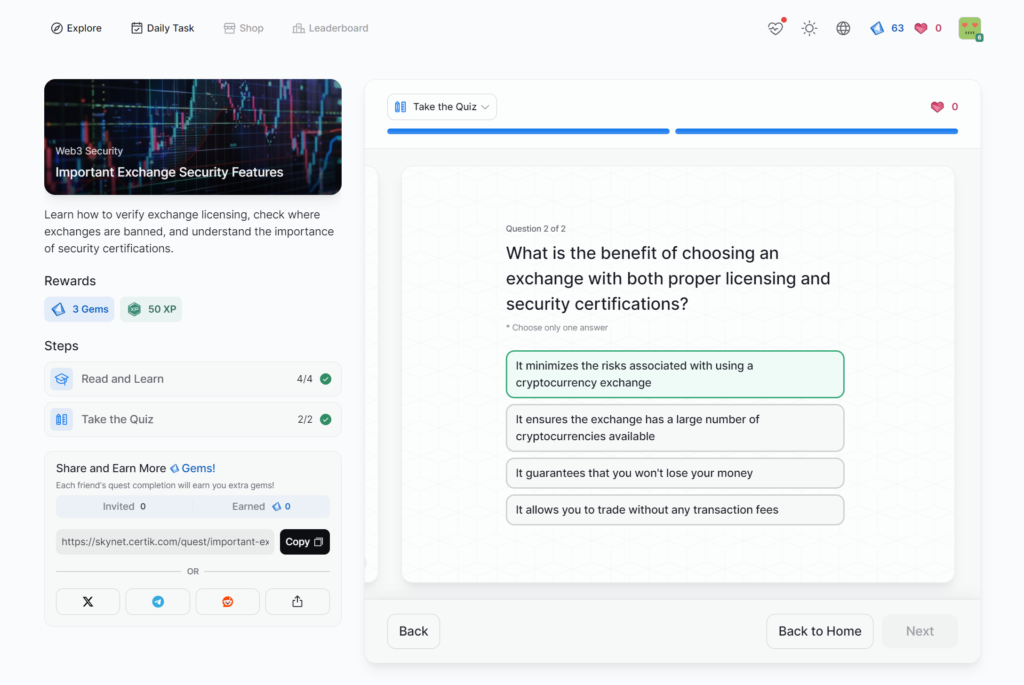
Important Exchange Security Features
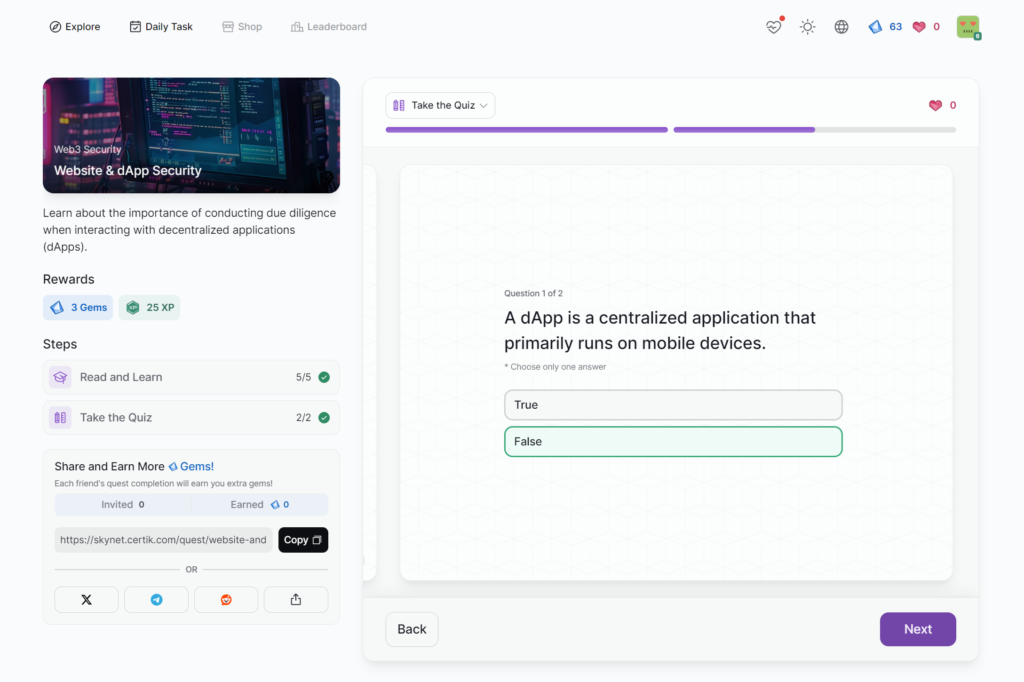
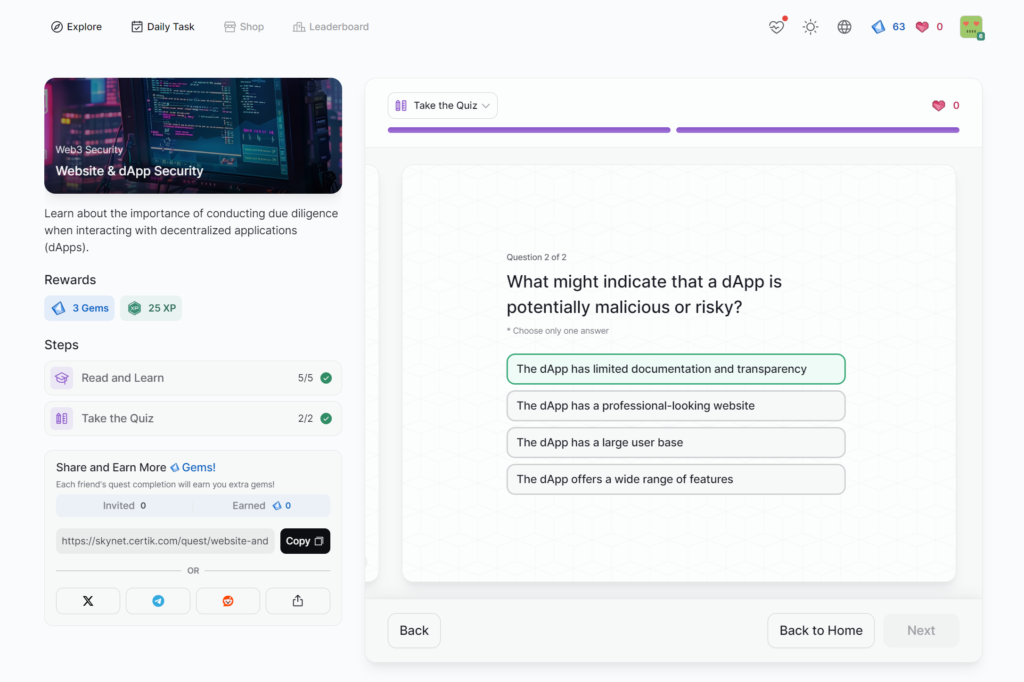
Website & dApp Security
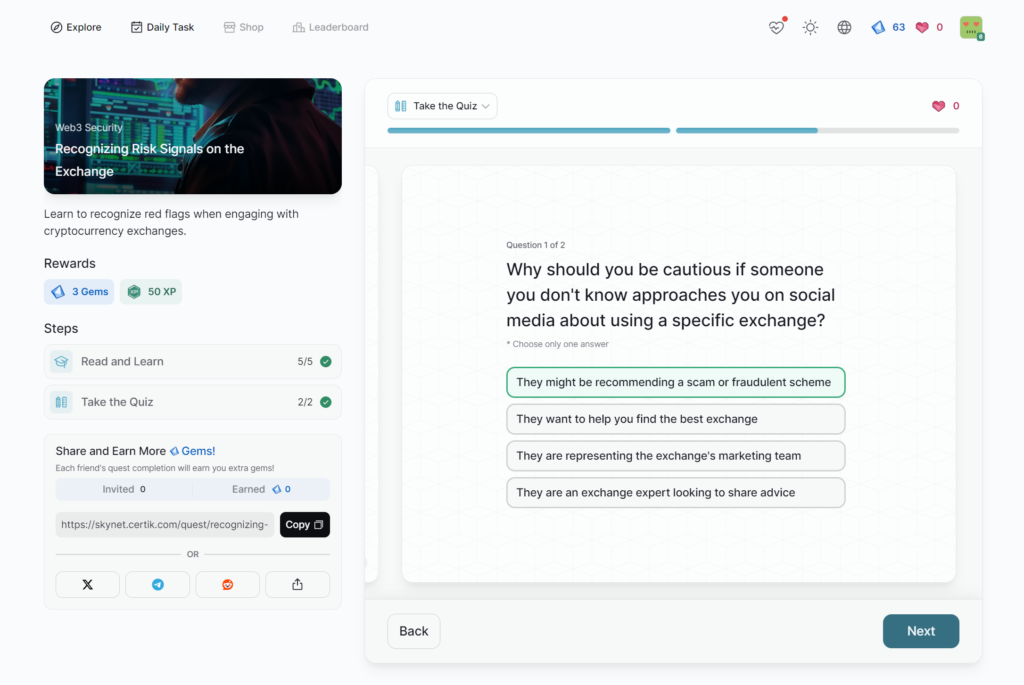
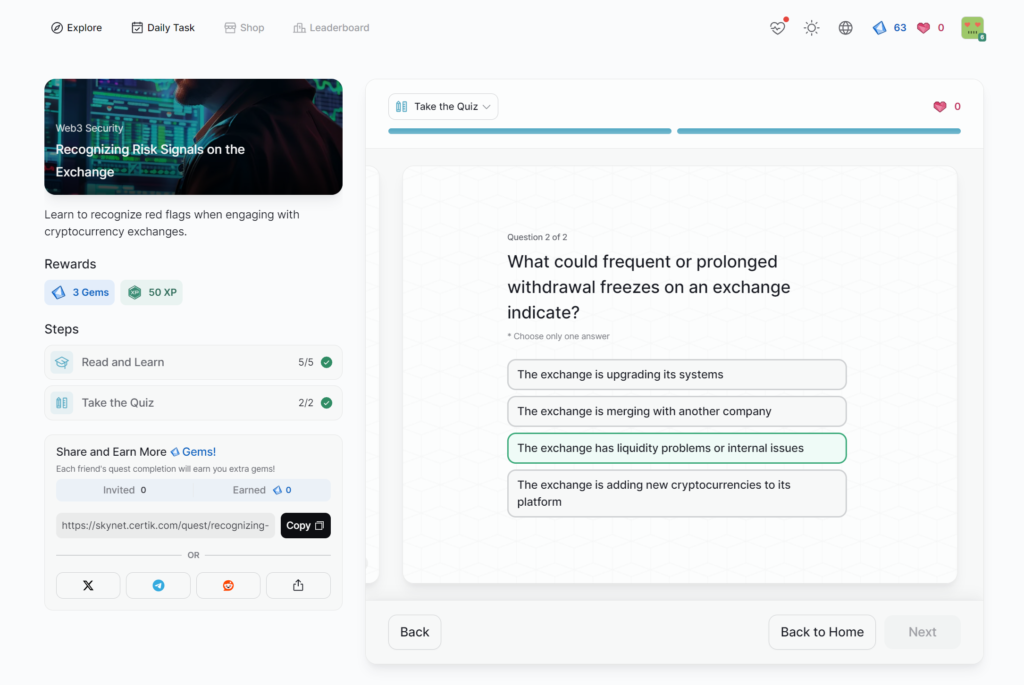
Recognizing Risk Signals on the Exchange
Proof of Reserve
Choosing a Secure Exchange
Introduction to Wallet Security
Losses Related to Private Key Compromises
Private Key Security: Seed Phrases
Identifying and Avoiding Phishing Scams in X Replies
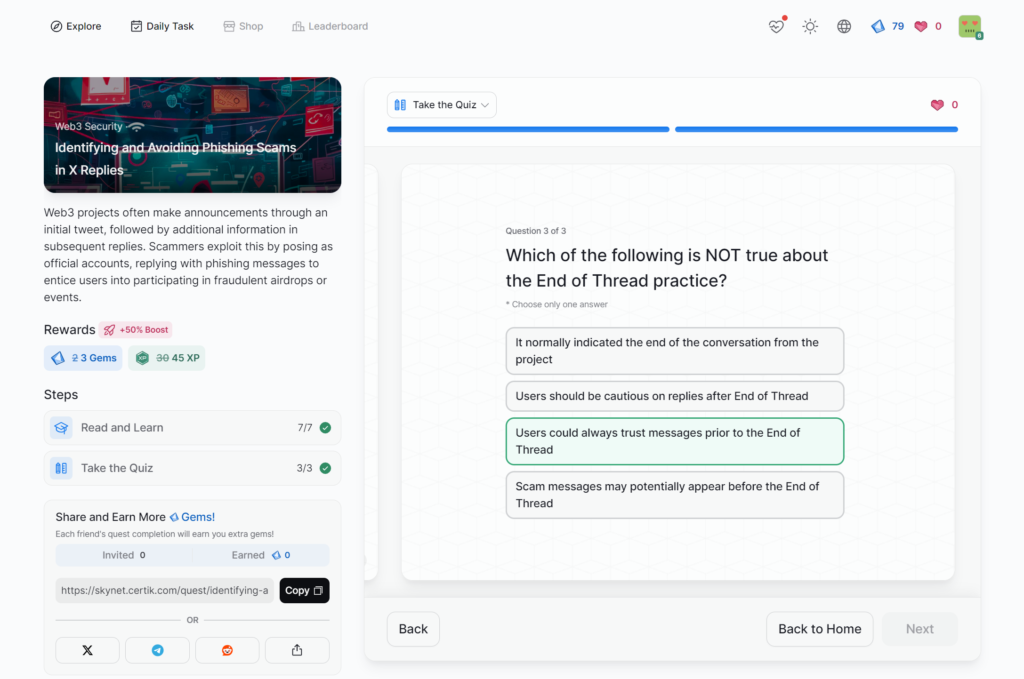
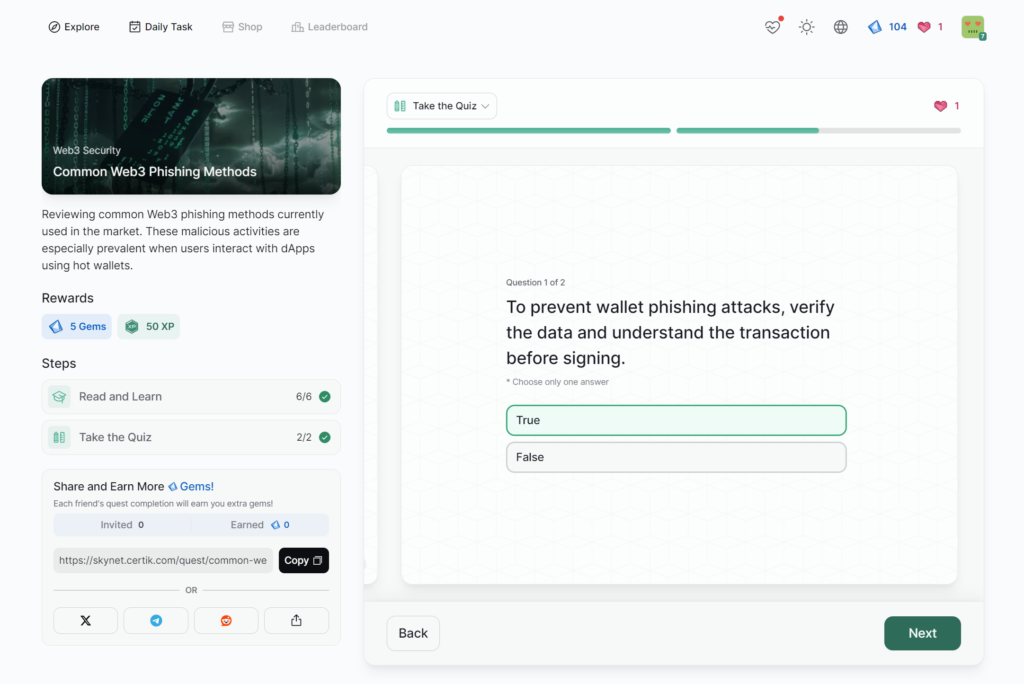
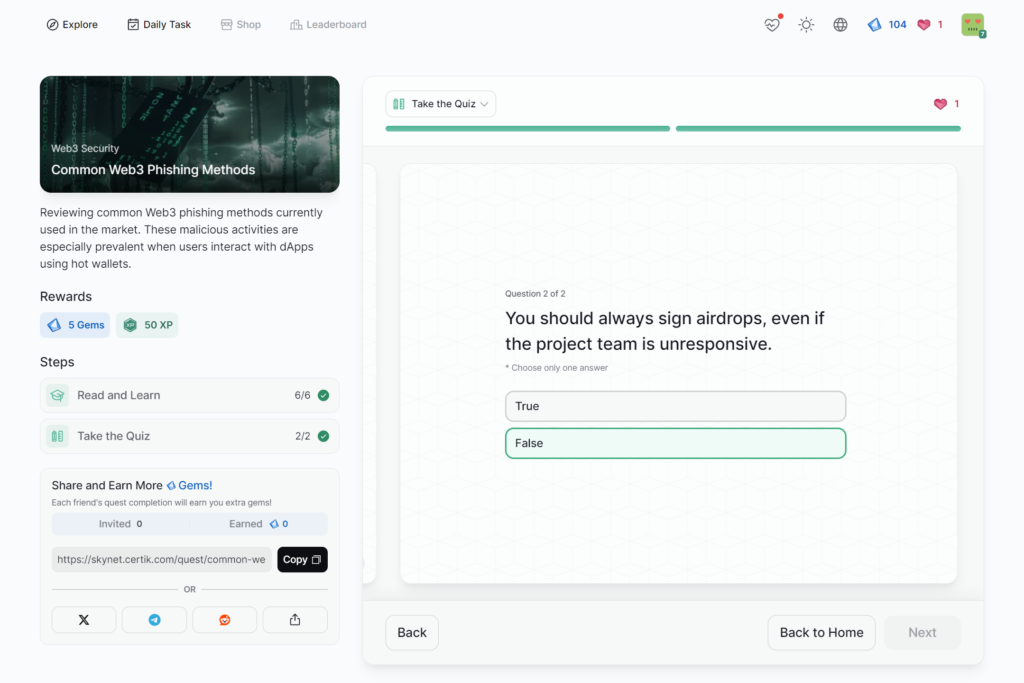
Common Web3 Phishing Methods
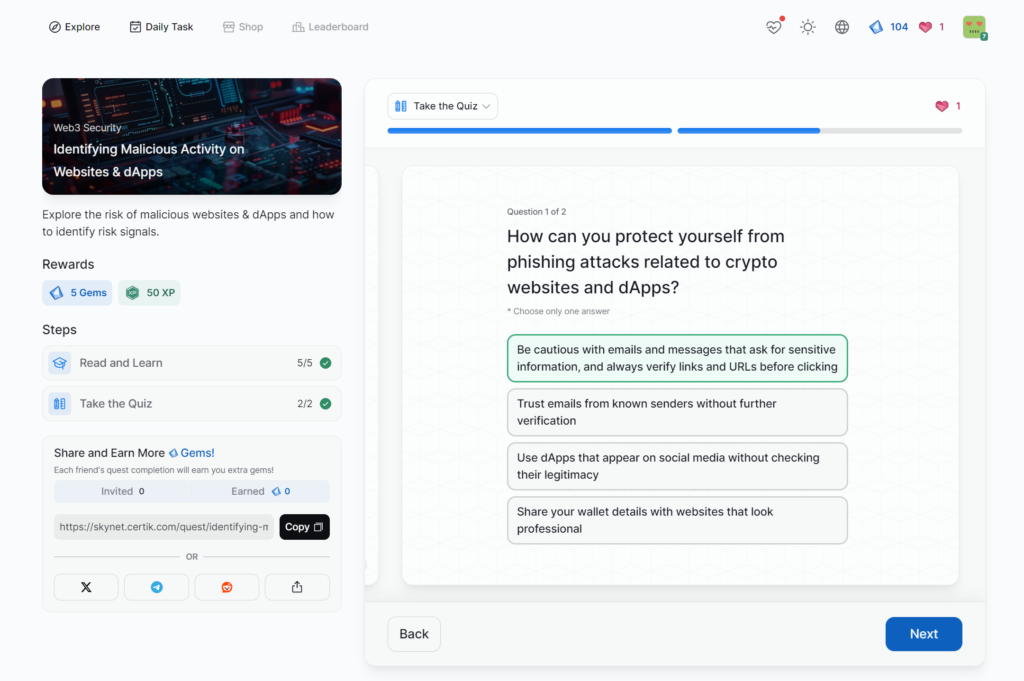
Identifying Malicious Activity on Websites & dApps
Introduction to User Security
Stay Vigilant on Browser Plugins
Best Practices for Wallet Security
Importance of Bug Bounty Programs in Web3
Intro to Crypto Drainers
Intro to Airdrop Scams
Evaluating Cryptocurrency News Sources
Hackers Infiltrating Crypto Job Boards
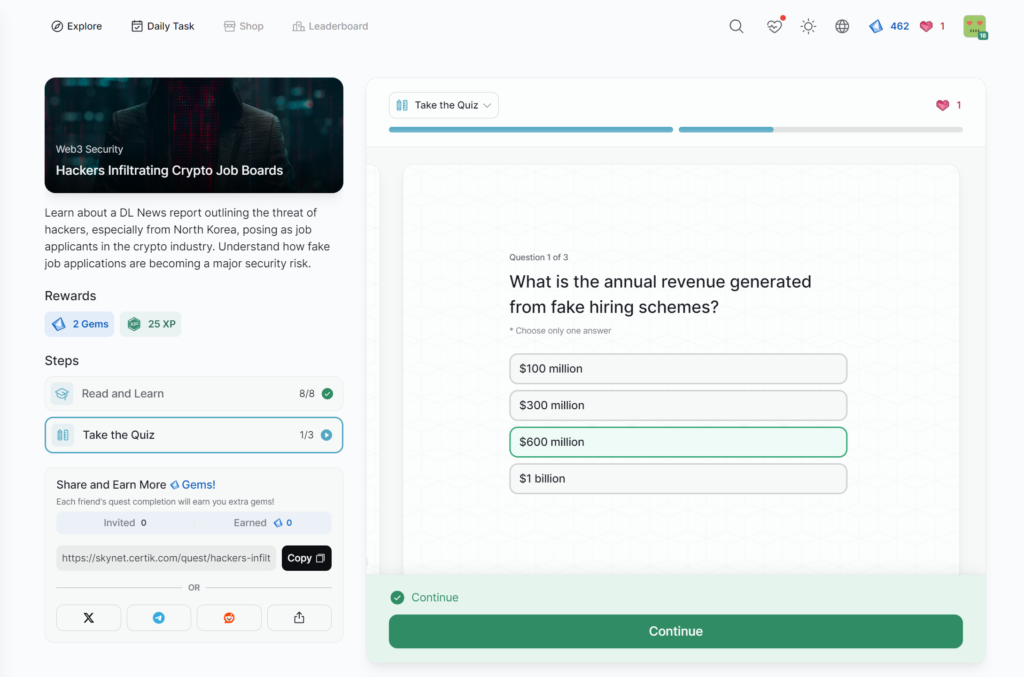
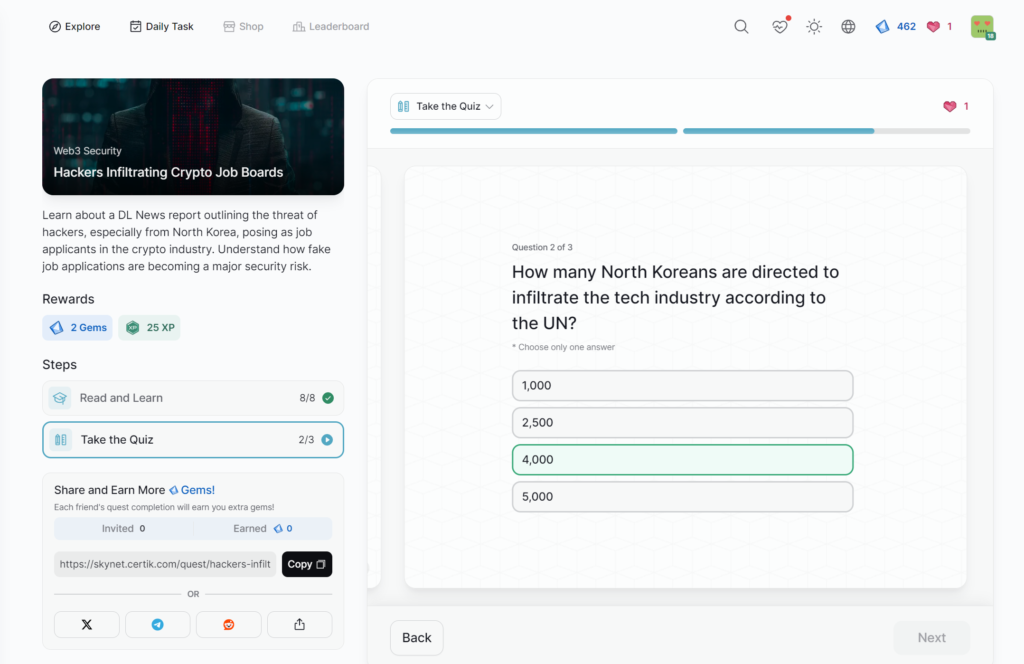
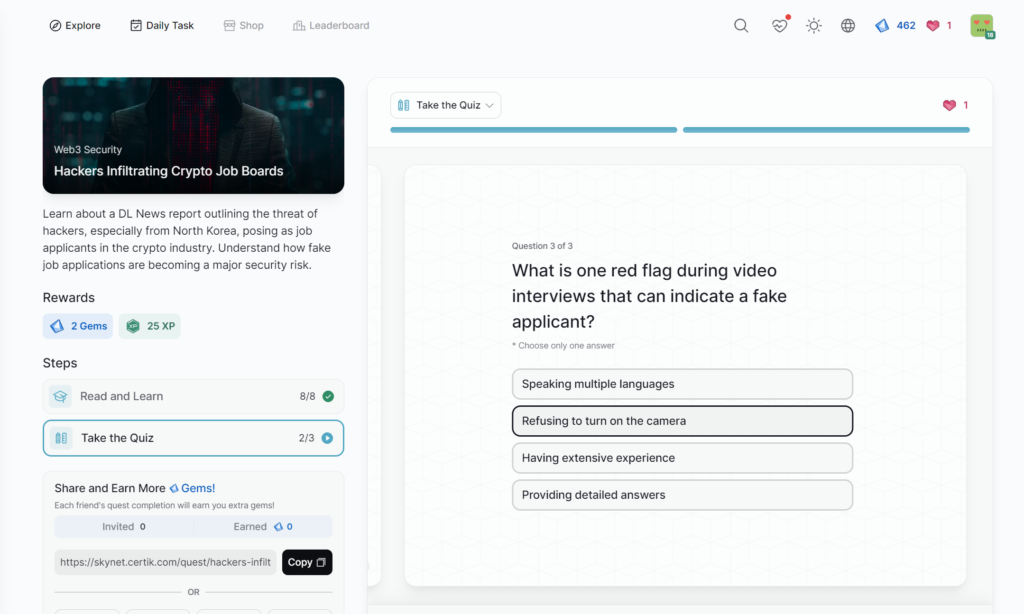
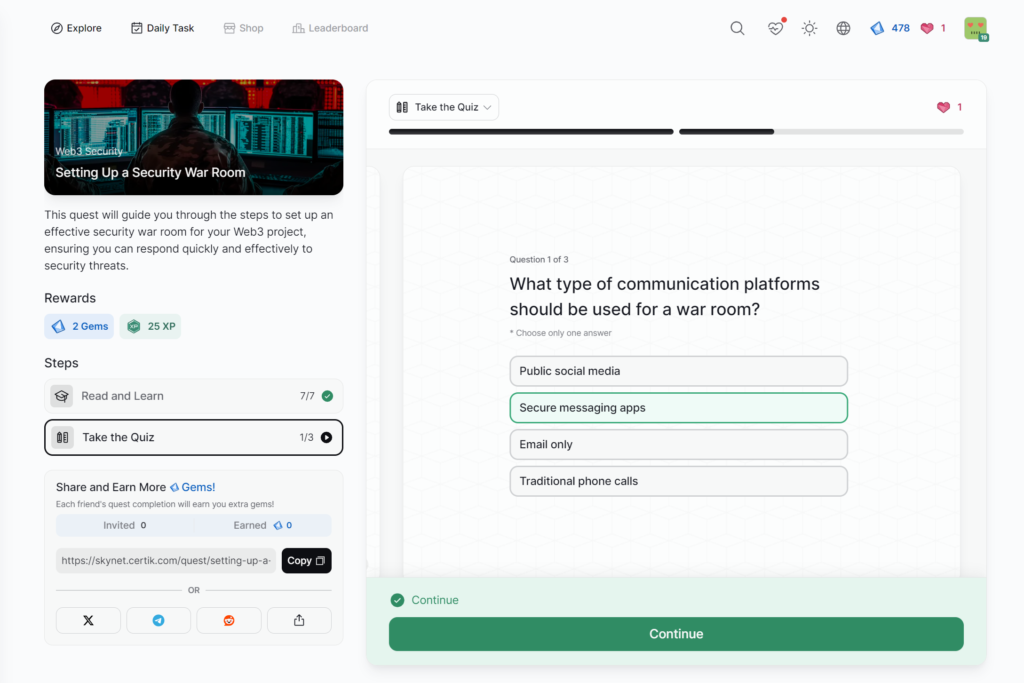
Setting Up a Security War Room
What Is a Keylogger?
Understanding and Preventing Sybil Attacks
Cold Wallets
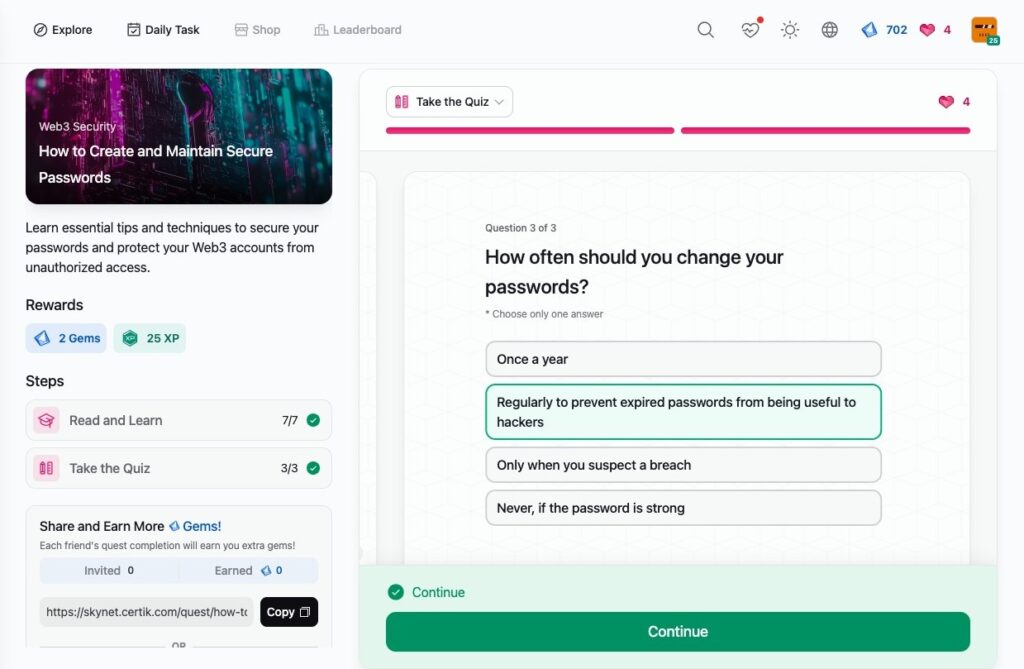
How to Create and Maintain Secure Passwords
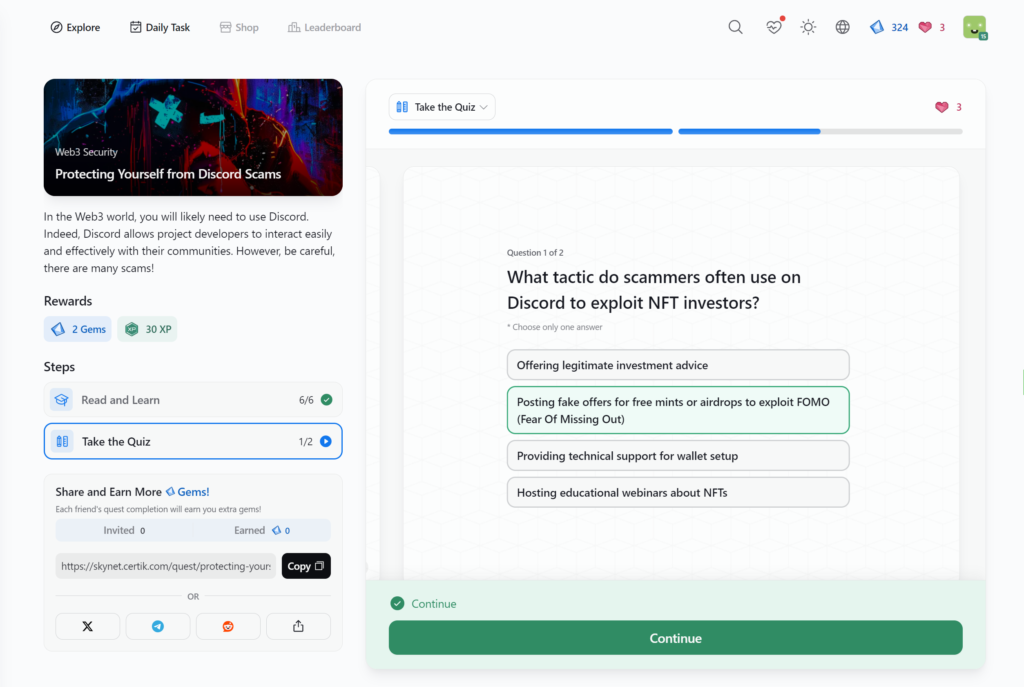
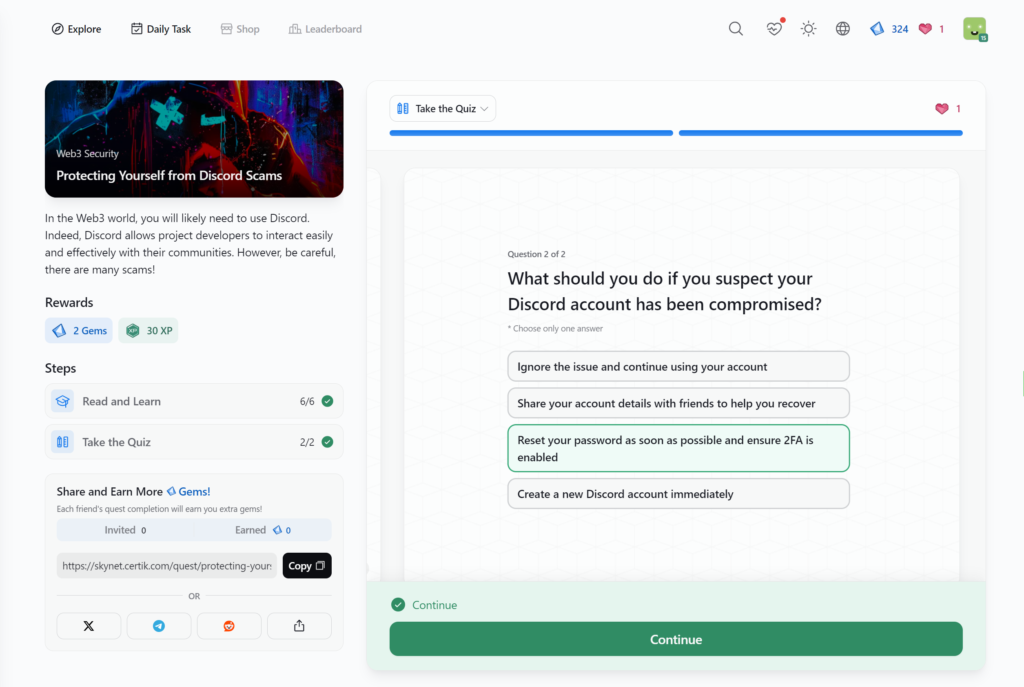
Protecting Yourself from Discord Scams
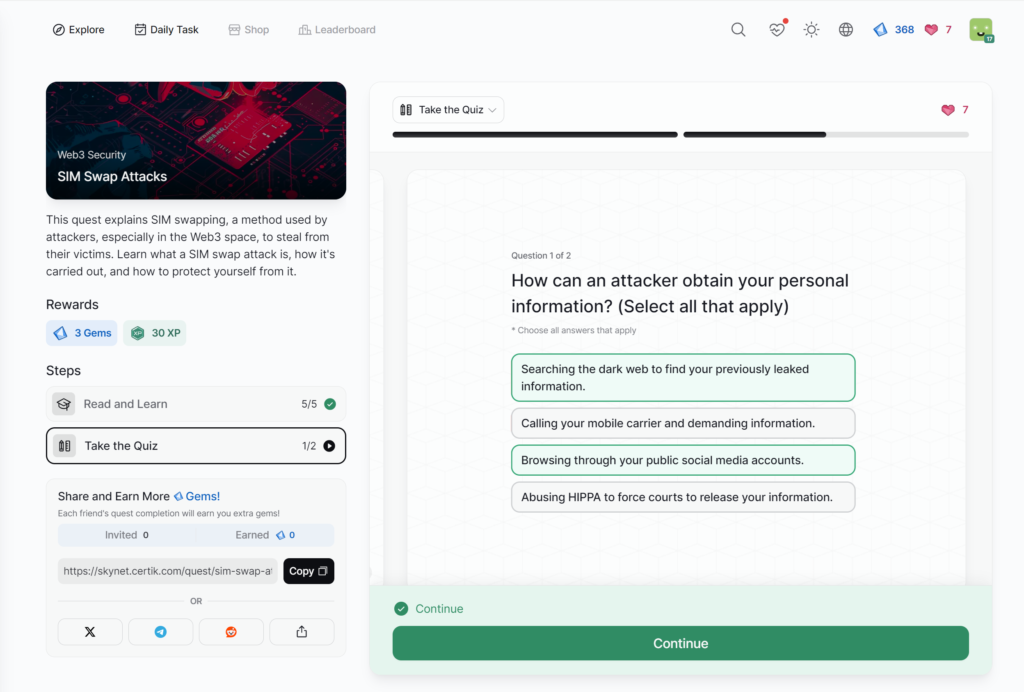
SIM Swap Attacks
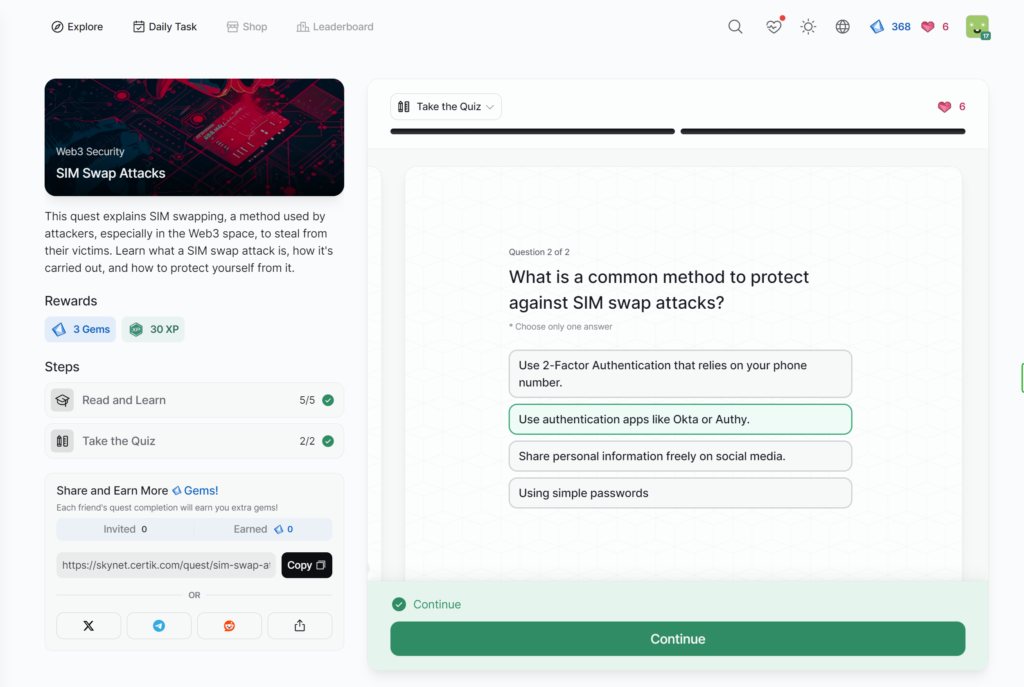
Understanding and Mitigating 51% Attacks
Protecting Your PostgreSQL Database from Cryptojacking
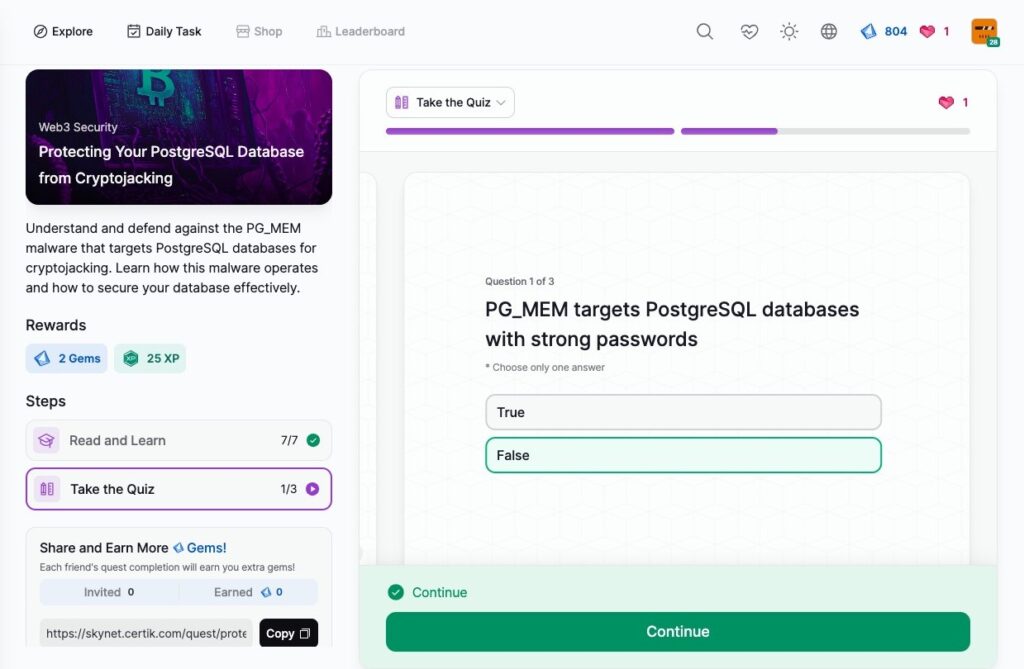
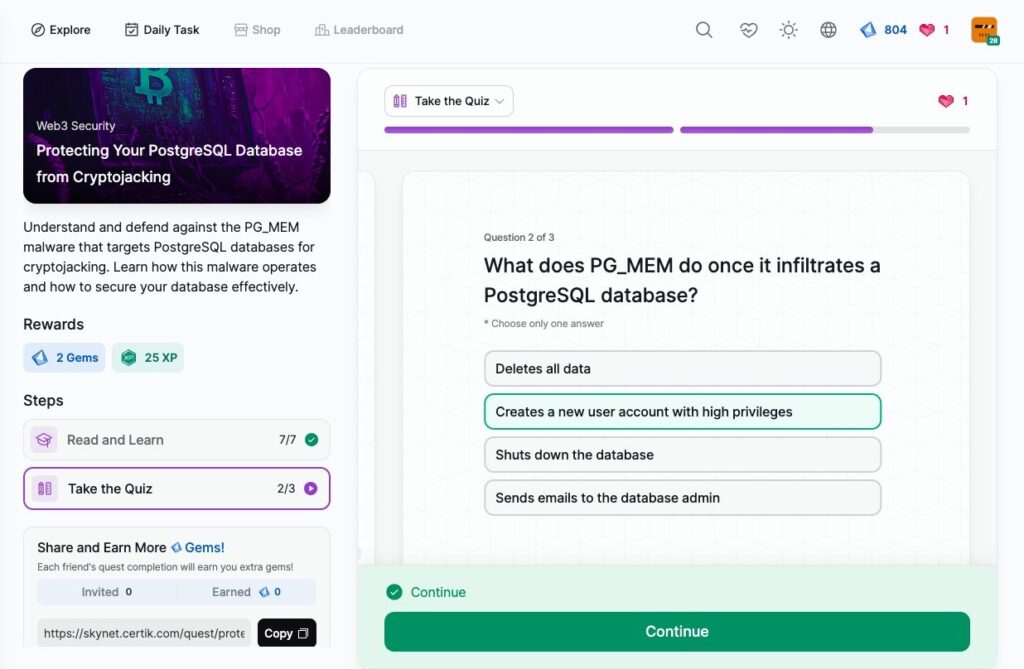
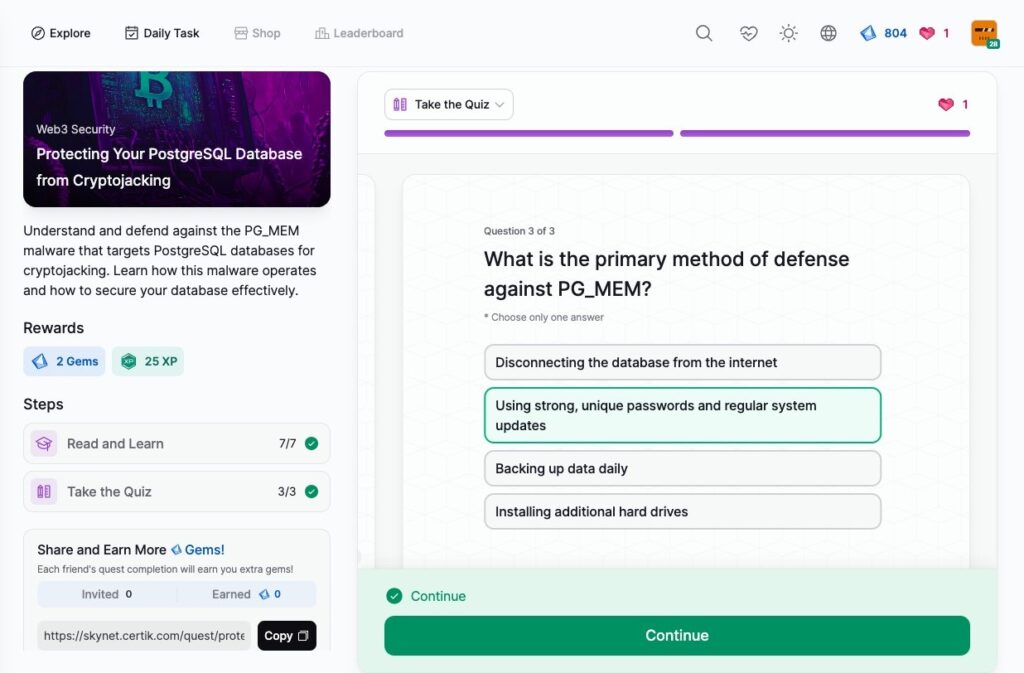
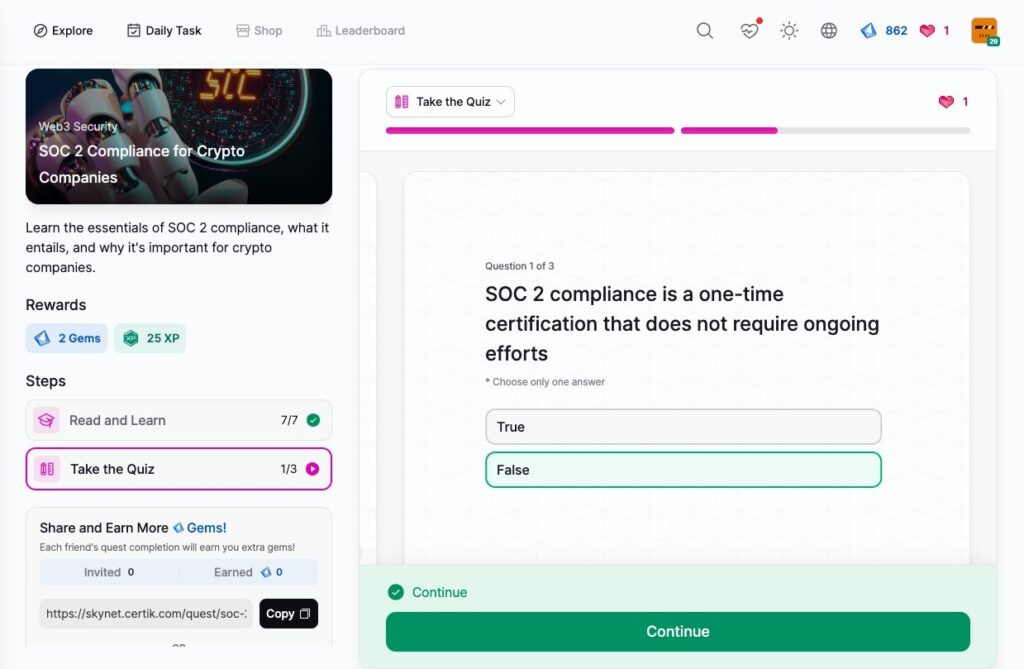
SOC 2 Compliance for Crypto Companies
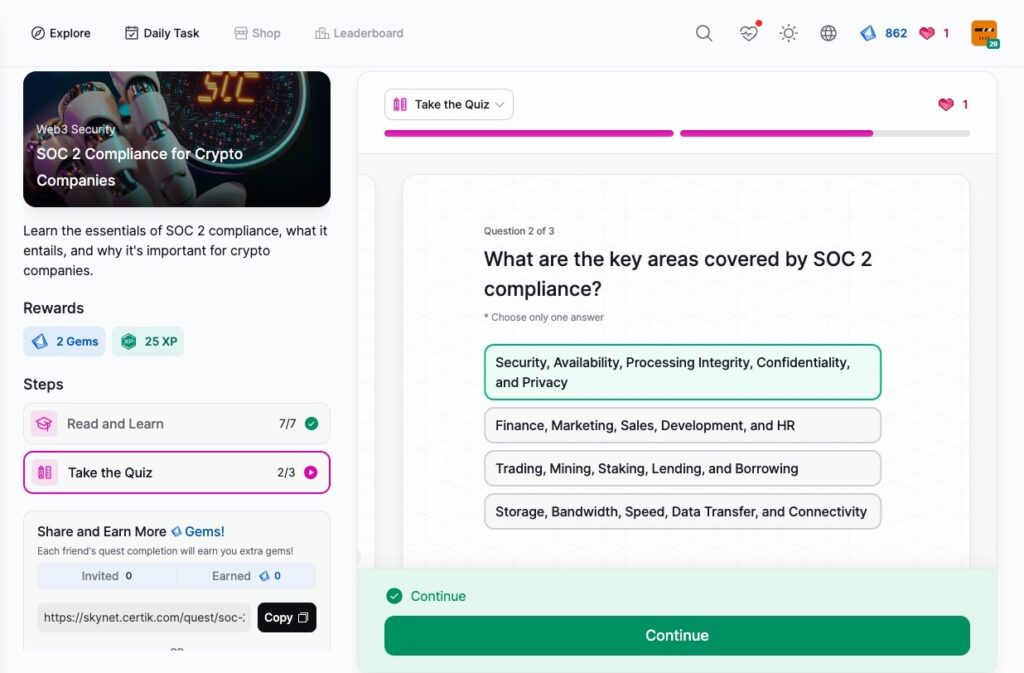
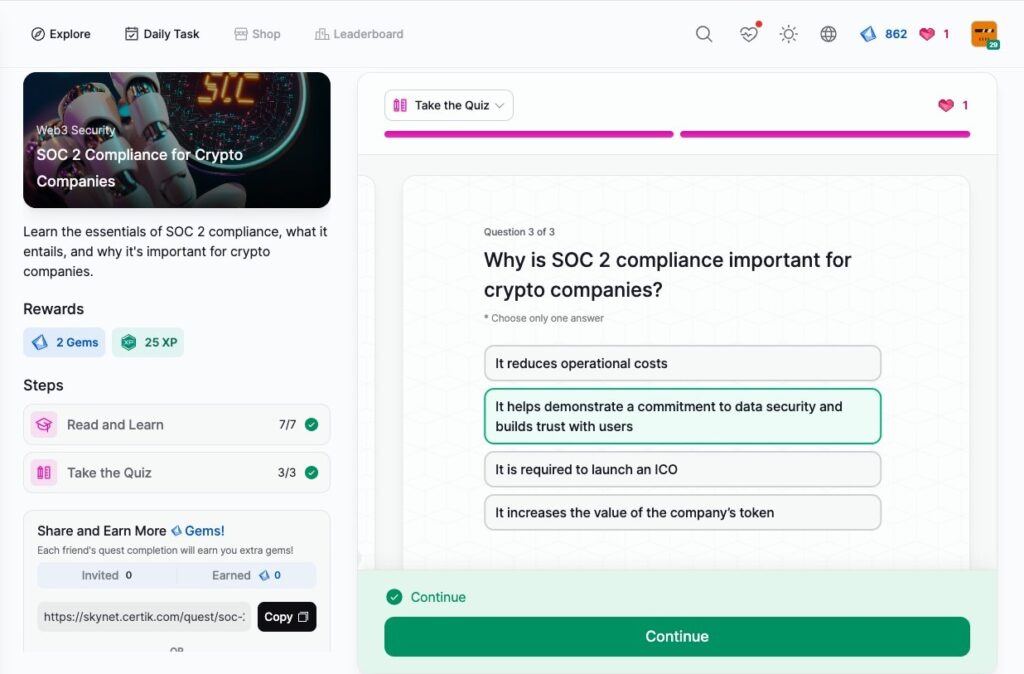
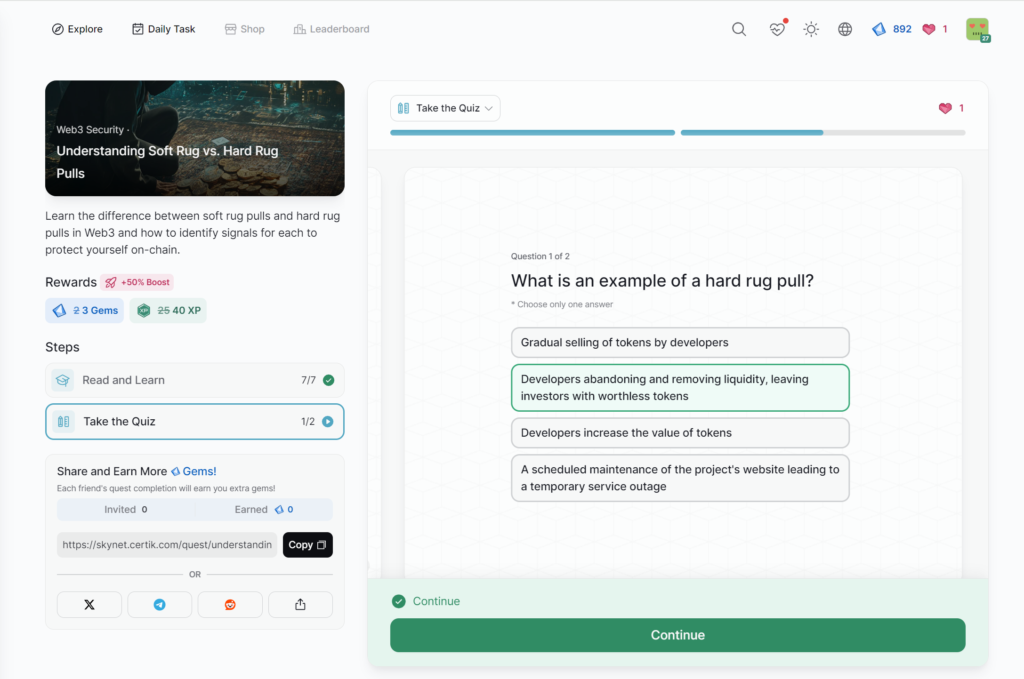
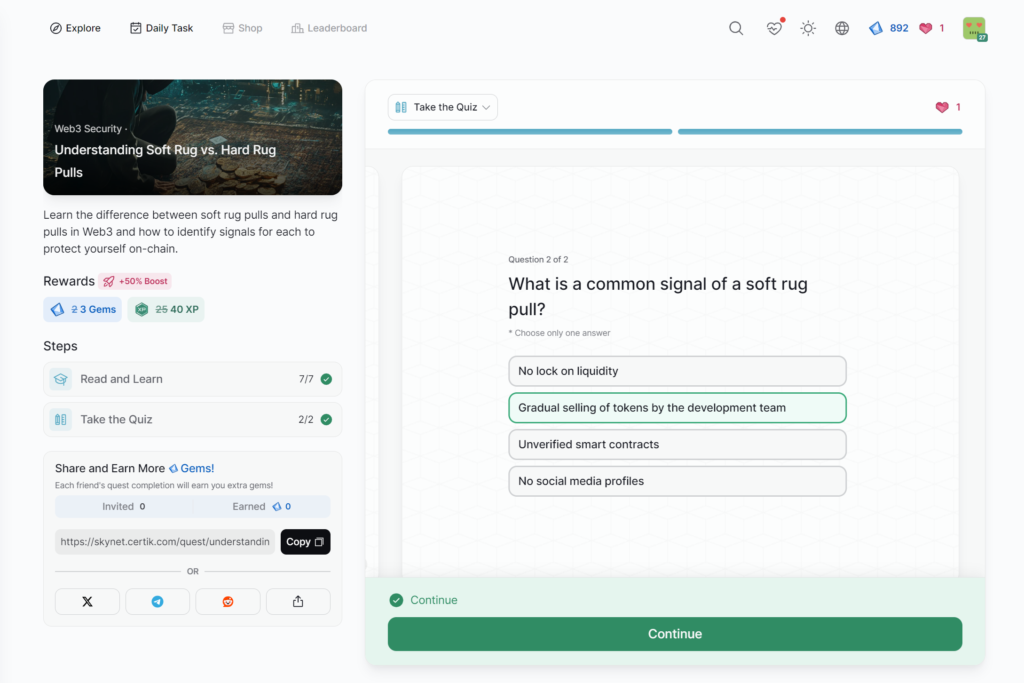
Understanding Soft Rug vs. Hard Rug Pulls
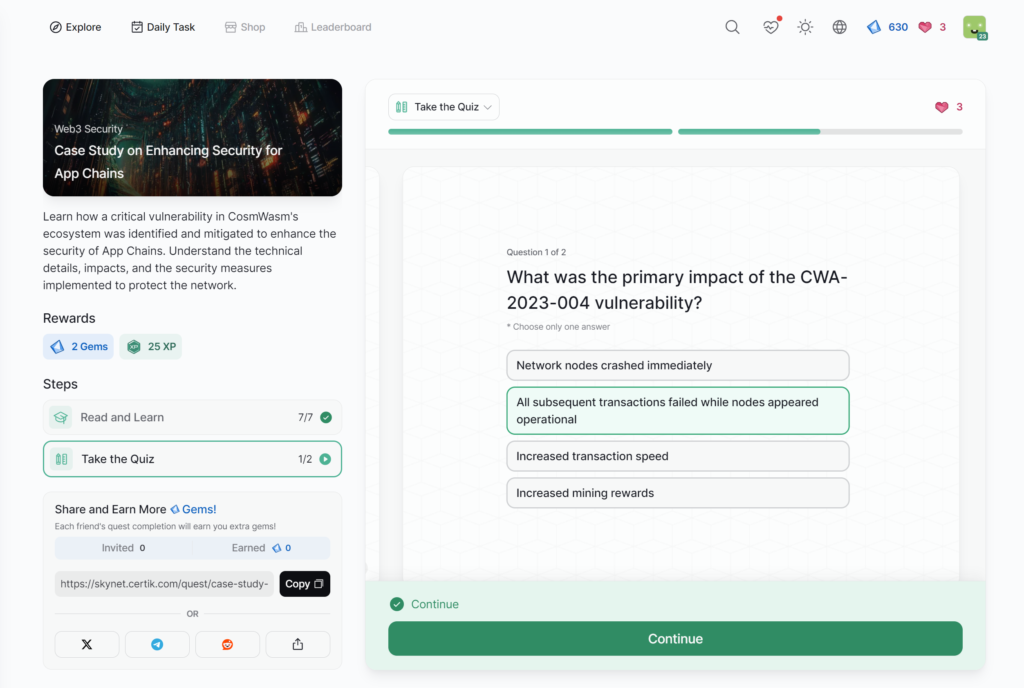
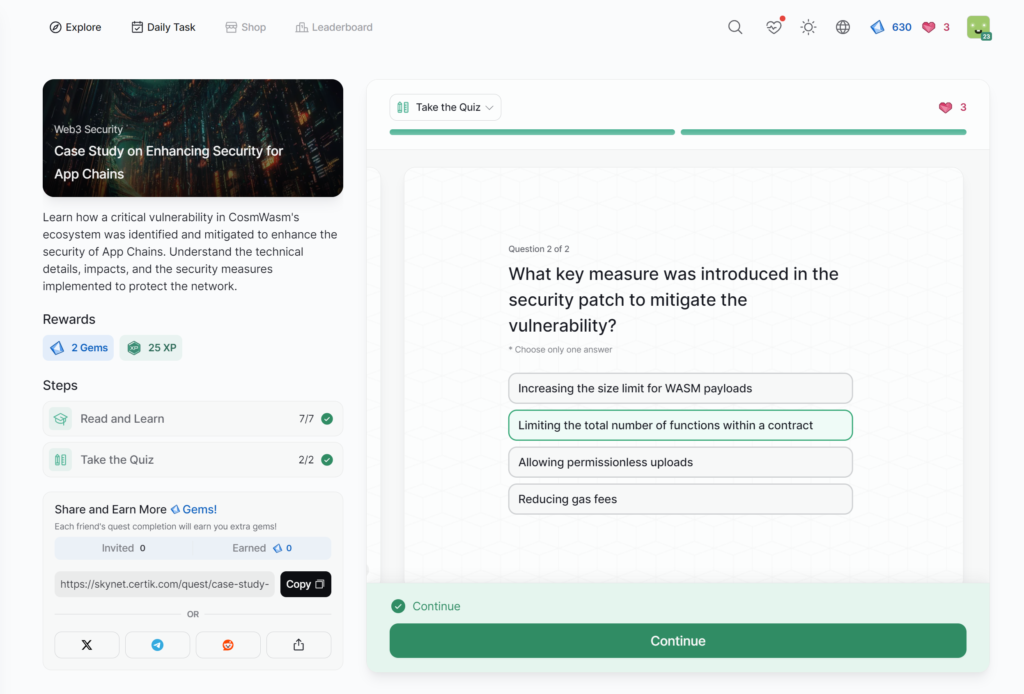
Case Study on Enhancing Security for App Chains
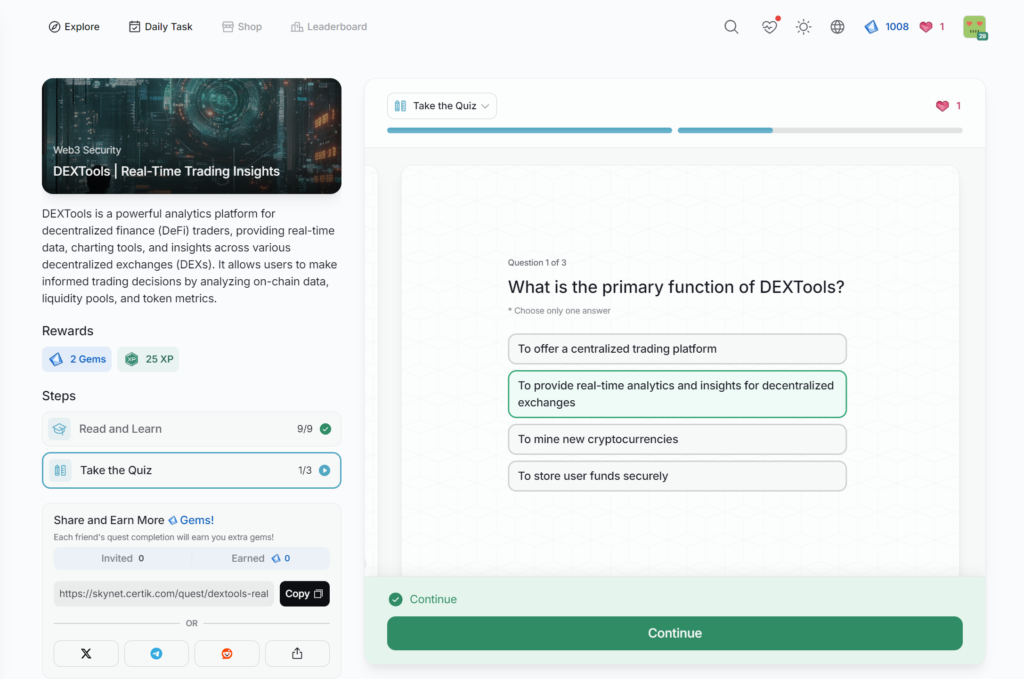
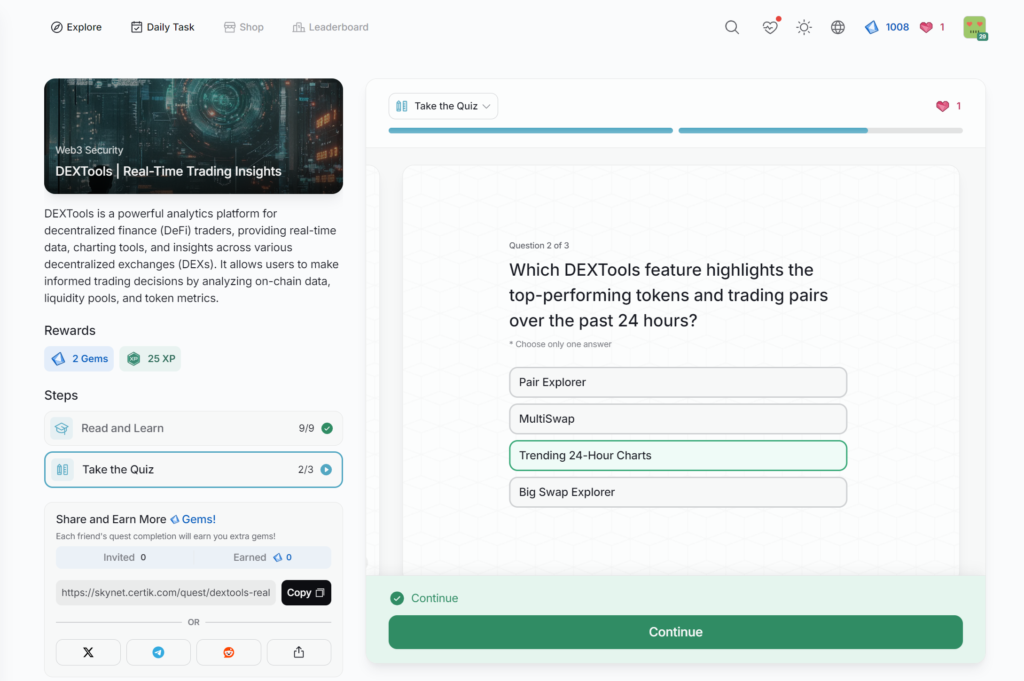
DEXTools | Real-Time Trading Insights
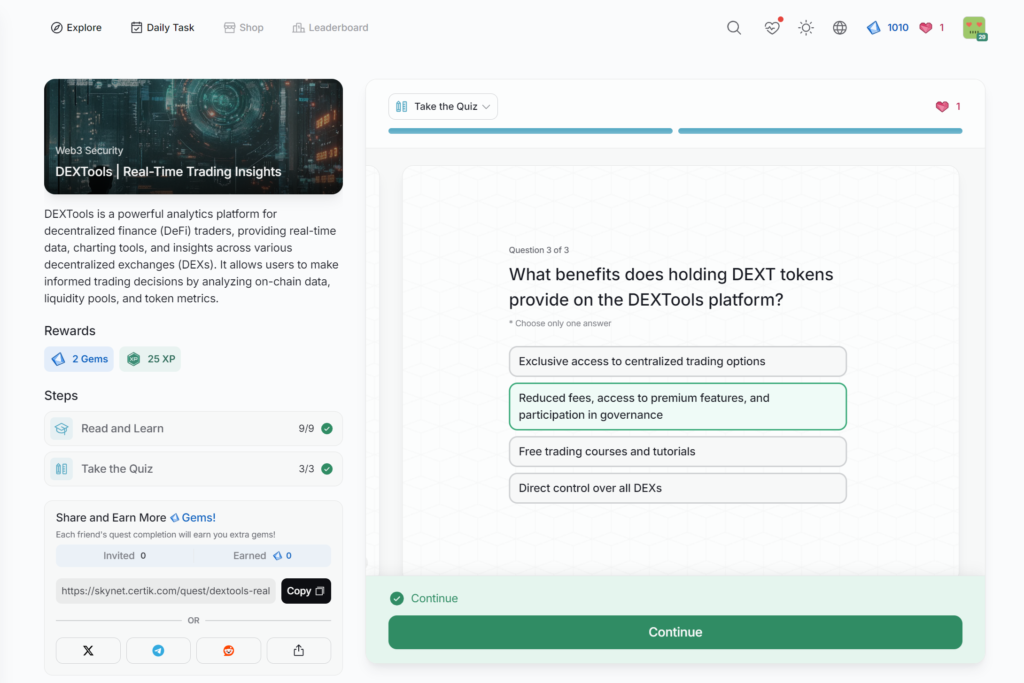
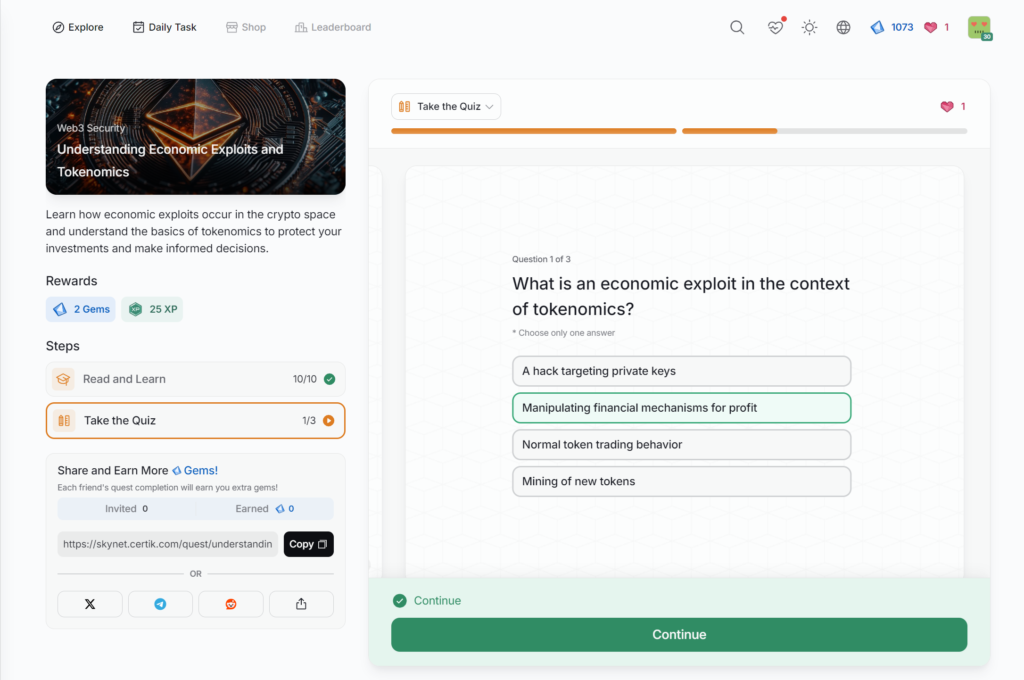
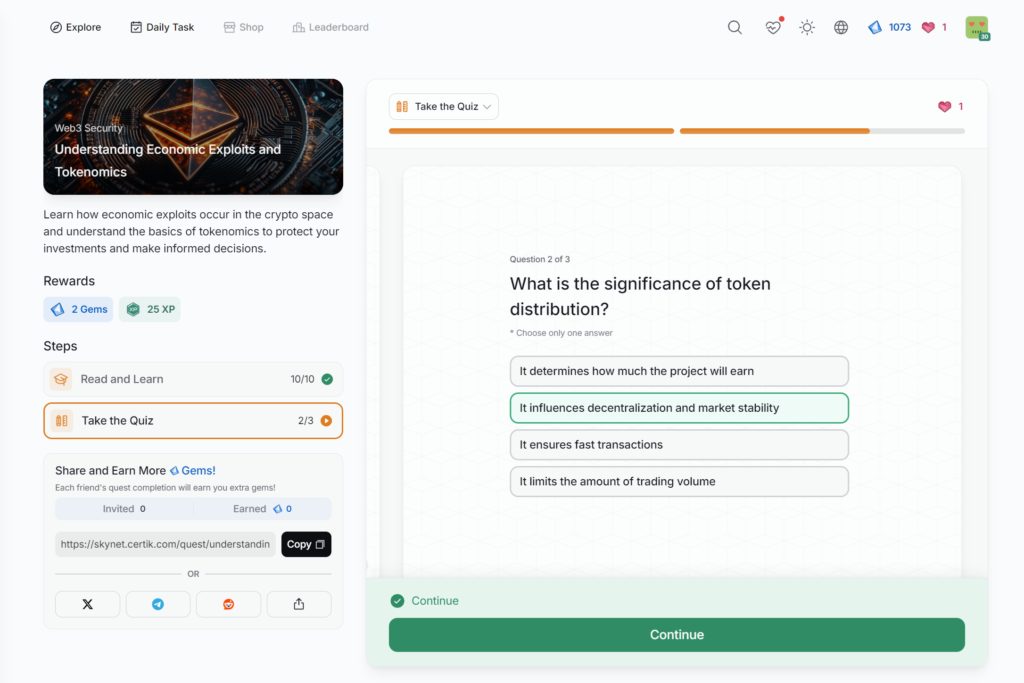
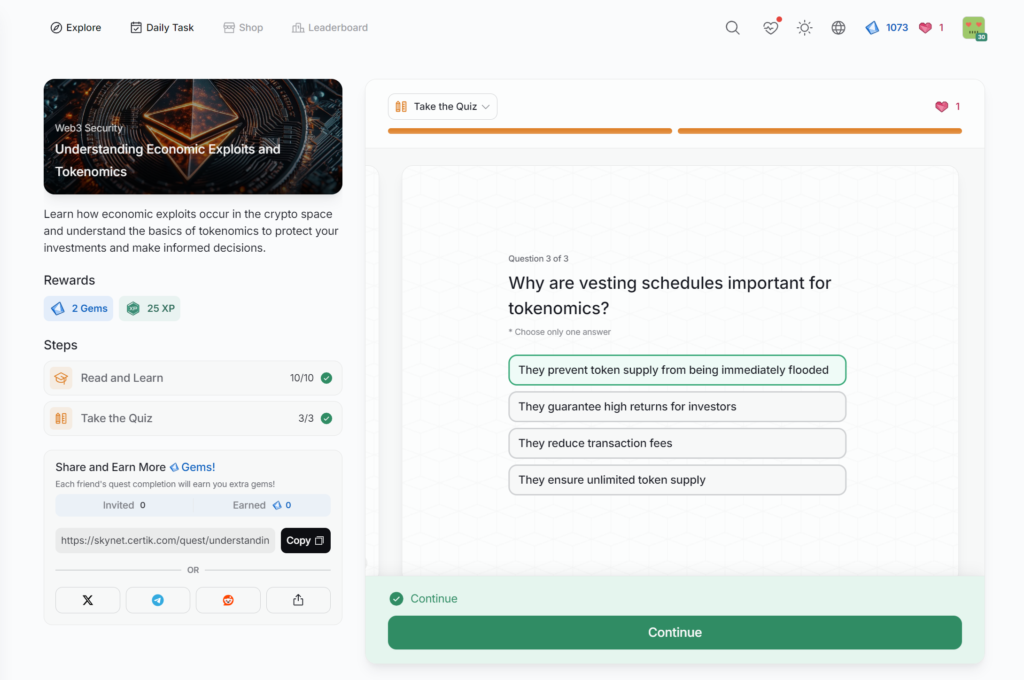
Understanding Economic Exploits and Tokenomics
Intro to AML and its Role in Crypto
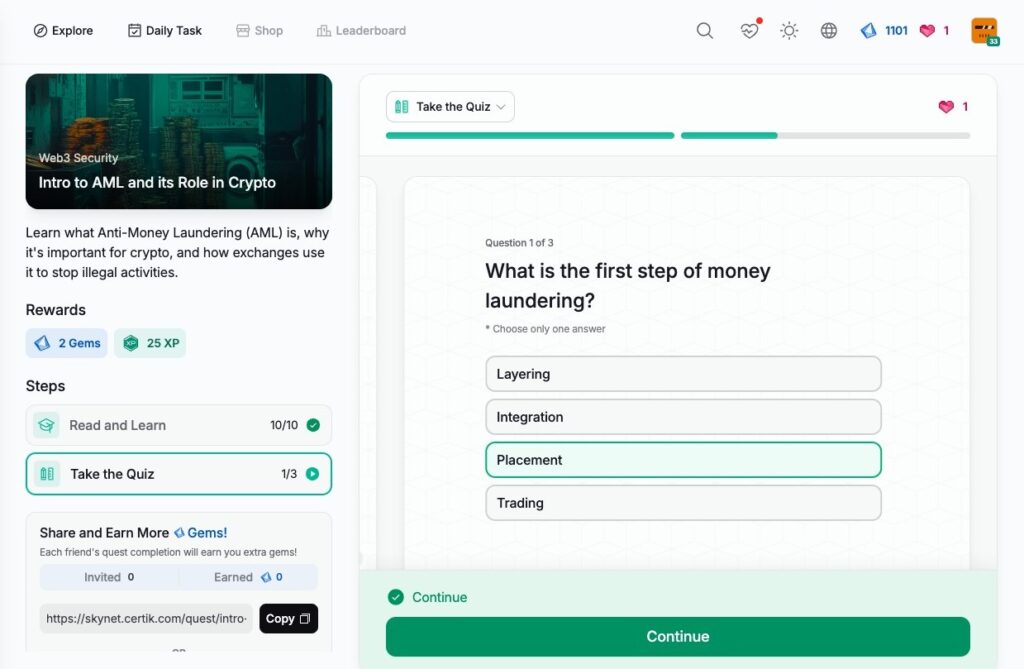
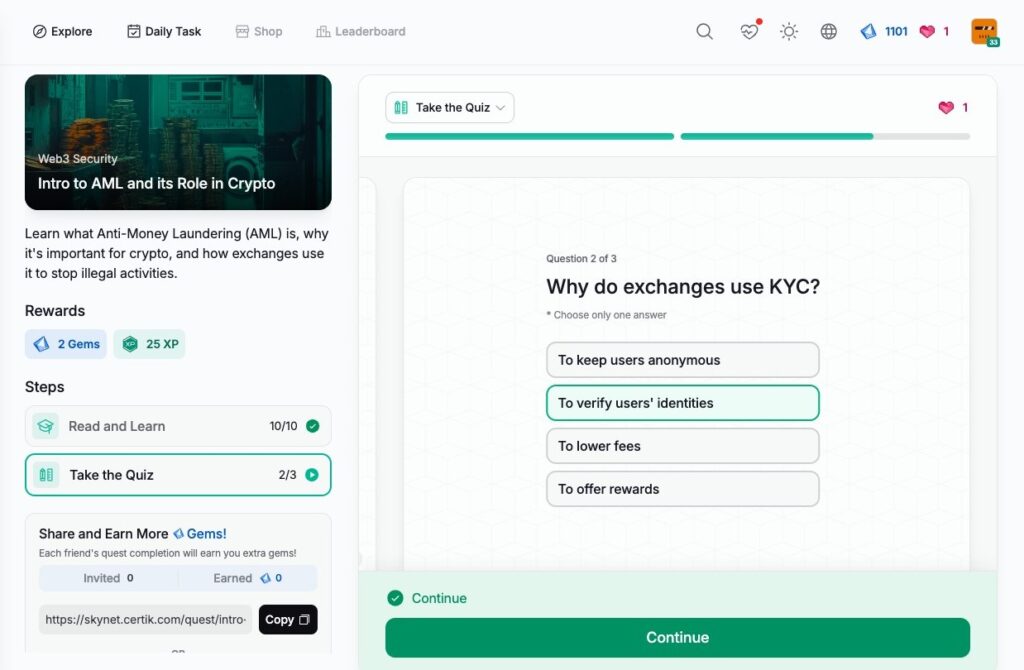
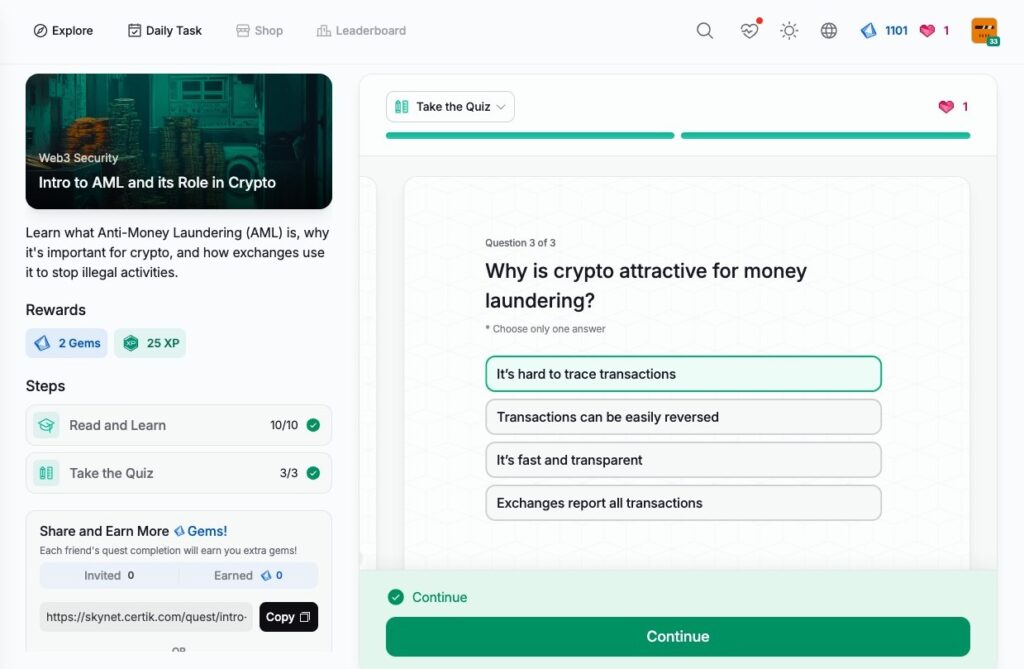
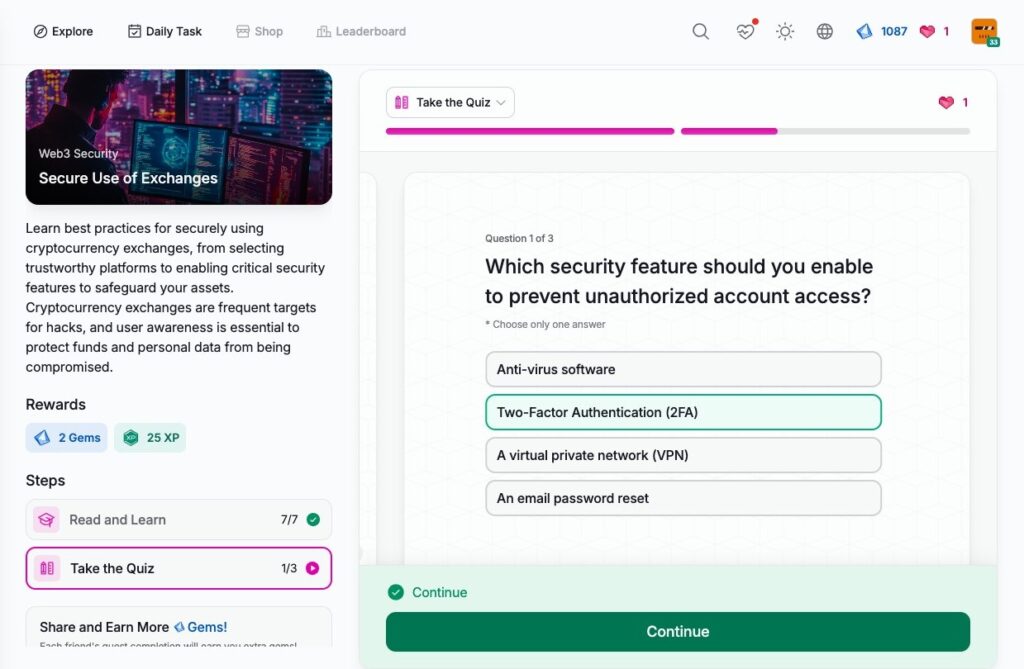
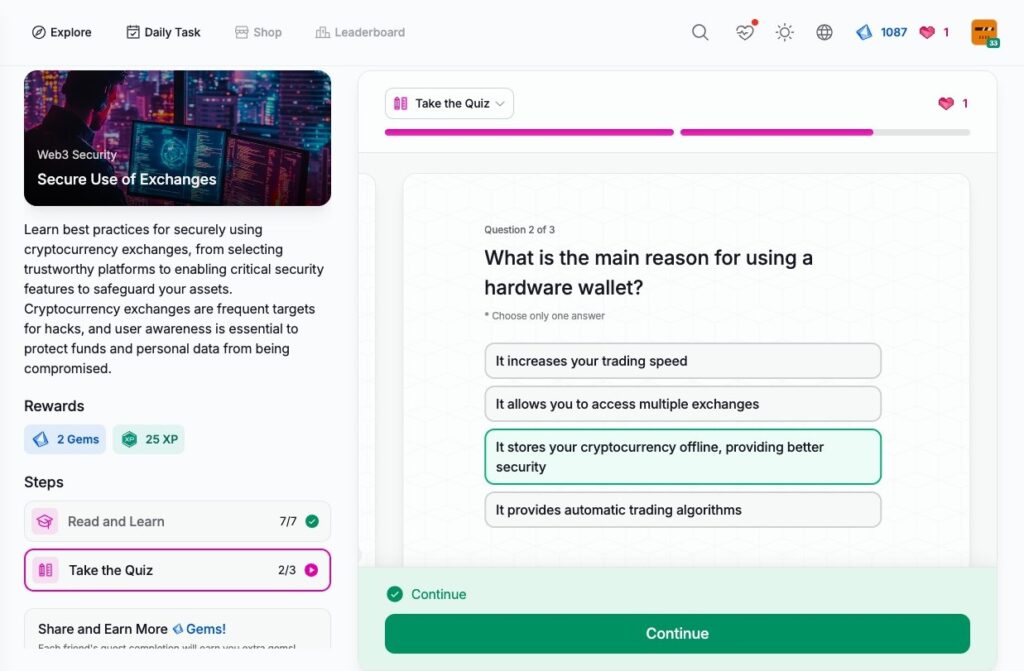
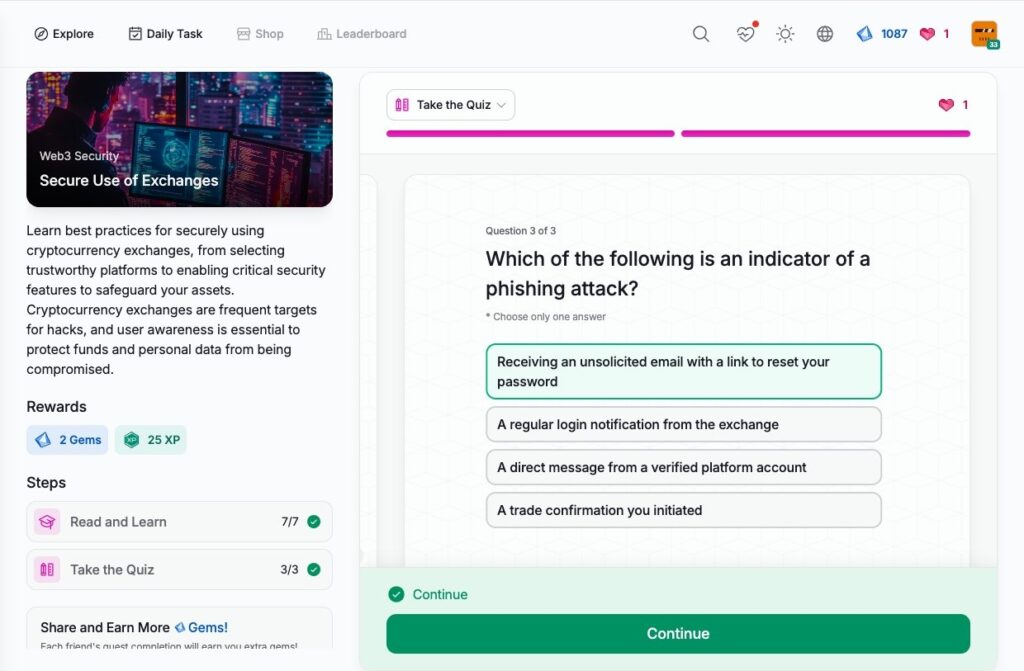
Secure Use of Exchanges
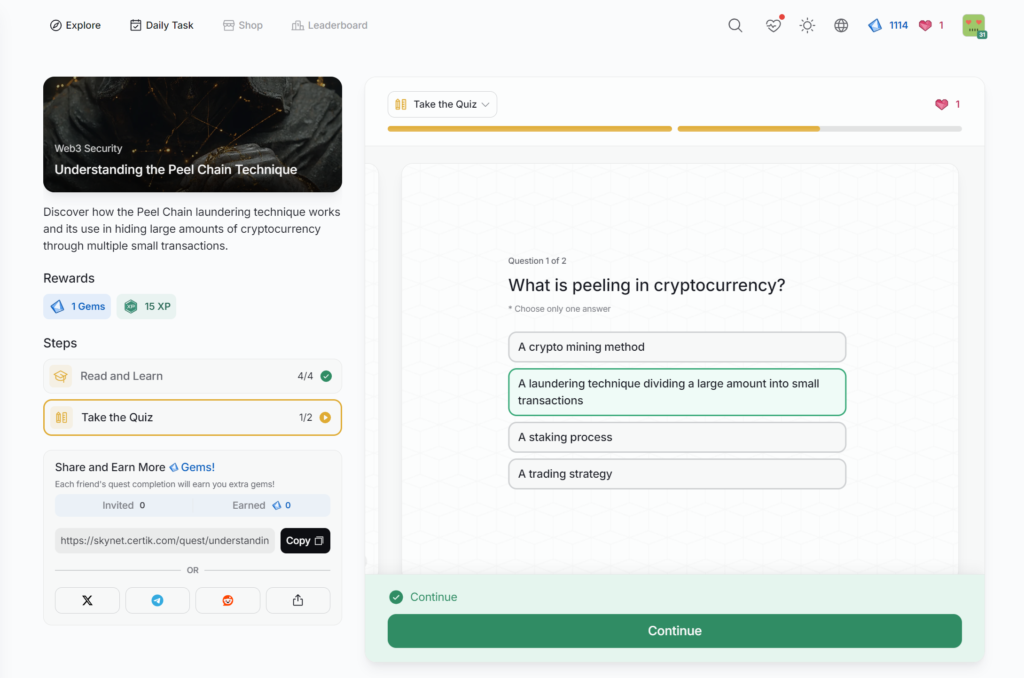
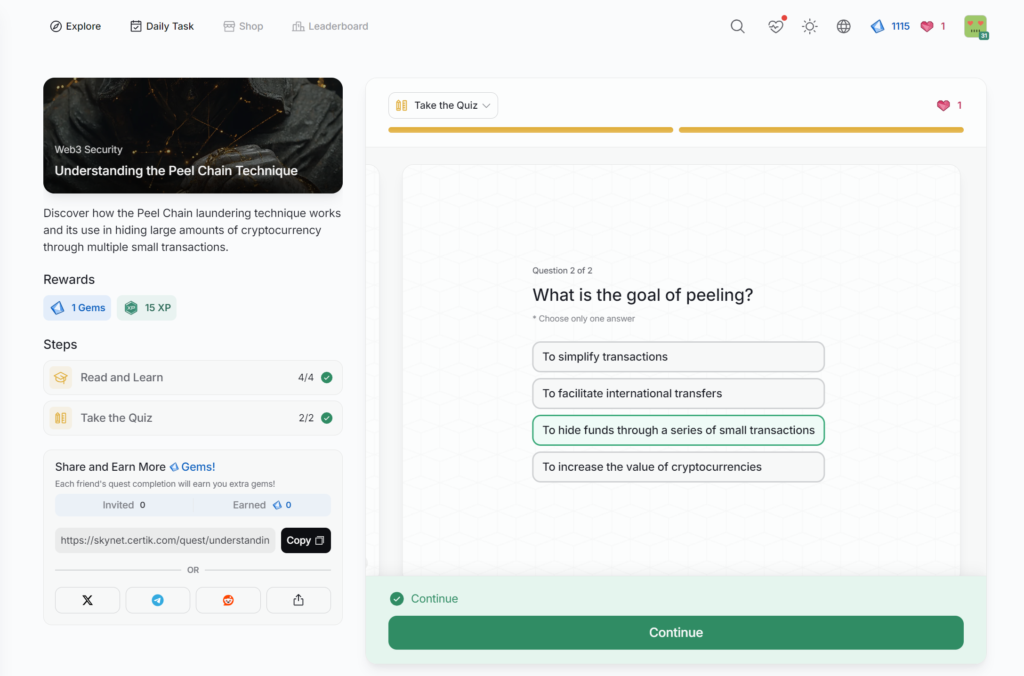
Understanding the Peel Chain Technique
Navigating NFT Security and Avoiding Scams
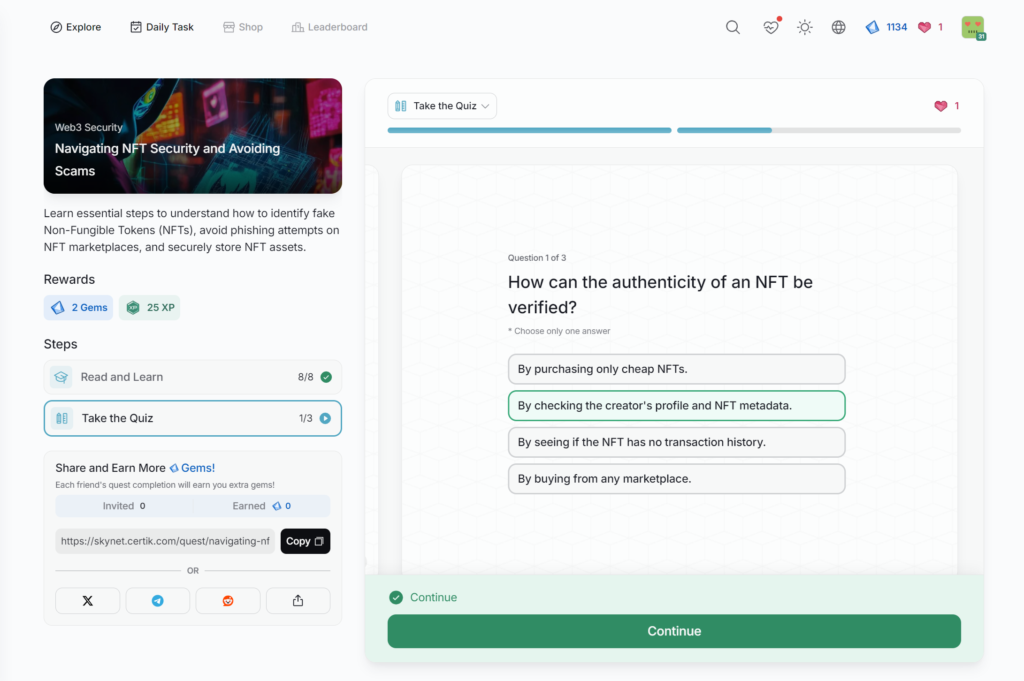
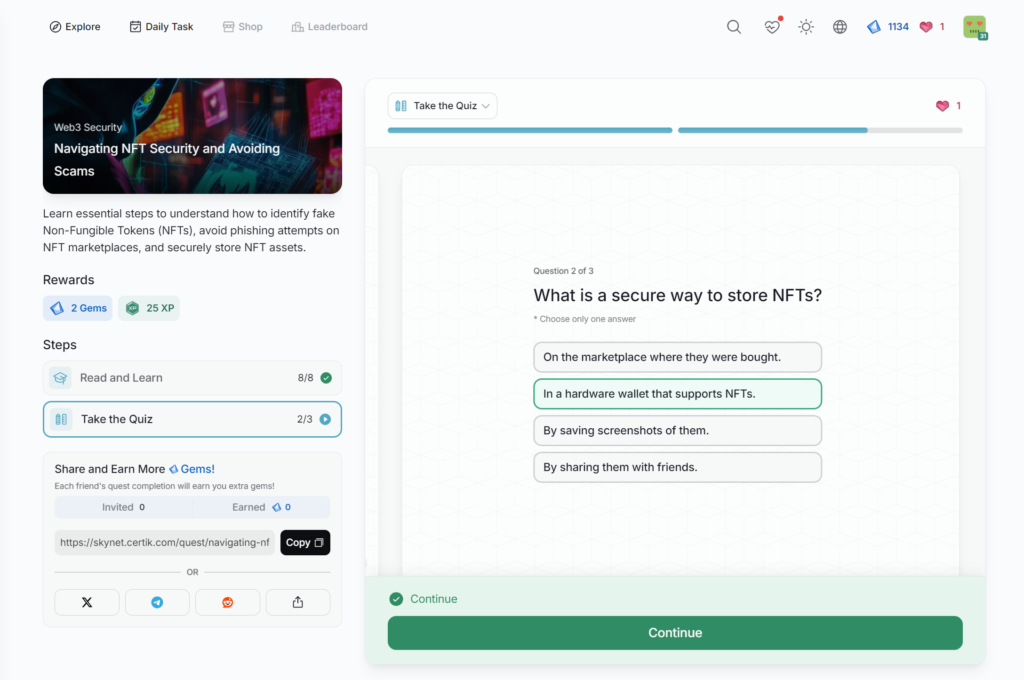
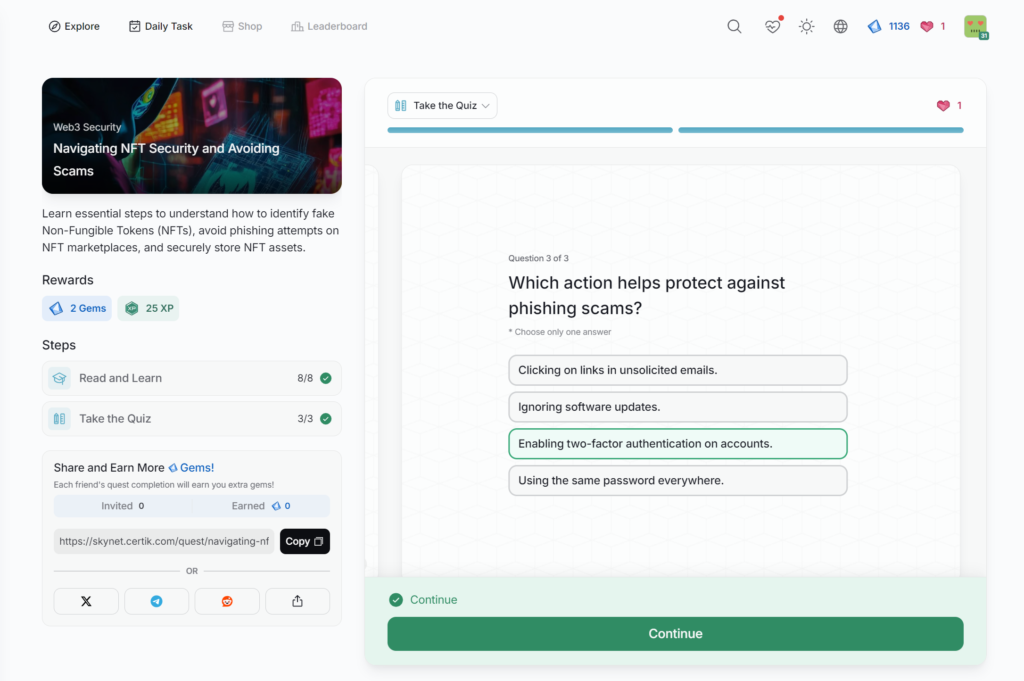
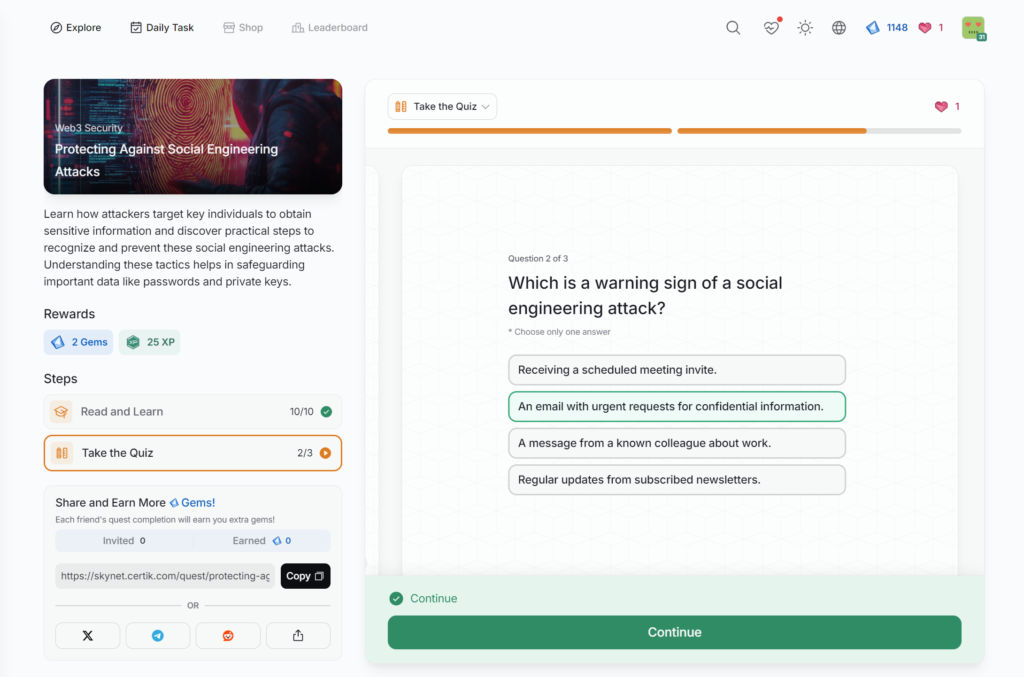
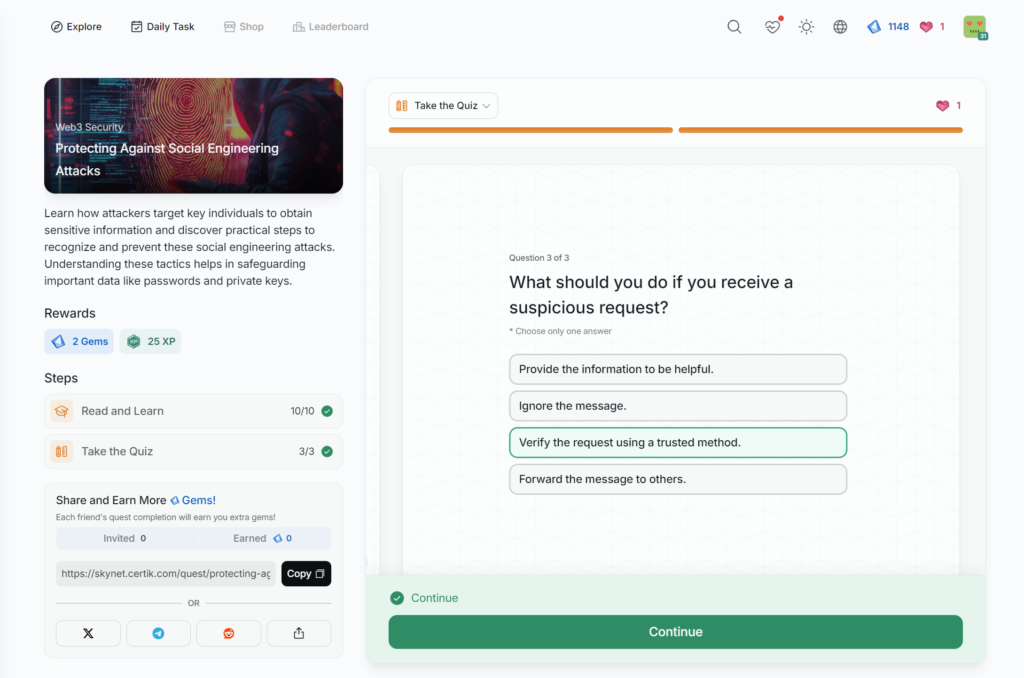
Protecting Against Social Engineering Attacks
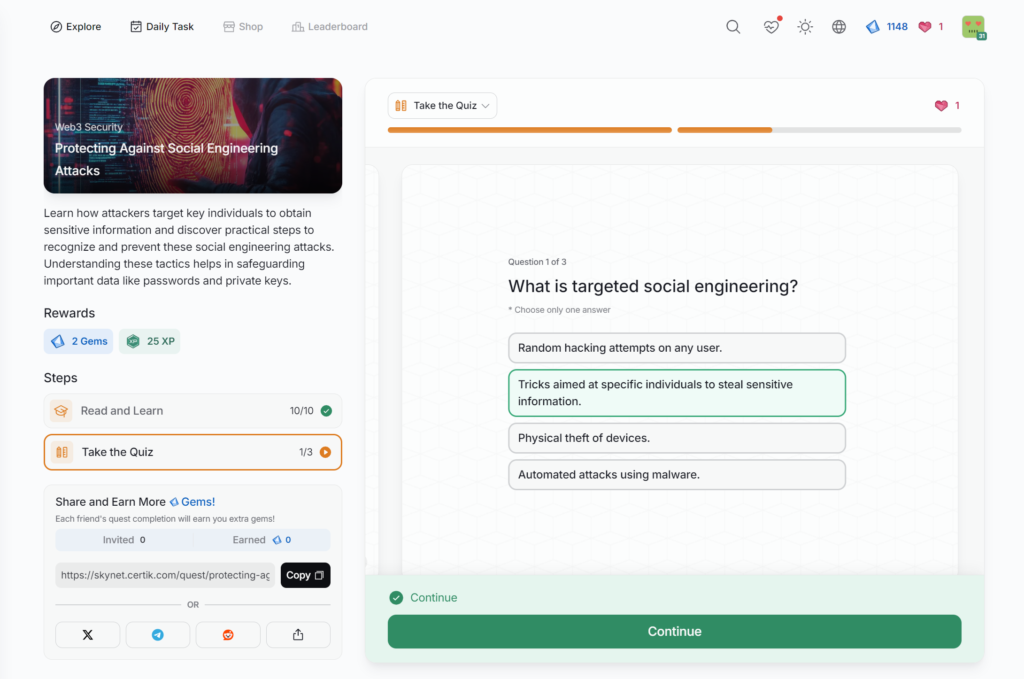
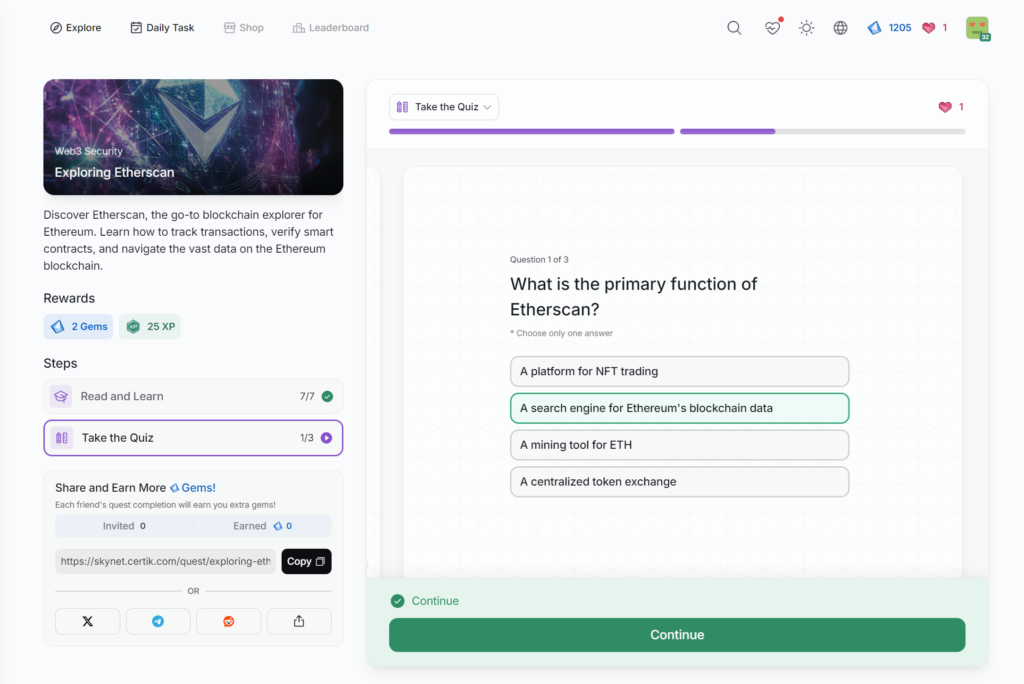
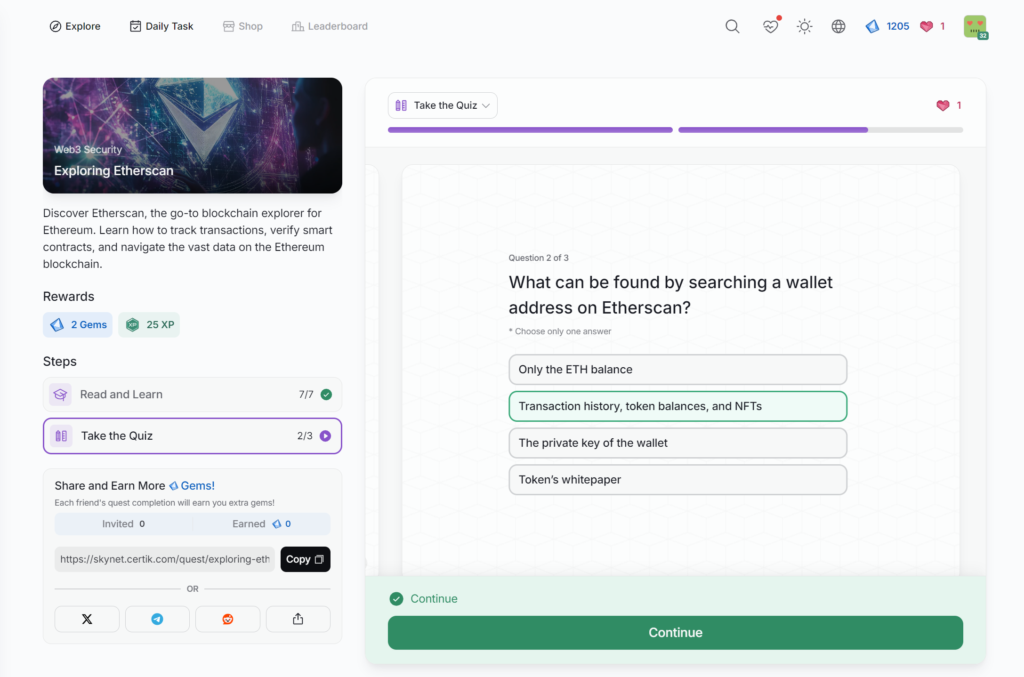
Exploring Etherscan
Understanding Chain Hopping and Crypto Money Laundering
How the DHS is Stopping Ransomware Attacks
About Satoshi Nakamoto
What is DePIN?
Identifying Crypto Market Manipulation
Radiant Capital’s M DeFi Hack Response
Defending Against Clipper Malware
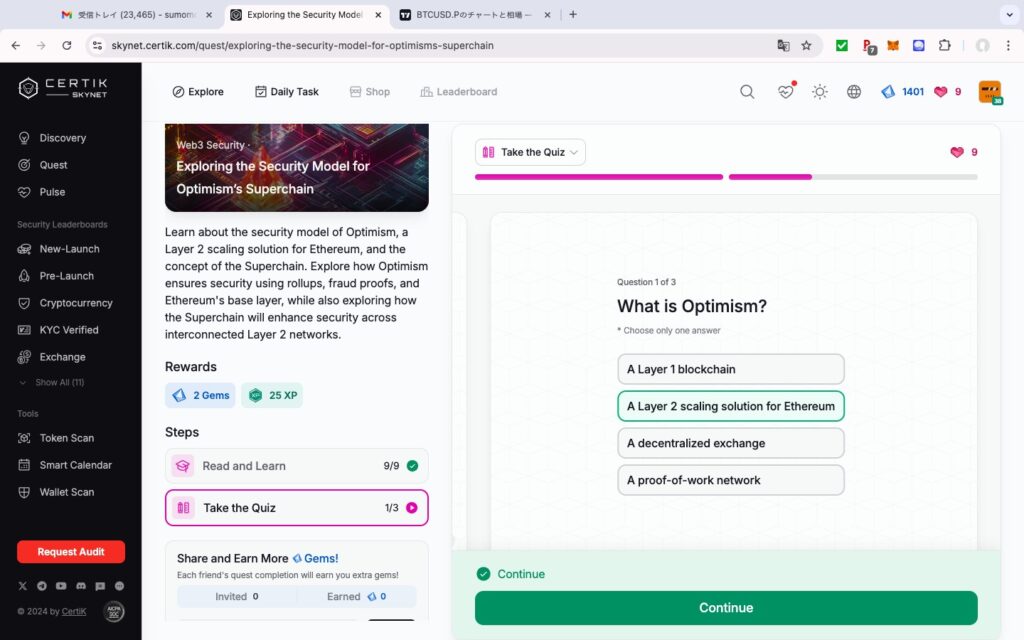
Exploring the Security Model for Optimism’s Superchain
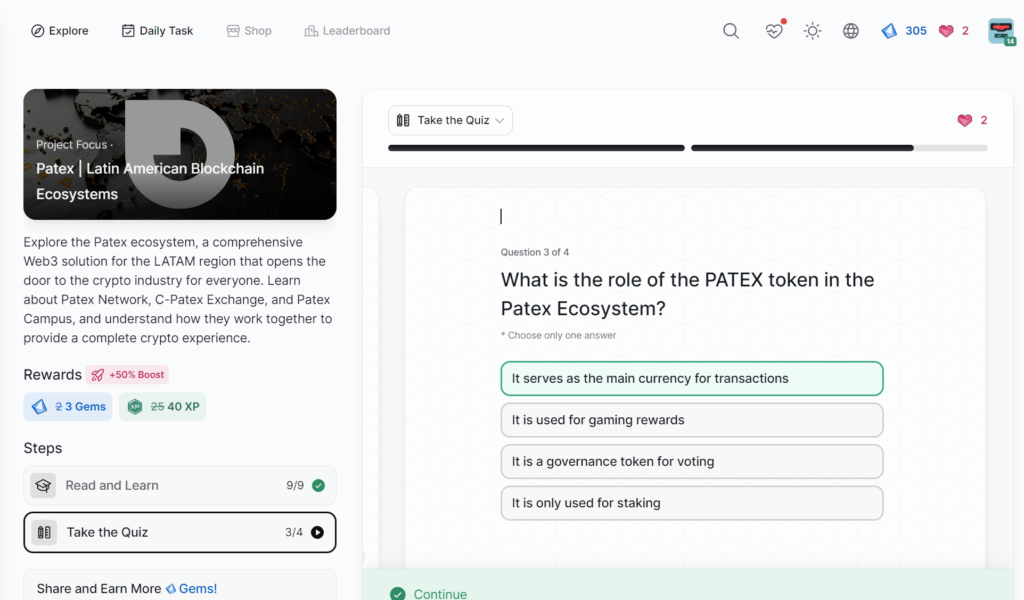
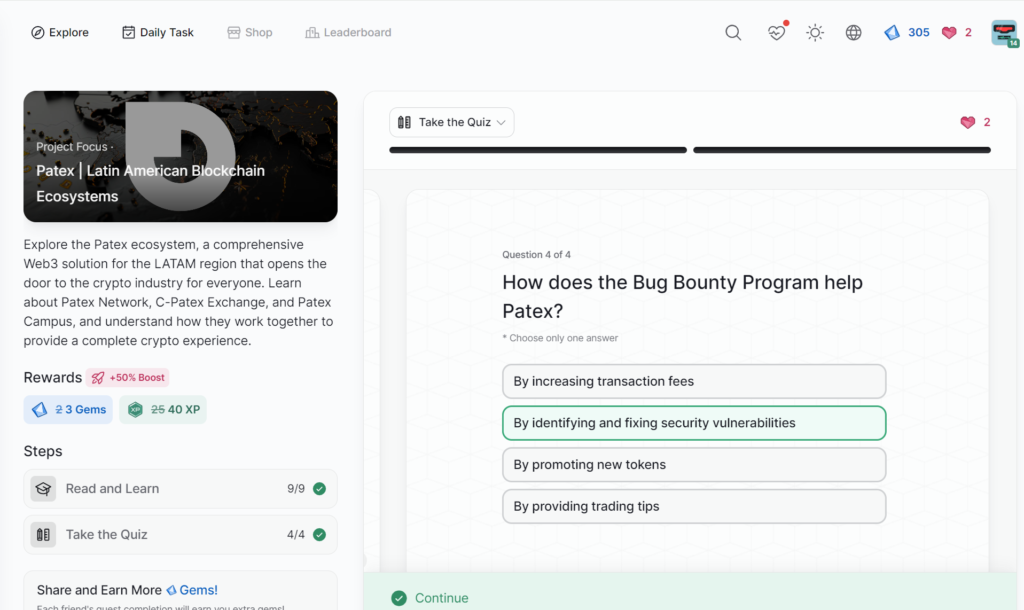
Patex | Latin American Blockchain Ecosystems
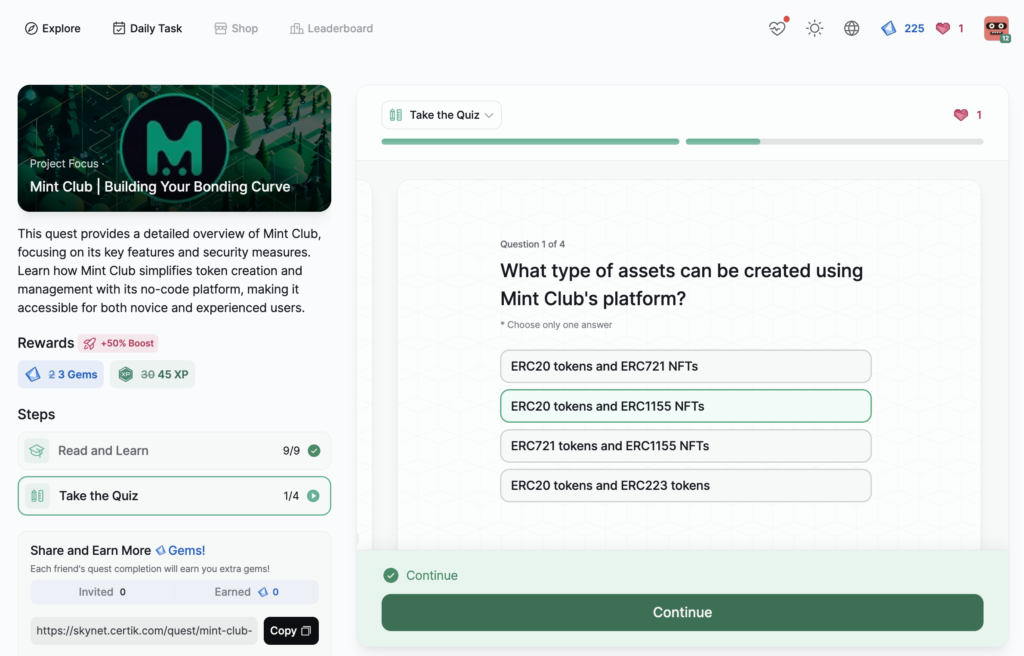
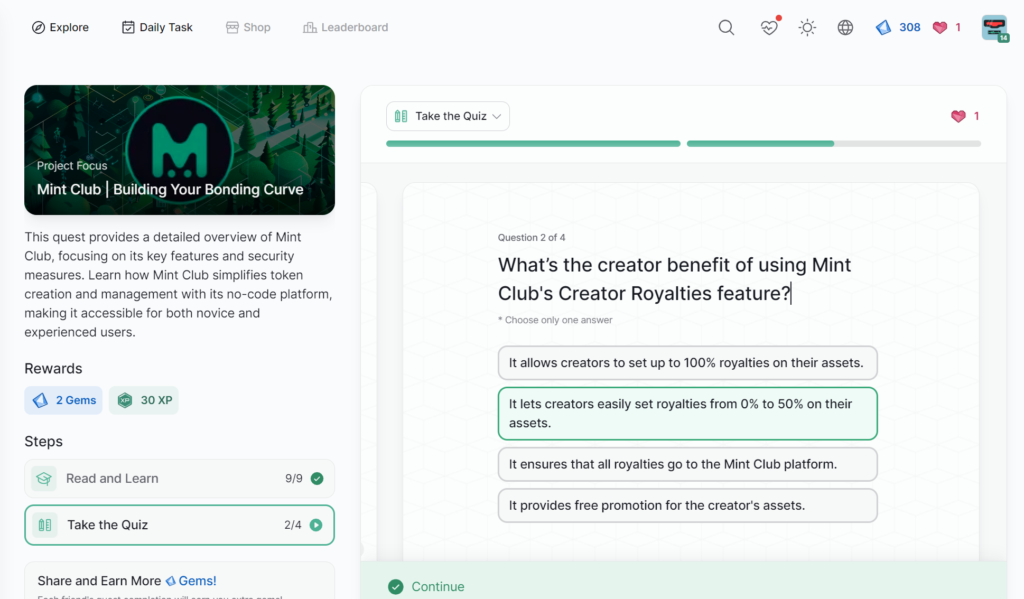
Mint Club | Building Your Bonding Curve
OpenGPU | Harnessing Decentralized GPU Computing




HanChain | Transforming Music Copyright



Wormhole | Infrastructure
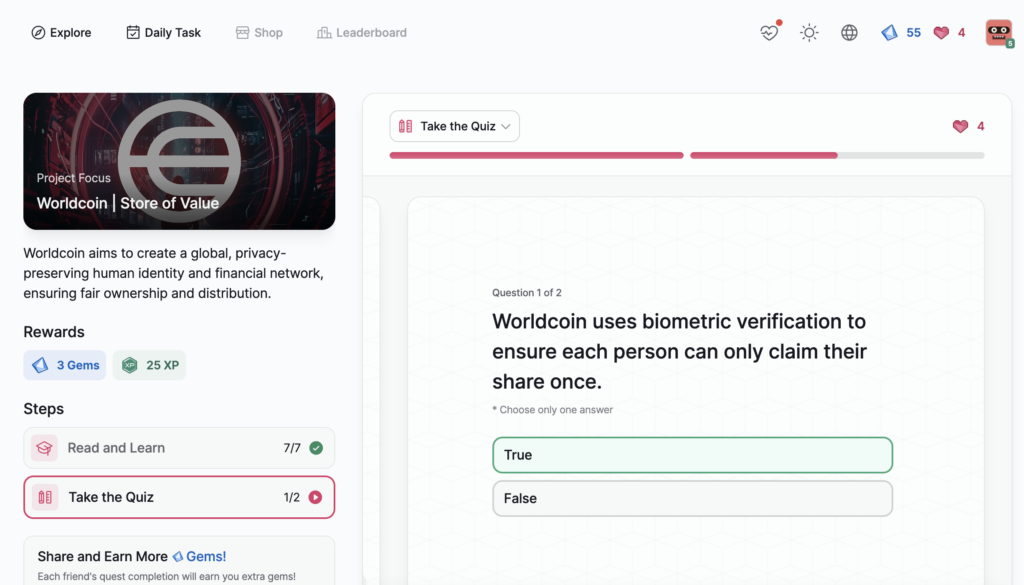
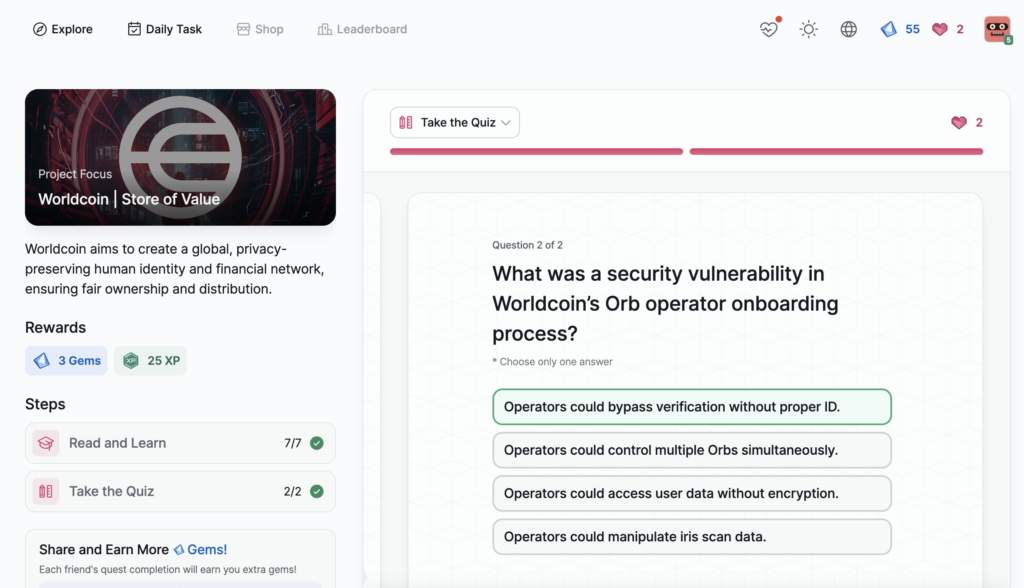
Worldcoin | Store of Value
Trinique | RAT



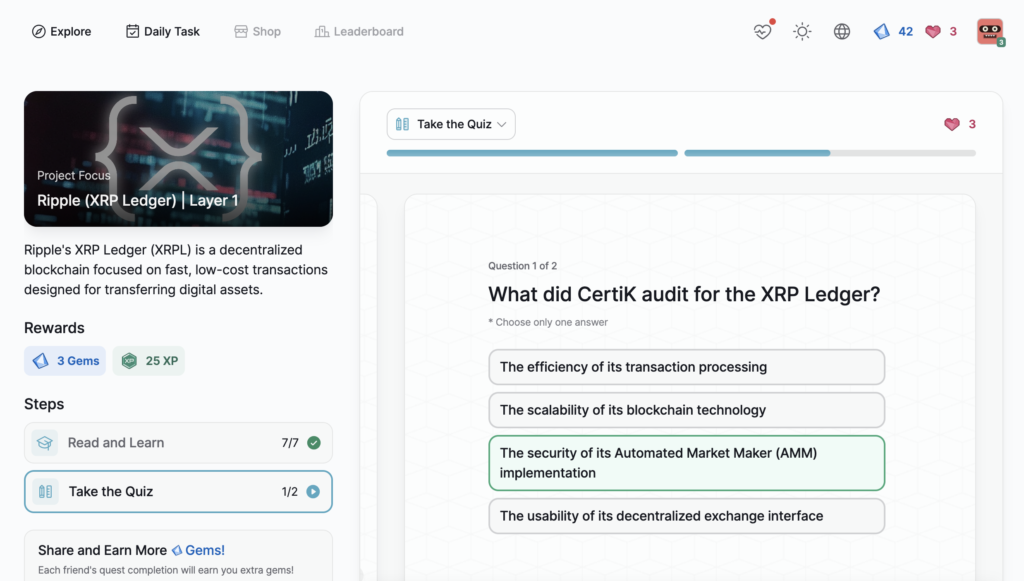
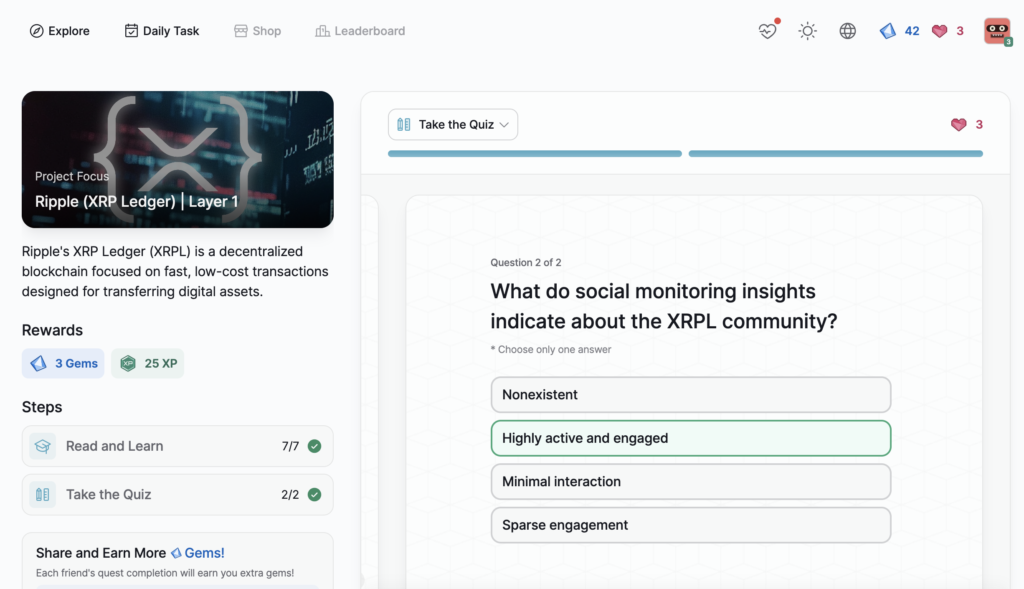
Ripple (XRP Ledger) | Layer 1
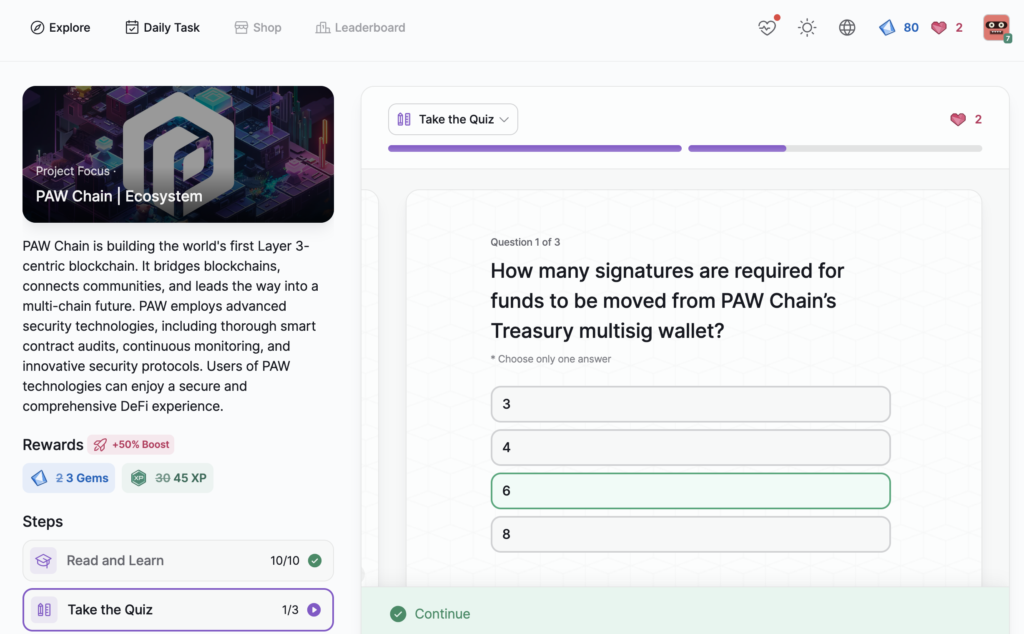
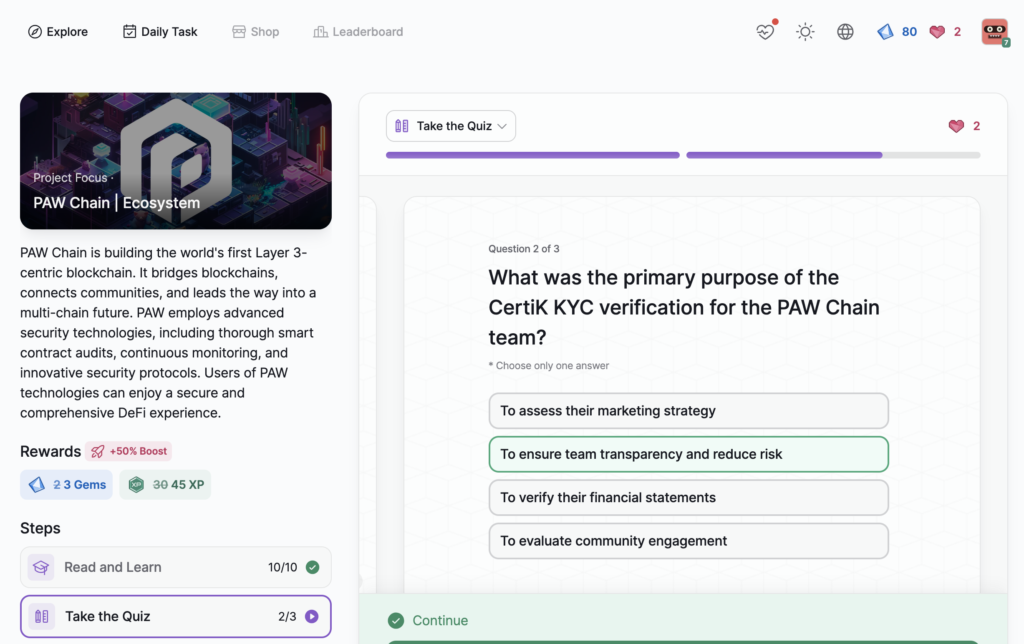
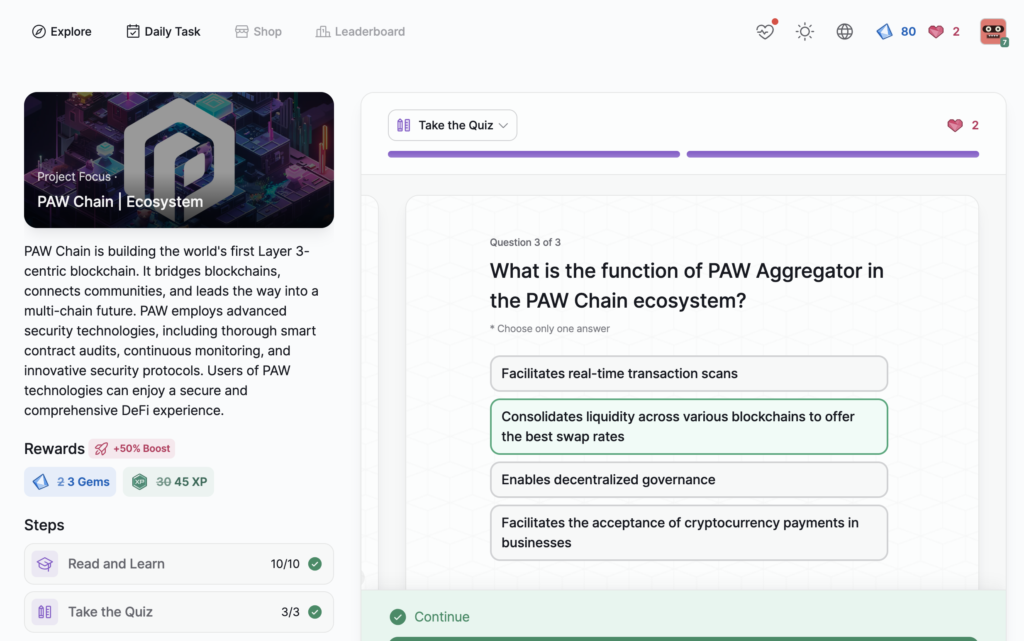
PAW Chain | Ecosystem
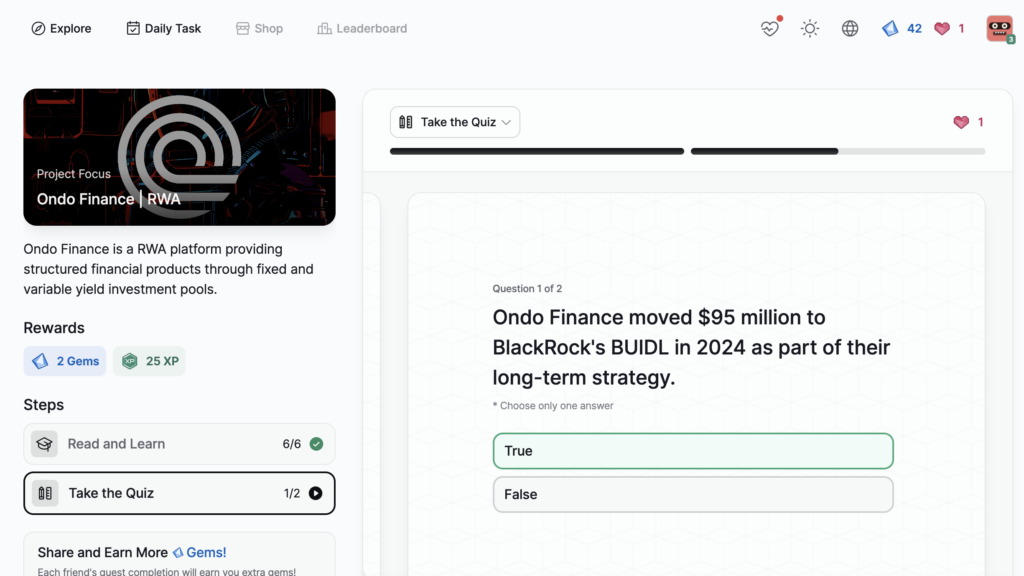
Ondo Finance | RWA
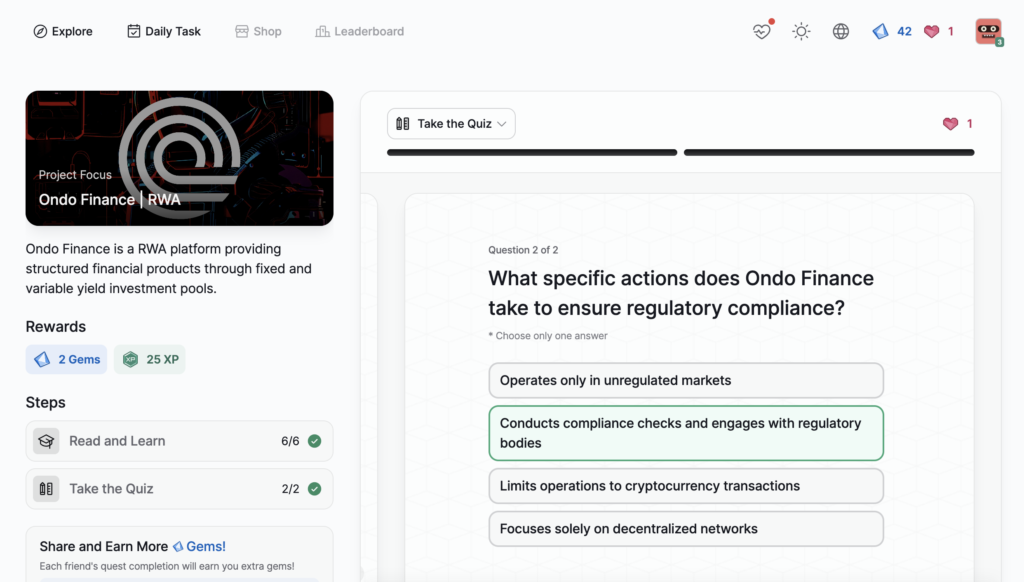
FriendTech | Social
Ethena | Stablecoin
Aptos | Layer 1
Arbitrum | Layer 2
Diamante Blockchain | Infrastructure
EigenLayer | Infrastructure
PEPE | Meme


TON | Layer 1


zkSwap Finance | DeFi



Core DAO | Infrastructure


Edu3Labs | The Future of Education



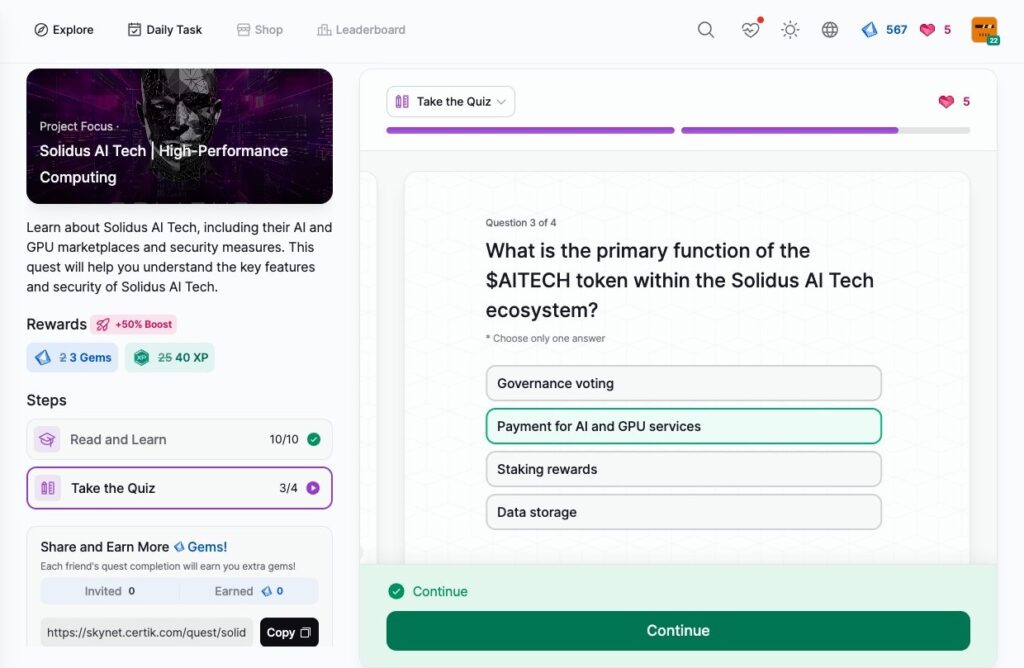
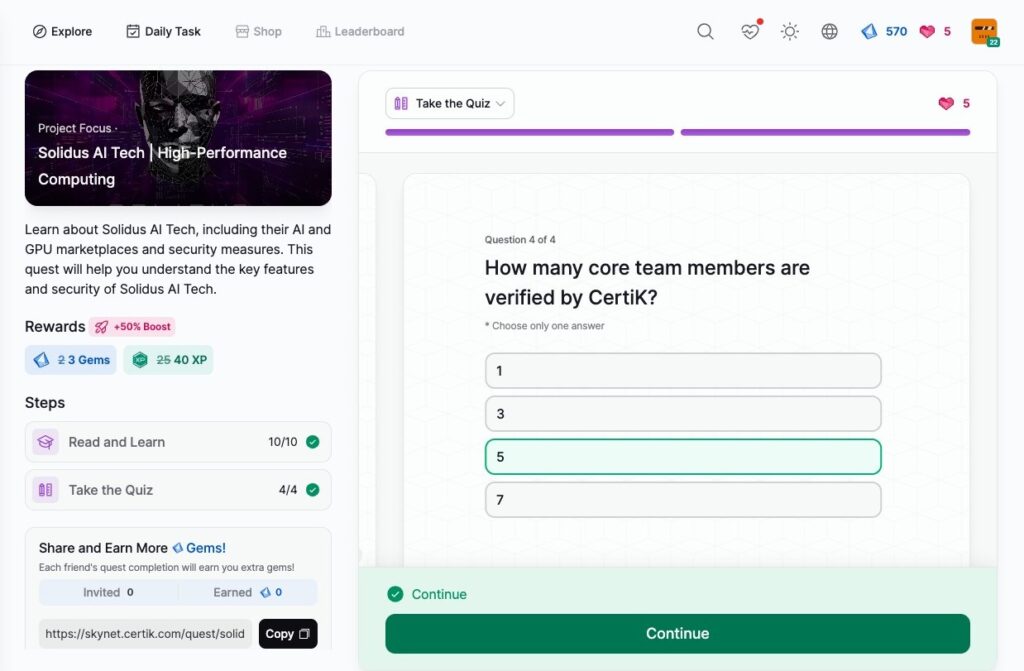
Solidus AI Tech | High-Performance Computing
Mintlayer | Build on Bitcoin




Script Network | Open Source Video Protocol




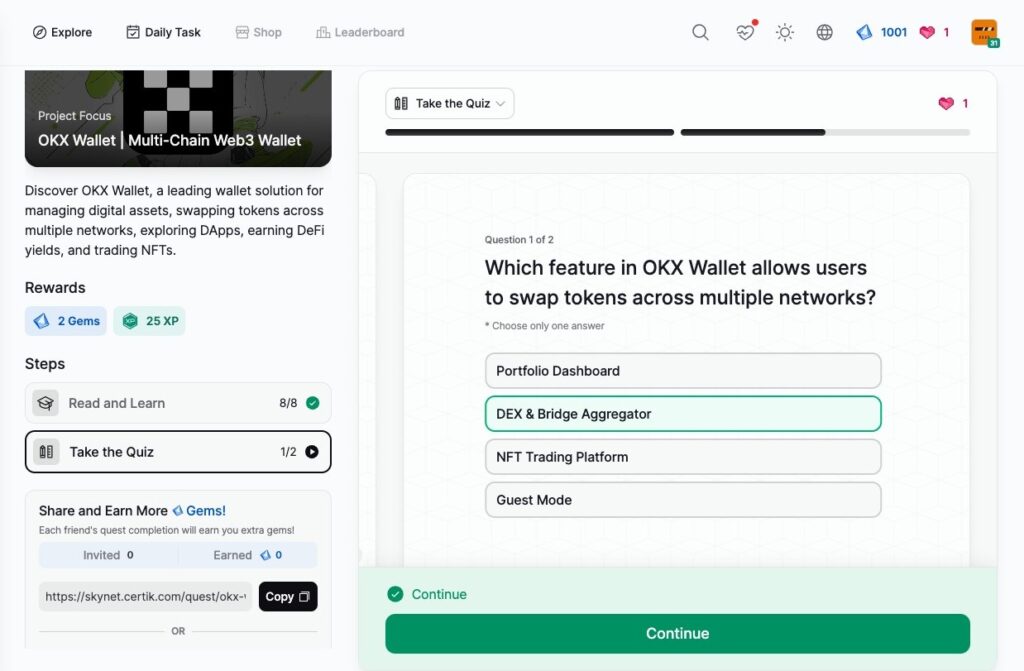
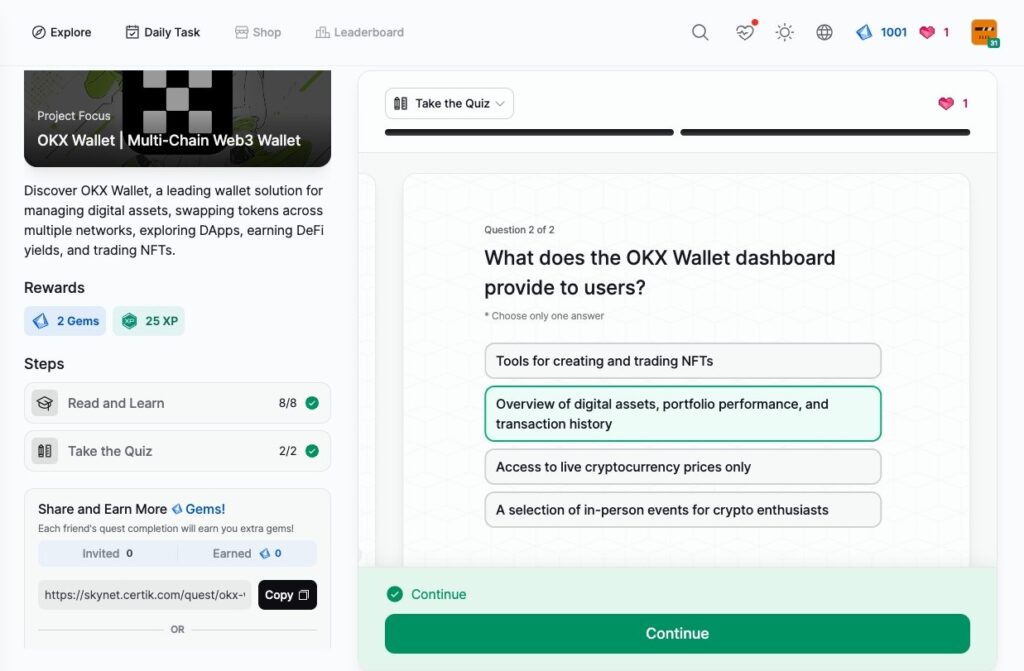
OKX Wallet | Multi-Chain Web3 Wallet
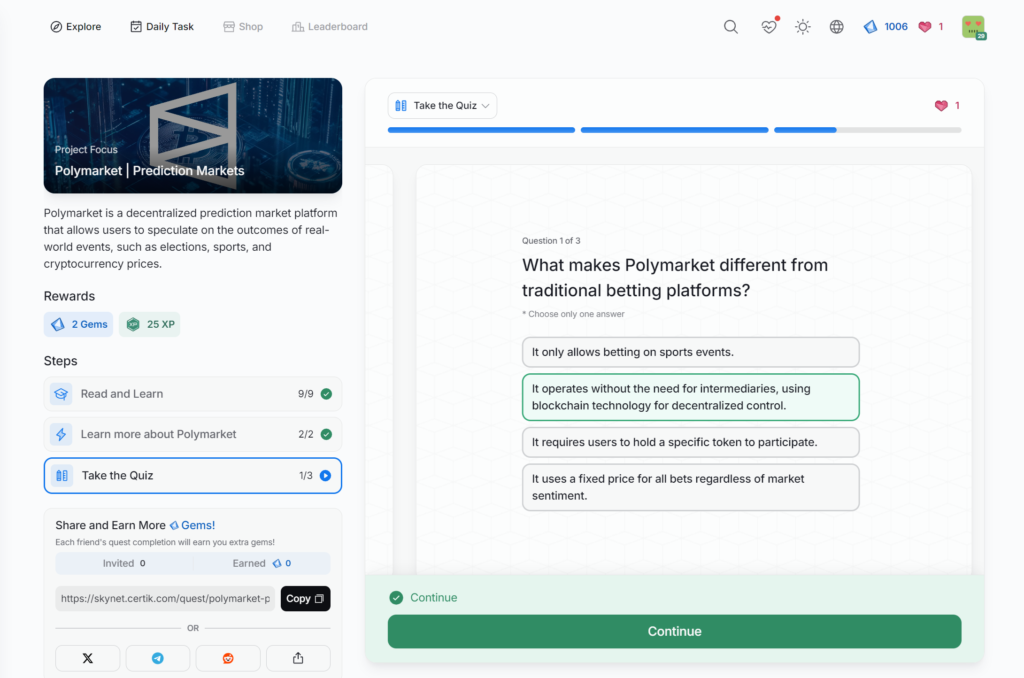
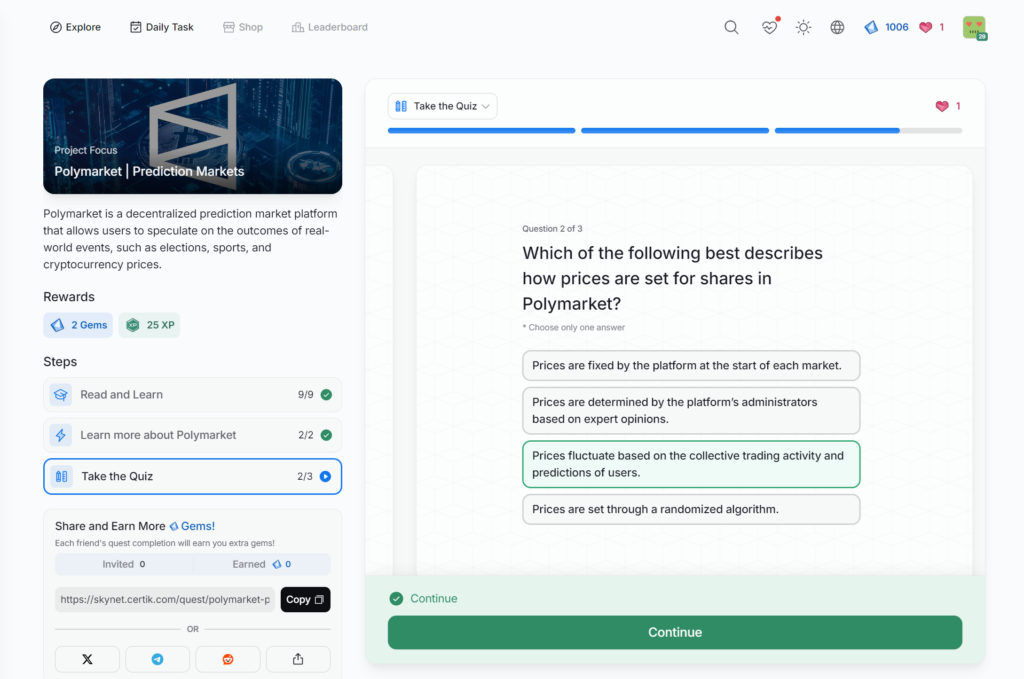
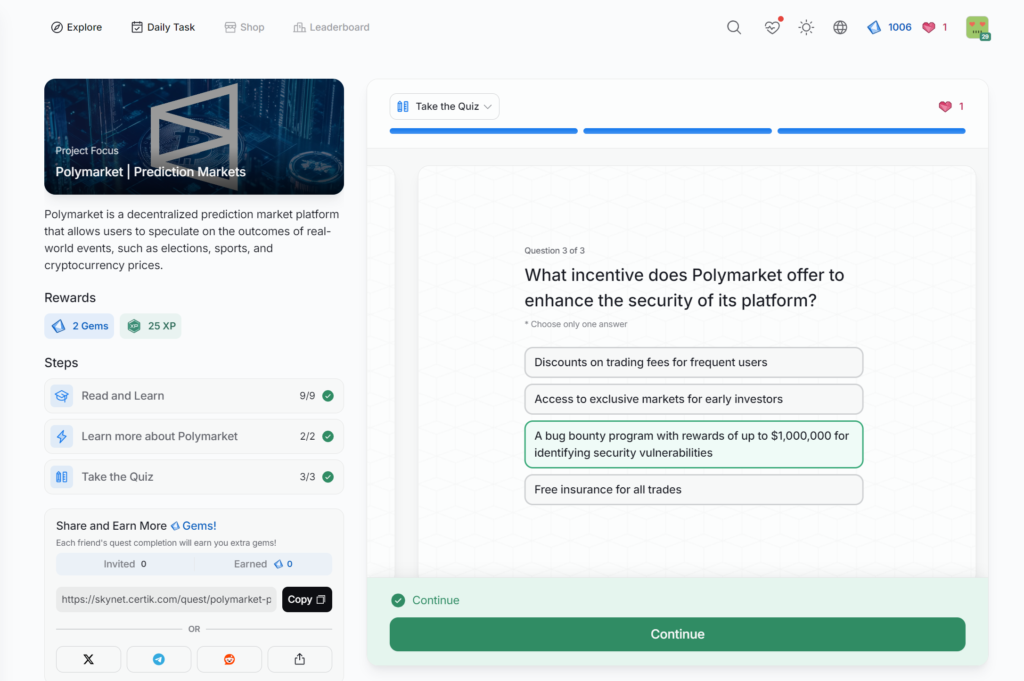
Polymarket | Prediction Markets
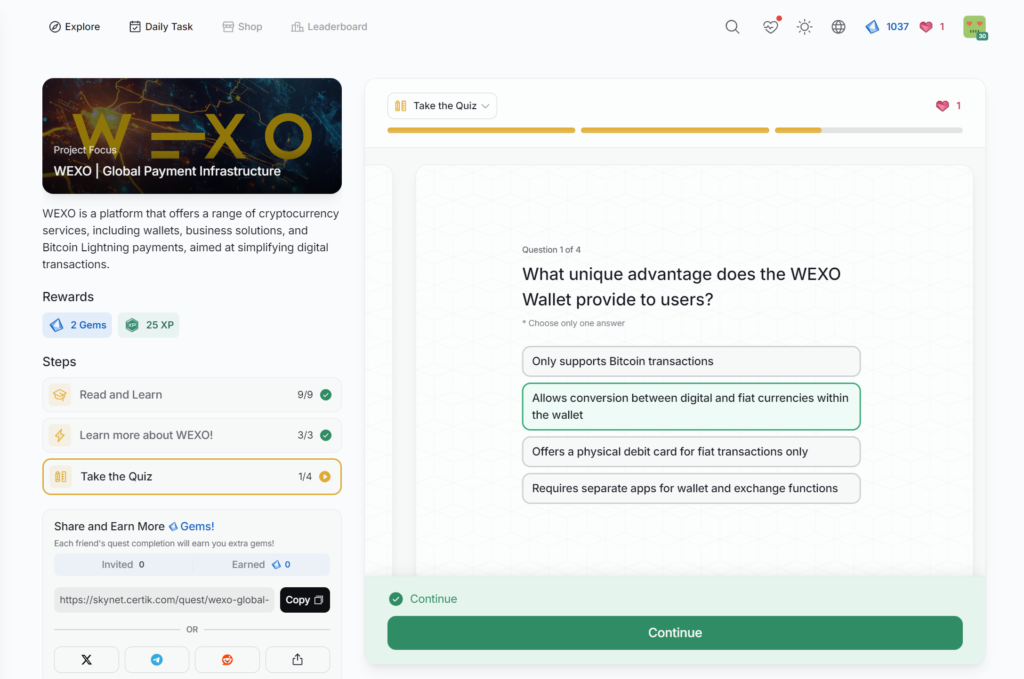
WEXO | Global Payment Infrastructure
MetaMask Overview
Phantom Wallet | Solana and Web3 Wallet
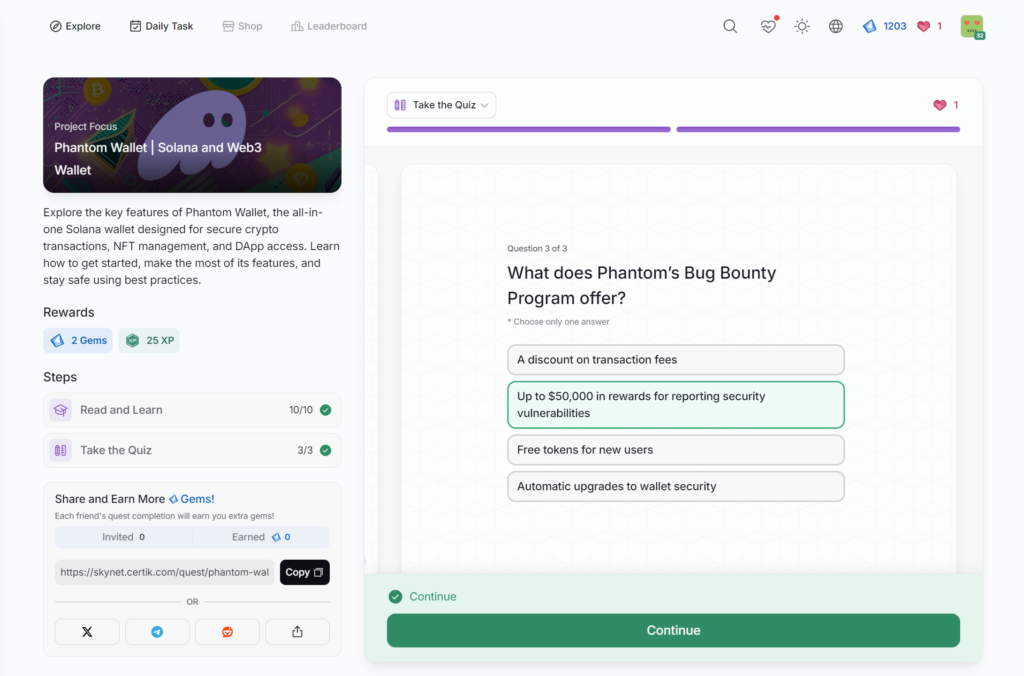
How Exit Scammers Mint Tokens Undetected
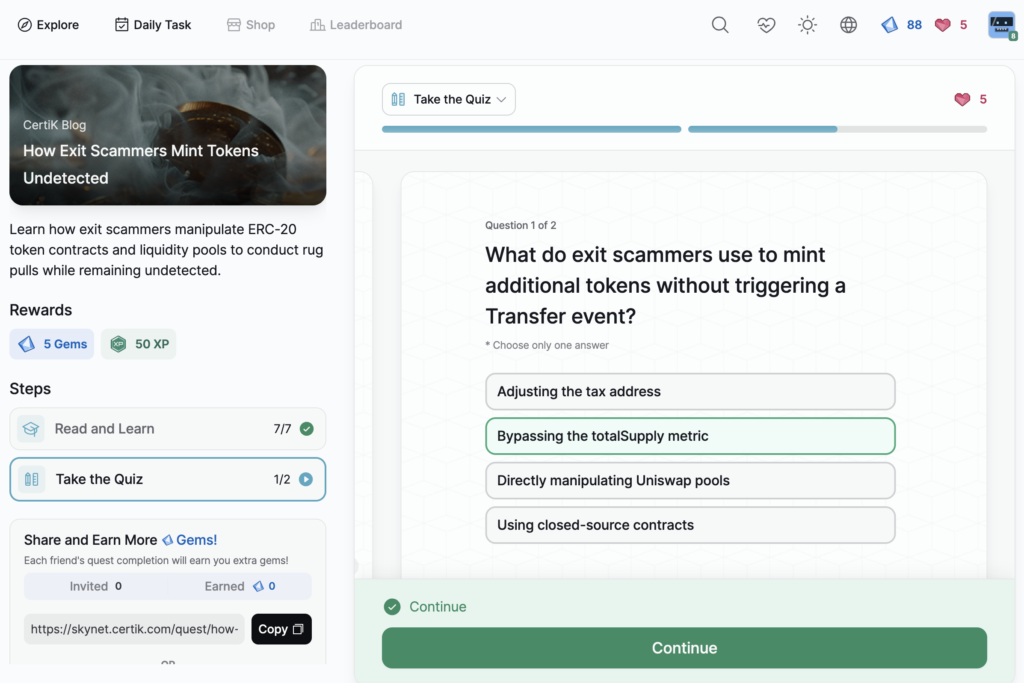
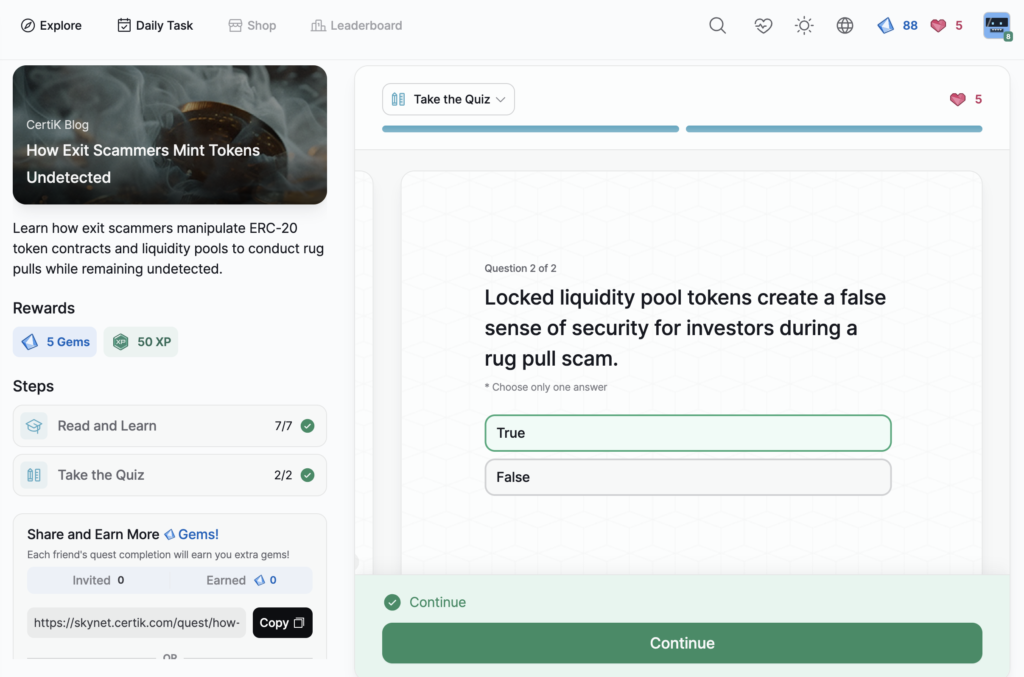
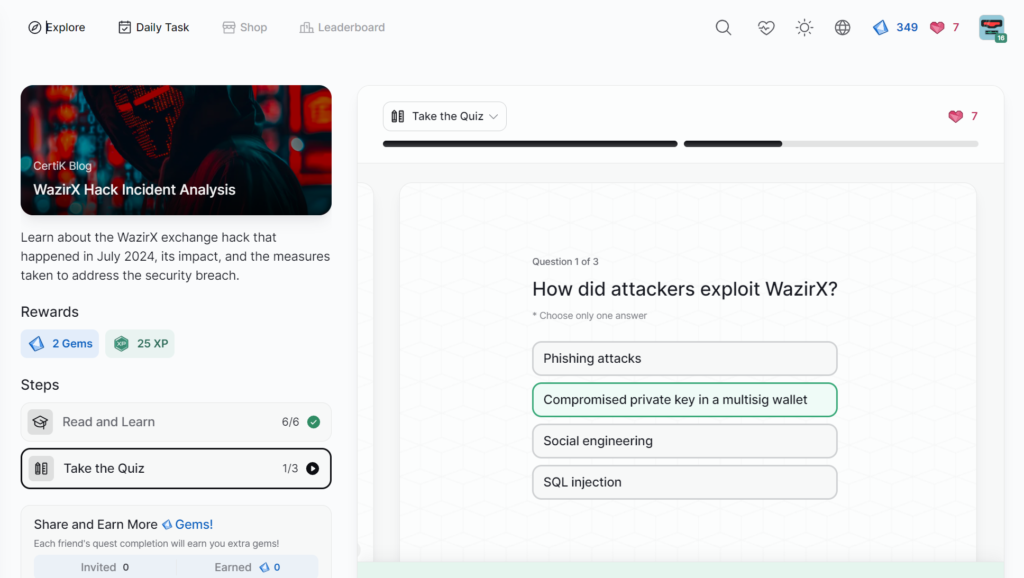
WazirX Hack Incident Analysis
Top Performing Cryptocurrencies of H1 2024
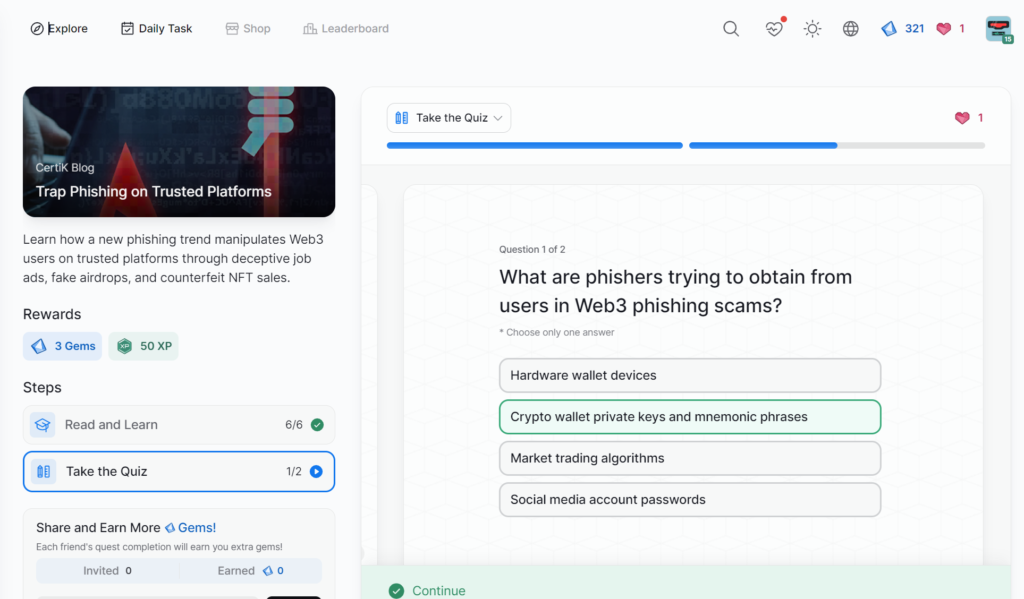
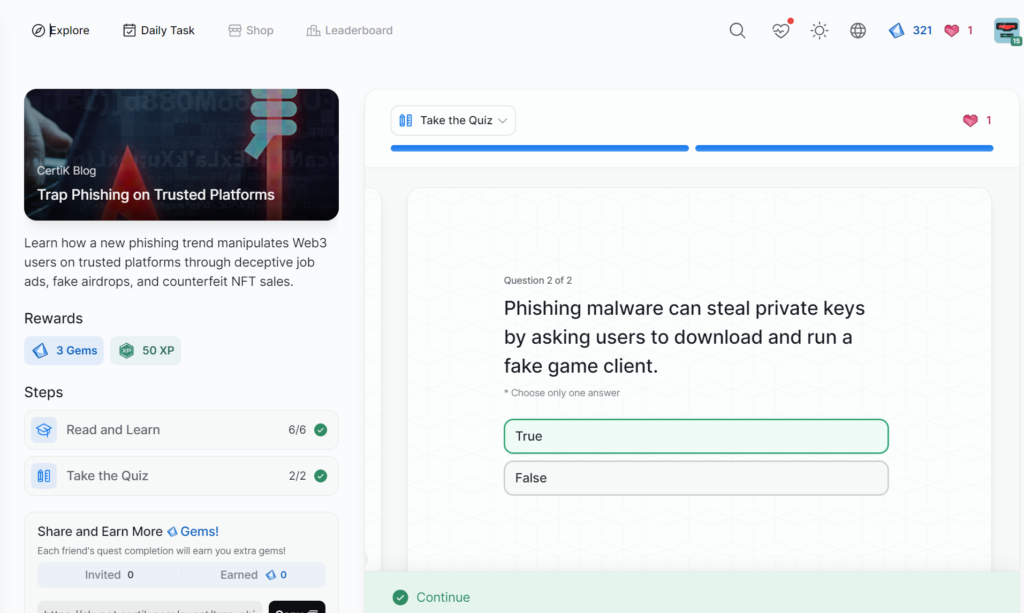
Trap Phishing on Trusted Platforms
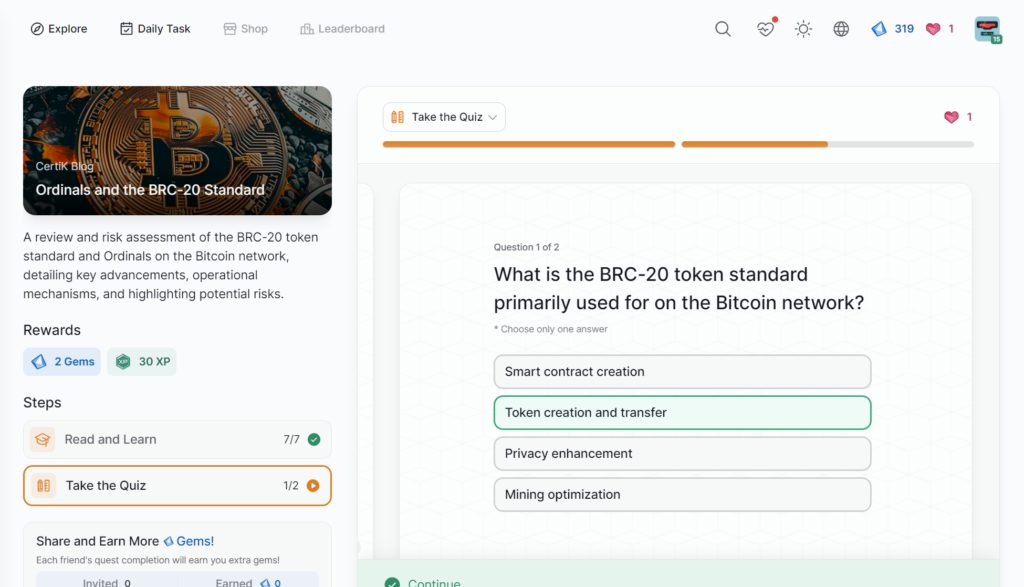
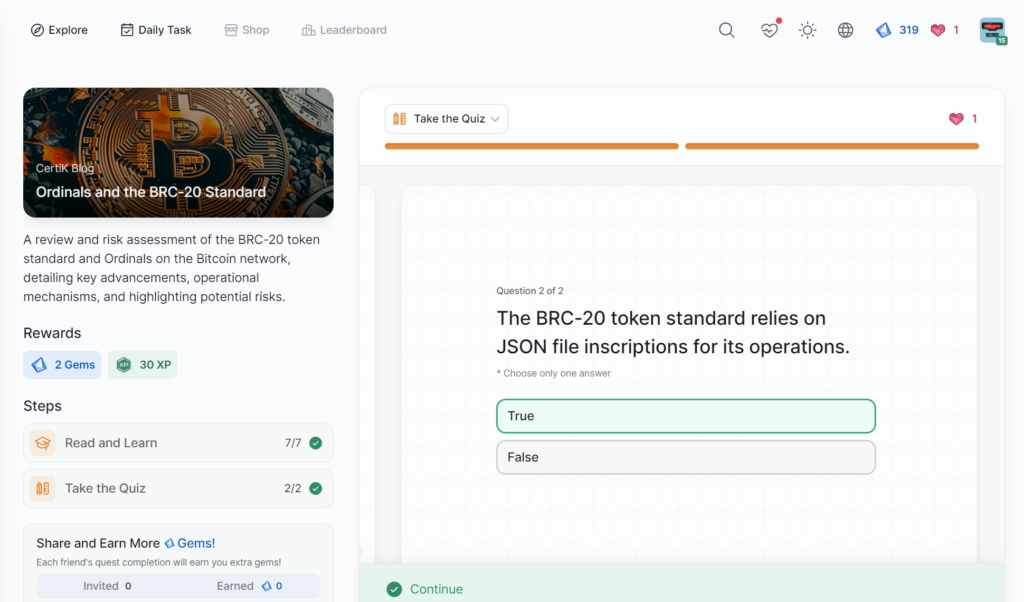
Ordinals and the BRC-20 Standard
Build trust and integrity in project teams with KYC
Introduction of Diamond Agency Contract
Best Tools for Tracking Top Crypto Wallets
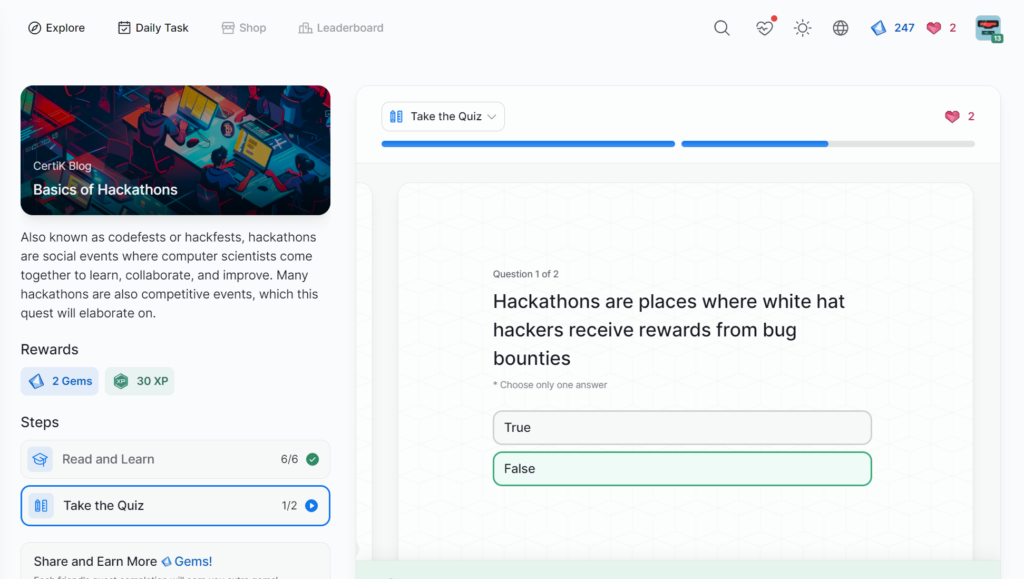
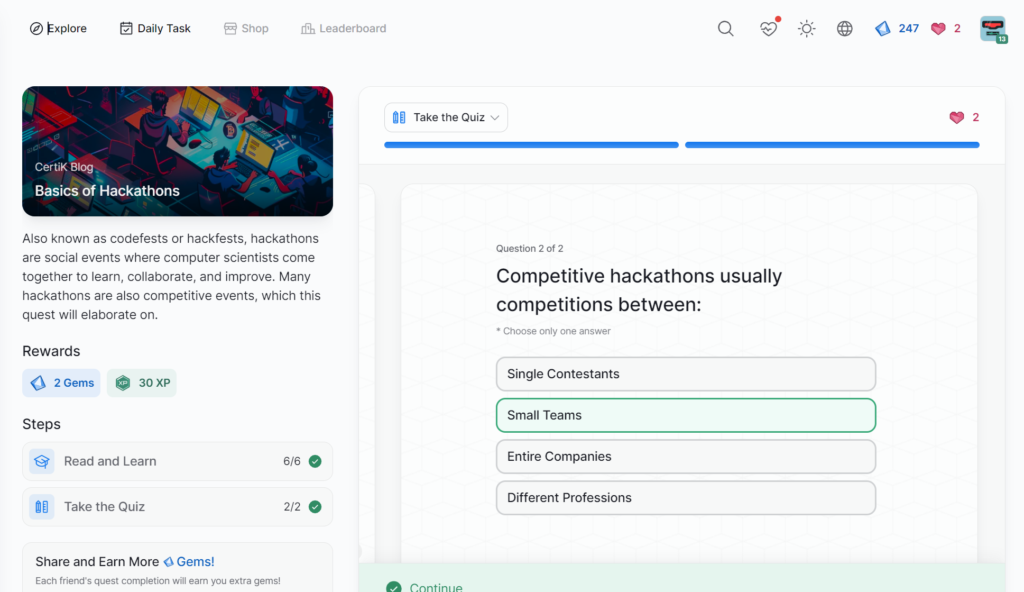
Basics of Hackathons
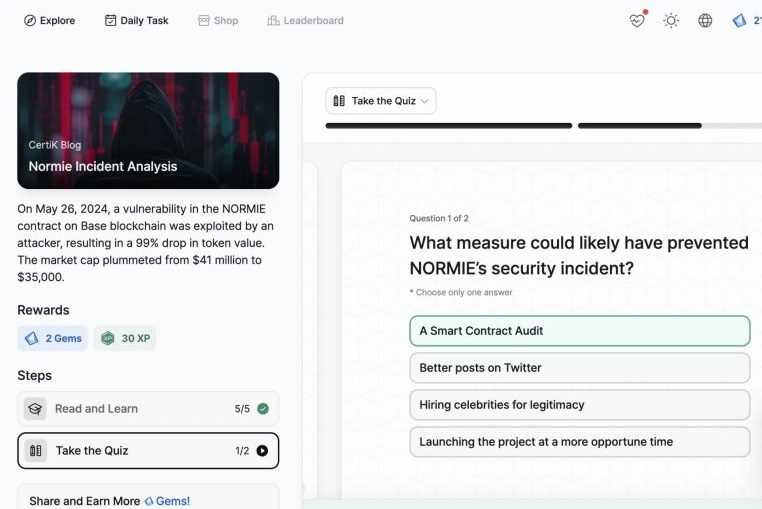
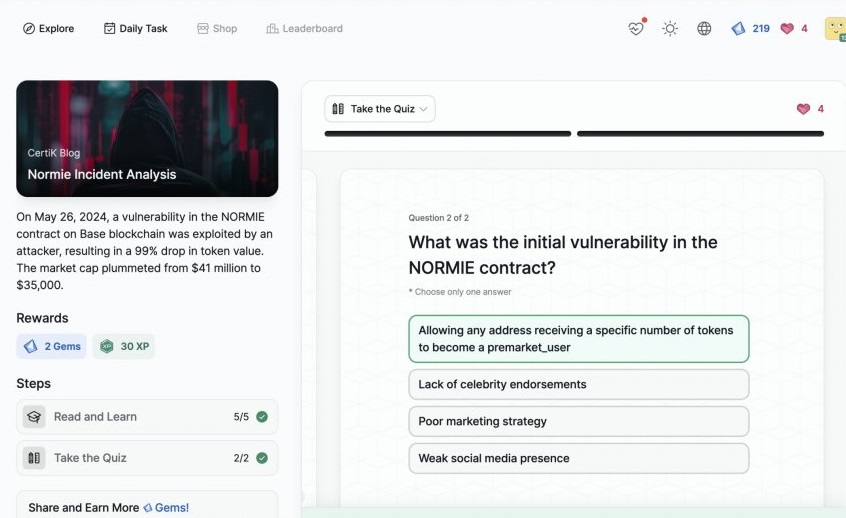
Normie Incident Analysis
Bot-Driven Wash Trading in Exit Scams
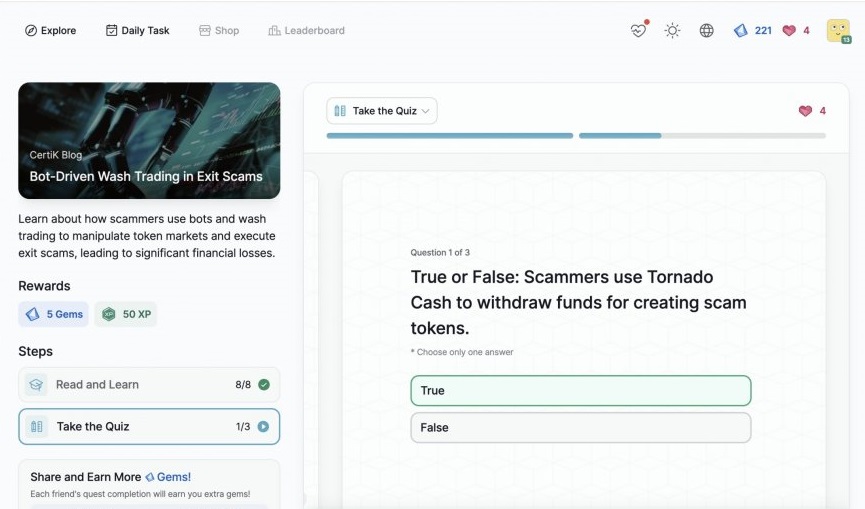
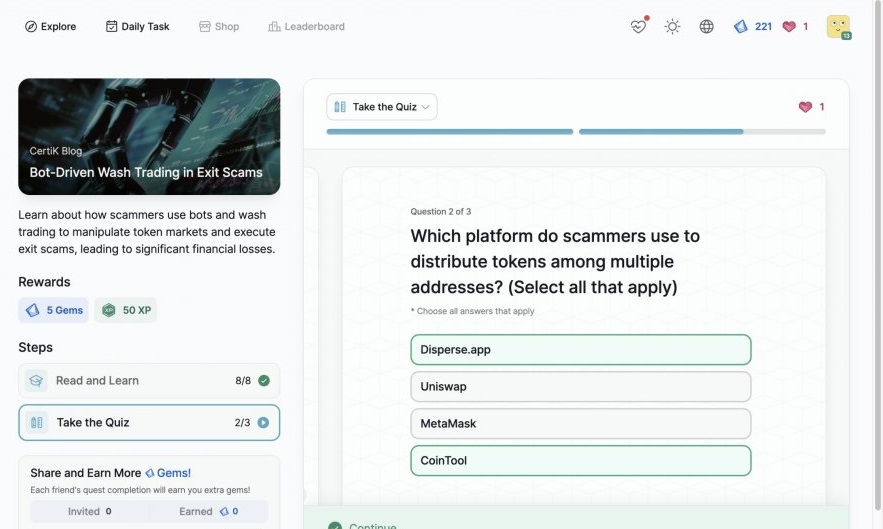
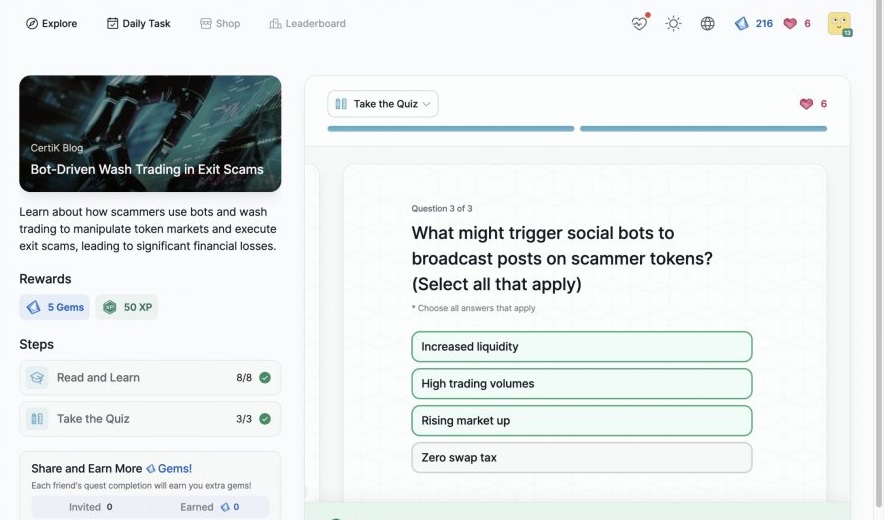
Advanced Formal Verification of ZK Proofs
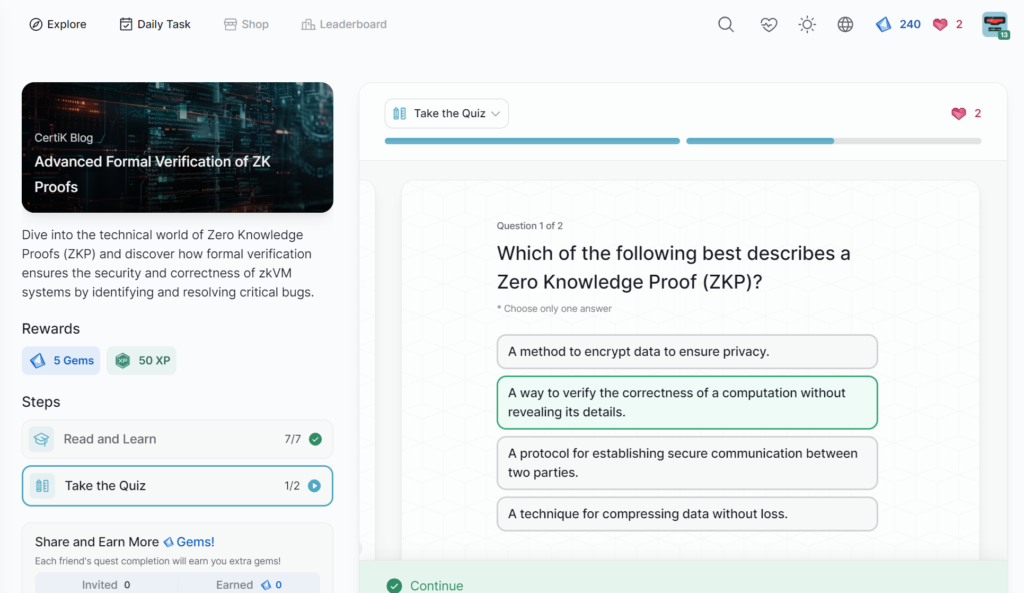
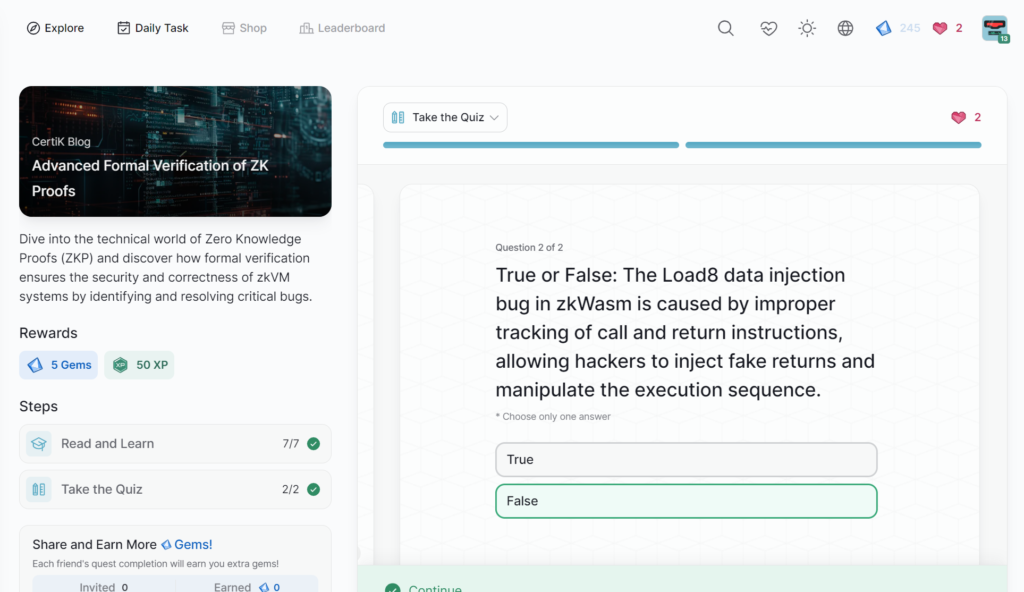
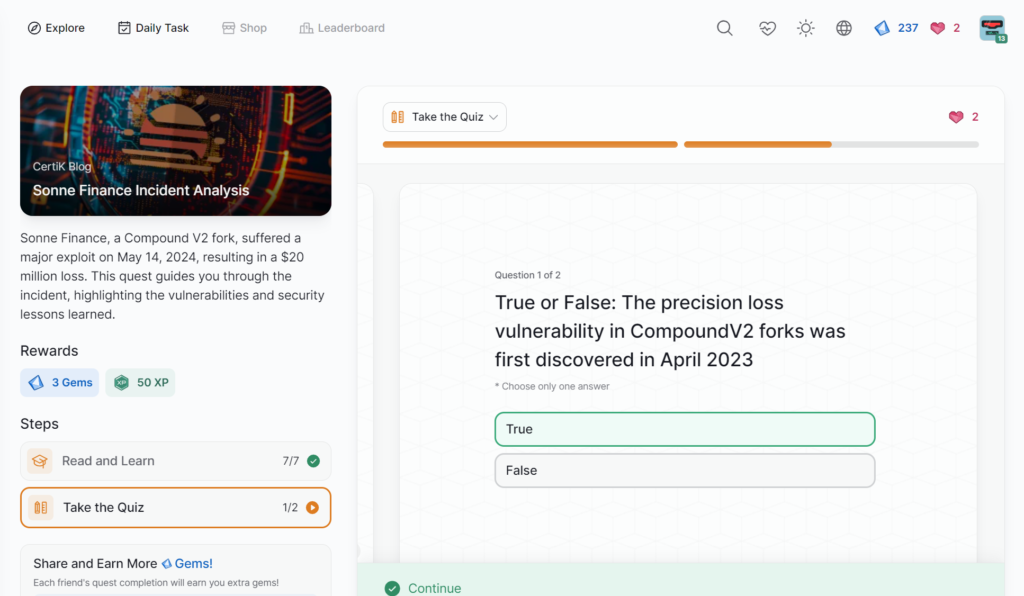
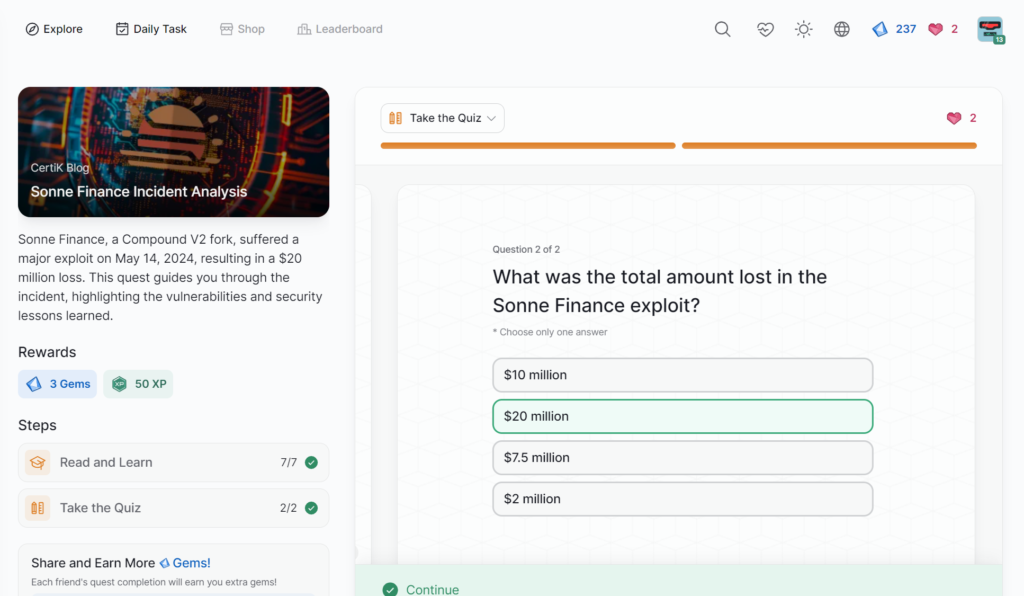
Sonne Finance Incident Analysis
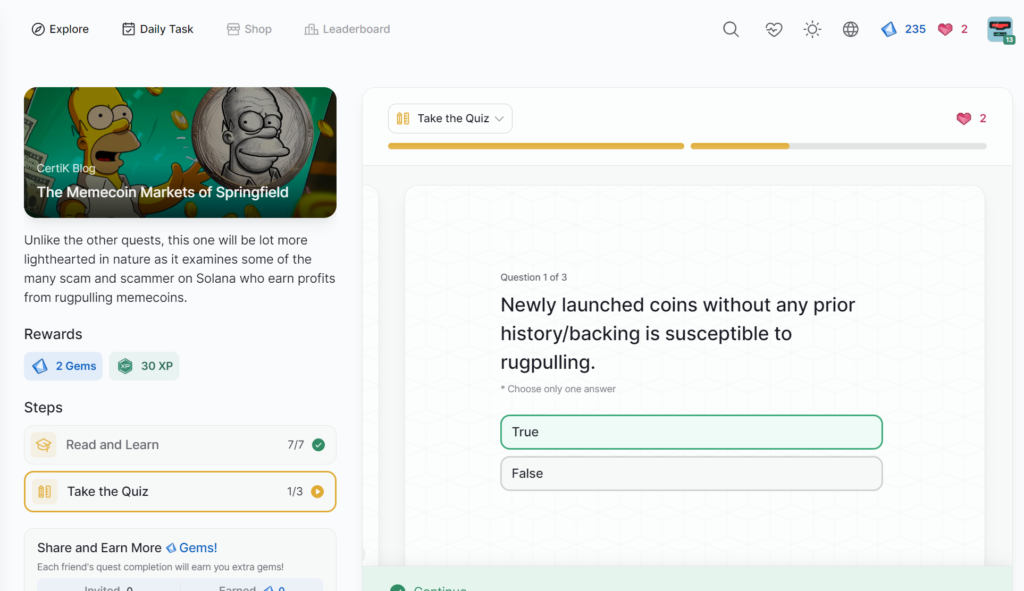
The Memecoin Markets of Springfield
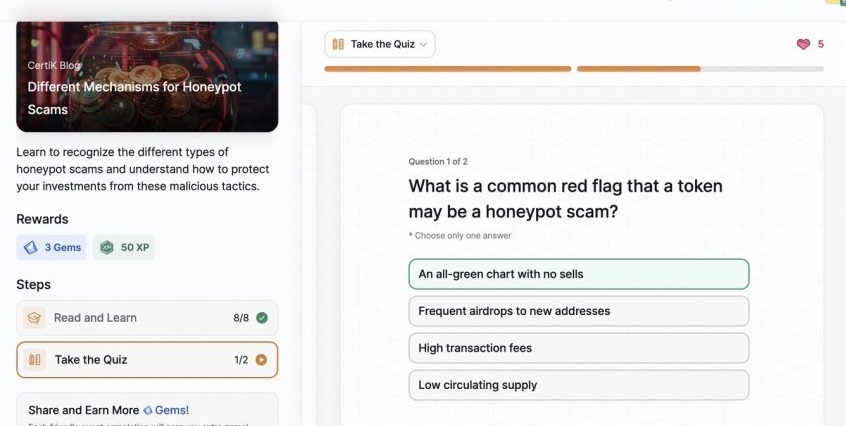
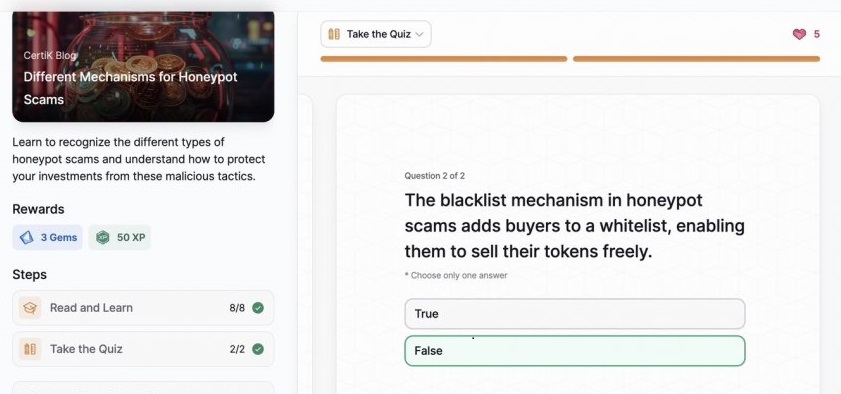
Different Mechanisms for Honeypot Scams
HACK3D Part 1: Top Incident Analyses
HACK3D Part 3: Rounding Issue Exploits
Hedgey Finance Event Analysis
How CertiK Does KYC
Introduction to Formal Verification
KYC Actors are Ramping Up Their Game
Recognizing the Misuse of CertiK’s Brand
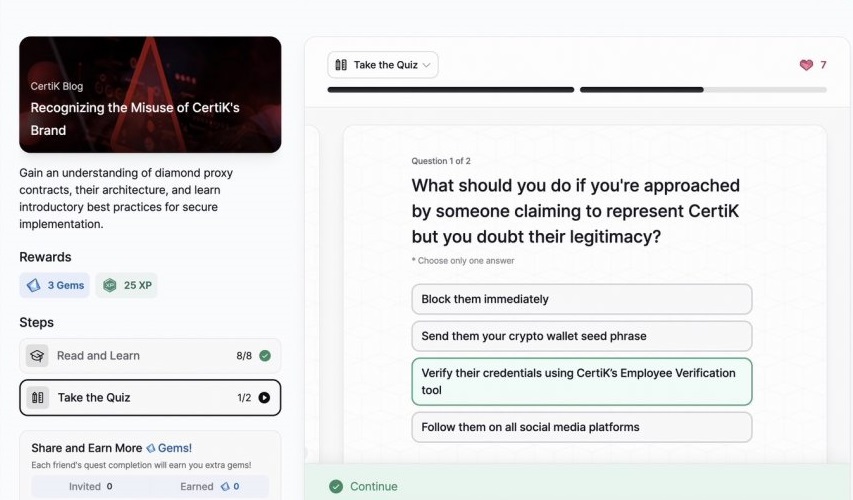
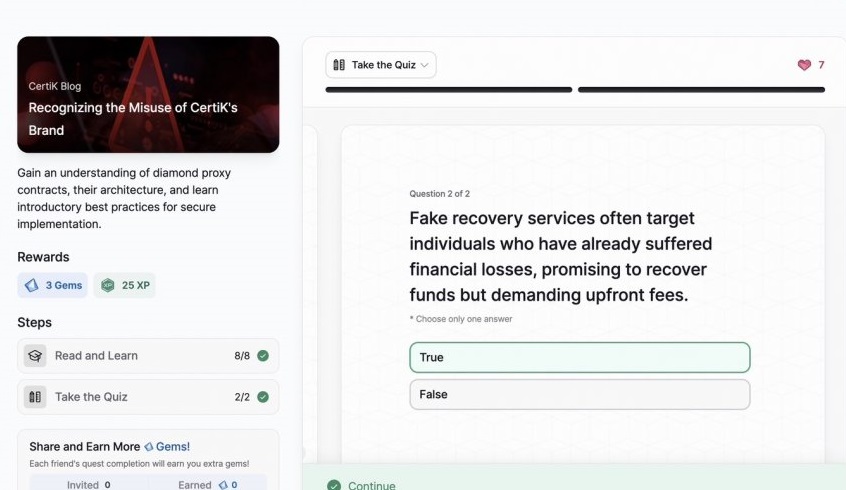
SkyInsights: Crypto Compliance
Unveiling the KYC Actor Industry
SkyKnight



Understanding BGP Hijacking and Internet Routing Security
CertiK’s Journey to Samsung’s Security Hall of Fame
Vanity Address and Address Poisoning
Hack3d Report Q2 H1 2024 – Part 1: Overview and Key Highlights
UtopiaSphere Incident Analysis
Top Compliance Risks in Crypto
HACK3D Part 2: Private Key Compromise
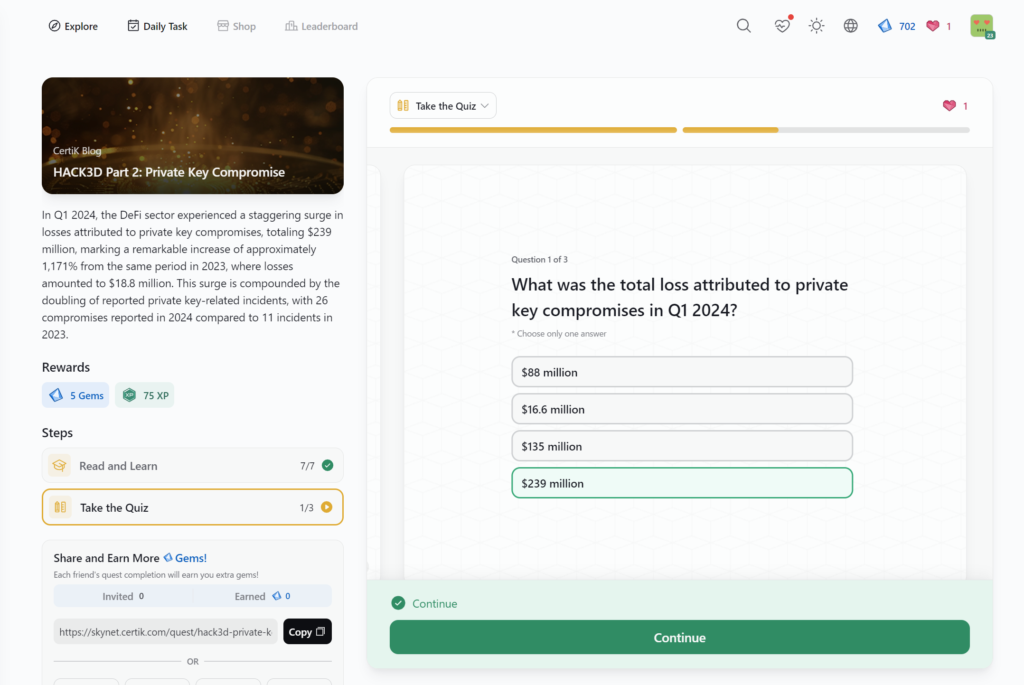
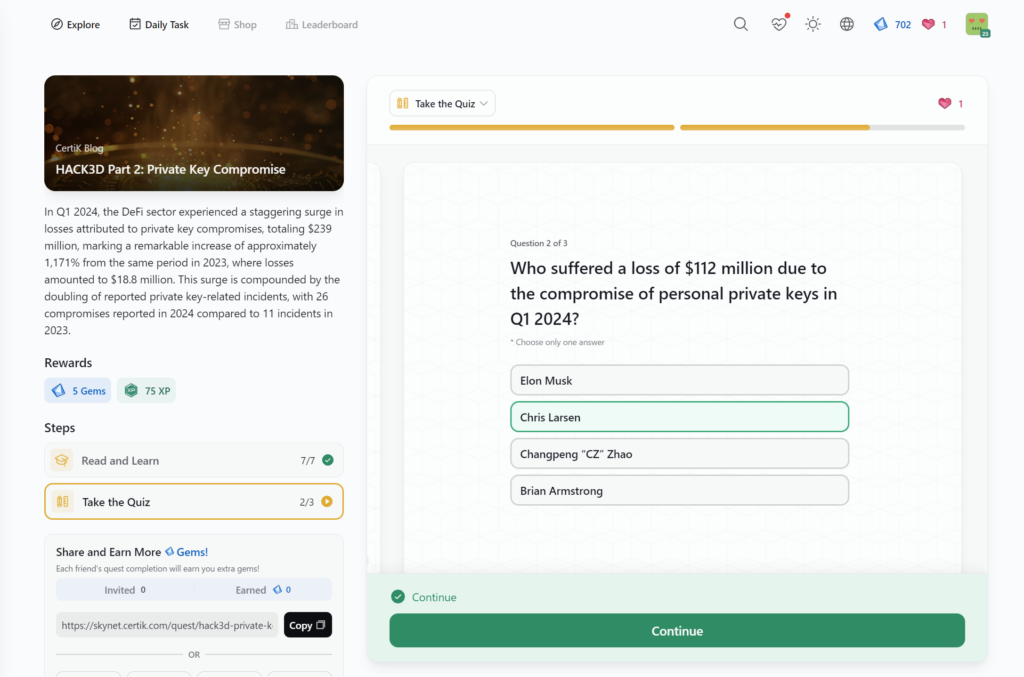
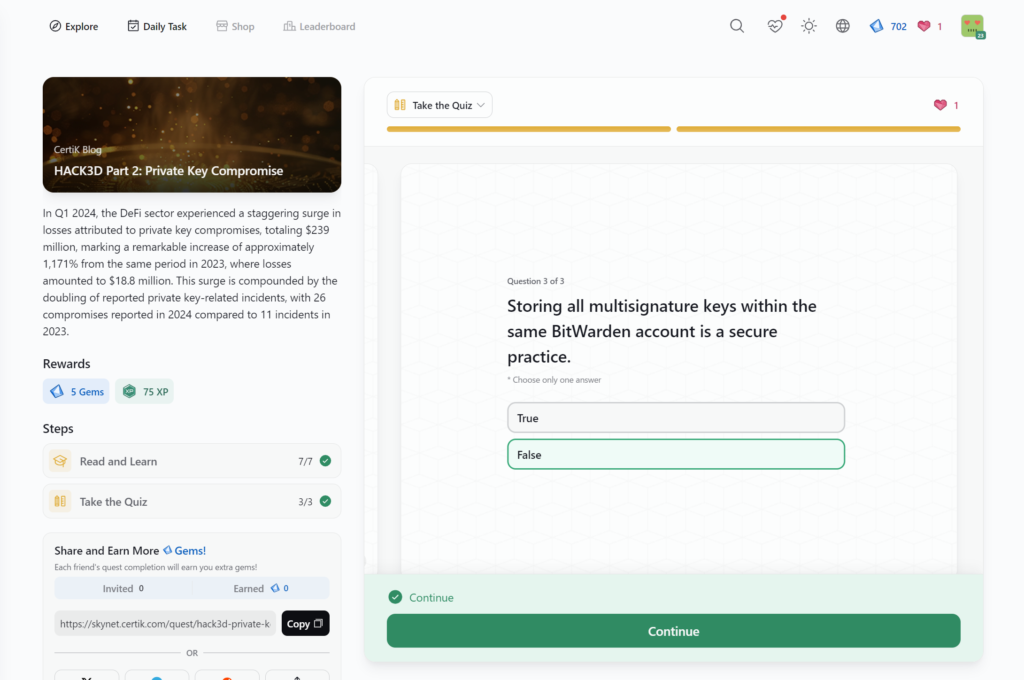
Hack3d Report Q2 H1 2024 – Part 2: Insights and Future Security Enhancements
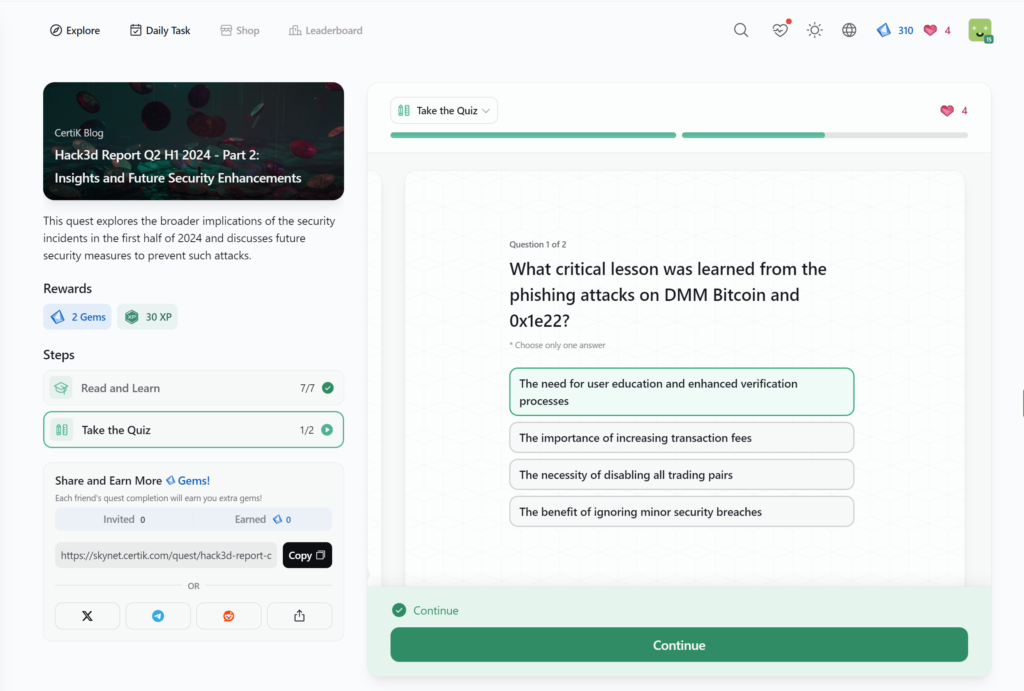
How AI is Transforming KYC for Crypto Project Teams
Understanding the Impact of FIT21 on Crypto Compliance
OKX and CertiK Fast Pass Program
Navigating DAO Governance and the Compound DAO Incident
Mastering Bridge Tracing
Introduction to Account Abstraction
How Binance Clawed Back M in Stolen Funds
Understanding AI’s Role in Enhancing Web3 Security
Evaluating Popular Web3 Messaging Apps
Web2 Meets Web3: Hacking Decentralized Applications
FBI warns of Crypto Social Engineering
Understanding the Android SpyAgent Campaign
A 0M Bitcoin Scam Uncovered
CertiK Uncovers Vulnerability in Apple Vision Pro
Understanding the DeRec Alliance
Hack3d Part 1: Most Common Attack Vectors in Q3 2024
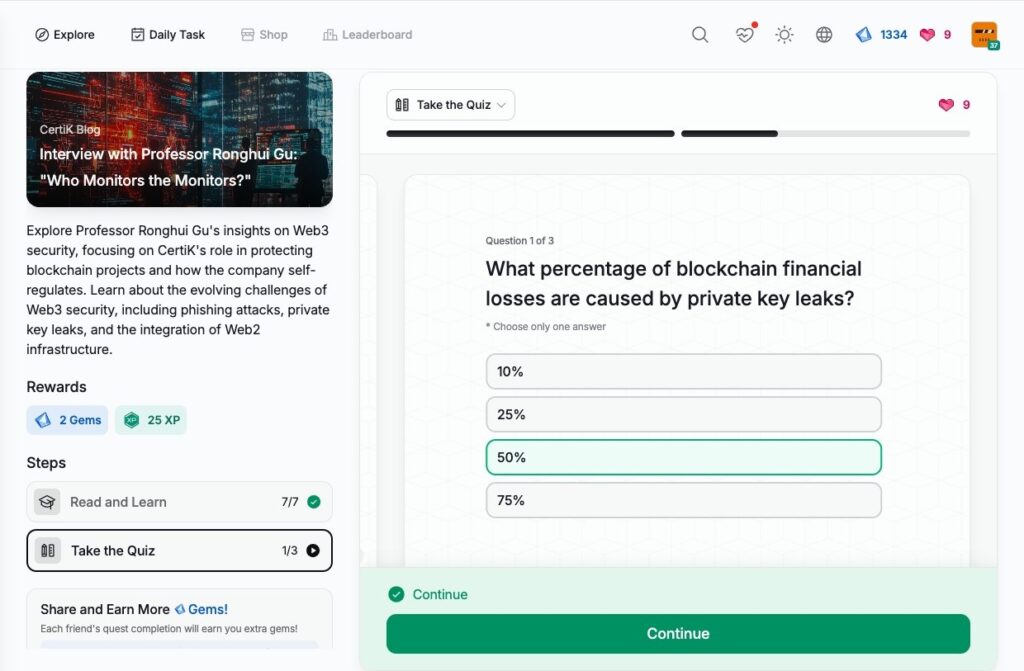
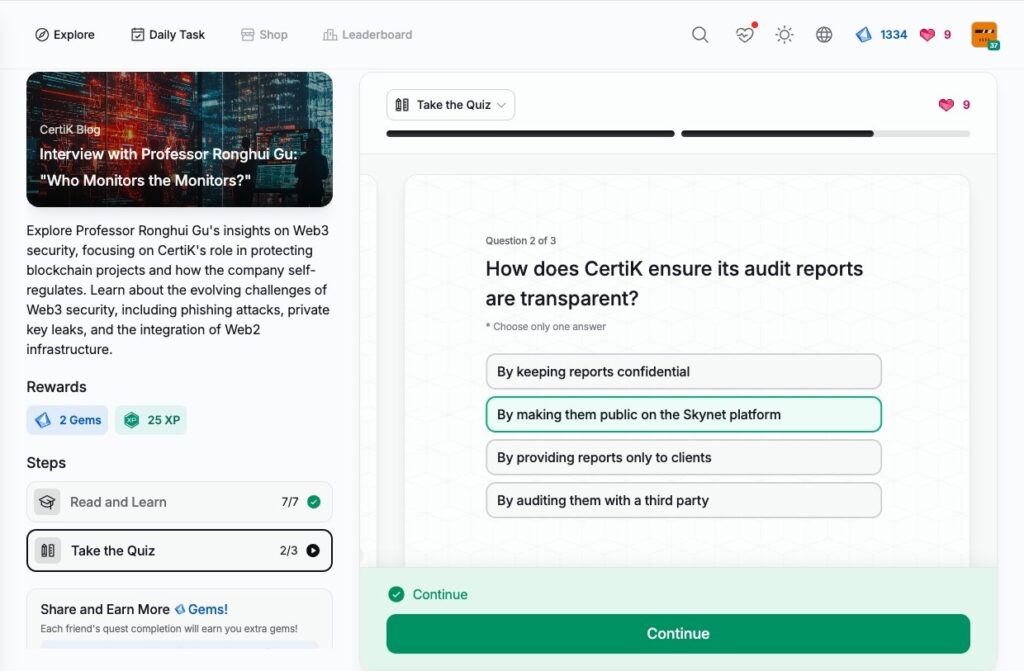
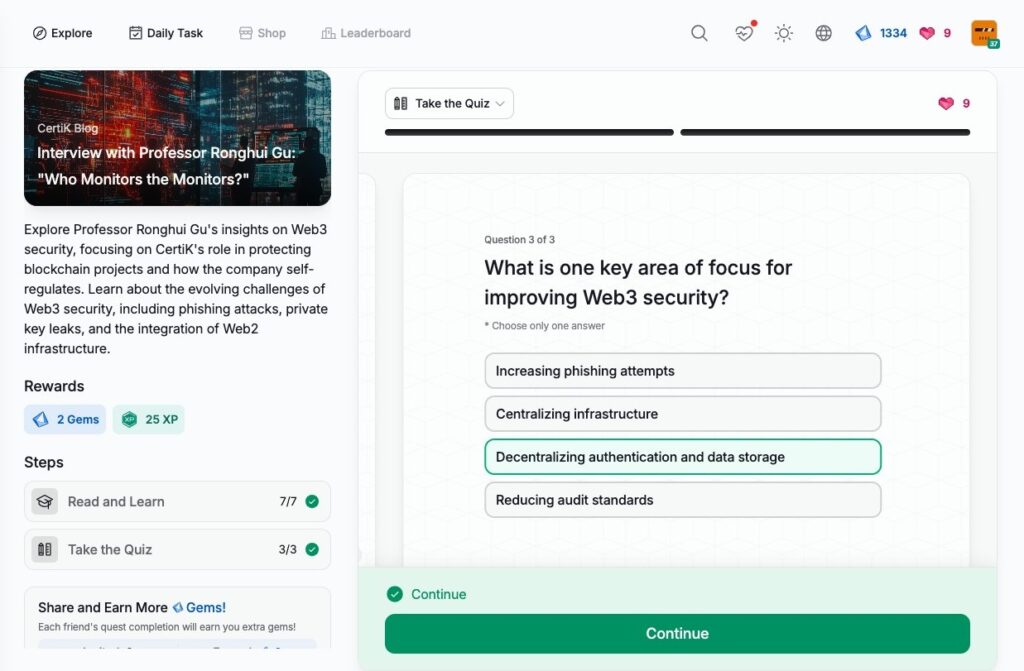
Interview with Professor Ronghui Gu: “Who Monitors the Monitors?”
Hack3d Part 2: Major Hacks of Q3 2024
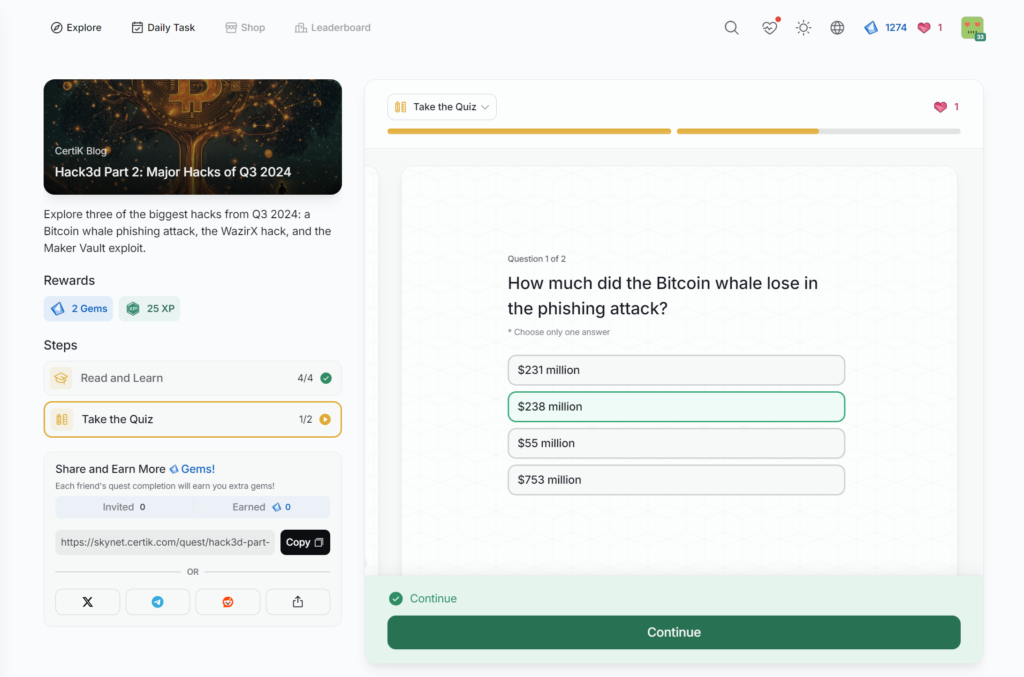
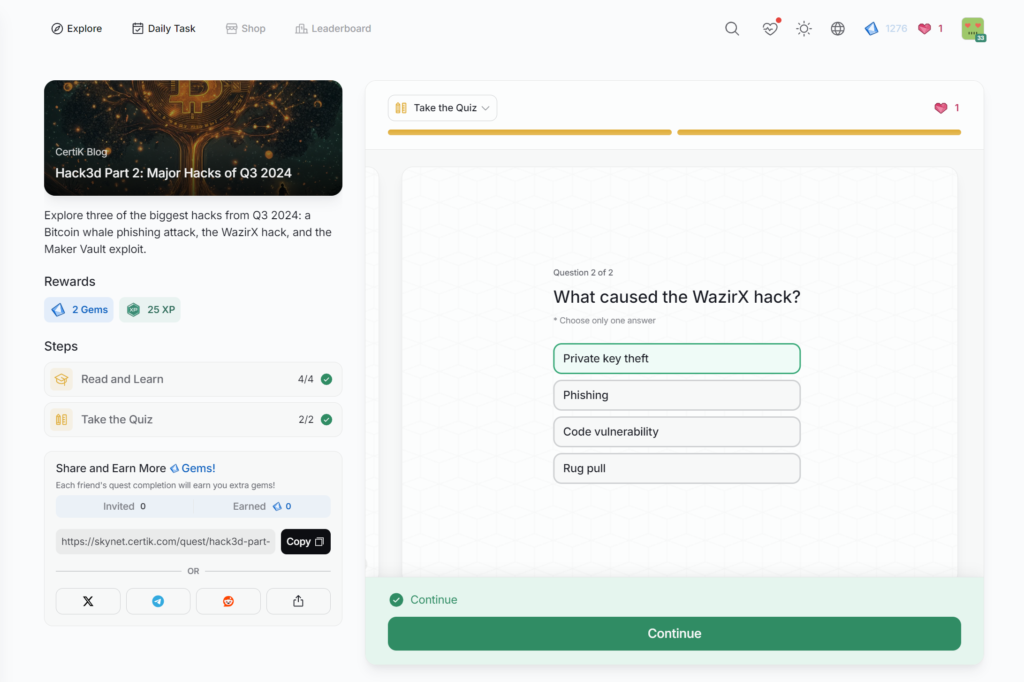
Understanding U.S. Crypto Tax Forms
Exploring the Rise of AI Memecoins
Proof of History Overview
Unmasking Crypto Market Manipulation
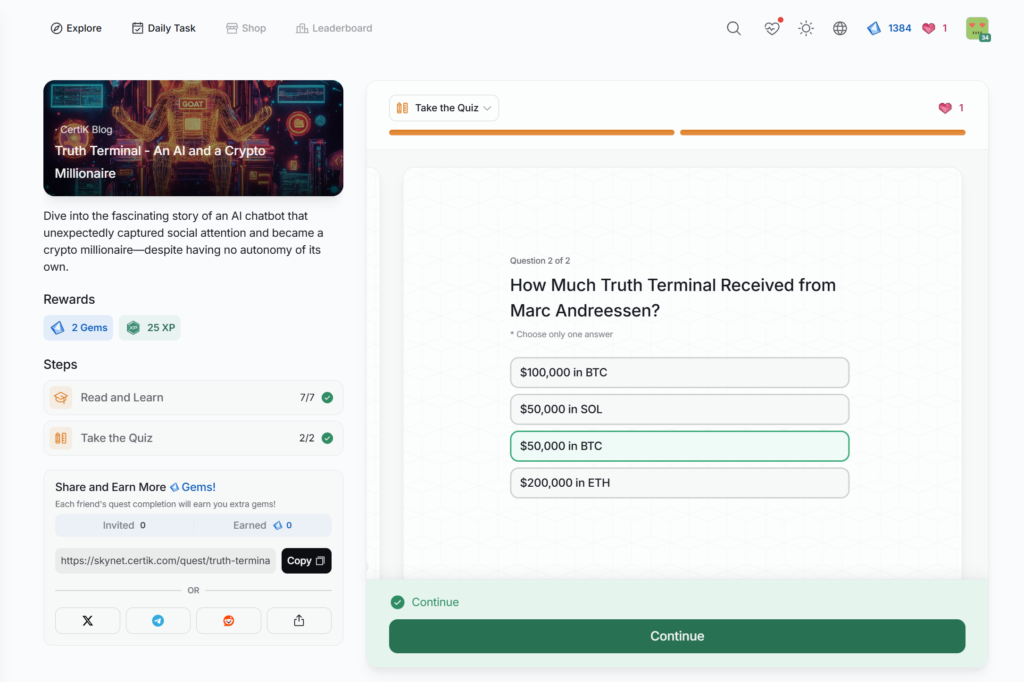
Truth Terminal – An AI and a Crypto Millionaire
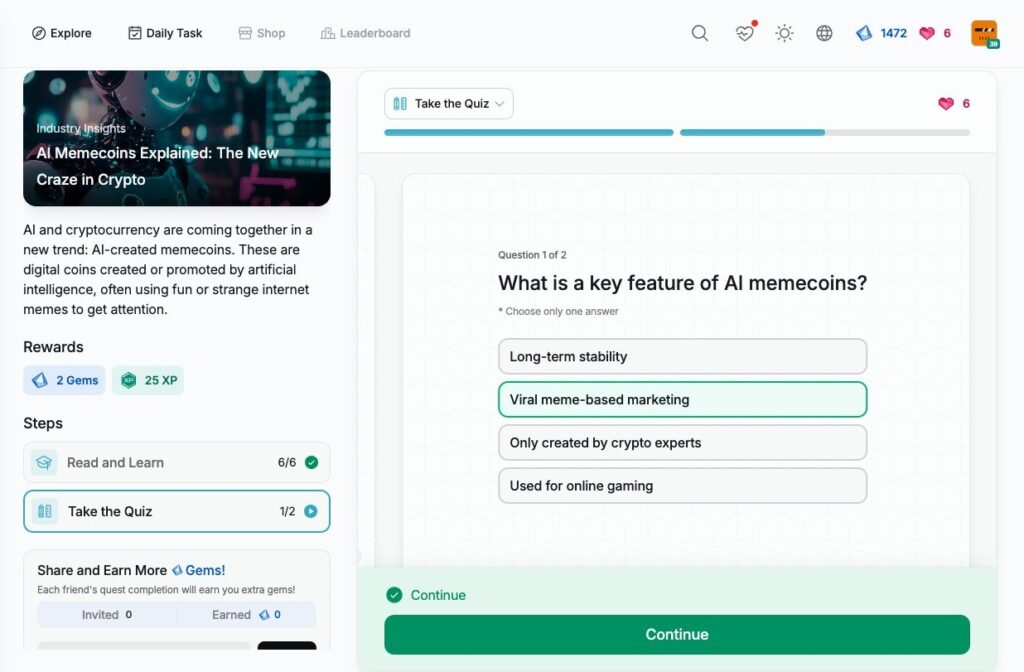
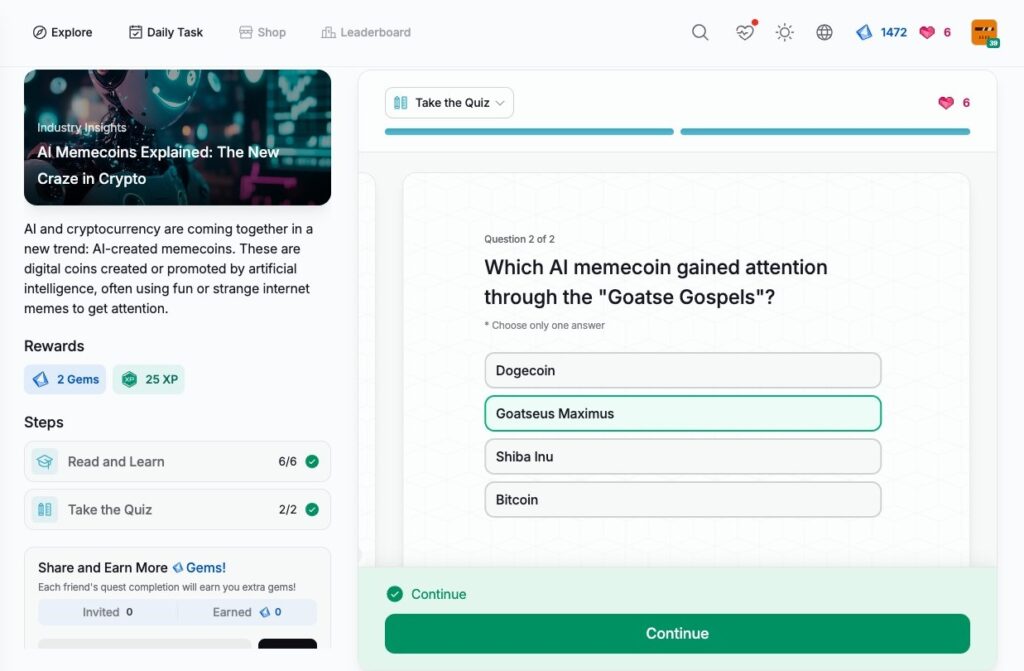
AI Memecoins Explained: The New Craze in Crypto
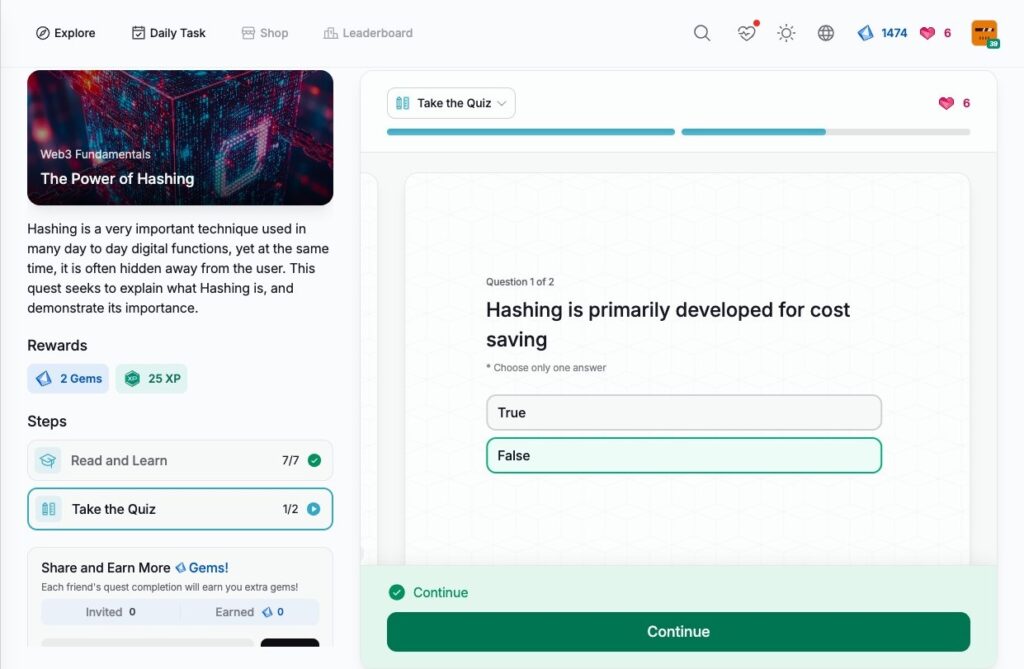
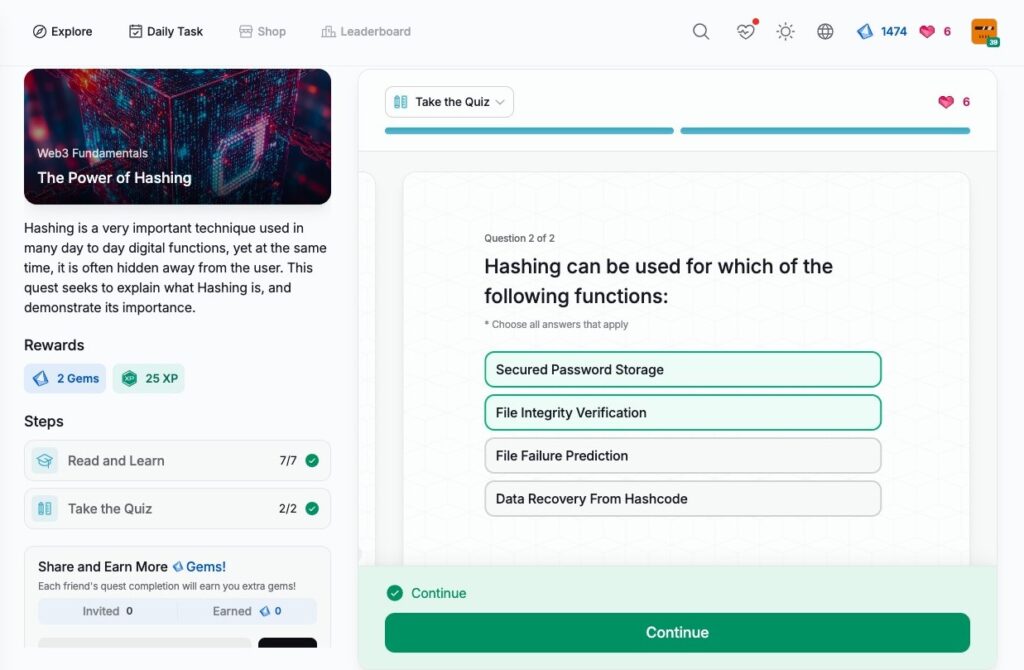
The Power of Hashing
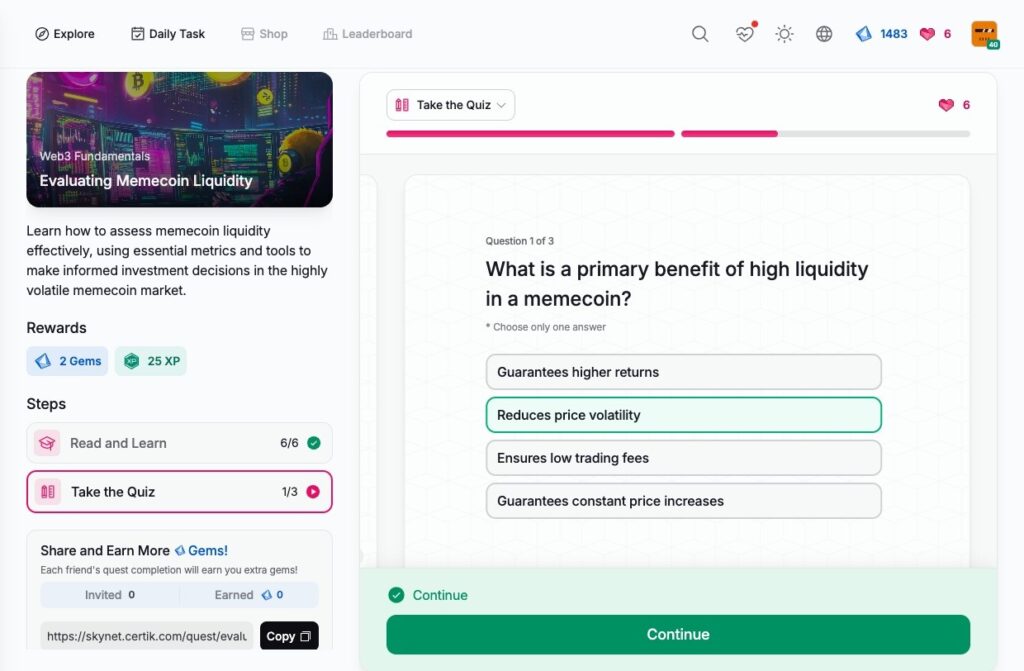
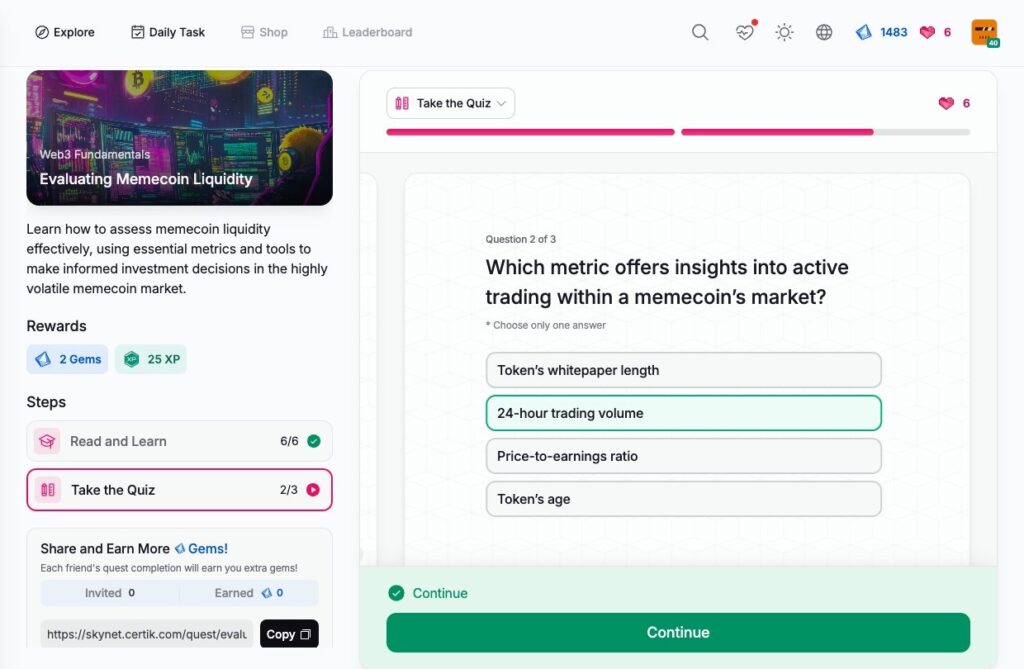
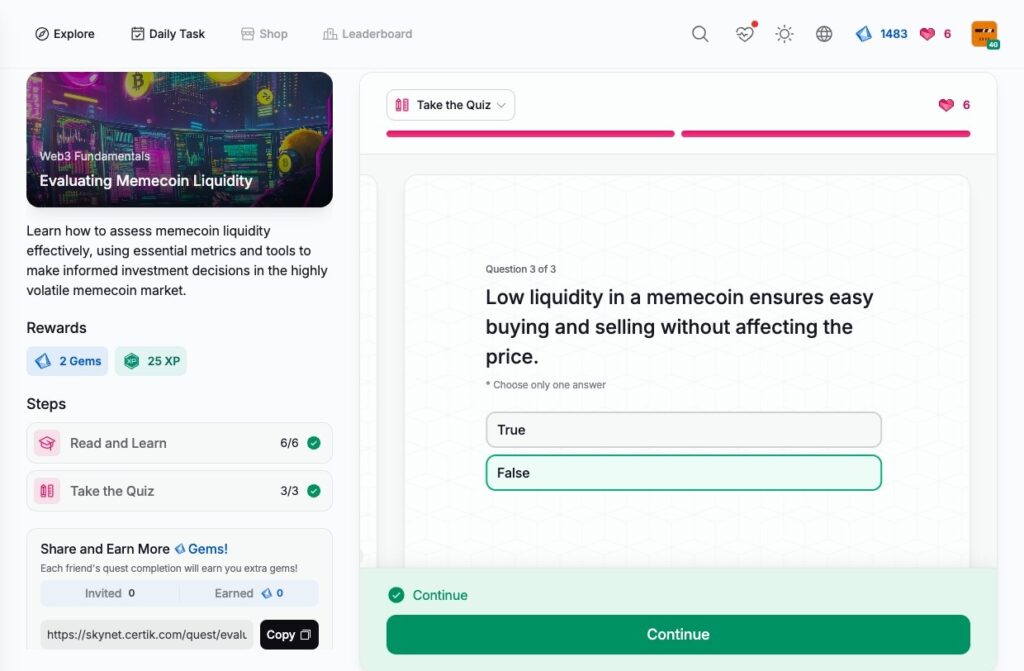
Evaluating Memecoin Liquidity
Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan – Part 1
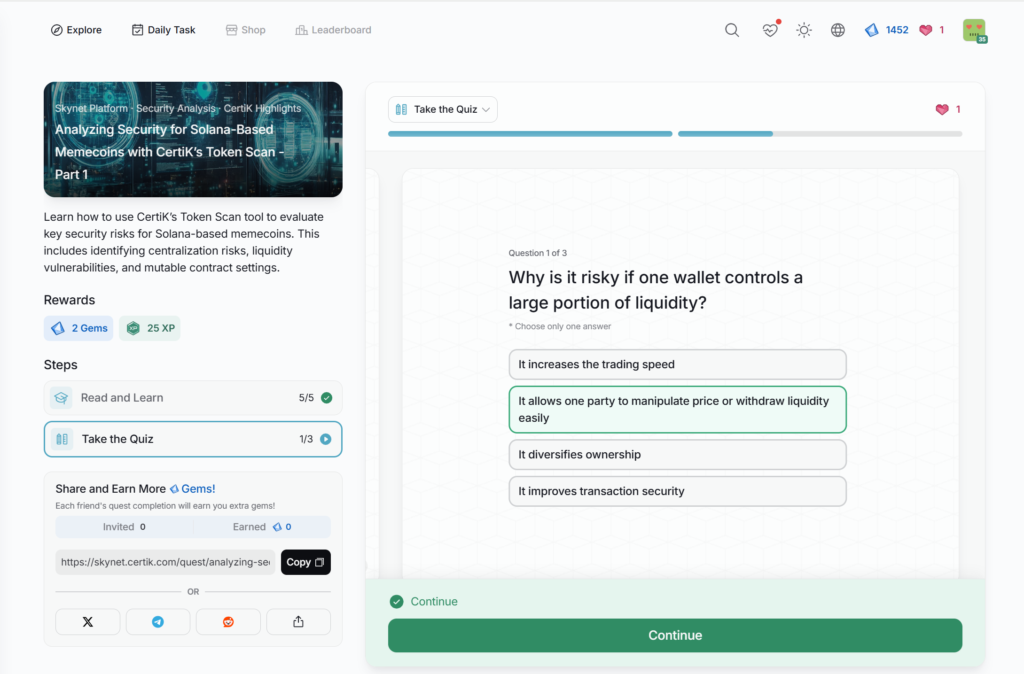
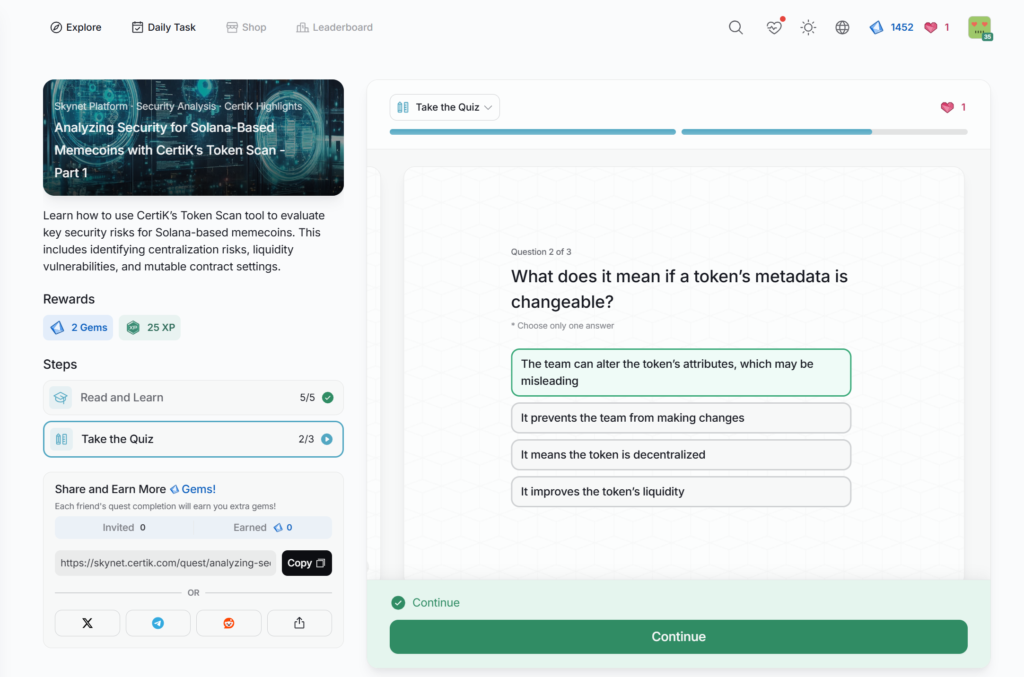
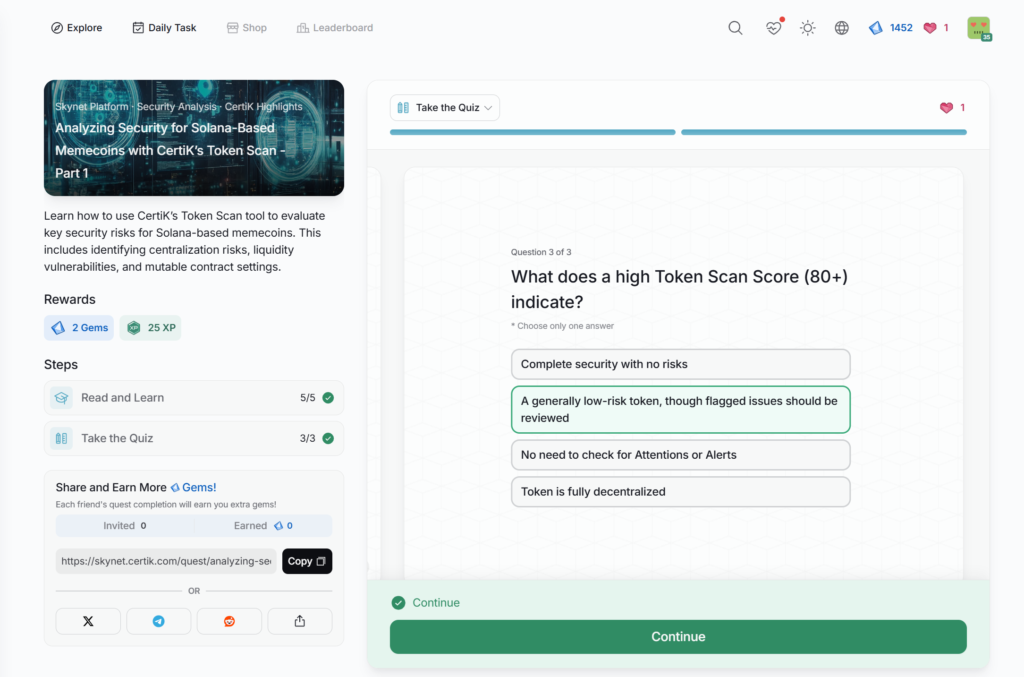
Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan – Part 2
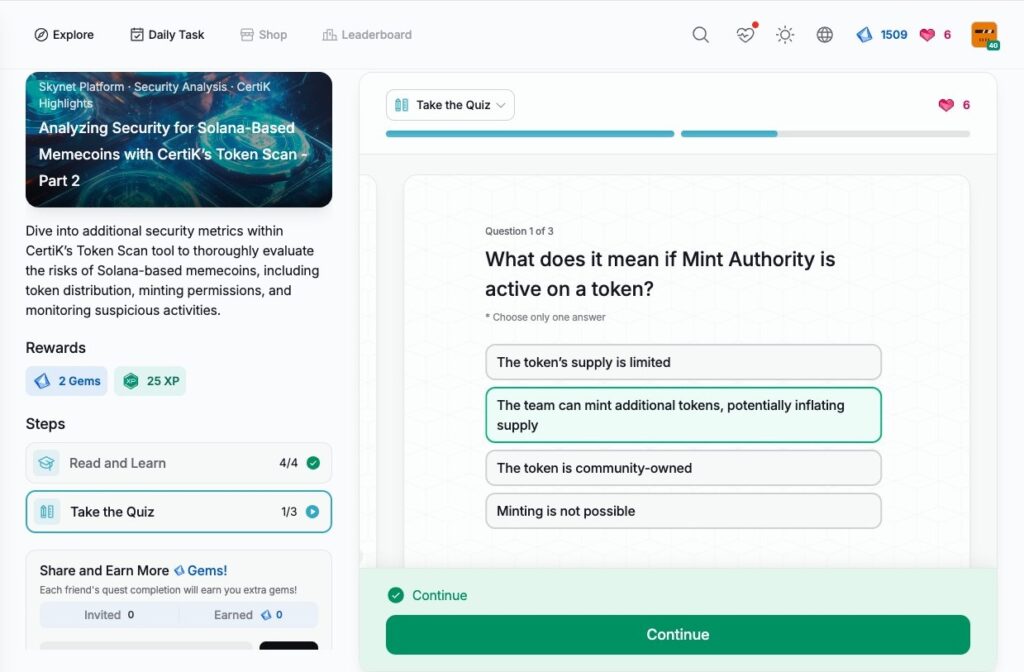
Case Study on the Risks of Phishing Attacks in DeFi
CryptoBottle Incident Analysis
Enhancing Security Awareness for Web3 Desktop Wallets
GOAT | AI Bot Meme
Pump.Fun
Understanding Stablecoin Reserves
Cybersecurity Best Practices for Telegram
Multi-Signature Wallets Explained
TNQ
How to Ace the CertiK KYC Badge
Understanding SkyNode: Blockchain’s Secure Foundation
Securing Solana SPL Contracts
Clipper DEX Withdrawal Vulnerability Exploit
World of Dypians | Future of Gaming, DeFi, NFTs and AI
Unlocking Ethereum ETFs With BlackRock’s ETHA
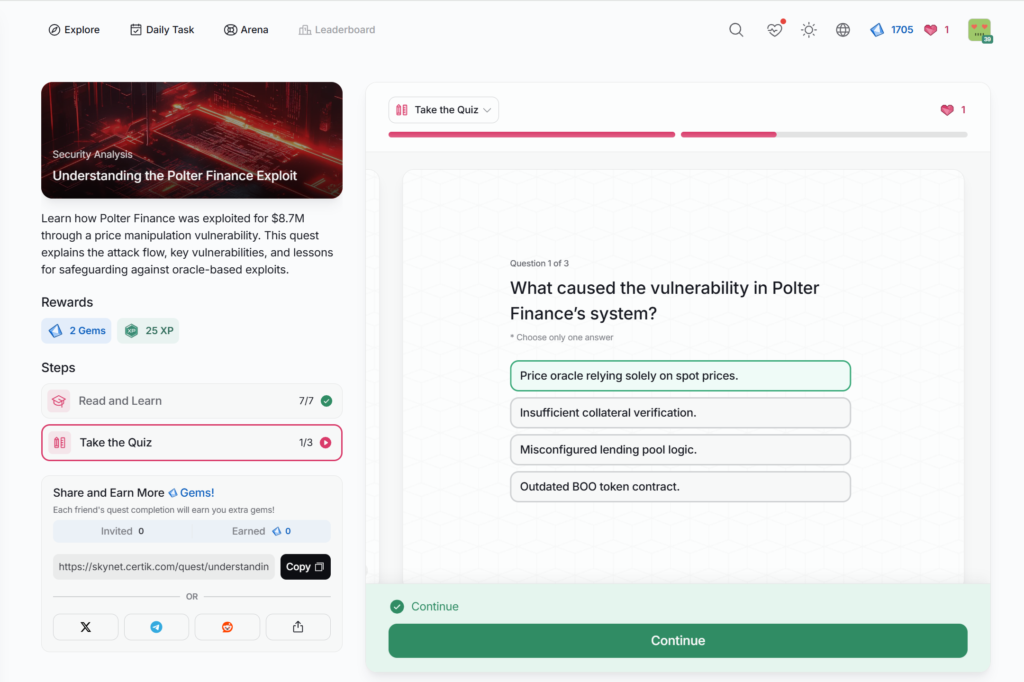
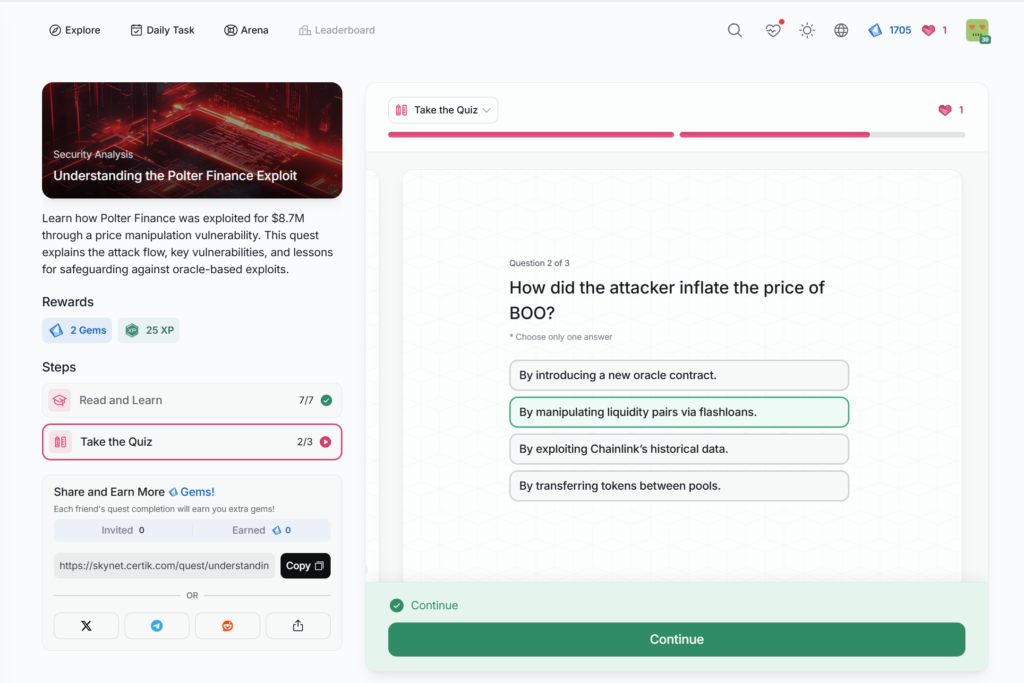
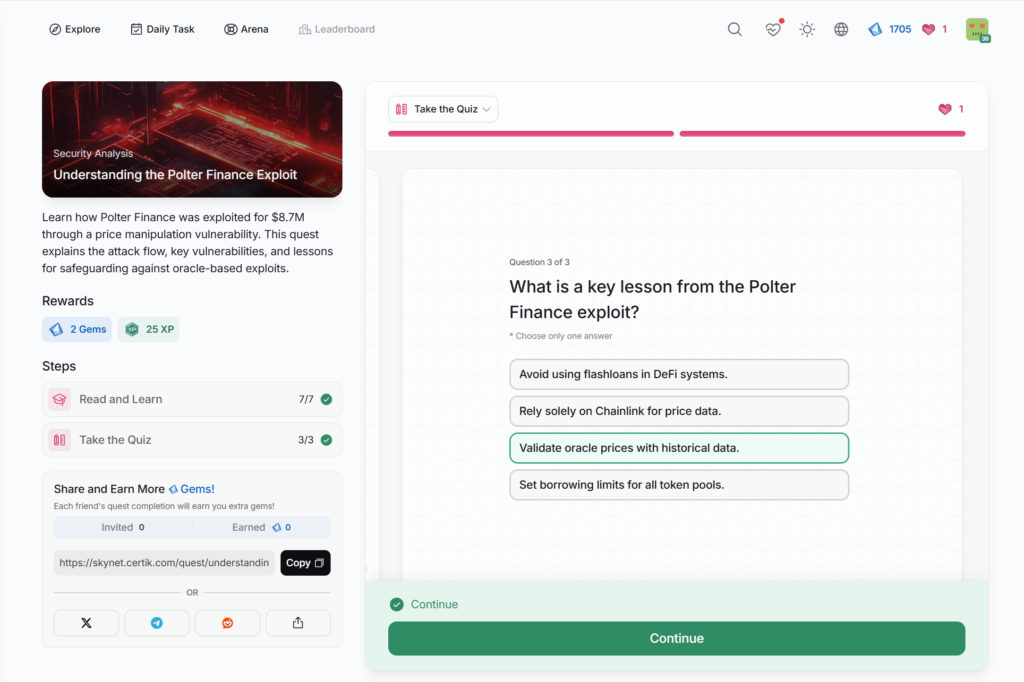
Understanding the Polter Finance Exploit
Protecting Against Crypto Phishing Scams During the Holiday Season
Stablecoin Risks: Identifying and Mitigating Vulnerabilities

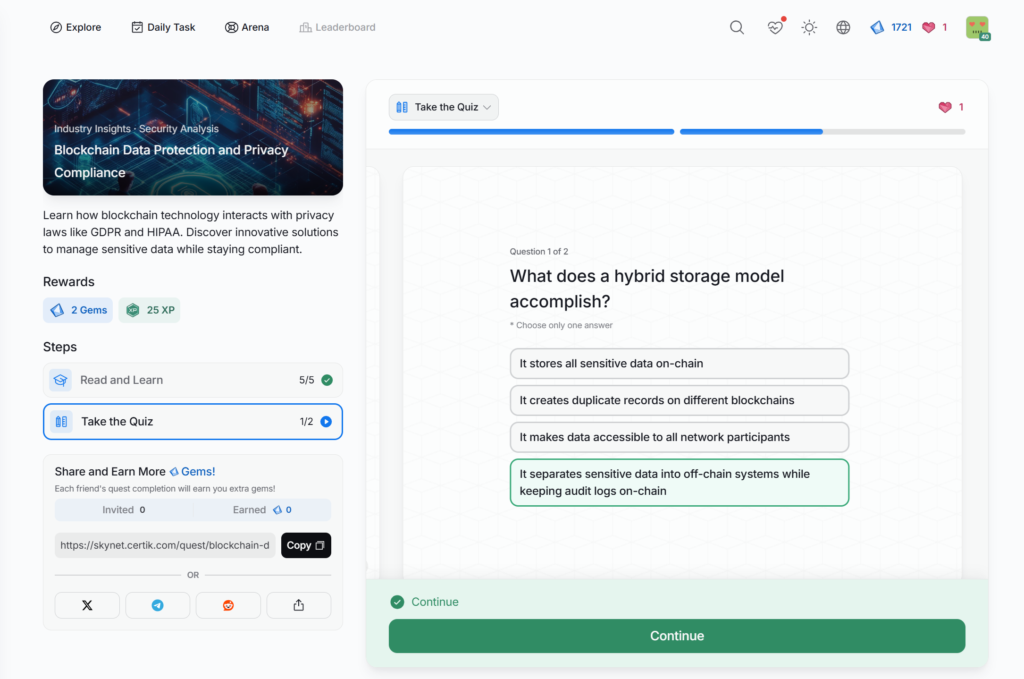
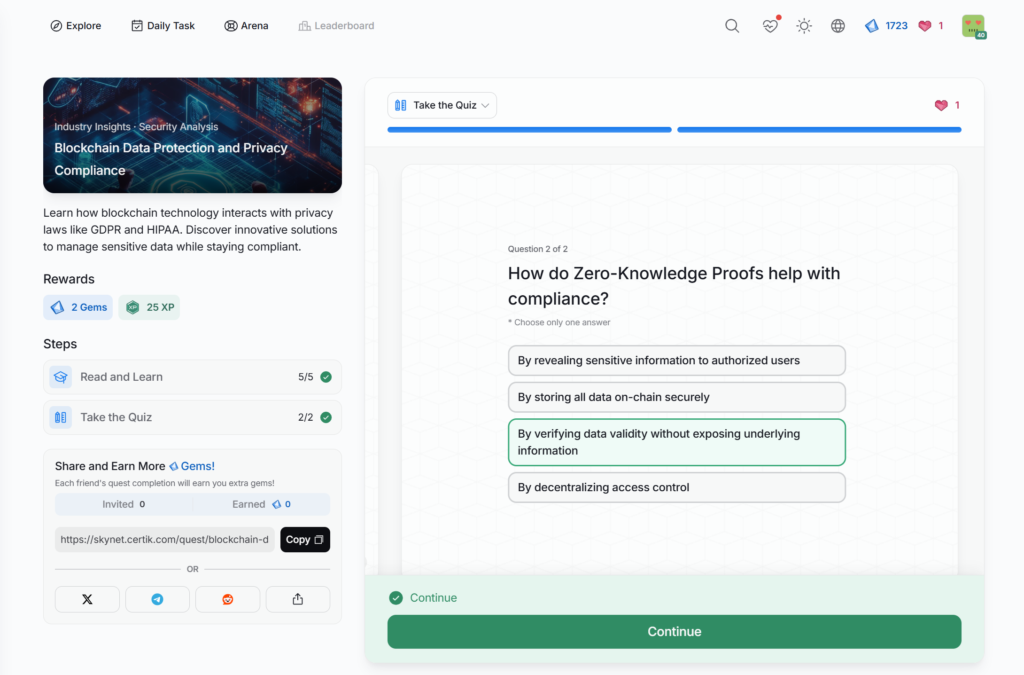
Blockchain Data Protection and Privacy Compliance
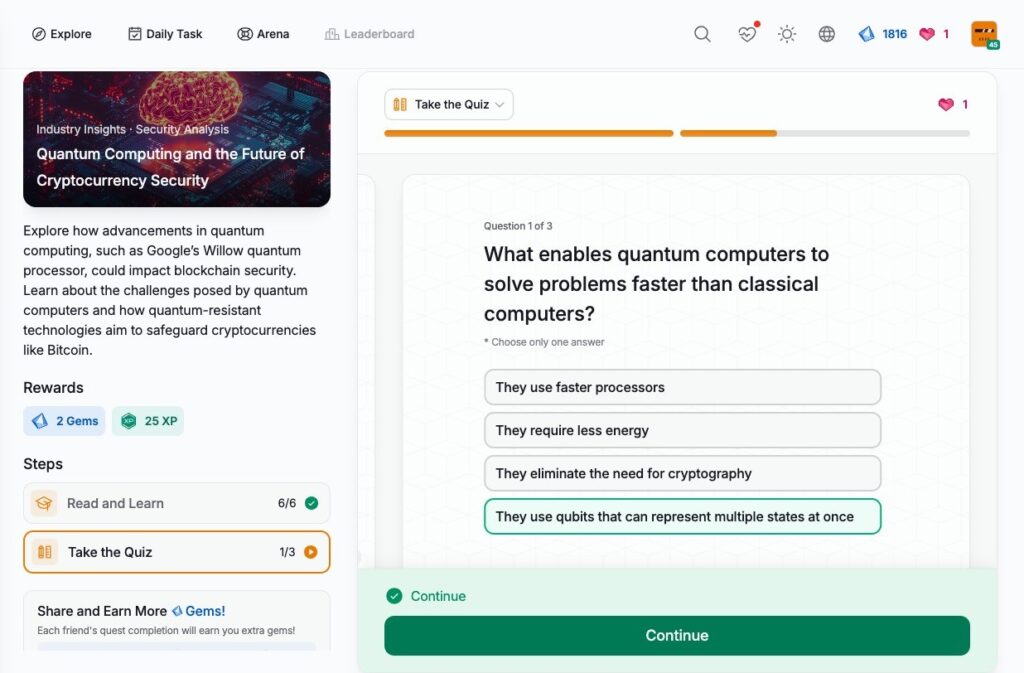
Quantum Computing and the Future of Cryptocurrency Security
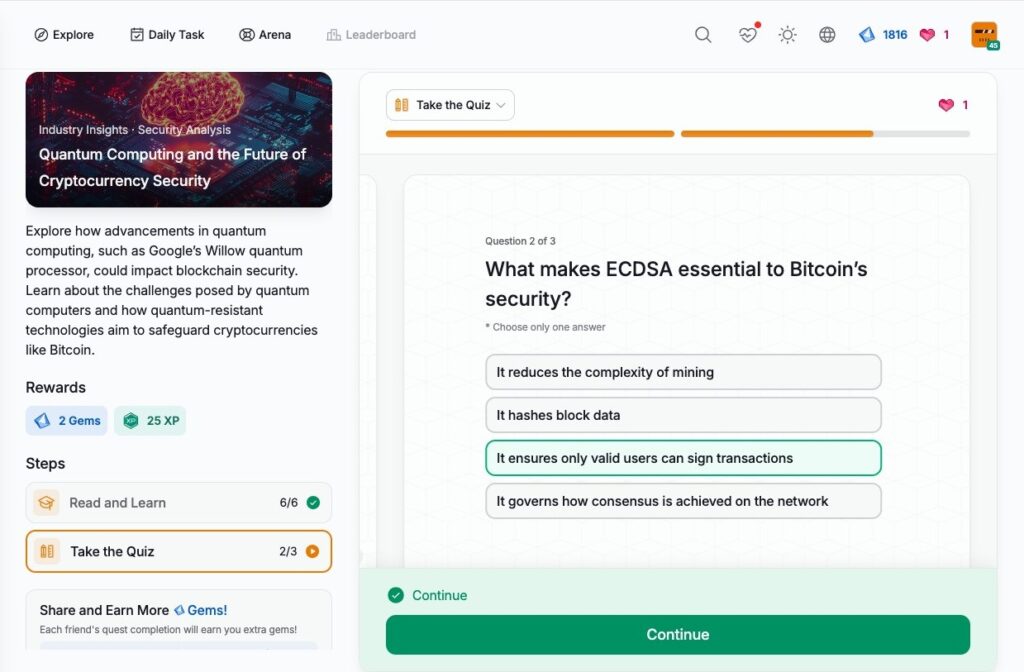
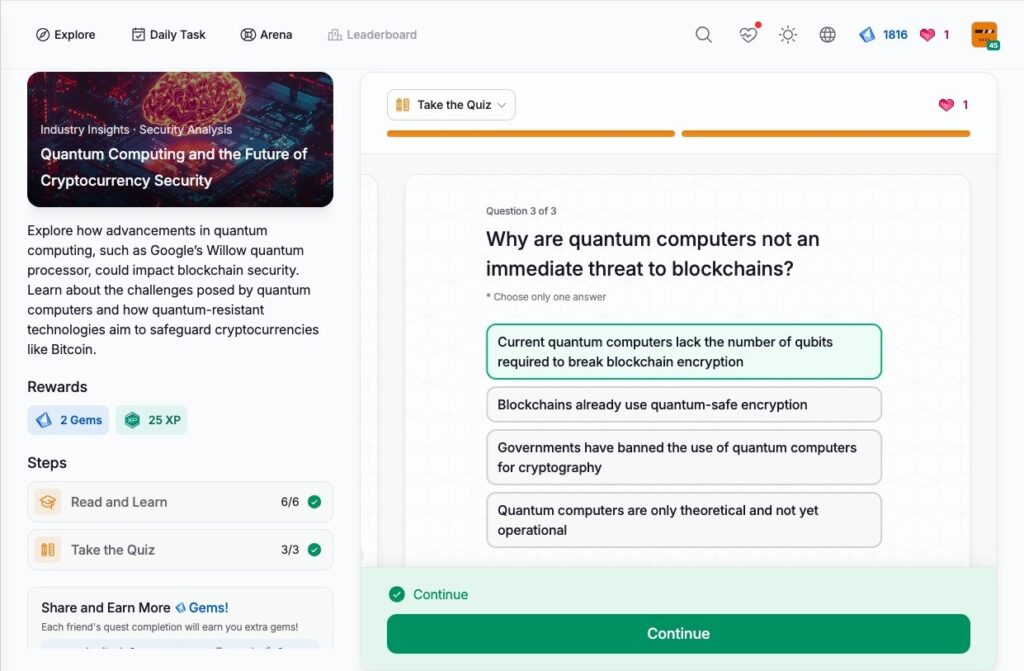
CertiK Hack3d 2024 Part 1 – Web3 Security by the Numbers
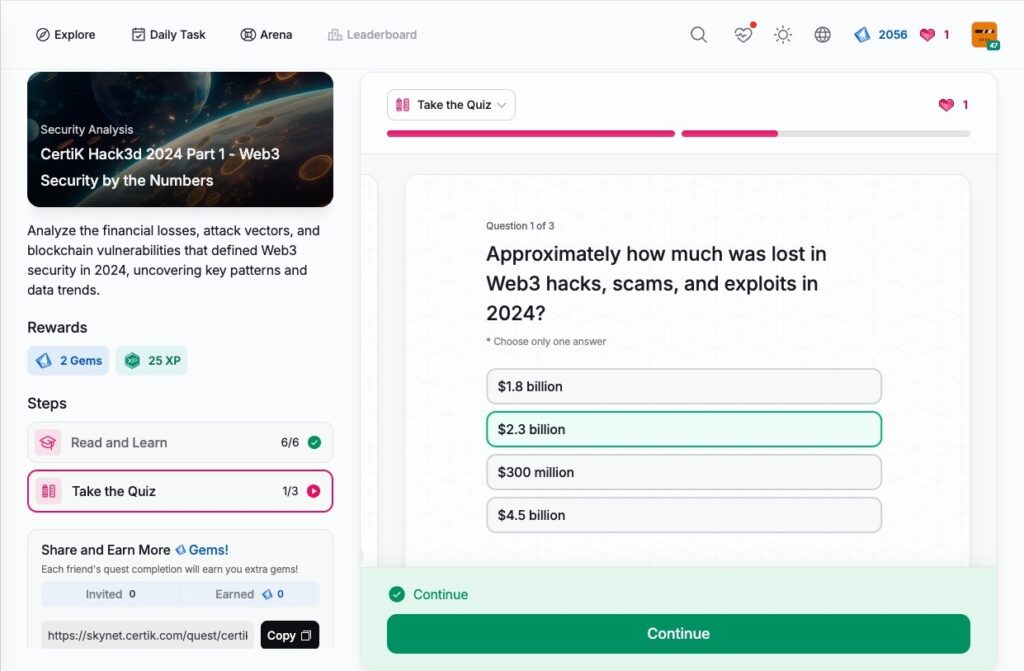
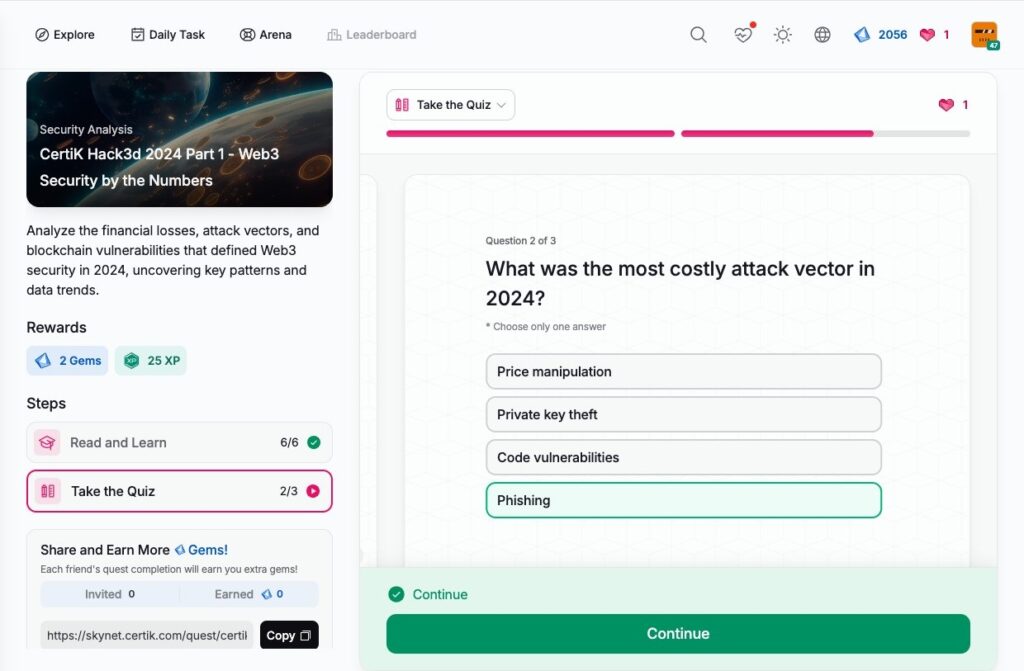
CertiK Hack3d 2024 Part 2 – Uncovering Major Incidents
CertiK Hack3d 2024 Part 3 – Building a Resilient Web3 Ecosystem
Kendu Inu | Organic Meme Community
Fundraising in the Web3 Industry
Protecting Web3 Workers from Fake Meeting App Scams
Exploring PSBT in Bitcoin DeFi Ecosystem
SpunkySDX | Revolutionizing Commerce with Blockchain and AI
Massa | The First Decentralized Cloud Network
Scam Pattern on Telegram Safeguard